Internet regulators are pushing a controversial plan to restrict public access to WHOIS Web site registration records. Proponents of the proposal say it would improve the accuracy of WHOIS data and better protect the privacy of people who register domain names. Critics argue that such a shift would be unworkable and make it more difficult to combat phishers, spammers and scammers.
 A working group within The Internet Corporation for Assigned Names and Numbers (ICANN), the organization that oversees the Internet’s domain name system, has proposed scrapping the current WHOIS system — which is inconsistently managed by hundreds of domain registrars and allows anyone to query Web site registration records. To replace the current system, the group proposes creating a more centralized WHOIS lookup system that is closed by default.
A working group within The Internet Corporation for Assigned Names and Numbers (ICANN), the organization that oversees the Internet’s domain name system, has proposed scrapping the current WHOIS system — which is inconsistently managed by hundreds of domain registrars and allows anyone to query Web site registration records. To replace the current system, the group proposes creating a more centralized WHOIS lookup system that is closed by default.
According to an interim report (PDF) by the ICANN working group, the WHOIS data would be accessible only to “authenticated requestors that are held accountable for appropriate use” of the information.
“After working through a broad array of use cases, and the myriad of issues they raised, [ICANN’s working group] concluded that today’s WHOIS model—giving every user the same anonymous public access to (too often inaccurate) registration data—should be abandoned,” ICANN’s “expert working group” wrote. The group said it “recognizes the need for accuracy, along with the need to protect the privacy of those registrants who may require heightened protections of their personal information.”
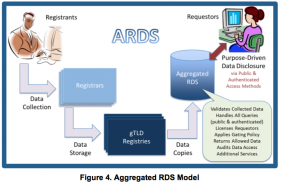
The working group’s current plan envisions creating what it calls an “aggregated registration directory service” (ARDS) to serve as a clearinghouse that contains a non-authoritative copy of all of the collected data elements. The registrars and registries that operate the hundreds of different generic top-level domains (gTLDs, like dot-biz, dot-name, e.g.) would be responsible for maintaining the authoritative sources of WHOIS data for domains in their gTLDs. Those who wish to query WHOIS domain registration data from the system would have to apply for access credentials to the ARDS, which would be responsible for handling data accuracy complaints, auditing access to the system to minimize abuse, and managing the licensing arrangement for access to the WHOIS data.
The plan acknowledges that creating a “one-stop shop” for registration data also might well paint a giant target on the group for hackers, but it holds that such a system would nevertheless allow for greater accountability for validating registration data.
Unsurprisingly, the interim proposal has met with a swell of opposition from some security and technology experts who worry about the plan’s potential for harm to consumers and cybercrime investigators.
“Internet users (individuals, businesses, law enforcement, governments, journalists and others) should not be subject to barriers – including prior authorization, disclosure obligations, payment of fees, etc. – in order to gain access to information about who operates a website, with the exception of legitimate privacy protection services,” reads a letter (PDF) jointly submitted to ICANN last month by G2 Web Services, OpSec Security, LegitScript and DomainTools.
“Internet users have the right to know who is operating a website they are visiting (or, the fact that it is registered anonymously),” the letter continues. “Today, individuals review full WHOIS records and, based on any one of the fields, identify and report fraud and other abusive behaviors; journalists and academics use WHOIS data to conduct research and expose miscreant behavior; and parents use WHOIS data to better understand who they (or their children) are dealing with online. These and other uses improve the security and stability of the Internet and should be encouraged not burdened by barriers of a closed by default system.”
Other public comments submitted so far reflect angst over the geopolitical ramifications of the proposed changes. For example, Afnic, which is the registry for the domain names in the geographical area of France (.fr) among others, notes that the ARDS would have to be legally established in at least one country, and its technical infrastructure would also have to be under at least one jurisdiction.
“We are concerned that the ARDS would use ‘one size fits all’ rules to assess request validity. With approximately 1500 TLDs in the root several of them will be highly local, and should not be subject to the same rules as .com or .net in terms of which Law Enforcement Agencies can request access to data,” wrote Afnic’s Pierre Bonis. “Should Chinese LEAs be granted access to private data for .berlin domain names for instance? We believe this issue is insufficiently taken into account so far.”
