Attackers appear to have compromised tens of thousands of Web sites using a security weakness in sites powered by the forum software vBulletin, security experts warn.
In a blog post in late August, vBulletin maker Jelsoft Internet Brands Inc. warned users that failing to remove the “/install” and “/core/install” directories on sites running 4.x and 5.x versions of the forum software could render them easily hackable. But apparently many vBulletin-based sites didn’t get that memo: According to Web site security firm Imperva, more than 35,000 sites were recently hacked via this vulnerability.
The security weakness lets attackers quickly discover which forums are vulnerable, and then use automated, open-source exploit tools to add administrator accounts to vulnerable sites.
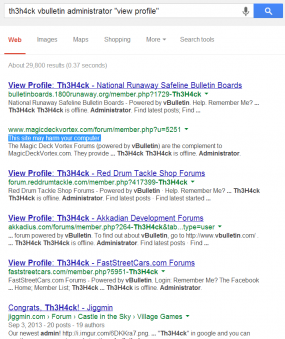
Imperva said the compromised sites appear to have been hacked by one of two sets of exploit tools that have been released publicly online. The first was apparently used in a mass Website defacement campaign. A Google search for forums with the the rather conspicuously-named administrator account added in that attack (“Th3H4ck”) shows that many of the hack sites also are hosting malware. Among the sites apparently compromised is a support forum for the National Runaway Safeline and a site selling vBulletin add-ons.
The second tool does effectively the same thing, except with a bit more stealth: The administrator account that gets added to hacked forums is more innocuously named “supportvb”. Here’s a Google search that offers a rough idea of the forums compromised with this exploit, which was apparently authored or at least publicly released by this guy.
 Amichai Shulman, Imperva’s chief technology officer, said the company believes the attackers are using some sort of botnet — a collection of hacked PCs — to help scrape Google for compromised sites and to inject the malicious code.
Amichai Shulman, Imperva’s chief technology officer, said the company believes the attackers are using some sort of botnet — a collection of hacked PCs — to help scrape Google for compromised sites and to inject the malicious code.
“In order to infect 30,000 targets in such a short period of time you need Google, but the problem is that you can’t retrieve so many search results that easily in an automated way. Google may show you that there are 30,000 [vulnerable target sites], but when you start scrolling through them all you may get to maybe page five or six [before] you get a message that your machine is performing automated queries, and it will start showing you CAPTCHA,” challenges to block automated lookups. “And if I repeat this behavior from the same Internet address, I’ll get blocked for a certain period of time.”
Barry Shteiman, director of security strategy at Imperva, said that distributing the searches through many different Internet addresses solves that problem.
“These guys can instruct each part of that distributed network to perform a partial search that would return a part of the entire results,” Shteiman said. “That way they can get the list sliced into much smaller pieces that a single machine can then crawl and scrape.”
If you run a forum or site powered by vBulletin, take a minute to check if you have followed vBulletin’s advice and removed the “/install” and/or “/core/install” folders. If your vBulletin site still has those directories installed, you may also want to check for new administrator accounts.
I followed up with the vBulletin folks and asked whether the company planned to automate the removal of these forums in future updates. A member of the vBulletin support team said version 4.2.2 “fixes the problem, but we still always recommend removing the install folder.” The same individual promised that the as yet unreleased vBulletin v. 5.1.0 will have additional, unspecified fixes, “however you still need to remove the install folder.”




The most recent patches and updates to Vbulletin force you to remove the /install directory at the end of the installation / upgrade process.
This is HUGE again. “Well done” Jelsoft. Just got a hacked customer’s forum yesterday. Now the skies are clear.
Jelsoft hasn’t existed in 5+ years.
Internet Brands Inc is the parent company of vBulletin (they bought out Jelsoft long ago).
I fear IP Board is no better in the long run as they had a total of 7 security updates this past year (more than vBulletin), although be it this one seems more extreamly exploited.
I would recommend XenForo which is developed by some of the original core members of Jelsoft, when vBulletin was still good, stable, and most importanly secure. They’ve not had an issue in the past 3 years (the life of the company).
Glad to see you’ve come out of the word work again Adam to spread more lies and falsehoods.
IP Charlie
False?
What is false in my statement…. IPB had a total of 7 security updates in the past year and to the best of my knowledge, vBulletin had only 2, XenForo 0.
I included a link to each one (all 7) of them in my review of IP Board http://www.webhostingtalk.com/showthread.php?t=1297652
And as stated, the current vBulletin exploit seems to be more extreamly exploited.
You not liking something does not make it untrue.
It’s the same crap as vulnerabilities in both WordPress and Joomla websites that are highly exploited then used as Phishing scams against worldwide banks and Paypal.
We paying 250 $ for a license and what we get for it — swish cheese ??
Bunch of amateurs !!
It really isn’t vbulletin’s fault if people do not follow the instructions. They have clearly told people to remove the install files for a long time.
Granted they could have done more as they do now by stopping the forum operating while the install file is there.
People should not be looking for scapegoats when it is they themselves that failed to read the instructions.
I think you meant:
We are paying $250 per year for a license and what do we get for it — Swiss cheese ??
What a bunch of amateurs !!
“Google may show you that there are 30,000 [vulnerable target sites], but when you start scrolling through them all you may get to maybe page five or six [before] you get a message that your machine is performing automated queries, and it will start showing you CAPTCHA,” challenges to block automated lookups.”
The researcher in question needs to do some looking around before making statements like this and using it to infer that there must be a botnet being used. That’s just idiotic to anyone who scrapes Google for SEO purposes.
