Security researchers have released new tools that can bypass the encryption used to protect many types of wireless routers. Ironically, the tools take advantage of design flaws in a technology pushed by the wireless industry that was intended to make the security features of modern routers easier to use.
 At issue is a technology called “Wi-Fi Protected Setup” (WPS) that ships with many routers marketed to consumers and small businesses. According to the Wi-Fi Alliance, an industry group, WPS is “designed to ease the task of setting up and configuring security on wireless local area networks. WPS enables typical users who possess little understanding of traditional Wi-Fi configuration and security settings to automatically configure new wireless networks, add new devices and enable security.”
At issue is a technology called “Wi-Fi Protected Setup” (WPS) that ships with many routers marketed to consumers and small businesses. According to the Wi-Fi Alliance, an industry group, WPS is “designed to ease the task of setting up and configuring security on wireless local area networks. WPS enables typical users who possess little understanding of traditional Wi-Fi configuration and security settings to automatically configure new wireless networks, add new devices and enable security.”
Setting up a home wireless network to use encryption traditionally involved navigating a confusing array of Web-based menus, selecting from a jumble of geeky-sounding and ill-explained encryption options (WEP, WPA, WPA2, TKIP, AES), and then repeating many of those procedures on the various wireless devices the user wants to connect to the network. To make matters worse, many wireless routers come with little or no instructions on how to set up encryption.
Enter WPS. Wireless routers with WPS built-in ship with a personal identification number (PIN – usually 8 digits) printed on them. Using WPS, the user can enable strong encryption for the wireless network simply by pushing a button on the router and then entering the PIN in a network setup wizard designed to interact with the router.
But according to new research, routers with WPS are vulnerable to a very basic hacking technique: The brute-force attack. Put simply, an attacker can try thousands of combinations in rapid succession until he happens on the correct 8-digit PIN that allows authentication to the device.
One way to protect against such automated attacks is to disallow authentication for a specified amount of time after a certain number of unsuccessful attempts. Stefan Viehböck, a freelance information security researcher, said some wireless access point makers implemented such an approach. The problem, he said, is that most of the vendors did so in ways that make brute-force attacks slower, but still feasible.
Earlier today, Viehböck released on his site a free tool that he said can be used to duplicate his research and findings, detailed in this paper (PDF). He said his tool took about four hours to test all possible combinations on TP-Link and D-Link routers he examined, and less than 24 hours against a Netgear router.
“The Wi-Fi alliance members were clearly opting for usability” over security, Viehböck said in a instant message conversation with KrebsOnSecurity.com. “It is very unlikely that nobody noticed that the way they designed the protocol makes a brute force attack easier than it ever should.”
Separately, Craig Heffner, a researcher with Columbia, Md. based security consultancy Tactical Network Solutions, has released an open-source tool called “Reaver” to attack the same vulnerability. Heffner notes that once an attacker has successfully guessed the WPS PIN, he can instantly recover the router’s encryption passphrase, even if the owner changes the passphrase. In addition, he warns, “access points with multiple radios (2.4/5GHz) can be configured with multiple WPA keys. Since the radios use the same WPS pin, knowledge of the pin allows an attacker to recover all WPA keys.”
The important thing to keep in mind with this flaw is that devices with WPS built-in are vulnerable whether or not users take advantage of the WPS capability in setting up their router. Also, routers that include WPS functionality are likely to have this feature turned on by default.
First the good news: Blocking this attack may be as simple as disabling the WPS feature on your router. The bad news is that it may not be possible in all cases to do this.
In an advisory released on Dec. 27, the U.S. Computer Emergency Readiness Team (US-CERT) warned that “an attacker within range of the wireless access point may be able to brute force the WPS PIN and retrieve the password for the wireless network, change the configuration of the access point, or cause a denial of service.” The advisory notes that products made by a number of vendors are impacted, including Belkin, Buffalo, D-Link, Linksys, Netgear, TP-Link and ZyXel.
Viehböck said none of the router makers appear to have issued firmware updates to address the vulnerability. The US-CERT advisory makes no mention of updates from hardware vendors. The advisory also says little about which models may be affected, but if your router has a “WPS PIN” notation on its backside, then it shipped with this WPS feature built-in.




This is where you need to make a tradeoff – Do we allow home users to secure their network “easy and less secure” or “hard and more secure”?
Personally, I disable Wifi Protected Setup and setup everything manually. But I don’t see your average non-techie user doing this.