The Center for Democracy & Technology (CDT), a nonprofit policy think tank based in Washington, D.C., maintains that the current system is broken and raises serious privacy and free expression concerns by revealing sensitive information to the public.
“According to the OECD’s privacy guidelines, personal data should be relevant to its intended purpose and should be protected from unreasonable or unauthorized disclosure,” CDT wrote in its official comments (PDF) on the proposal. “The WHOIS system needlessly exposes registrants’ sensitive data to anonymous queries, granting easy access to malicious users.”
CDT has proposed a hybrid system that would allow individual, noncommercial registrants to choose to keep their sensitive information private, but maintain public access to commercial Web site registration information. CDT said it favors an approach similar to that adopted by Nominet — the registrar that handles the dot-uk gTLD.
“This policy properly balances the interests and obligations of commercial and non-commercial entities in the internet ecosystem: entities offering services or engaged in trade should necessarily disclose more contact information as part of WHOIS, such that the public can access details needed for commercial and legal activities,” the CDT argues. “Nominet also employs a simple but clever method of dealing with those that abuse this distinction: if Nominet determines that a commercial entity has improperly self-identified as an individual, they can change the setting on that registry entry such that more detailed commercial-entity contact information is publicly shared through WHOIS.”
Garth Bruen, principal investigator at Knujon (“no junk” spelled backwards) and a longtime, vocal critic of ICANN’s lack of progress on WHOIS data accuracy, said the working group’s interim recommendations are about burying — not fixing — the WHOIS problem.
“For 14 years now, ICANN has been criticized for not dealing with this issue directly, and now they want to bury WHOIS records behind a wall so that nobody can criticize them anymore,” Bruen said. “The offering of tiered access with higher access for law enforcement and security operations should not be seen as some kind of positive development, it is actually a red herring. Law enforcement already has superior access to registrant data, they always did. WHOIS is about ordinary Internet users being able to find out who owns a domain name. The consumer is ultimately being frozen out, now having to go to the police or some for-pay security service to get information about a domain name.”
As a journalist and cybercrime researcher, I tend to side with those who favor maintaining the status quo on WHOIS records. As the numerous stories in my Breadcrumbs series make clear, WHOIS records are extremely useful for finding and exposing fraudsters and cybercrooks. Even when spammers or scammers quite obviously put false identity and address information into WHOIS records, they still very often leave behind clues that can be used to draw important connections and correlations, such as the re-use of the same email address or phony phone number. Also, WHOIS records are extremely important means of reaching Web site owners whose sites are infected and being used to spread malicious software.
Finally, the working group’s interim report leaves open in my mind the question of how exactly the ARDS would achieve more accurate and complete WHOIS records. Current accreditation agreements that registrars/registries must sign with ICANN already require the registrars/registries to validate WHOIS data and to correct inaccurate records, but these contracts have long been shown to be ineffective at producing much more accurate records.
Dozens of comments on ICANN’s plan have been posted here and here. What do you think about it? Sound off in the comments below.




“As a journalist and cybercrime researcher, I tend to side with those who favor maintaining the status quo on WHOIS records. As the numerous stories in my Breadcrumbs series make clear, WHOIS records are extremely useful for finding and exposing fraudsters and cybercrooks.” To test this statement I used Google’s “site:krebsonsecurity.com WHOIS” targeted search. Google responded with “About 1,230 results”.
I don’t think that’s how you do a WHOIS look up on a site…
Brian’s records are safe from another person for another day.
I believe he was referring to the fact that Brian does in fact find WHOIS records useful and uses them, due to the number of results found.
Try using this command prompt program:
http://technet.microsoft.com/en-us/sysinternals/bb897435
The google command “site:sitename” will list anything about the site , cached or otherwise. All it does is list anything that is related to the site web wise.
I won’t mention any specific website names, but there are free web crawlers out there. All you need is a URL and then you can crawl the site.
Another way to dig deep into a web URL is a sitemapping tool. Yep, there are many out there as well. All you have to do is slap in a URL, make a few choices and decide how long you want to wait. Some of the sitemapping tools will follow every stinking link within, and out of the site that is being crawled. its crazy.
With that information, all pages that are viewable, or some that may be misconfigured – can be viewed. If some one wanted into a site bad, this is probably one of the first things they would/could do to a site.
That has little to do with the ICANN privacy matters. I think ICANN is concered about the POC info.
