KrebsOnSecurity has obtained an exclusive look inside the back-end operations of the recently-destroyed Grum spam botnet. It appears that this crime machine was larger and more complex than many experts had imagined. It also looks like my previous research into the identity of the Grum botmaster was right on target.
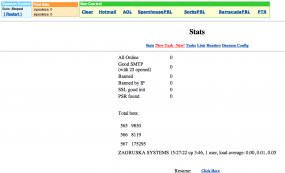
The “Stats” page from a Grum botnet control panel show more than 193,000 systems were infected with the malware.
A source in the ISP community who asked to remain anonymous shared a copy of a Web server installation that was used as a controller for the Grum botnet. That controller contained several years’ worth of data on the botnet’s operations, as well as detailed stats on the spam machine’s size just prior to its takedown.
At the time of Grum’s demise in mid-July 2012, it was responsible for sending roughly one in every six spams delivered worldwide, and capable of blasting 18 billion spam emails per day. Anti-spam activists at Spamhaus.org estimated that there were about 136,000 Internet addresses seen sending spam for Grum.
But according to the database maintained on this Grum control server prior to its disconnection in mid-July, more than 193,000 systems were infected with one of three versions of the Grum code, malware that turned host systems into spam-spewing zombies. The system seems to have kept track of infected machines not by Internet address but with a unique identifier for each PC, although it’s not immediately clear how the Grum botnet system derived or verified those identifying fingerprints.
The Web interface used to control the botnet was called “Zagruska Systems,” (“zagruska” is a transliteration of the Russian word “загрузка,” which means “download”). The HTML code on the server includes the message “Spam Service Coded by -= ( Spiderman).”
The password used to administer the botnet’s Web-based interface was “a28fe103a93d6705d1ce6720dbeb5779”; that’s an MD5 hash of the password “megerasss”. Interestingly, this master password contains the name Gera, which I determined in an earlier investigative story was the nickname used by the Grum botmaster. The name Gera also is used as a title for one of several classes of forged email headers that the botnet had available to send junk mail; other titles for falsified header types included the names “Chase,” “eBay” and “Wachovia,” suggesting a possible phishing angle.
This Grum control server also hosted some unbelievably large email address lists — more than 350 GB worth in all. There were dozens of separate email address lists on the Grum control server, many containing between 20 million and 60 million email addresses each. I was unable to determine how many unique or active email addresses were contained in these files, but a quick tally of 60 different address list files found in one directory on the server showed that they contained more than 2.3 billion addresses.
Most of the junk mail that Grum sent was for ads promoting rogue Internet pharmacies and replica watches, although there are indications that the botnet was at some point in 2011 used to distribute malware disguised as a DHL shipping notification.
Further poking around this control server revealed that it contained the customer information for more than 1.3 million orders placed at rogue Internet pharmacies between Feb. 2006 and March 2010. The order information for the online pill shops was in a folder on the system called “Rx-Partners,” suggesting they were records belonging to the pharmacy spam affiliate program by the same name. The database includes order numbers, dates, the type of drug purchased, strength, quantity, price, customer country, and email address, among other information. I’ll have more details on this aspect of the Grum data trove in a future post.




Stupid guy to use such a weak password for such a powerful system…
projects open and never die lol
https://s19.postimage.org/9q5b82sch/grum1.jpg
https://s19.postimage.org/9enuvbbwh/grum2.jpg
https://s19.postimage.org/lht6ivmyp/GUI.jpg
see and know , research lost time!
Lol at the Yoda evals (if true is…) 😉
Nice! Hey, that’s my site’s IP address at Prolexic! Cool.
Although, this would not be the first time, I guess.
From this piece:
http://krebsonsecurity.com/2012/07/top-spam-botnet-grum-unplugged/
Very soon after my investigative piece on Grum was published, KrebsOnSecurity.com was the target of a rather large distributed denial of service (DDoS) attack. I’ve recently learned that the attack was launched by the Grum botnet, suggesting that the findings were a little too close to home for the Grum botmaster(s).
Brett Stone-Gross, a senior security researcher for Atlanta-based Dell SecureWorks, analyzed a copy of the Grum malware from that time and found that it was instructing all infected systems to visit 94.228.133.163 (the IP address for krebsonsecurity.com). The nonexistent filename that the Grum bots were told to fetch from my site was “fuckingyou^^/9590899.php”.
fantastic blog.. thanks
Please fix mistake in your post.