There is no clear solution, sadly.
On a Netgear router, under WPS settings, if the routers PIN is disabled, will this keep me secure.
Actually, there is a clear solution and that’s to have routers set up as secure out of the box, with a simple flyer shipping with them containing the codes and options to select when setting up clients.
My ISP has been doing that for years, works perfectly.
There is a working Google document that is publicly accessible which shows the results of various tests run by users against dozens of different routers with WPS. The results are all over the map, and a pretty fascinating look how differently the vendors approached this technology. Many allow users to disable WPS but doing so doesn’t eliminate the vulnerability. Other routers have WPS that cannot be turned off. Very few have shipped firmware updates to address these issues.
https://docs.google.com/spreadsheet/lv?key=0Ags-JmeLMFP2dFp2dkhJZGIxTTFkdFpEUDNSSHZEN3c
That’s a good report except for one thing. They did not test the Belkin N150, F9K1001v1 with the firmware update Belkin put out on 12/27. It is not available from their website but you can get it by checking for updates in the router’s configuration screens. I asked Belkin what changes were made in the update but all they could say was thank you for updating and that I should reset the router. No details on what it did at all. It’s numbered 1.0.12
I don’t see how this is a security risk at all. In order to activate the WPS, a person has to push a button on the router itself which has a timed window where the person has to enter the code onto their computer. After the code is entered, the window closes and WPS shuts off.
If the attacker has access to the router itself to where they can activate WPS and sit there waiting for the brute forcer to find the right combination, than they most likely will be able to turn the router over and look at the combo and type it in.
The only time this would be a security risk is if someone that owns the router, presses the button and never authenticates it with their computer. This would cause the WPS time frame to stay open until the attacker bruteforced it and activated it. But the chances of someone actually leaving that window open are probably less then 1 in a million. And the chances of an attacker finding that person would probably be impossible.
The physical button is only used in the context of the “Push-Button-Connect” option.
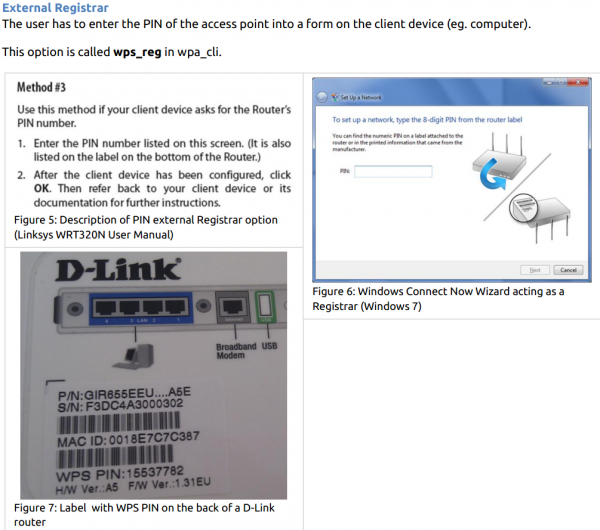
For using the “PIN External Registrar” option (that’s the one the brute force attack is targeted at) you only have to be within the range of the wireless access point.
Thanks for clarifying that, Stefan. For those who would like to better understand how these attacks can be carried out, I’d strongly suggest reading the Stefan’s paper, linked above but also here:
http://sviehb.files.wordpress.com/2011/12/viehboeck_wps.pdf
Even though that seems to be the case, it still doesn’t validate it being an exploit. At least on the several routers I’ve tested it on.
Once a user types in the pin code they are asked to set up the wep/wpa/wpa2/etc.. security settings. Also once the security has been set up, the WPS is completely disabled (unless you reset the router completely and reconfigure it.)
This “exploit” would only work on routers that have never been configured before and most likely not even in use. Unless there are some old routers that don’t function this way. As I said, I tested this on several routers I own and all of them ask you to set up the security pass phrase AFTER you type in the code.
The only possible problem this would be is if the attacker hijacked a non-used router through bruteforcing and then opening up the network for other people to connect to. Then doing arp poisoning or something of the sort.
WPS appears to provide services to allow new clients to join the wireless network. That wouldn’t be possible of WPS was “disabled” after the initial setup.
My whole point was the fact that it doesn’t show wps after it’s initially set up. After the pin is entered, it asks the user to set up the encryption. Re-read my reply.
