Adobe and Microsoft today each issued security updates to fix critical vulnerabilities in their software. Microsoft pushed 14 patches to address problems in Windows, Office, Internet Explorer and .NET, among other products. Separately, Adobe issued an update for its Flash Player software that corrects at least 18 security issues.
 Microsoft announced 16 bulletins, but curiously two of those are listed as pending. Topping the list of critical updates from Microsoft is a fix for a zero-day vulnerability disclosed last month that hackers have been using in targeted cyber espionage attacks. Another critical patch targets 17 weaknesses in Internet Explorer, including a remotely exploitable vulnerability in all supported versions of Windows that earned a CVSS score of 9.3 (meaning it is highly likely to be exploited in drive-by attacks, and probably soon).
Microsoft announced 16 bulletins, but curiously two of those are listed as pending. Topping the list of critical updates from Microsoft is a fix for a zero-day vulnerability disclosed last month that hackers have been using in targeted cyber espionage attacks. Another critical patch targets 17 weaknesses in Internet Explorer, including a remotely exploitable vulnerability in all supported versions of Windows that earned a CVSS score of 9.3 (meaning it is highly likely to be exploited in drive-by attacks, and probably soon).
That flaw is a rare “unicorn-like” bug according to IBM X-Force, which discovered and reported the issue privately to Microsoft. In a blog post published today, IBM researchers described how the vulnerability can be used to sidestep the Enhanced Protected Mode sandbox in IE11, as well as Microsoft’s EMET anti-exploitation tool that Microsoft offers for free.
“In this case, the buggy code is at least 19 years old, and has been remotely exploitable for the past 18 years,” writes IBM researcher Robert Freeman. “Looking at the original release code of Windows 95, the problem is present. In some respects this vulnerability has been sitting in plain sight for a long time, despite many other bugs being discovered and patched in the same Windows library (OleAut32).”
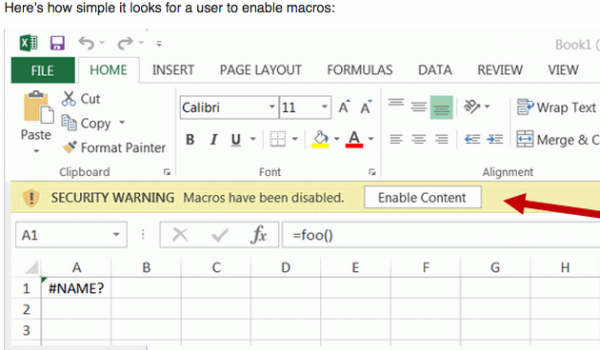
Freeman said while unpatched Internet Explorer users are most at risk from this bug, the vulnerability also could be exploited through Microsoft Office files. “The other attack vectors this vulnerability could work with are Microsoft Office with script macros, for example in Excel documents,” Freeman told KrebsOnSecurity. “Most versions of Office (since about 2003) have macros disabled by default so the user would have to enable them (which can be a fairly mindless YES click at the top of the screen). Or if a user is using an old enough version of Office, the macros will be enabled by default.”
According to Shavlik, the two pending patches, MS14-068 and MS14-075, are both listed on the bulletin summary page as “release date to be determined,” which apparently is an anomaly we haven’t seen before. “Typically, a pulled patch is removed from the list entirely,” wrote Chris Goettl, product manager at Shavlik. “This could mean it may still come this month, but not today. These two patches were likely an OS and the Exchange patch based on the advanced notification list,” That is at least one less major product admins will need to be concerned about this Patch Tuesday, although the date to be determined could come at any time.”
As I’ve noted in previous posts, the few times I’ve experienced troubles after applying Microsoft updates have almost all included a fix for Microsoft’s widely-installed .NET platform. If you have .NET installed, it’s probably a good idea to install this one separately after applying the other updates and rebooting.