If the prvacy is to work, there should be a process in place to verify your credentials each year.
Spammers usually register websites that make no sense, and often with stolen CC info. They use it for as long as possible, and then move on. So as jacked up as the registration is for websites, the privacy side of the house is simply a convenience for the people who don’t know there are other ways to circumvent all of the POC data.
LoooooL. Seriously, nice WHOIS search bro. Maybe term, “whois krebsonsecurity.com” or go to whois.com, click on whois and put the site in. I mean… WOOOOW
Just for note, Brian utilized PRIVATE REGISTRATION as anyone with a brain does in today’s day and age. Nonetheless, here’s his whois:
omain name: KREBSONSECURITY.COM
Administrative Contact:
Contact Privacy Inc. Customer 0122383209, email@contactprivacy.com
96 Mowat Ave
Toronto, ON M6K 3M1
CA
Another wooooooosh. Nice. but you bring up the other side to this story, that is the current system is really only as useful as a perpetrator lets it be, since there are many ways of falsifying/obfuscating, or even privatizing/anonymizing the whois data. Not that the proposed system would reduce that, but the system in general does deserve attention since it really only is fodder for salacious blog posts, and cant be trusted for anything useful.
Isn’t this solving a non-problem? There are tons of services that will anonymize your WHOIS for you at a small fee if you need it. Why is anyone wasting time on this?
Well, for people in countries under tyrannical rule, private registration is a must, but if you hand any gov’t over access to that info, it’s a moot point. The gov’t has plenty of info they can NOT release. Public info such as who owns a website, should NOT fall into that category and if this is actually adopted, you will see a LOT of domains NOT be renewed, but WILL see a lot of people turning to bogus registration info and anonymous payment methods. In the end, it’s a lose/lose proposition and I’d wager that a group like HTP will rip their database within days of the conversion.
WHOIS has its share of problems, but isolating it from the public is not the answer. The proposed solution is extremely heavy handed and seems to be a desperate attempt to avoid addressing the real problem.
This is a double edged sword. And its somewhat difficult to explain.
For the legitimate business owner with their nose to the grindstone, its a good move. I am sure there are people hired to obtain email addresses any way they can. The spammers are always looking for new victims, and new victims are added to a new list that can be sold over and over again.
There are several registars that allow a person to purchase privacy for a website, where the registar will put their address in the point of contact information, and then if there is an issue, the registar can contact the web site owner.
So in that case, paying like 12 bucks a year, ANYONE – including spammers can use this type of service. I am sure if the spammers are located on an ISP or a registar that doesn’t give a hoot, then the information could be distorted as well.
One other thing. One assumes that when people sign up for websites, that their point of contact information is correct. Who knows for sure? There are ways around everything.
I honestly think this isn’t going to help much. I pay attention to alot of the websites out there, and MANY if not all the bigger businessses have limited their email addresses and personal contact information. They may have a generic form out there for a user to fill out and send, but for the most part this is a self policing and controlling feature the businesses are doing by themselves. I’d say they are ahead of the ICANN momentum by a good margin.
I am sure there are ways to get information if one wants to dig deep enough. The people over at SPAMHAUS.org and other sites as well seem to find links to the bad people without much issue.
So as A. Miller above stated, its either a late thought by ICANN, or it is a marketing scheme to have people pay attention to their domain names and look for other services that they may, or may not need.
Or you could stop using Dumbdaddy and go with a registrar that gives privacy for free such as InternetBS. Not as if the domains cost you more to make up for it.
I have a domain where the postal address required non-ASCII characters. The result was that my registration was fairly corrupt (surprise!). I couldn’t fix it later when I moved to a new address with only ASCII characters (I can’t remember what prevented me from fixing it). Now my new address is probably outside the region. I’m not going to touch the registration information.
I’m not opposed to being able to do research into ownership, but I have a hard time understanding a genuine use for the postal address requirements in the modern age. My registrar never sent me mail to my postal address. My registrar has contact information for me (email).
If I want to get a high quality Certificate, let the CA send me mail to a postal address, and let it manage information requests. [CAs in my opinion don’t provide sufficient service to end users — they should be on the hook to individuals who have questions about a certificate they’ve been presented instead of just earning money by selling the certificate.]