Where has it claimed they were scraping google for SEO purposes? They were scraping google to find vulnerable targets. And as an FYI this is a very common practice. Many automatic tools use the same practice.
Technically this is the same.
I can easily scrape more than 30K pages just from my home PC, even without proxies.
Just shows that these “security” “reearchers” are bunch of useless human crap.
Ryan Barnett from Trustwave Spiderlabs just sent me a note pointing to an interesting and very relevant post he put together last year which documents the same type of botnet scraping activity referenced by the Imperva guys.
http://blog.spiderlabs.com/2012/05/honeypot-alert-inside-the-attackers-toolbox-botnet-web-attack-scripts.html
isc.sans.edu – Internet Storm Center – the people who work incident handling for free…..is probably all over this. I am sure some one behind these scenes somewhere has a way around the CRAPCHA code.
You miss a ” at the end of this search in your article: https://www.google.com/search?q=%22supportvb%22+vbulletin+administrator+%22view+profile
Agreed but in all honesty the results are almost identical for both queries.
I have observed IRC botnets that query Google to find vulnerable applications using “Google dorks” – once a dork is found to match a particular application and version, attackers feed this query to automated scanning bots that quickly uncover thousands of vulnerable sites. (OS Commerce and WP TimThumb scanners seem to be the most popular targets from my experience)
Most of the time these bots also have automated exploit options, and a common payload would be to add a new user to the application.
Bot masters sit on the IRC channel, scanning new dork queries, waiting for replies. When a bot finds a vulnerable application, if exploitation is successful, the bot sends back a “Success” message to the IRC channel. The bot admin can now check the application by logging in with the new account.
Irc.Byroe.net (apparently offline now – Google for examples) used to host these scanning botnets. This particular IRC network was amateurish, mostly all channels were scanning for something, and admins were open to letting people even control the bots and issue their own query.
Very interesting, P, thanks for that.
There’s alot of servers like that. Run a web honeypot (I.E. – Glastopf) for any length of time and you’ll find the names of such networks in the RFI’d php script you’ll eventually find.
I am a developer for Web Wiz Forums which is a free forum application and with our forum software rather than having to remove the install folder, which we call setup, we simply add a check on the install files to see if Web Wiz Forums has already been setup and if it has the install files will not run.
@Peter. It is Vbulletins fault as a simple check in their install files to see if vBulletin has been setup already would have avoided this issue, especially as most people do not read instructions, which we are all guilty of at one time or another, to have manually removed the install files.
If you are producing website applications where the source code can be read security has to be top priority as it is amazing the lengths and time hackers put in to going through thousands of lines of code to find even the smallest vulnerability.
“however you still need to remove the install folder.”
Well… I’m thinking of removing the whole /vbulletin directory and find a better forum software. 🙁
I moved to XenForo and have never looked back
This is nothing new. I can tell you from past experience that most of the forum style software will tell you to remove the installation directory in the documentation or on-screen during installation.
Some software will “nag” you that the directory still exists.
If anyone has previously installed the software before, and didn’t see the instructions, then they should ask. Its a 2 minute ordeal that could have saved them months of recovery.
Vbulletin hasn’t been a favorite amongst many. If I recall correctly, early on, say 6-10 years ago , they had a snafu and well, it stuck. When people mentioned their name, it was sort of shunned.
The software – any software for that matter is only as good as the programming behind it. REMEMBER – its internet facing, and a prime target. People will find a way to wiggle in, and its important to set up as many security controls as you need to, to keep the evil ones out.
Somebody keeps DoSing your site, Krebs. At 2am last night they attacked your DNS servers, which were timing out for at least a half-hour.
Cloudflare for the actual website won’t help much if they can get at your name servers. You need to look into adding some kind of added redundancy there.
I say leave it as is. Its like building a road for excessive traffic for just on the weekends. Overall, time wise, if the system works without additional costs, leave it be.
Though the reads here are interesting, they are far from critical which would require some additional avenues out. brian probably doesn’t host his own server in house and uses a 3rd party web hosting service, so unless they want to pony up for the additional expense or resources, its probably not going to happen.
If anything – the hosting comany gets some great practice on thwarting DOS attacks.
I can recommend the Simple Machines Forum (SMF) as a very good, very secure forum package (and it’s free). They’ve had some minor issues over the years but overall I’ve had no problems with it, and the developers take security seriously.
I don’t understand one thing.
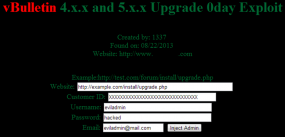
The image that Brian calls “Attack tool for exploiting vulnerable vBulletin forums” is not the same code listed in the goo.gl link from $Doc’s Twitter feed which leads here (hxxp//www.indetectables.net/viewtopic.php?f=59&t=47785).
That link shows what $Doc’s code displays as which looks totally different from the “attack tool” image.
The above link has a Pastebin URL which shows the actual code.
I’m confused as to why there is a difference.
Thanks.
Sorry – ignore the above.
I see that the first tool is the “attack tool” and $Doc’s code is the second program.
What about vBulletin 3.xx series? Are they affected?
Why do they have to use Google?
xRumer has already done the legwork, just buy a copy & use their DB.
First thing about any form of online transaction is security and the second thing is security, why because the internet is anonymous.
Interesting, I posted a comment about hos I deleted java and never looked back and my comment was deleted.
I’m a moron, was on the wrong article, nothing was deleted. But I do love how Krebs puts the hackers picture up. I just showed my son, and he laughed like heck. Nothing like putting up a pic of a hacker who got caught. Great job Krebs. Love this site.
I have been hacked. Only renamed install as install.old – no good