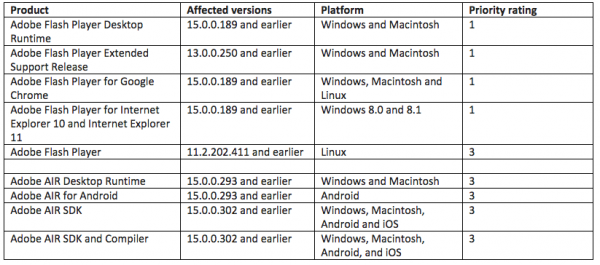
Adobe’s update addresses a whopping 18 security holes in Flash Player and Adobe AIR. Updates are available for Windows, Mac and Linux versions of Flash. Adobe says Adobe Flash Player users should update the program to the version 15.0.0.223. To see which version of Flash you have installed, check this link. IE10/IE11 on Windows 8.x and Chrome should auto-update their versions of Flash.
The most recent versions of Flash are available from the Flash home page, but beware potentially unwanted add-ons, like McAfee Security Scan. To avoid this, uncheck the pre-checked box before downloading, or grab your OS-specific Flash download from here.
Windows users who browse the Web with anything other than Internet Explorer may need to apply this patch twice, once with IE and again using the alternative browser (Firefox, Opera, e.g.). If you have Adobe AIR installed, you’ll want to update this program. AIR ships with an auto-update function that should prompt users to update when they start an application that requires it; the newest, patched version is v. 15.0.0.356 for Windows, Mac, and Android.




Adobe’s getting quite a track record…are we to the point yet where it’s time to dump flash?
Um, that moment happened quite some time ago. It’s adivsable that people disable the automatic playing of flash and other active content in their browsers and use “click to play” features. Not 100% (not much is) but should significantly reduce the risk profile.
Just use NoScript and be done with it.
You can then selectively enable Flash on known properties like YouTube.
Or just remove flash from the program files – you shouldn’t need it any more from IE-11 on or any modern browser.
“Adobe’s update addresses a whopping 18 security holes in Flash Player and Adobe AIR. ”
Shouldn’t the number of vulnerabilities asymptotically approach zero as a product matures, or do they just keep adding new holes as time goes on? I sure hope Adobe’s primary income these days isn’t from McAfee Security Scan commissions from unsuspecting updaters… 😉
Thanks for the update info, Brian.
“Shouldn’t the number of vulnerabilities asymptotically approach zero as a product matures?”
Theoretically, if the core product stays the same, and all development changes were related to bug fixes, then yes.
But like other Adobe products, Flash is bloatware that has been expanded over the years to perform numerous different functions, most of which the average user doesn’t need in the first place. Why is a video playing plug-in almost 20MB? It’s like Adobe Reader, a PDF viewer that clocks in at almost 75MB, when something like Sumatra is literally 90% smaller. Bugs for these smaller products are not even remotely as common, certainly not 15 new ones every month.
Kurt Godel’s Incompleteness Theorem plus Alan Turing’s solution to the ‘halting problem’ may provide insight on the matter of whether or not fixes will ever improve matters beyond the specific issue the fix was intended to fix.
Actually Adobe is one of a few that has a good process in place to find issues and create patches. That’s probably why they are upfront most other vendors in this matter. Remember no patch is bad, not good. A complex product /system without patches released from time to time is too good to be true.
Anyway BSSIM describes the secure development process adopted by Adobe, Microsoft and some others. Worth a look at the document.
Or hell even if they had an updater that actually worked. Boggles my mind after this many flaws and years to fix it that they still haven’t figured out a way to let non-admin (ideal corporate user) get updates quickly and reliably.
” I sure hope Adobe’s primary income these days isn’t from McAfee Security Scan commissions from unsuspecting updaters… ;-)”
No, I think they make something off the Ask Jeeves toolbar they try to install too.
They must be so proud.
whac-whac-whac that mole
flash may be the No.1 vector for drive-by infections. I cleaned 337 infections off my daughter’s laptop yesterday that she depends on to do her online university schoolwork. her laptop is protected with a top rated a/v.
this virus stuff isn’t funny anymore. we need to start eliminating software that is virus prone.
my daughter had the noflash plug-in active on one browser but not her alternate. I corrected that.
Outdated anything is the #1 vector in my experience.
Very few things besides targeted phishing attacks utilize 0day exploits, but old exploits are used by every miscreant under the sun.
the problem with the Adobe AIR is that its factory installed on most systems and does not auto update (most are as old as 2009) AIR only updates when its opened via an app (and only if the app needs an updated version)
as bad as java that is generally never updated as well
“In this case, the buggy code is at least 19 years old”
Hmm, wasn’t there an outburst of pundits complaining about how insecure Open Source software is after the OpenSSL Heartbleed/etc vulnerabilities this year? About how the “many eyes” assumption was false?