‘Zagruska Systems’ in this case means ‘System load’,’System perfomance’
‘Загрузка’ can be translated as ‘download’ and also can be translated as ‘load’
Wow… the kind of news you won’t find anywhere else!
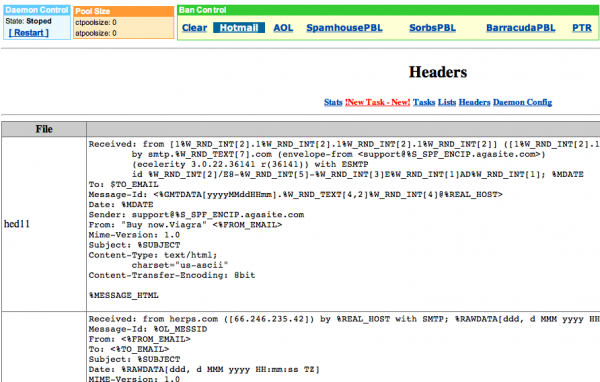
I’m curious about the “Ban Control” feature which has SpamhousePBL (sic) and a few others listed. What happens when those links are clicked? I could guess, but guessing isn’t worth much.
I tried to avoid getting too clicky with the buttons. But now that you mention it, hey I wonder what this button here do
It probably just checks if a domain/ip has been blacklisted.
Maybe it replaces such blacklisted resources as backup ones as well.
“one in every six spams delivered worldwide, and capable of blasting 18 billion spam emails per day.”
“large email address lists — more than 350 GB”
“more than 2.3 billion addresses”
They/He wasn’t doing things by halves was he ROFL 😉
I make my daily bread through internet marketing and it’s pretty much an open secret that many supposedly reputable affiliate partners, both networks and vendors themselves, will tolerate non-compliant email traffic. Often with the full knowledge and cooperation of the affilate manager.
I’m not talking only fly-by-night operators either but rather some of the largest names in the business. Traffic that converts is a win/win for both parties are making money so you know … it happens. It should be noted that AFAIK most partners will NOT be happy with email campaigns that have no opt-out (even if they will allow unsolicited email to generate leads) and expect suppression lists to be applied and adhered to.
Most marketers operating along these guidelines will hire several VPS servers in Eastern EU, Asia and the Middle East that will ignore complaints – at least for a time – and use corporate solutions such as Interspire Email Marketer for example.
They also use fairly well known tactics to minimise honeypots and people marking addresses as spam such as sending out a blast of innocent enough messages. “Hi, I’ll be in town we should meet – Bob” or the like.
Anyhow, the point of this rambling (sorry) post is it seems to be far more profitable to market legitimate products this way – dating sites leads that involve a free signup for example – than counterfeit pills and Rolexes if you look at the numbers of messages being sent. I mean these small time blackhatters are not sending hundreds of thousands of messages per day let alone *billions*(!) and yet a few grand a day isn’t uncommon.
Why do you think these criminals only spam pills mainly? They just can’t being themselves to sell anything legal?
.oO(Some servants do serve more than one master…)
Fantastic article!
(Can you believe 1.3 million suckers actually ordered from those “pharmacies”?)
I can. In some of the biggest prosecutions of career pill spammers, notably that of Chris “Rizler” Smith, the affiliates attracted repeat business from people who were clearly addicted to things like Oxycontin or other highly addictive painkillers. These were all people who had been cut off from any further prescriptions, or who had no insurance, who were desperate to gain access to more of these pills.
These scumbags have a habit of targeting these kinds of people, and further they also attract people who are un-insurable under the US system.
If US health insurance were to be less restrictive than it is now (pre-existing conditions, etc.), pill spammers would see a significant drop in business. Residents of the UK and Canada, which have socialized medicine, rarely have a need to purchase these kinds of pills (although yes, doctors will still restrict how many refills on a prescription will be available to a patient.)
SiL
Krebs, you are becoming a real publicity wh##re. 🙂 You may want to validate/confirm your conclusions next time.
“Zagruzka Systems” here means “System Load”.
Megera has nothing to do with Gera, it most likeky refers to Megaera
http://en.wikipedia.org/wiki/Megaera
hah! you know it’s close to home when the nit-picking starts. “download” versus “load?” seriously? and yes i’m sure your right that this spamer has such a deep grasp of greek mythology! why then was his password not megaera? do you know the guy? are you speaking from experience? tell us more plz. 🙂