A new service aims to be the Google search of underground Web sites, connecting buyers to a vast sea of shops that offer an array of dodgy goods and services, from stolen credit card numbers to identity information and anonymity tools.
A glut of data breaches and stolen card numbers has spawned dozens of stores that sell the information. The trouble is that each shop requires users to create accounts and sign in before they can search for cards.
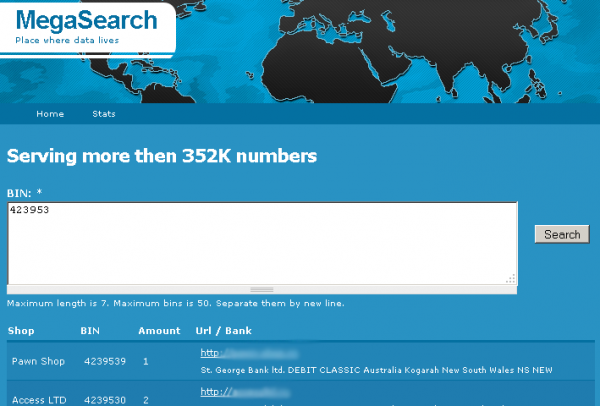
Enter MegaSearch.cc, which lets potential buyers discover which fraud shops hold the cards they’re looking for without having to first create accounts at each store. This free search engine aggregates data about compromised payment cards, and points searchers to various fraud shops selling them.
According to its creator, the search engine does not store the compromised card numbers or any information about the card holders. Instead, it works with card shop owners to index the first six digits of all compromised account numbers that are for sale. These six digits, also known the “Bank Identification Number” — or BIN — identify which bank issued the cards. Searching by BIN, MegaSearch users are given links to different fraud shops that are currently selling cards issued by the corresponding bank.
I first read about this offering in a blog post by RSA Fraud Action Research Labs. It didn’t take much time poking around a few hacker boards to find the brains behind MegaSearch pitching his idea to the owners of different fraud shops. He agreed to discuss his offering with me via instant message, using the search service as his screen name.
“I’m standing on a big startup that is going to be [referred to as] the ‘underground Google,'” MegaSearch told KrebsOnSecurity. “Many users spend a lot of time looking [through] shops, and I thought why not make that convenient?”
The service currently indexes compromised BINs from five different card shops, although he said several more shops are close to completing their integration with MegaSearch. He acknowledged garnering a small advertising fee for each relationship, although he repeatedly declined to discuss the particulars of those arrangements. But he said both sides benefit: stolen card data grows less reliable with age, and fraud shops that are indexed by MegaSearch stand a better chance of clearing their inventory faster, the hacker argues.
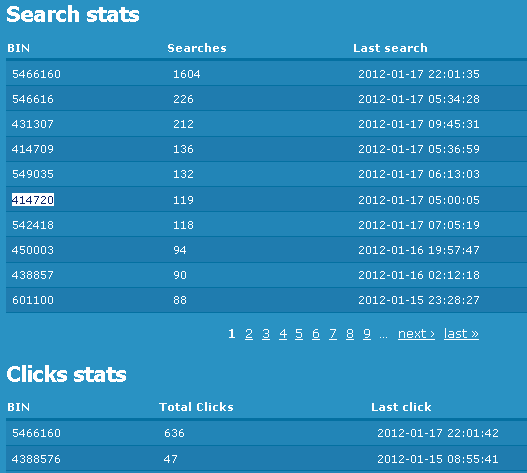 MegaSearch said that when his site first launched at the end of 2011 and began indexing the five card shops he’s now tracking, those shops had some 360,000 compromised accounts for sale, collectively. Since then, those shops have moved more than 200,000 cards. The search engine currently has indexed 352,000 stolen account numbers that are for sale right now in the underground.
MegaSearch said that when his site first launched at the end of 2011 and began indexing the five card shops he’s now tracking, those shops had some 360,000 compromised accounts for sale, collectively. Since then, those shops have moved more than 200,000 cards. The search engine currently has indexed 352,000 stolen account numbers that are for sale right now in the underground.
According to BIN search stats published on the site, Citibank cards are the most sought-after, followed by cards issued by FIA Card Services, Capital One and Chase.
In the coming weeks, he said, the site will include new features that index other types of criminal wares, including Social Security numbers and proxies — addresses of hacked PCs that paying clients can use as a relay to anonymize their online communications.
“I’m about to add more services to that site that would help newbie underground, including proxies, stolen identity information, etc.,” MegaSearch told me. “I’m also going to add a survey [to rate] the best shop.”
2011 has been called the Year of the Data Breach. If services like MegaSearch are indicative of a trend, 2012 may well become known as the year the criminal underground started getting a clue about how to better index and use all of its stolen data.