…and yet here we are with a 19 YEAR OLD vulnerability in a commercial OS.
Pot, meet kettle 😉
The point was that open source software isn’t magically more secure than commercial software, as open source pundits have been claiming for decades. Nobody is claiming that commercial software is bug-free, we know perfectly well that it isn’t.
Chrome is already updating from 38.0.2125.111 m to 38.0.2125.122 m including the flash update.
and Adobe never seems to tell ya when there’s a new Shockwave Player issued either, well today there is. version 12.1.4.154
I just don’t get Adobe. Flash Player for most people has one job, to play video in the browser. It is very hard to understand how a product with such limit scope of use by the average user can have security flaw after flaw through more than 15 years of version iterations. Even if it ends up in the scrap heap as we move to HTML5 I really fear that HTML5 will be no better. People will still likely do stuff in their code that perverts what should be a basic and safe task – (Play video and allow no harm to the viewer)
That may be how certain users typically use Flash, but the product is far more capable than that very limited feature set.
That feature, the ability to play video in a web browser through the Flash plugin, was added quite late in Flash’s development. Flash was available for years before the video player was added. Since the video player was added they’ve added other non-video features to the product.
In fact, this attitude that Flash is solely used to play video content is rather annoying in certain circles. For instance, on PowerPC systems the main Firefox fork dropped all support for plugins. Their workaround for the lack of Flash is an extension that enables you to download video and play it through Quicktime. Yet when asked about all the other functionality that Flash provides there’s little more than crickets chirping.
Now, in that case I totally understand why Flash had to be nuked, since Adobe stopped updating the PPC port of Flash years ago, with many many many cross-platform vulnerabilities available for exploit – but that attitude (Flash is only for video) from someone who I would expect to be very knowledgeable is frustrating… and worrying.
SeymourB wrote:
In fact, this attitude that Flash is solely used to play video content is rather annoying in certain circles.
But that’s kind of the point – Flash has all these other capabilities and no one uses them. If no one uses them, they add no value to the product and are nothing more than an attack vector for the bad guys. Flash is an outdated video player that’s bloated with useless features that lead to security vulnerabilities. Sorry if that’s annoying in certain circles, but a spade is a spade.
If all of those features were all optional and turned off by default nobody would care either. But it is a monolithic steaming pile of software that doesn’t allow you to do something as advanced as that.
Thats complete and absolute nonsense, that the only function used in Flash is the video player. Have you been to a car company website lately on a computer that has Flash available? 9 times out of 10 entire site is built in Flash.
The problem isn’t that Flash is only used for video, its that certain people have a very limited exposure to the commercial uses of Flash and therefore they think their experience is the only experience. They keep hemselves on a very limited number of websites, so therefore all websites must be like the backwater sites they visit.
It’s like people who say there’s no need for antivirus on Windows because they’ve never gotten infected. 9 times out of 10 they’re infected and don’t realize it, but again, their use of the environment yields a very warped view of the environment.
“In fact, this attitude that Flash is solely used to play video content is rather annoying in certain circles.”
There’s an other circle that’s annoyed that Flash is used at all. I wonder which one is larger?
I suspect the “Flash is annoying” group is smaller than the “I use Linux as my desktop OS” group, which is very small numbers indeed (no matter how vocal a minority they are, they’re still very small).
@ SeymourB, yes admittedly my assessment of the scope of Flash was understated. I am familiar with the animation capabilities it lends to sites. For security reasons I’ve long abandoned the use of Flash and I manually enable it when needed on hopefully trustworthy sites to watch a video. I would really appreciate if there was a paired down version where it was a simple and secure video player. If I really want to view an auto sales website once a year I basically have to switch over to an alternate browser and just leave my system open to attack on the hope that an auto website can be trusted. I can understand the frustrations that must come from the developer side of the equation. I’d really like to see us get to the point where the browser is just a window to the outside world and the user could interact freely without any significant risk of the outside getting in. Choose to download a file, always a risk. Choose to run a program outside the browser, always a risk. Choose to share information with a site, always a risk. The typical behavior required to interact with the internet is a view-only experience with some user input; it should be possible to view complex engaging content without the outside world having any persistent exploitable attack surface.