My phone number lapsed too, but again, as with the postal address field, why does a normal person need it? In the old days (1970-1985?) when a site was down and you needed to contact someone, you might call them, but you were comrades. Today, you don’t do that, you send an email (or use Facebook or Twitter). And more connected people are adversaries than comrades.
When a site I visit is spammed, sending a letter through the postal service isn’t going to get it fixed quickly. And while I could call the number listed it’s probably not a technical person who could actually fix the site – I tried the contact but not because of whois. In my sample of size one, tweeting would have been more effective since it would have reached the social / technical contacts.
My solution: Status quo WHOIS. Redo ICANN, or scrap it to be replaced with one regional ICANN member (I lean towards Knujon) .
Totally bad move on ICANNs part. As a Moderator at 419eater.com and a member at aa419.org access to WHOIS is essential if fake banks, diplomatic courier companies etc are to reported.
Thanks for posting! You guys helped me shut down a fraud site once, and I lost your URL after a hard drive crash. So thanks for your service!! I now have a better backup plan! 🙂
Shut it all down .
As a user, I like to to check out, from time-to-time, IP addresses that my PC is communicating with. For obvious reasons. I consider this to be an important component of defensive computing.
My tools of choice on Windows are NirSoft’s IPNetInfo and CurrPorts:
http://nirsoft.net/utils/cports.html
http://nirsoft.net/utils/ipnetinfo.html
Please keep WHOIS open.
Some of your readers seem to have no idea what WHOIS is – maybe you should have explained it more fully.
When someone buys or renews a domain name, they are required to give registration information, including a real address, phone number and email address. This information is generally publicly available.
This is similar to any business anywhere who incorporates – they are legally required to publicly register their business name (“doing business as”) and anyone in the public can access this info. It is part of the “public” in public corporation.
Same with domain names – as a requirement for a name being issued, there must be a public registration so someone is held responsible and can answer to complaints and other legal matters.
Even the private registration companies are required to have info about who registered the name, and they must contact the “real” owner when there is some issue.
You or anyone else can go to a domain registrar and request the public info about any domain name. One place to go is network solutions, here:
http://www.networksolutions.com/whois/index.jsp
Hehehehehe. For the techie who fills out the Point of contact info, most companies use a blackhole email address or other bogus information.
network solution offers a privacy cover-up solution for like 12 bucks a year. Sure they want your info, but mainly its a yearly checkup thing. The bad websites are typically up 12 days, let alone 12 months.
You have to realize that this isn’t a solution to anything. All a BAD guy has to do is to buy some advertisement space on a well known website. The legit ad runs for several days. depending on where the ad is being kept, the BAD guy simply changes the landing page to be malicious on a late Friday afternoon, so the BAD ad now has time to poison as many visitors as possible.
Another method is to populate a website to mimic a trend such as a “breaking news” event, or a service that is always being used, like a travel agency or Hollywood soap opera site. Then when the hits increase, simply have all links on the URL turn vile.
In those scenarios, not matter what you slap in the POC info, its not going to help. The entire internet would have to have updates every single second to watch for the bad stuff that pops up. Thats beyond reality. Web site reliability scores would change quicker than the NY stock exchange.
There is no self-repudiation process for proving that the contact info. You can simply enter whatever you wish, and it’s a done deal. Sure there are honest people out there, but if you want marketers wanting to clean your office/bathrooms, advertisements, spammers and such feel free to put legit info in there.
There is a better way. There is WOT, another is the symantec/norton website checker. All that is good for established websites.
Only other way out to determine whether the site is foul is to have an Internet Security suite that updates the bad site list on a regular basis. I use a service that offers to strip all ads, offers various levels of protection and more.
I have no idea why this is all of a sudden a “big deal”. People have a tendancy to click next, next, next and not pay attention to the outcome unless it affects their bank accounts.
The focus should be on securing the legitimate websites, vice worrying about whether you can contact someone on the other end after a device gets infected with something foul.
What political wing-nut organization thought up this plan?
Reading between the lines reveals that the ICANN Wanking Group’s proposal has little real benefit or merit and is just another dollar gouge.
It’s all about the money!
Can’t sell whois data if everybody can get it for free.
Or it’s an order from higher-up that want to get their hands on those dirty foreigners’ information.