Ahh, but is it going dark at 8am EST?
looks like http://www.yourprivatevpn.com/
Well in theroy shouldnt it be easier for the CC companies security divisions to try and get these sites shut down saince all the info in one place….. Oh wait that would mean ICANN/ASN’s/Registars and upstream and down stream providers would have to do their jobs and actually put forth ad effort to shuttering these carder forums…my bad!
It’d be a lot smarter for the owner of MegaSearch to run this on the deep web, such as TOR, Freenet, or I2P; although TOR would be the better place at it’s the more popular deep web.
Mike,
It probably looks like that, because he stole the background image for the site you linked to.
Not really. If he/she hasnt got complete confidence in their host they can use various methods to anonymise themselves to do administration of the website such as TOR, private proxy purchased through the “underground” etc.. As can any visitors to the site. It’s simpler and more effective to do this.
TOR has is slow most of the time full stop (though granted this depends on what path the requested data is taking but this changes at least every 10 minutes).
Freenet has such high latency as to be almost unuseable for websites with many small elements and in any case can be unusable depending on popularity of those elements (how much they’re accessed) although if that’s all you got then that’s all you got. And then there’s the issue of how to interface with the online stores.
I2P is comparatively better (though still not what you’d call fast) but requires the client to act as a relay and has the stores issue as well (although I2P -> open net is possible afaik).
“If services like MegaBreach” – may be “MegaSearch” you meant?
My question is how do these people do transactions? Obviously you wouldn’t trust someone buying stolen credit card numbers to give you a real number, so do they use Paypal? Direct bank transfers? Either of those will leave some kind of trail.
Just wondering.
@Miz – Most of the time, these sites accept payment only through comparably unregulated virtual currencies like WebMoney and Liberty Reserve.
Also they happen to use currencies like BitCoins that are p2p and decentralized
While I agree Bitcoin would be idle for this, the size of the economy right now just doesn’t support its widespread use, criminal or otherwise.
Do you have a link to a site that accepts Bitcoin as payment for these types of services? I’ve seen a couple of items for sale here and there, but no one that has used it as a primary means of payment.
Is this Kimble again? He likes the word “mega,” after all, and seems to have a knack for ripping stupid investors off.
This has nothing to do with Kimble, but your comment was ominous (unless you knew about Kim’s arrest already) 🙂
This misfit is not going to last long with his current activities. He is on the radar screen now and the next step is the graybar extradition hotel.
Can someone please start a countdown clock on how long it takes Inspector Cluesoe from Interpol (in Lyon, France) to connect the dots and introduce him the charade that will now occur?
You just did. Countdown started at January 19, 2012 at 9:37 am.
Now, can someone please determine what the initial countdown value should be, in seconds?
That didn’t last long.
It looks like megasearch.cc now resolves to the same IPv4 address as krebsonsecurity.com.
Wow! You’re right. Someone has a sense of humor.
bailiwick megasearch.cc.
count 1
first seen 2012-01-19 13:40:07 -0000
last seen 2012-01-19 13:40:07 -0000
megasearch.cc. A 94.228.133.163
bailiwick krebsonsecurity.com.
count 1101431
first seen 2010-06-24 06:24:11 -0000
last seen 2012-01-19 13:00:23 -0000
krebsonsecurity.com. A 94.228.133.163
And now they resolve to localhost 🙂
#host megasearch.cc
megasearch.cc has address 127.0.0.1
Brian, they are just showing you the love for your work…lol.
Tor Mail works well it’s more secure than SSL:
http://jhiwjjlqpyawmpjx.onion/
In order to load the site you need Tor installed, but that is trivial. It’s not related to the official Tor Project.
Quick signup, free, no strings.
You can visit Tormail.net without Tor to view more information.
* Tor: https://www.torproject.org/
If you use it please post here to this thread with your feelings.
I’m wondering if the figures claimed by Megasearch and quoted by Brian could be true: 200 000 stolen cards sold collectively by the 5 online shops through Megasearch since the end of 2011 seems to me an extremely large figure. I imagine once they are bought, the carders will use them to commit fraud (or attempt to, but find the card already blocked, or fail the transaction as the CC company flags the transaction as suspicious). Even if one fifth of those stolen cards result in a successful fraudulent transaction, it still makes my head spin on the level of fraud committed.
It’s really not surprising (the amount of cards). “bases” can run anywhere from 500 to 30k cards (there have been bigger breaches, but it’s rarer although not unheard of) depending on the size of the site infiltrated (at least what I’ve come across in research and “lurking” on these types of sites in order to hopefully develop active strategies to counter many types of credit card and bank related fraud for my consulting business).
oogqdn, hooked on phonics pre-k, OkOLZfg.