I don’t want to see 99.8% of the videos that are pushed at me every time I go on the Internet. I have Flash set to “ask to activate”. My question is: am I still subject to Flash security vulnerabilities even if I’m not watching any videos or enjoying RIAs?
Whatever the hell an RIA is.
Thanks!
One of the updates has totally hosed IE11 on Win7 64-bit on 3 PCs at home.
If you are running EMET, you need to update to version 5.1 which came out today, since there is an incompatibility of the EAF+ mitigation with the new version of IE11.
Cheers for that! That seems to have done the trick.
A suggestion … I recently put the Microsoft Security Live Bookmark on my PC, which alerted me to the EMET 5.1 release a day or two ago. So it turns out that I implemented the EMET update before downloading the recent “Second Tuesday” release, and had no problems. I’m guessing that those without previous versions of EMET installed also had no problems???
Wish they would have single streamed the emet 5.1 before the IE 11, would have saved me a few moments of fixing stuff.
I had to back off KB3003057, then upgrade emet to 5.1 then put the IE fix back on. Emet would not let IE11 even load prior to the update.
At least it was easy to find the fix on tech-net. Wish I would have seen this post first.
A busy Microsoft Patch Tuesday, indeed
Just updated Adobe Flash, Adobe Air, and Shockwave. Video sound cuts off about 2 minutes into the video. Been going on for two months now. Windows 7, IE 11, Toshiba Satellite.
You could always look into whether an update is available for whatever you’re using to play audio. If it’s HDMI, then you typically need to update your video card drivers. If it’s a stereo miniplug then it’s your sound card/chipset.
I normally avoid PC OEM sites for driver updates, and instead go straight to the manufacturer of all the various chipsets (e.g. Realtek, AMD, NVidia) since most PC OEMs don’t release updates once the system is discontinued, and manufacturer drivers normally work perfectly fine.
This month’s batch went like last month’s batch for me (Win8.1 Pro, some Office 2010, and one Windows Home Server). Namely, on about 1 in 4 computers, the monthly Malicious Software Removal Tool stalled and had to be terminated, like last month.
If that trend continues, I’ll just unselect the MSRT; it’s redundant anyway, since the systems use Microsoft’s antimalware in the first place, and scan daily. On the systems that didn’t gag on the MSRT, the updates went smoothly in one shot.
I don’t believe that the Malicious Software Removal Tool is redundant. Unless something has changed, I believe that it’s designed to scan very specific/prevalent pieces of malware , directly after your computer reboots from that month’s updates.
Not sure that the “regular” Microsoft anti-malware includes those specific items in their normal scans. But I guess it’s possible.
Technically it runs a scan immediately upon installing MSRT, though any removals occur after a subsequent reboot.
Here is the list of malware families the MSRT targets:
http://www.microsoft.com/security/pc-security/malware-families.aspx
If you check a few of the families listed there, it looks like my surmise was correct… “Microsoft security software detects and removes this family of threats” is the common theme. In a scenario where my regular antivirus software had been disabled by malware, then perhaps the MSRT would have its moment in the spotlight (as long as the malware hadn’t disabled Windows Update as well).
That may indicate a deeper problem with those machines (or perhaps an incompatibility between MSRT and some third-party software you’re running). I don’t think it’s a common problem, though I could be wrong.
Those are logical suggestions. “A deeper problem” in the form of malware is pretty unlikely here. These are secured at considerable depth, including application whitelisting, and the configurations are standardized, primarily by Group Policy. I run a very tight ship in that regard. We don’t use much third-party software, and what we do use is common to all of them, with the exception of not all of them having Office.
Anyway, if there is a common denominator, I haven’t stumbled upon it yet. Next time around I’ll have a look at the Windows logs for clues; sometimes Software Restriction Policy will block an attempt to execute stuff with a user’s privileges from an unauthorized location, for example.
The application whitelisting and other security measures might actually be the cause of the problems with MSRT. It may not be very well tested for compatibility with a tightly locked down configuration. (If you have to choose one or the other, I’d drop MSRT in a heartbeat!)
Is it the same machines that fail each time around? It might just be a race condition of some kind, randomly failing a certain proportion of the time.
For the second time in 2 months, I had to stop installation of the updates because the Windows MSRT took too long. I’m gonna try to install all the other updates, instead.