If you do any tracking research these records allow some light on the subject. Over the last 10 years the data has gotten more obfuscated and useless, but there are still history records that allow some background digging that helps to attribute the ownership or connect the ownership in a way that has been useful. As long as I can still get to the data for free I don’t care if they vet me first. If they start making me pay to track down the information I will find another way.
I’m one who always complains about the lack of information or inaccuracy of WHOIS. But my God its better then nothing!?
I guess i know now why CRISP never succeeded WHOIS. http://en.wikipedia.org/wiki/Cross_Registry_Information_Service_Protocol There go my hopes for a better WHOIS for the public.
And so instead of making WHOIS more detailed or accurate for the average home pc user that wants to protect himself, or report fraud or criminal activity, they are making ARDS only for law enforcement? I can’t believe this.
So now law enforcement, hackers with stolen access, and rich people who can afford investigators are the only people who can investigate suspicious internet connections.
When is the Gov’t gonna realize, that the things they are doing like back doors and mass information retrieval, even if well intended, are actually achieving the opposite affect and making us all less safe and secure!
I think trying to convince people that WHOIS does more harm then good is nonsense. It seems, once again, the avg home user and our infrastructure in general is being made more vulnerable like sitting ducks.
Being a domain name owner myself with a 100 percent valid WHOIS record, I always thought that then when you sign up on a domain registrar, that a person should prove their identities. Everywhere you go now and days whither it’s a signing up for a bank account, getting a license or going on a airplane you have to prove your identity. In my opinion , when in the sign up process of a domain name you should have to provide your full credentials to prevent abuse of the internet. Their shouldn’t be any anonymous records or immediate registration without a waiting period to validate your information. I’ve seen way to many phishing scams where the registration date is on or very near the actual date in time of discovery. Their should be at least a one week waiting period for registration of all domain names regardless of the T.L.D. to prove that you are in fact the registered owner, government agency or organization .
For sure! That will ensure that a new black market for domain names will spring up immediately, using stolen identity data.
And who is going to pay for validating this proof of who you are and how far are they going to take it in any case seeing as people already fake identities for other activities in a trivial manner?
As a website operator – under 5 domains – I find having access to whois data invaluable. 75% of the traffic to my domains are crap, unwanted spiders and spammers. With whois, I can quickly decide to block a complete subnet … especially if it is outside the target audience or local. We want to sell to corporations in the USA and Canada, not China, Ukraine, Romania or Kenya, etc.. All the bandwidth those unwelcome visitors take is a complete waste. The blog spam that must be remove/cleared is a waste and eats into our profitability too.
Using forward and reverse lookups is extremely handy.
yes exactly , even as a home user i will block whole address blocks after using WHOIS….good point.
This isn’t about subnets/IP ranges. That’s a different kind of whois. This relates to domain names, particularly those ending in “.com,” which are controlled by ICANN.
There are already registries that don’t require public whois, like .ru or .eu domains. If you’re dealing with a site with one of those domain names, you have to understand the ownership information isn’t available to you. It’s intrinsically riskier to do business with a site like that.
.com domains are supposed to be commercial sites with no reason to hide their whois, any more than a bricks and mortar store would want a secret address. (That idea was thought up before spammers started harvesting email addresses from the public whois, so that secrecy started looking like a good idea.)
But you still need to be able to check the ownership of a commercial site before you decide to send them money, and knowing that the whois information has been public and unchallenged for several years is very helpful.
Whether that same openness needs to be extended to all the new top level domains that will start being used (like .berlin as mentioned) is a matter of whether consumers are going to trust those sites as much as a .com or trust them no more than a .ru domain.
yes but even if I can’t get domain names associated with an ip addres…. Which might be 1000 diff names, half of which doesn’t even make sense.
TO be on the safe side at least I can get the whole subnet or range of that ip’s network from WHOIS and block it which gives it some worth.
WHOIS is not a good indicator of geographical location. Run a WHOIS on my FiOS DHCP address and you will think I’m in Virginia. That’s the owner of the IP address, not the user. It will take some digging into DNS records to show that I, the user of that IP, is in California. Do you think all that traffic from 1.1.1.1 and 1.2.3.4 is really coming from Australia?
The article is talking about WHOIS lookup of domain names, eg google.com, not ip addresses.
