A hacking group calling itself the Syrian Electronic Army (SEA) has been getting an unusual amount of press lately, most recently after hijacking the Web sites of The New York Times and The Washington Post, among others. But surprisingly little light has been shed on the individuals behind these headline-grabbing attacks. Beginning today, I’ll be taking a closer look at this organization, starting with one of the group’s core architects.
Earlier this year I reported that — in apparent observation of international trade sanctions against Syria — Network Solutions LLC. and its parent firm Web.com had seized hundreds of domains belonging to various Syrian entities. Among the domains caught in that action were several sites belonging to the SEA.
At the time, the SEA had a majority of its sites hosted at Internet addresses belonging to the Syrian Computer Society, an organization considered to have been a precursor to the SEA and one that was previously headed by Syrian President Bashar al-Assad. Following the Web.com domain seizures, the SEA was forced to find new homes for their domains. Soon enough, the group moved its domains syrianelectronicarmy.com and sea.sy to a host in Russia (no doubt adding further chill to already frigid US-Russia relations vis-a-vis Syria).
Sometime during that transition period, the SEA’s main Web site got hacked. As in…completely owned. According to one confidential source, the attacker(s) gained access to the virtual servers that hosted the SEA’s site and downloaded the entire user database for sea.sy and syrianelectronicarmy.com. Shockingly (or perhaps less so for many security researchers who’ve dismissed the SEA as mostly a group of tenacious but relatively unskilled hackers), many of the top members re-used the passwords they picked for their sea.sy accounts at their Hotmail, MSN and Outlook email accounts.
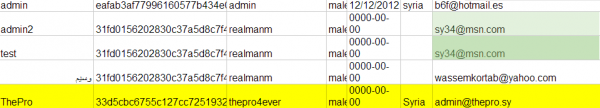
A snippet from the hacked database from syrianelectronicarmy.com. In the third column are plain-text passwords.
In nearly any dump of a Web site user database, it’s generally safe to assume that the first few users listed are founders and administrators of the site. In the hacked sea.sy database, for example, we can see that the first two usernames in the table are “admin” and “admin2.” Admin2’s email address is listed as sy34@msn.com. The last entry in the database is April 19, 2013, just a few days after Web.com began seizing domain names in its stable with the “.sy” designation.
A Google search on that email address reveals its ties to the SEA, and shows that the account was in 2010 tied to a now-abandoned hackforums.net user named “SyRiAn_34G13” (leet-speak for “Syrian Eagle”). A reverse WHOIS search at domaintools.com on the sy34@msn.com address shows that it was used in Feb. 2011 to register a site called codepassion.net.
Codepassion.net is no longer active (perhaps because it was hacked and defaced in May 2012 by other script kiddies), but thanks to the Wayback Machine at the indispensable Internet Archive, we can see the site lists as its creator a 23-year-old “virtuoso web designer” named Mohammed from Damascus, Syria. Mohammed says he is a senior front end developer at a firm in Damascus called Flex Solutions. Mohammed reveals that his last name is “Osman” when he links to his Facebook and DeviantART accounts, as well as his Gmail address (osmancode@gmail.com). That same Gmail account is also used for another account in the sea.sy database: يوزر – which Google translates to “Yoezer” “User” and used the password “963100”.
Osman’s DeviantART account — “medothelost” — says in Arabic that he is a member of the Free Syrian National Rally, a founding member of the Syrian Civil Youth Movement, and a member of the Syrian Social Nationalist Party. Another account named “medothelost” in the sea.sy database uses the email address medo_sy@hotmail.com and the password “963100.”
Looks like since working at Flex Solutions, Osman struck out on his own, and changed his identity slightly: Running another reverse WHOIS record search at domaintools.com shows that osmancode@gmail.com was used to register the site mohamadstudio.com (I guess mohamMEdstudio.com was already taken?). Anyway, Osman’s Mohamad Time Line tells readers more about this guy, who says he recently moved to Turkey. He currently lists his name as Mohamad Abd AlKarem. Around the same time that Mohammed Osman stopped tweeting at @osmancode (April 27, 2013), @mohamadabdalkarem started up. Osman/AlKarem could not be immediately reached for comment.
A short time ago, Vice.com ruined my scheming and published information on the next guy I’d planned to profile in this series — the individual listed as registered user number 4 in the database screenshot above: “ThePro.” See their story here for more on him. Thankfully, there is enough here to keep me busy for a while yet.