I’ve read your post, it makes no sense. WPS is not magically disabled…period. While I can appreciate you doing some leg work to try and verify, what you suggest would make the paper, and the related advisory from US-CERT, and the related brute-force tool provided by another party, and the firmware upgrades from vendors…all pretty pointless. Do you really think that’s a reasonable position?
Well considering that no one can access WPS directly without pushing the button after the security is set up, in my mind that means its disabled. At least the “exploit” is.
Even if the WPS isn’t fully disabled, like I said, it’s no longer possible for someone to access the wps-reg in order to bruteforce the pin. Which goes back to what I said previously, after the proper security settings are set up, the wps-reg no longer works. And usually the proper security settings are set up after the initial use of the router.
In order to use the router, you need to setup the security which in return makes wps-reg unavailable for anyone else.
“Well considering that no one can access WPS directly without pushing the button after the security is set up,”
Read the paper already, it proves this is an incorrect assumption. I suspect it’s based on experiences with the standard interfaces that get exposed to us normal users.
PBC is not relevant in this vulnerability. It’s the PIN method via what the paper refers to as an *external registrar* that is being brute forced. I think you’re getting hung up on the fact that the typical way to activate WPS is either pushing a button on the AP or providing a client PIN via the AP web interface. In the paper, those are called push-button-connect and PIN via internal registrar respectively.
In at least some implementations there is an additional registrar interface that allows a client to get information about the wireless network with the PIN from the AP. That is what is being brute forced.
Here is a post from back in 2009 that illustrates this well enough. It shows an example of wpa_cli being used to fetch AP settings from hostapd. How difficult would it be to brute force this?
http://lists.shmoo.com/pipermail/hostap/2009-August/020126.html
Exactly, Matt.
If you doubt whether your WPS-equipped router can be attacked this way, why not download the free tools linked here in this story and try them against your router? That’s really the only way to find out in the short run, given the sheer number of different routers out there. And if you do this, please post your results here 🙂
Thanks!
I didn’t even know about WPS until I recently purchased a new wireless router. Once I saw how it worked, even with the button push, I had a gut reaction that told me this was a bad idea. So I disabled it immediately on my router.
It should be easy enough to put in a long enough delay before trying another pin that would make brute force all but useless though. In fact, doing so on websites and everything else that uses a password would make things a lot more difficult for attackers.
That’s nothing! Now THIS is bad ass:
Owned Over Amateur Radio (Remote kernel exploitation) [PDF]
http://vulnfactory.org/research/defcon-remote.pdf
rose-exploit – Remote kernel exploit for ROSE amateur radio [code]
https://github.com/djrbliss/rose-exploit
Using Part 15 Wireless Ethernet Devices For Amateur Radio (AX.25 over Ethernet) [ftp/PDF]
ftp://ftp.tapr.org/software_lib/ether/Ham_Ethernet_GBPPR.pdf
Google: ax.25 over ethernet
THIS is the REAL global conspiracy!
At a conceptual level, why not simply require the button to be pushed before the PIN is useful as an authenticator? meh, nevermind, just read the paper. pushing a button is too hard apparently, so we had to engineer 2 additional ways to make it easier? Is there just one engineer working on wireless and is it the same guy since WEP? 🙂
in many corporate settings, the router is physically inaccessible to the people setting up network clients…
Distribution of labour, software (so client configuration) is done by different people from hardware maintenance and configuration and those people are not allowed access to the hardware.
And the larger the corporation, the harder such rules are to change.
Most people who use wireless (at home or work) don’t need it. It’s like Java — unnecessary in most but not all cases, and wrought with flaws that don’t exist in other technologies.
As for me, I laid a single cable over a year ago. It hasn’t moved, and in that time I’ve had 0 seconds of downtime related to the local network. Compare that to my parents wireless network that experiences downtime during over half of my visits.
Admit it, there’s at least a small masochistic desire in most people. When choosing between two options: one proven and robust, the other badly flawed, more often than not, they go with the one that gives them problems.
It was hard to find!
I have a CableOne supplied Motorola modem/router. I logged into the router and searched, but I could find nothing labeled WPS. I was about to assume my router didn’t have it, when I clicked help under the wireless network section and found a description of what WPS was. That made me search harder, and I found it.
There was a drop down menu under the words – Automatic Security Configuration. It was set on DISABLED, but the menu had two other options – WPS and SES.
Found it! Apparently it ships disabled, but if you can’t find WPS, you might want to look for Automatic Security Configuration. Even if it is disabled you might want to know if it is lurking in your router.