It’s possible to do WHOIS lookups on IP addresses. I do it all the time. But it’s not always the most accurate way of getting data about who owns IP addresses or blocks of addresses. In most cases, it’s best to query ARIN or RIPE for these things.
Thanks Brian. I use the whosip command line utility from Nirsoft for both IP and domain WHOIS queries (http://www.nirsoft.net/utils/whosip.html).
I mean yes i guess we should just be looking up domain names instead of ip addresses. programs like iftop, etherape etc can give this info.
But you can use whois for ip addreses too, and most of the time, to be honest, I don’t care what company owns an ip address. I’m not interested in researching them, I just want to block their whole dam network.
So even for a lay guy like me, whos not a security researcher I find whois somewhat useful, even if for most other things its totally inaccurate or lacking info.
sometimes also you can’t resolve a domain name and only choice is to look up the ip address.
In my country CIRA makes all domain registrations private for non-business users unless the user specifically sets it to public. Businesses have theirs as public only – though they can buy and use private services to shield their information. This came after long consultation and there hasn’t been much of a problem since.
Face it – scammers, hackers, spammers etc only put a real email address on their whois details. It’s the only part they really need to be real so they can administer the domain at the registrar/move it etc.
I have had a few privacy companies remove privacy from domain whois reports due to spamming etc and you quickly find as noted above – it’s all fake anyways apart from the email. And even with the email they can if they choose to can use a new one each time (though it seems many are too stupid or lazy).
The bigger issue is ICANN being under the thumb of the U.S..
Surprisingly, scammer often use real stolen identities to register domains. That way, if someone challenges the whois, the registrar can send a letter to the name/address in the whois. The recipient, of course, will think it’s a scam and discard it, because he/she will have no idea what it’s about. But all that is important is that it not return “undeliverable.” Then the whois is assumed accurate.
The way to track those is to call the person in the whois to prove they didn’t register it (and often had their credit cards stolen to pay for it).
Seems a rather odd thing to do if the same things happens as if they just made up details. Unless I’m missing something which wouldn’t be unlikely.
I reach out to the owners of 40+ domains each month that have failed to secure their website in order to get phishing content they host taken down. Having some intermediary operate all the whois services isn’t going to do anything but delay these legitimate queries and end up costing organisations who want to query money. In my view this is nothing but an attempt to control the internet, monetise what is now a free service and limit peoples ability to research who is behind a given site.
This seems to be a problem of authentication. What exactly are the validation requirements that ICANN uses? Why not make it a bit more like how a CA authenticates a web server?
ICANN – can this one !
“To replace the current system, the group proposes creating a more centralized WHOIS lookup system that is closed by default.”.
… and of course for security folks to do they jobs, conducting lookups or getting information on a specific domain or IP, you’ll need to have a subscription… for a “small fee”, of course.
“the dot-uk gTLD”
http://en.wikipedia.org/wiki/Top-level_domain#Types_of_TLDs categorizes dot-uk as a ccTLD.
What do you do when you find that the owner of 1000 domain names used in internet frauds is a 80 years old russian farmer? Take his goats away? Or beat his wife to death? Just what the bad guys didn’t do when they told him to register the domain names. Well, at least you can make some money on your “secure”, restricted whois-records.
my big question is: “how should this improve the accuracy of WHOIS data”?
right now we have some badly managed TLDs without or broken WHOIS. (most WHOIS data is fine as it is)
I have no idea how ARDS should fix that. Theres no law to force TLDs to submit their stuff to ARDS and keep it updated.
I guess they could try to offer them money, which would explain why access to the system will be restricted. so they can sell access to it.
i guess they run out of ideas for stupid new TLDs to launch, so they try a new money avenue 😉
I use WHOIS occasionally, but its usually to check up on who is trying to do business with me, and to check the credentials of suspect entities, and it’s saved me embarrassment on numerous occasions. I’d hate to lose access to such a service, but wouldn’t want to pay an extortionate access fee, either per item or annually.
It is no surprise domaintools.com is against this considering they profit for supplying historic records.
I think some govt folks were suprised, when after the big TOR/Firefox attack, that they would be found out so easily. Expect more crazy stuff like this.
This is insane, how we are going to verify the domains if they are available or taken ? The billing system is using whois constantly. This (if true) will really mess a lot of online businesses.
yes i agree this is a joke we all need this to fined the web dumaine