Update, Aug. 29, 2:23 p.m. ET: Several reporters contacted me to say they’d heard from the person at osmancode@gmail.com, who claimed he was not a member of SEA and was never contacted by me; in fact, I sent an email to this same address yesterday requesting an interview. I also never received a reply from the Twitter account tied to Mohamad Abd AlKarem). A few minutes ago, Mr. Osman replied to my email, stating that he was not part of the SEA, and furthermore if he was would he have been so careless with his information? He also said Mohamad Abd AlKarem is not him but his client. Here is his reply:
“Dear Sir
I am not a member in “Syrian Electronic Army”, and if I were, would I mention where I work, post my personal photo as declaring my political views?
Dear Sir, Would I, if being a SEA member, publish where I live and my real name, would you do that?
Actually I do believe that the most stupid man on earth wouldn’t do it, then what about someone to be considered one the best hackers?
Thus dear, you can verify that I am not a SEA member, not as well their leader, just as you have mentioned in one of your articles, depending on odd information that has – at any rate- any relation to a matter of fact.
By the way, Mr. Muhammad Abed Al-Karim is my client, and I have made reservation as any other regular common customer.”
Update, Aug. 30, 12:14 p.m.: Mashable published a story after interviewing AlKarem, which quotes AlKarem as saying he is not Osman; AlKarem told Mashable he knows Osman through the art website DeviantART, but the two have never met in real life. AlKarem told the publication that while Osman had developed some graphics for the SEA, “I don’t think he’s a member of them.” Meanwhile, Motherboard ran a piece Wednesday claiming to have identified a different member of the SEA; that publication featured a Tweet from one of SEA’s leaders “ViCt0r” who last year gave a shout out to fellow SEA members, including a Mohammed Othman.
Further supporting Osman’s statement that AlKarem is just a client are domain hosting records for mohamadstudio.com, which list Osman’s employer FlexSolutions as the technical contact. Also Osman’s personal site — osmancode[dot]com — includes a picture of him that appears different from the one on AlKarem’s site. Based on the evidence available, it seems likely that AlKarem and Osman are two different people. The image from AlKarem’s site has been removed from this story.




What kind of ‘hacker’ leaves plain text passwords in their own site database? And then uses those same simple passwords on major email host accounts. Answer: None. You don’t have a real hacker here–you might have someone trying to become a hacker. But from what it looks like you have a little boy or girl playing games.
“What kind of ‘hacker’ leaves plain text passwords in their own site database?”
I think that these are cracked passwords. What you see in the second column is the password hash that would have been in the database. The discovered passwords are the result of cracking the hash with something like hashcat or John the Ripper. Though it would be nice if the article were more clear on that.
We should also keep in mind that a couple of years ago it was discovered that the the email account used by Assad’s staff had a password of “12345”. (Though I don’t know what kind of combination he has on his luggage.) So it looks like hackers aligned with the government are not particularly sophisticated. Contrast with Iran, which has been quite successful in this domain. Perhaps the IRI can offer assistance and training to Syria.
According to my source, this is an unprocessed database, meaning the passwords were stored in plaintext. As you can see there is also an MD5 hash of each password. But I agree it’s unusual to see this side by side.
I did double check many of these passwords with the MD5s. When I went through and submitted the first 100 MD5 hashes in the database to cmd5.org, about 70 percent came back within a few seconds as cracked.
Remember many, if not all, CRAM-MD5 implementations require the password stored in a readable format by the server.
They may have thought CRAM-MD5 was a better authentication option than PLAIN when logging into their email, and felt their database was sufficiently secured.
The simplest explanation…
Osman’s claim that he is not the same guy as Abd AlKarem and that the latter is just a client makes little sense. If Abd AlKarem — who we know from his site is a Web designer — really was a different guy than Osman, why would he hire a competing Web designer to design something and register sites on his behalf. That just seems very unlikely.
People contract work out to other people in their fields all the time, it’s called ‘out-sourcing’.
I think it’s fake article, those people are not a part of SEA, even the database looks fake
That’s not the database, per se. It’s a paste from the database into a spreadsheet.
Really funny, and do you believe that??!!! LOL
I won’t believe it until I see the original punchcards the database was kept on.
Yes, I do. I was the one who pasted it 🙂
Whole thing smells of a cia or fbi fish attempt to me. We’ll see who’s dumb enough to bite.
I have to agree with this comment. The content, timing and the too obvious bread crumbs make it very convenient for American interests. I think it’s a false-flag operation.