Does this continue as a vulnerability, even after configuring WPA2 encryption?
@doug:
The important thing to keep in mind with this flaw is that devices with WPS built-in are vulnerable whether or not users take advantage of the WPS capability in setting up their router. Also, routers that include WPS functionality are likely to have this feature turned on by default.
Belkin put out a firmware update on 12/27 so it looks like they’re on top of this.
Thanks, Dch48. Do you have a link to the update?
I just did the check for updated firmware from within the router’s configuration screen. It said there was one and let me download and install it from there. The router is a Belkin N150
Great article, Brian.
I think there needs to be serious discussion in the industry about wireless security in general, not just WPS. We all know WEP is flawed and can be cracked in minutes, but if you go war driving I bet the majority of wireless networks that you see will be protected by WEP and not WPA or WPA-2, if they’re secured at all.
The biggest reason for this is probably that some major ISPs are still recommending that their customers use WEP. I worked for AT&T for a couple of years, and I did freelance work as a contractor working with some AT&T customers, and as of last year they were still recommending WEP to all of their customers. The equipment ships with WEP instructions, and when you call to setup DSL or U-Verse the tech support person tries to walk you through setting it up. The worst part was that I told one of them I had already setup WPA for a customer and they informed me that I shouldn’t do that because it’s unsupported!
On top of that, most WPA “keys” are just simple one word passwords. The problem is that the nature of wireless makes it possible to do a dictionary or brute force attack as fast as your computer can process it. With modern processors that’s millions of tries per second.
The way that I secure my own wireless networks is with a long (really long) key made up of special characters. I usually put a long “passphrase” style key on the guest wireless, making it more susceptible to a good dictionary attack, but also easier for guests to remember.
I do understand the trade off between ease of use and security. I really do. I know most people aren’t going to enter a gigantic random key into each device that they need to configure. But that doesn’t mean that basic security can’t still be accomplished. Make the key 12 characters long with uppercase, lowercase, numbers, and a couple of special characters thrown in. People can deal with that. It’s not the end of the world. Start producing wireless routers that won’t let you put in a passphrase unless it is a minimum of 12 characters with the same special requirements. Start producing routers that don’t do WEP. I haven’t even crossed a non-WPA compatible device in years. Or, if you feel that you just have to leave WEP in for backwards compatibility, default to WPA and throw a big huge warning on the screen if people try to change it to WEP.
Wireless is just pathetically insecure, but it doesn’t have to be. There just doesn’t seem to be serious dialogue or attention being given to the issues surrounding it.
So, once again, great article, and thanks for raising attention to this issue!
Security is even less likely if one of the ISP’s outsourced techs comes to your house to set it up. I found my parent’s network set to “no security” when I went to their house recently. Apparently he’d had trouble getting my father’s older laptop to connect (I think its wifi card is broken) so he just turned off all the security on the network. The cynic in me thinks he wanted to be able to drive by at some time in the future to steal their signal.
Shades of Microsoft Bob1
The problem is not the easier PIN for setting up. It’s the router replying and helping someone out who’s guessing the PIN.
I believe MS Bob had a feature that if you entered the wrong password enough times, it replied “It appears that you forgot your password. Would you like to set a new password?” or something like that.
What were they thinking? It’s great to help out the non-technical folks with a simple PIN. But if they can’t enter 8 digits correctly maybe they shouldn’t be the ones setting up the router after all.
@josh, to get a feel for WiFi security, check out the stats page on wigle.net. WEP is far less common than it used to be, but still far TOO common for 2011/12.
I found my ActionTec PK5000 (CenturyLink DSL) had WPS turned on by default in PBC mode. Thankfully it can be completely turned off. Two interesting features in the config are the ability to choose the mode you want to use (Push Button (PBC), AP PIN, or Device PIN), and a stored list of each device that has config’ed via WPS.
Has anyone tried compiling Reaver on OS X (Snow Leopard)? Could be interesting to test the various APs I have lying around.
Re: OSX and Reaver, I found a couple tickets in their Wiki where they say there is not, and probably never will be, support for OSX. A Linux VM with a USB WiFi dongle would work under VMware, etc.
Pretty much surprised as I found WPS on my router turned on. Even much more surprised that it really took less then 4 hours to get my >15 chars WPA passphrase.
The reaver tool itself is a nice polished piece of software.
Hats off to you Stefan!