Why do I need Adobe AIR running on my laptops? All I see from Adobe is that is lets people use RIAs, with no real explanation of what an RIA is.
What happens if I uninstall Adobe Air?
Worst case? One or more applications stop working, at which point you can reinstall it.
If none of the applications installed on your machine use AIR, you don’t need it.
Adobe Air disappeared from the list of FF add-ons after yesterday’s Flash update.
Hi Brian
For the last two update cycles of the flash add-in in IE 11, I did not have to do anything. It was automagically updated during those Win7 64bit updates. Is this a known feature?
I checked the version in the add-in manager in IE and there was always the latest version with a very recent update date/timestamp.
For FF I always have to do the update to get the latest version of flash plugin.
Yes, it is, he even wrote as much:
> IE10/IE11 on Windows 8.x and Chrome should auto-update their versions of Flash.
You should note that Oliver was asking about IE11 on Win7 64-bit not IE11 in Win8.
All updates, Adobe’s and MS’s installed easily and without incident. After installation all functions on the machine seem to be normal, using FF 32.03 & IE 11.0.9.
Sys: Lenovo; Intel multi-cpu; Win 7 pro x 64.
Hey Eaglewerks,
FYI – my (non-beta) Firefox just updated to 33.1…
Keeping up with the updates is as burdensome as keeping up with the Kardashians!
Yes, thanks. I have been ‘Decide Later’ clicking that FF update for a few days, LOL. Each one of the FF updates seems to change or delete or add a feature, and I haven’t had time to discern how the most recent FF update will effect the tweaks I have applied to the version I am currently using.
I used Flash’s regular update system, and wasn’t prompted to download any additional software this time.
hi
“Shouldn’t the number of vulnerabilities asymptotically approach zero as a product matures, or do they just keep adding new holes as time goes on?”
Well, yes, but for-profit developers (think MS) seem to be much more interested in coding new “eye candy” and pseudofeatuers than actually writing better code.
Think of Detroit and automobiles. They continued building junk until Japanese competition forced them to begin to upgrade… it’s capitalism, folks.
With the latest update, EMET 5.0 stopped IE 11 from running. Had to upgrade to EMET 5.1 to get the fix.
After updating my IE11 I get “Internet Explorer has stopped working.”
Any thoughts?
Brian – unless you remove postings like ‘Zeroday1’ and the like you will lose your interested readers
Thanks for the notes about spam in the comments, but I almost always get to them within in a few hours or a day. For how much spam this blog gets, you all would be amazed that there isn’t more of it here. As it is, I do my best to keep it clean.
Win Update running in background while Firefox and a couple of other internet-enabled applications were running:
Win 7 Home Premium 64 bit, no AV realtime monitor running, MSAM tool installed, dotNet 3 and 4 latest editions installed, but nothing using them at the time.
Win Update client advised *before the usual reboot prompt* that ‘one of the updates’ had failed because it needed access to system files that were in use’. Update number not specified.
In a few years of admining a home network I’ve never had this kind of notice from Win Update *before restart*.
At restart, the failed update was re-notified as ready to download in the usual growl-style toolbar slider.
It was 3003743.
Large file for anything other than the browser – – it was 5+Mb.
I noted that the rather opaque and vague description of the update (s0me fix for Remote Desktop) included a reference that there was no registry entry for verifying the completion of the update.
So I’m guessing that there would be quite some few systems where the precise configuration running at the time precluded the whole of that 5+Mb getting installed in the session -hence the number of failing installs getting reported.
After all those years complaining about the messy and bloated Win Registry, I never thought I’d hear myself say I feel quite unprotected when an update declares it won’t self-verify via the Registry.
What a laugh!
Registry verification is weak; it just means that the update thinks it completed successfully, which doesn’t necessarily mean that it did. The best way to confirm that updates have installed successfully is to get Windows Update to check for new updates after you’ve rebooted.
The behaviour you describe isn’t particularly rare, I’ve seen it quite a few times. My guess is that sometimes two updates can interfere with one another. The failed update will usually either install successfully after the next reboot, or turn out to be no longer needed.
Thanks for the background there Harry Johnston; Win Update has indeed always done the right job over failed/missed updates here, so I can now go back to grumbling over the Registry 🙂