An increasing number of services offered in the cybercrime underground allow miscreants to purchase access to hacked computers at specific organizations. For just a few dollars, these services offer the ability to buy your way inside of Fortune 500 company networks.
 The service I examined for this post currently is renting access to nearly 17,000 computers worldwide, although almost 300,000 compromised systems have passed through this service since its inception in early 2010. All of the machines for sale have been set up by their legitimate owners to accept incoming connections via the Internet, using the Remote Desktop Protocol (RDP), a service built into Microsoft Windows machines that gives the user graphical access to the host PC’s desktop. Businesses often turn on RDP for server and desktop systems that they wish to use remotely, but if they do so using a username and password that is easily guessed, those systems will soon wind up for sale on services like this one.
The service I examined for this post currently is renting access to nearly 17,000 computers worldwide, although almost 300,000 compromised systems have passed through this service since its inception in early 2010. All of the machines for sale have been set up by their legitimate owners to accept incoming connections via the Internet, using the Remote Desktop Protocol (RDP), a service built into Microsoft Windows machines that gives the user graphical access to the host PC’s desktop. Businesses often turn on RDP for server and desktop systems that they wish to use remotely, but if they do so using a username and password that is easily guessed, those systems will soon wind up for sale on services like this one.
Pitching its wares with the slogan, “The whole world in one service,” Dedicatexpress.com advertises hacked RDP servers on several cybercrime forums. Access is granted to new customers who contact the service’s owner via instant message and pay a $20 registration fee via WebMoney, a virtual currency. The price of any hacked server is calculated based on several qualities, including the speed of its processor and the number of processor cores, the machine’s download and upload speeds, and the length of time that the hacked RDP server has been continuously available online (its “uptime”).
Though it is not marketed this way, the service allows users to search for hacked RDP servers by entering an Internet address range, an option that comes in handy if you are looking for computers inside of specific organizations. For instance, I relied on a list of the IP address ranges assigned to the companies in the current Fortune 500 listing (special thanks to online banking security vendor Greenway Solutions for their help on this front).
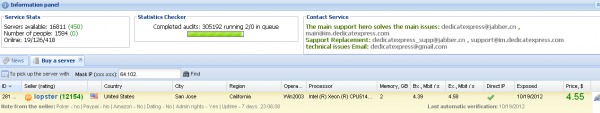
I made it about halfway through the list of companies in the Fortune 100 with names beginning in “C” when I found a hit: A hacked RDP server at Internet address space assigned to networking giant Cisco Systems Inc. The machine was a Windows Server 2003 system in San Jose, Calif., being sold for $4.55 (see screenshot below). You’ll never guess the credentials assigned to this box: Username: “Cisco,”; password: “Cisco”. Small wonder that it was available for sale via this service. A contact at Cisco’s security team confirmed that the hacked RDP server was inside of Cisco’s network; the source said that it was a “bad lab machine,” but declined to offer more details.
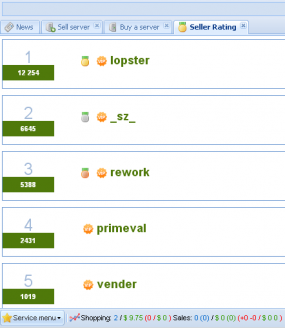
Dedicatexpress works directly with hackers who earn commissions for selling the RDP machines to the service (see screenshot below). The number beside each seller’s name indicates how many servers he has sold to dedicatexpress.com. The service says it will not buy RDP servers from Russia, probably because its proprietors are from that country and do not wish to antagonize Russian law enforcement officials (the site is in Russian but the images pictured here are from Google-translated versions of the pages).
Sellers can specify how the servers that they contribute may be used, and very often state that their RDP servers may not be used for particular activities, such as online gambling, PayPal or dating scams. Buyers may also be limited to running regular user accounts on the hacked systems, barring them from installing many types of software (the Cisco server sold above granted the buyer administrative rights).