I believe Reaver was published by Tactical Network Solutions not Stefan…
Brian, could you possibly interview AP vendors and ask them for info about how to disable WPS PIN Registrar? I have a Linksys E1200 and while I could find and download the manual, and found that it supports PIN, I couldn’t find anything in the manual about disabling it. (The AP isn’t plugged into anything, and I’m not in a hurry to play with it.)
I was surprised that the manual didn’t seem to mention how to turn it on/off.
Buffalo WZR-HP-G450H, DD-WRT v24SP2-MULTI (05/27/11) std (SVN revision 17140)
Disabling everything WPS or ‘AOSS’ (OEM Branding) related, disables the PIN method as far as I can tell. I deleted the wireless network in Win 7 and then tried to reconnect. Where normally you would see the PIN box with the little router symbol (with the option to enter a straight WPA2 key by clicking a link)…with everything disabled, I just get the normal WPA2 Key Entry Box.
PD
Thanks for posting this. . . easy to disable AOSS on the G300NH, running “DD-WRT v24SP2-EU-US (08/19/10) std,” a Buffalo custom rev.
WPS is not available with this version of DD-WRT, which is the default, but only with a “User Friendly” (Buffalo’s term) firmware alternative that comes with the router. Also, AOSS is only available when the G300 is used as an AP, not in other modes such as a bridge.
Haven’t got around yet to flashing this with Open-WRT, so don’t know what options are available there.
___________________
My mantra: Security is inversely proportional to convenience.
I have an Actiontek GT784WN (router/DSL combo). It has WPS enabled by default. Just click the virtual button to disable, after locating it. However, you wouldn’t know WPS even existed without reading Krebs. Thanks for the info, I have now disabled WPS.
I also have this router and my WPS button suddenly began flashing, sometimes green, sometimes red. I was concerned that someone outside my network was attempting to hack in and looked for additional knowledge re the WPS…but I don’t know where I need to go to disable this feature. I am using a MacBookPro as my main computer at this time………………..help, please.
Game Over…it appears even with WPS disabled, reaver is still obtaining WPS PIN and WPA PSK. I wonder if the router companies will respond with a method of mitigating this vulnerability. I would think small or mid-sized businesses running these vulnerable routers have valuable data loss potential.
See here:
http://arstechnica.com/business/news/2012/01/hands-on-hacking-wifi-protected-setup-with-reaver.ars
Cisco response.
http://tools.cisco.com/security/center/content/CiscoSecurityResponse/cisco-sr-20120111-wps?vs_f=Cisco%20Security%20Response&vs_cat=Security%20Intelligence&vs_type=RSS&vs_p=Wi-Fi%20Protected%20Setup%20PIN%20Brute%20Force%20Vulnerability&vs_k=1
As a rule I have always implemented MAC address filtering on my routers. Each time I want to allow a new device to connect to my network I have to log into my router from a computer already allowed access to enter the new devices MAC. I wonder if this vulnerability is still present in this situation?
@Zack – MAC address filtering is a good security practice, but it should be thought of as a layer of defense, and not a terribly difficult one to circumvent at that. There are open source attack tools that let intruders sniff and spoof MAC addresses.
Ditto what Brian said. MAC addresses can be spoofed, and, contrary to popular belief, you do not have to be authenticated to a wireless access point to see the MAC addresses. You just have to be in range of the signal and be running the appropriate tools on the right kind of hardware. It doesn’t take a lot of money or knowledge to setup.
Even more importantly, MAC filtering doesn’t encrypt your traffic. It only keeps someone from authenticating to your access point. If they’re sitting in range with a sniffer then they can find out all kinds of juicy information.
On a similar note, hiding the SSID isn’t a fix either, because there are free tools available to sniff SSIDs out of the air. If it’s a signal being transmitted through the air then it’s not truly hidden. It might be “hidden” from the perspective of the default software on the OS, but that doesn’t mean it’s not detectable.
MAC address filtering is more of a tool for businesses imho. There are legitimate uses for it there (I.e., locking a switch port if the MAC address changes or if more than one MAC is detected on a port). When it comes to home users, using encryption is the only real method of security. It’s easier than MAC address filtering, and anyone who knows how to attempt to crack your wireless key is going to find it super easy to bypass MAC filtering.
The danger to the WPS flaw is that it makes pretty much any router running it vulnerable, regardless of the type of encryption, length of key, or other security measure in place. (I’m speaking for the home user of course, corporations with the right equipment have some tools in their bag of tricks that most people won’t have access to.)