False flags? You assume these hackers are off the grid, they’re a bunch of young kids… much like the age of the rebel fighters, except they use a computer and not a gun, similarly they’re not professionals either…
Good post, not too sure on leaking names in a crisis like this – if you’re wrong this could be some poor guy getting tortured for nothing, alot of copy cats do exist… not that I am saying this is a copy cat case, it looks too unlikely from the other snippets i’ve seen.
The simplicity of that password and the fact that the guy contaminated his accounts by mixing his personal and “other” accounts is almost unbelievable, considering the press these guys have garnered.
This simply demonstrates the guy is an idiot, or it’s subterfuge. It’s too neat, doesn’t seem right.
Why bother when the internet is anonymous.
Wait … it is anonymous … right?
And, so the supposed dumps on pastebin from the name.com breach containing mysql-sha1 hashes for several users including one “deviantart” are thus connected to the SEA. Interesting…
Do you think they’re really from Syria? It sounds like it from the organizations he belongs to.
20-year CIA employee “Tim Osman” (Osama Bin Laden) died of natural causes in December, 2001.
just a little correction: “يوزر” in Arabic is a transliteration for “User” . The word’s phonetics are literally “User”. The translation of “User” to Arabic is “المستخدم”
Any significance to the Charles Tillman jersey?
http://store.chicagobears.com/Charles-Tillman-33-Nike-Game-Day-Jersey.aspx
Yes, just ask Plaxico Burress.
Who knows? There is no shortage of idiots in the hacker community. Nor is there a shortage of “false flag” operations by Israel… Or for that matter, the Syrian insurgents…
Besides, who’s going to arrest him for hacking the New York Times? Assad? Not likely.
Whoever these guys are, they’d better keep their heads down when the US and NATO and Israel bombs Syria into the Stone Age. (And no, these won’t be “surgical strikes not intended for regime change” any more than Libya was…)
I have to agree with some of the comments above. Seems a bit too convenient that all of this fits and ties back together.
I’m no hacker, but even I know that it’s good to hide your web registration and keep your address/name confidential. Those anonymity services come nearly free of charge these days, and we’re supposed to believe that these bad-ass hackers that pawned everyone from MelbourneIT, NYT and even The Onion made such a ‘rookie’ mistake?
Also plain-text passwords, and even then what sort of hacker uses ‘realmanm’ as a password?
Thats cos its all BS .Americans are full of it this days ,you cant believe a word they saying .
Propaganda machine at its best .
Noted but then are you living in a country that has buckleys chance of a successful conviction originating from the countries you are attacking.
And are you operating in a manner which aids or is at least aligned with the interests of the powers that be in your country?
I wouldn’t exactly consider redirecting NY Times Traffic for a few minutes the cutting-edge of hacking. Its not quite the most complex thing to do.
If what the author is saying is true then virtually anyone can hack NYT, isn’t it?
I understand the frustration of american’s technical might being challenged by “Syrians” but that doesn’t mean to spread BS …
One more thing, if u r that smart, can u register twitter.com as ur own domain like the SEA did? Yeah, didn’t think so!
Cheers
It’s not that difficult actually, and involves little technical proficiency.
Anyone with little concern for consequences or sheltered in a country that doesn’t formally have any agreements in place with said target for extradition or a place that doesn’t prosecute “hacking” can pull off social engineering or spear phishing attacks to gain the access required with a little practice (enough practice and you are bound to succeed somewhere). Combine that with a bit of technical reading and tinkering/experience (also known as hacking, the old fashioned way) and you’re set!
We don’t yet know if this was their intial target to use towards compromising twitter and NYT, etc., or if this was one of multiple weak links in a chain that they moved on to, so it’s hard to judge their tenacity.
Given the above and knowing Brian’s history, it’s hard to believe he would be so easily duped, but even the best of us makes mistakes, and that applies to the SEA as well – it happens (see previous story of clown who thought he was safe but left his backups available for inspection – oops!).
It happened last night, if you were online at the time you could watch it all happening in real time
I wouldn’t exactly consider redirecting NY Times Traffic for a few minutes the cutting-edge of hacking. Its not quite the most complex thing to do.
(The person above me posted a much better response)
I guess mohamMEdstudio.com was already taken?
Mohamad is a valid transliteration. Arabic, Cyrillic, and Hebrew (and others I suppose) don’t have exact mappings to English spelling.
Maybe you missed the part right before that where he had already spelled it “Mohammed” on his personal site.