Before a server can be purchased, the service prompts buyers to use its built-in system for checking the reputation of the hacked RDP installation. I ran a check on the Cisco box and found that it had already been blacklisted by 10 out of 15 popular services that track malicious activity online, such as spam and malware hosting. Not to worry, though: The service’s operators assure buyers that “if you have any problems with the remote server you have just purchased, you will always be able to file a ticket with technical support and we will be happy to assist you.”




Love it.
I believe many of these servers are honepots 😉
[at least this is the way I would setup them working as LE]
of course honeypots (no honepots … sorry)
this is managed services 101. the bad guys are innovating their business models faster than we are innovating our defences… this has to change
as you say ” the service allows users to search for hacked RDP servers by entering an Internet address range” how can i use this service? how to check my ip wether in there list?
Andrey, that is an option that might come in handy. But as I understand, you should also be able to search using the name of your company. If you really want to use numbers you can check the block of IP that is assigned to your company.
re: “You’ll never guess the credentials assigned to this box: Username: “Cisco,”; password: “Cisco”. Small wonder that it was available for sale via this service. ”
Brian, it seems to me that a cracker, having administrative access to this machine, added the user “Cisco,” with password “Cisco.”
Please tell me I’m not mistaken.
Hi Dan. It’s certainly possible. However, others that I stumbled across almost by accident did not have credentials that matched the name of the company network or any company name for that matter. For example, not long after I discovered the Cisco box, I skipped ahead and took a gander at Microsoft’s IP ranges; I found four boxes in this range: 157.56.xxx.xxx (according to some meager searching online, it looks like this range is part of Microsoft’s managed hosting network).
Unlikely. If the hacker wanted to give themselves a back door, they probably would do so with a better password, to keep other hackers out. Having worked in a number of corporations and having seen this type of issue repeatedly, I believe it far more likely that this was the result of internal IT.
cisco/cisco is how a lot of Cisco devices ship – I wouldn’t be surprised (well, abhorred, but not surprised) if those are authentic.
The real shocker to me is how cheap these services are. Same with the article Brian posted a couple weeks ago on purchasing SSNs and DoBs. I would have imagined access to these machines would cost 3,4, or 5 figures, not 5 dollars.
Hi Brian,
Is it possible for you to publish the list of companies available on this service, so those of us without the means to enter this site can check if our employer’s computers have been compromised?
Hi Leonard, I thought about doing that, but it doesn’t seem right to call them out without giving them a chance to fix it first.
Also, it took way more time than I thought it would just to get to the Cisco example. I’m positive there are plenty of other examples, but I don’t really have the time right now, sorry.
like Leonard say,i want to know whether I’m in the vulnerable list.how can I contact you get the company list,or directly check by the Dedicatexpress.com service? hopeful get your reply.
I love your blog and its nice to know that we have a white hat like you out there, Keep up the great work.
Just FYI, arstechnica picked up the story, it’s showing up on their home page:
http://arstechnica.com/security/2012/10/cisco-machine-gets-listed-by-blackhat-org-that-rents-out-hacked-pcs/
I agree with your statements above, the cisco credentials were most likely set by admins who have not yet “experienced” a compromise.
Well done Brian.
Question: are there any good security tools available that would allow me to scan for such vulnerabilities inside my network?
Hey Brian, I just found a bug on your comments section: I can’t seem to give my own comment a thumbs-up vote.
That means you are reading my blog in the https:// version. I’m not sure why so many people are doing that (maybe some plugin that forces https when possible), but you’ve discovered a source of frustration for me: The voting plugin doesn’t support https. I’ve been on the developer about this, but so far no response.
Actually, I was just able to give your reply a thumbs-up, so I think the problem may not be the voting plug-in, it may be my ego. Or my dry sense of humor needs a reboot.
As sometimes happens when I write about these services, the service is no longer available at its previous URL.
And why are we patting ourselves on the back?
Because patting ourselves on the front is Just Wrong, and leads to night sweats and hairy palms.
Who’s patting themselves on the back? Just making a statement about the service. Obviously, services like these are more useful to some when they are online; the RDP installs are still hacked, whether you know the address of a service that’s selling them or not.
I think 67GTV was referring to the fact that tarzanthejunglelover was trying to give his/her own comment a thumbs up.
Oh. If that’s the case, then pardon me, 67GTV! 🙂
Nice ‘pull’ wiredog!
LOL Brian! My comment was indeed directed towards tarzanthejunglelover wanting to Like his own post. Rest assured tjl, at least you cannot Dislike your own post either. 😉
Hey, if you are on microsoft, use Microsoft Security Baseline Analyzer and it will list out all the admin accounts on your system.
If you want to pay, use LanGuard from GFI or Nessus if you want to get really deep
Off-topic, but is there a new botnet online? My spam volume, across several inboxes, has gone from maybe 20/day to over 20/hour just in the past 2 or 3 days.
As I understand statistics ‘Cutwail 1’ and ‘Lethic’ are pumping up volumes. (According to the 34.2% ‘Other Sources’ there may be something under the radar, but that decreased the last weeks as far as I remember…)
https://www.trustwave.com/support/labs/spam_statistics.asp
And now it’s down to 50/day.
BrianKrebs question?
You yourself are sitting on the forum or you verified.ms someone merges information from the forum ?
Да сам он черт ебливый маниторит вериф, давно пора найти и пизды дать
Hmmm… Something about petting other people’s cat?? 😀
Check out seculert
1) the compromised server was in a lab, which means it might not have been under IT policy. Engineers might have fought for the right to be excluded from firewalling policies reserved for corporate LANS. The ever popular “they’re engineers and they need access without policies to do their jobs” thing.
2) Engineers / Telco noc flunkies at my former employer were fairly infamous for stupid moves such as these. One engineer got his lab linux server rooted in 26 tries by the remote russian malware bot. His excuse: “I thought the lab was firewalled!” No. It. Wasnt. engineers argued for it to be open. Then he got Pwned. So we called him my lil pwny from that point on.
3) Cisco/Cisco is used in lots of default contexts. Entirely believable on that front.
Its always possible its a honeynet. But in a testing lab, I’d easily believe security unconscious employees or security hubris on the part of technical employees is also in play.
Brain, Your blog post were always entertaining, fun to real, and educational!
Most of the “fortune 500” servers that were sold at that shop are simply testing servers, honeypots, or servers that people simply have no use of and just play with it – also, they probably have been sold/scanned/obtained by dozen other people.
All servers that are being sold at that store are obtained by scanning IP ranges, and trying default passwords for specific ip that runs windows, and remote desktop. Such as admin/admin, admin/password, sysadmin/secret…cisco/cisco.. etc.
“Fortune 500” Systems are being hacked everyday, but not necessary it means, that it can do any damage, to the corporation, or infrasture itself.
Most of the systems sold there are already compromised multiple times, and multiple people have access to it, runs various malicious software, torrents, scams on it.
As article mentioned “I ran a check on the Cisco box and found that it had already been blacklisted by 10 out of 15 popular services that track malicious activity online, such as spam and malware hosting.” — This just simply means, that box is compromised by multiple people, some are using server for bad things, other guys are selling it.
Brain, Here is something that should be interesting – https://srvc.iframeservice.net:666/
Hi Tadas. Thanks for reading and for your comment. I’m assuming you’re giving us a hunch as opposed to stating this as fact, unless you know something I don’t about this service (which appears to have vanished for the time being).
As to the iframeservice, I wrote about it a few months back .
http://krebsonsecurity.com/2012/05/service-automates-boobytrapping-of-hacked-sites/
Really mental that there are so many computers for hire although Tadas P’s comment is interesting reading. We’re doing more and more security audits and risk assessments for smaller companies and this caught my eye while reading another article, I’m pretty shocked.
they are selling RDP, which they are using for geo proximity to wherever they are credit or bank frauding from, they are most likely not interested in what’s on the system only to use it’s browser fingerprint to steal from somewhere else undetected