He currently lists his name as Mohamad Abd AlKarem
I hope people realize that life isn’t like a TV show or movie. There’s a theme running through the comments to this post that suggest the evidence presented is “too convenient” and “too neat.” IRL the world is run by flawed humans who make mistakes constantly. The real reason there are no real comic-book-style “super-villains” in the world is because anyone brilliant enough to be one is also smart enough to know that the world is far too flawed and random for even the most meticulously planned attempt at a power grab to work. Only idiots think that fate or God or whomever will smile on them long enough to get away with it. So they go for it and sometimes immediately get caught. It may be awfully convenient that all this intel links everything together AND that this guy made these blaringly stupid mistakes, but reality doesn’t have a writer that has done several drafts to make things more believable. Besides, you’d have to be pretty stupid to think you could get away with hacking some of the biggest websites out there. I just wish he’d taken down Facebook. >_<
Oh and, side note, "Tim Osman" was the CIA codename for Osama bin Laden. Don't know of that means anything, but I'm automatically suspicious of anyone using that last name.
Interesting to see how many comments there are from people thinking that these guys are too elite to have made such rookie mistakes. In my experience, however, even some of the most skilled hackers are quite sloppy with their identity information, and given enough time will leak plenty of clues about their origins and identities.
Any doubts? Check some of the stories that have led back to the world’s biggest spammers, or Russian malware coders.
http://krebsonsecurity.com/category/breadcrumbs/
Occams Razer comes to mind as well…
I think you are trying to collect some attention…. so if you published their identity you think that they will stop? if you think then you are so dumb.
If I think then I am dumb? I think I am not the one who sounds dumb.
As I said in the opening paragraph to this story, the purpose of this piece (and others to come) is to look at clues pointing to the identities of those behind the SEA, since surprisingly little has been written about this aspect of the SEA so far.
Seems you are going in the right direction sir… Can’t wait for the follow-up.
Do you think the SEA is actually launching the attacks or are they seeking out former Anonymous members (and break aways groups) who now whoring out their services? These attacks and targets seem all too familiar and use Anonymous like tools and tactics.
As anonymous has gotten quiet these mid east hacker collectives have gotten active. Maybe it’s an odd coincidence. Then again, there have been a lot of Guy Fawkes masks appearing at Islamic uprisings.
Its far more likely they took part in Anonymous activities, then branched out on their own. It explains why they seem to have been mired at the technical competence of using LOIC and similar script kiddy tools.
Sounds like other articles where you’ve stepped on toes. The comments section lights up with apologists and attackers. Seems you may have poked them in the eye yet again.
Keep it up Brian. You are correct about the sloppiness of many run of the mills and wanna be’s. 1337’s are different, these guys are NOT!
Well, even if nobody else is saying it, I think this is a great article. I have been on your end of the “Finding Intel without actual Intel” game and you hit some pretty good pay dirt here Brian. If you need some further evidence of their novice ability, check out my blog from Jun last year about the RAT Blackshades being used against Syrian rebels. If the SEA is supported/funded by the Syrian government than it’s not real surprise that they use tools that require little technical ability but utilize well executed social engineering attacks.
Keep up the good work man!
Blackshades In Syria: Malwarebytes Blog =P
It’s possible that these people have an over large ego – They’re doing the hacking but no one will think of hacking them. Hence the poor passwords.
Ya these malicious hackers think they are the smartest people in the world, that noone cares what they do or can hack them back, or that they are untouchable.
Just like a thief who steals so much it becomes habit or second nature…He thinks he’ll never get caught. Or a liar who lies so much he doesn’t know how to tell the truth anymore.
Total delusions, maybe from being on the pc too much, where pretending to be smart and making up stuff with big words to support nothing but untested theories is the norm.
I think alot of computer guys are so arrogant and rude because they really do feel most of society is just dumb monkeys to them. And i don’t know who these queers and anti social nerds, who grew up hating society, think they are gonna cause a revolution against. But its ironic the only people affecting anybodies daily life or taking away freedoms. Is malicious hackers….. and ironic they mostly only affect poor people still…..
Being new to this game myself, and as a reformed programmer, once you get into the hacking game (or anti-hacking in my case) you start seeing the world differently. A more likely scenario, in my opinion, is that when these guys started, they were newbs (or n00bs) and learned as they went. Unfortunately for them, and fortunately for us, they did not completely erase their footprints. “Shockingly (or perhaps less so for many security researchers who’ve dismissed the SEA as mostly a group of tenacious but relatively unskilled hackers)”
As you get more skilled, and you find out how more hackers get pwnd, you learn what not to do. An analogy is how some in prison learn to be better criminals when they get out. Keep up the great reporting! It helps me understand what I am looking for!
“Complacency breeds contempt …” and it’s no different for a “hacker(s)” who thinks that they cannot be touched. Let’s hope Brian and other security sites who’ve exposed THEM, aren’t on their “required” reading lists.
Besides, what do you expect them to do… use an SSO service?
And again email this email that . But no concrete proof of anything .This is Fake again . Crebs listen , SEA is just a cover for CIA operations .Usa will try anything to get they hands on Syria . Im not surprised they left password in the plain text .
Long live Assad .
The SEA mentioned domains are offline, as well as syrian-es (dot)net mentioned in the Vice article.
We all know to good how American and British secret services operate this days they will use lie ,murder,torch er ,bribery and so on , my list is endless . to get what they want . Just look at 9/11 /2001 .
So Brian, you must know that you are “hitting home”… because there is so much hate going on around here, you must be doing something right.
Sapiens hasty novelist
We Arabs we have the idea of you Americans, you are careful too do not you write anything before making sure of it thou become Ka Albgbghae your mind in your ear, because you did not open the sterile son Mohammed even know who is so Please, open the site and you will know who will be without all these analyzes her watch holiday writing your subject honestly فاتم the Americans, we do not believe one of you
What? Google Translate is not your friend.
يوزر is the same ‘user’! 🙂
Given the arrogance of your typical blackhat and given that someone young takes one path and then alters course as he matures, it would be natural to expect a lot of cases where the perps leave a trail of evidence.
Young blackhats are not known for having the next 20 years of their lives planned out. Mohammed Osman took a new path in life and, consequently, tried to change his online persona. He got busted and the rest of SEA is probably sweating out the fact that the head of SEA just got fingered by one of the top security sites on the Web.
Bad opsec, in retrospect, always appears to be stupidity. But to claim poor opsec is proof that the person is not a blackhat, Osman’s only argument, is to ignore the last 30 years of watching hackers getting sent to the clink. Blackhats are handicapped by the same thing everyone is subject to… human nature. But they have one further disadvantage which is that arrogance inevitably breeds bad opsec. How many “Anonymous” hackers have had their mug shots plastered all over the web?
Brian has repeatedly shown his skill in unmasking the perps, but he must admit that the arrogance of the perps has been one of his top assets.
Nailed it, Kurt.
Kudos, Brian.
I just wanted to thank the author for taking the time to illustrate this trail of bread crumbs. His passion for his work and dedication to the common decency of humans is to be commended. In other words, thank you for putting this out there.
wow nice investigation, finally revealed
Y’know…The thing that I just love about Krebs is how he immerses himself in the comments and isn’t afraid to call a spade a spade (see above posts from him, had me LOL, heh).
Some “public” information on the server that Syrian Electronic Army are currently using to host their website.
– Ping to sea.sy lead to : 141.105.64.37
– From http://bgp.he.net/ip/141.105.64.37
Their Russian ISP is Navitel Rusconnect Ltd with AS number = AS49335
with the whois button, we get :
inetnum: 141.105.64.0 – 141.105.64.64
netname: ShorefrontM-net
person: Andrey Shevchenko
address: Navitel Rusconnect
address: 19/2 Lva Tolstogo st.
address: Moscow 119034
address: Russia
abuse-mailbox: abuse@hostkey.ru
phone: +7(499)2463587
– From http://ip.robtex.com/141.105.64.37.html
Other domain/site found on this same server : qatar-leaks.com, Sea.sy, mail.sea.sy and http://www.sea.sy
– From http://route.robtex.com/141.105.64.0-24.html#sites
Others servers and sites hosted on the same ip range (at the bottom of the page)
With info from this page, and whois contact (abuse@hostkey.ru), we can suggest that they used http://www.hostkey.ru/ to rent their server.
– From http://www.hostkey.com/about/ :
Telecommunications company “Mir Telematiki” (The world of telematics), trade mark “HOSTKEY” is a joint venture with foreign participation, which has been providing, starting from 2007, services of colocation and leasing of equipment …
(basic vps are at 5 euros per month)
– Further information
Two hour ago, sea.sy and qatar-leaks.com was responding to ping, and these websites were accessible, but it is no more the cause. Maybe their server is currently under ddos.
Concerning the syrianelectronicarmy.com domain, it doesn’t resolved and seems to have been seized.