A number of readers have complained recently about having their Hilton Honors loyalty accounts emptied by cybercrooks. This type of fraud often catches consumers off-guard, but the truth is that the recent spike in fraud against Hilton Honors members is part of a larger trend that’s been worsening for years as more companies offer rewards programs.
 Many companies give customers the ability to earn “loyalty” or “award” points and miles that can be used to book travel, buy goods and services online, or redeemed for cash. Unfortunately, the online accounts used to manage these reward programs tend to be less secured by both consumers and the companies that operate them, and increasingly cyber thieves are swooping in to take advantage.
Many companies give customers the ability to earn “loyalty” or “award” points and miles that can be used to book travel, buy goods and services online, or redeemed for cash. Unfortunately, the online accounts used to manage these reward programs tend to be less secured by both consumers and the companies that operate them, and increasingly cyber thieves are swooping in to take advantage.
Brendan Brothers, a frequent traveler from St. John’s in Newfoundland, Canada, discovered a few days ago that his Hilton Honors account had been relieved of more than a quarter-million points, rewards that he’d accumulated using a credit card associated with the account. Brothers said the fraudsters were brazen in their theft, using his account to redeem a half-dozen hotel stays in the last week of September, booking rooms all along the East Coast of the United States, from Atlanta, GA to Charlotte, N.C. all the way up to Stamford, CT.
The thieves reserved rooms at more affordable Hilton properties, probably to make the points stretch further, Brothers said. When they exhausted his points, they used the corporate credit card that was already associated with the account to purchase additional points.
“They got into the account and of course the first thing they did was change my primary and secondary email accounts, so that neither me nor my travel agent were getting notifications about new travel bookings,” said Brothers, co-founder of Verafin, a Canadian software security firm that focuses on anti-money laundering and fraud detection.
Brothers said he plans to dispute the credit card charges, but he’s unsure what will happen with his purloined points; nearly a week after he complained to Hilton about the fraud, Brothers has yet to receive a response from the company. Hilton also did not respond to requests for comment from KrebsOnSecurity.
PUT A PIN IN IT
Hilton gives users two ways to log into accounts: With a user name and password, or a member number and a 4-digit PIN. What could go wrong here? Judging from changes that Hilton made recently to its login process, thieves have been breaking into Hilton Honors accounts using the latter method. According to the travel loyalty Web site LoyaltyLobby, Hilton recently added a CAPTCHA to its login process, ostensibly to make it more difficult for crooks to use brute-forcing programs (or botnets) to automate the guessing of PINs associated with member accounts.
In a post on October 30, LoyaltyLobby’s John Ollila wrote about a hacker selling Hilton Honors accounts for a tiny fraction of the real world value of points in those accounts. For example, the points stolen from Brothers would have fetched around USD $12 — even though the thieves in his case managed to redeem the stolen miles for approximately USD $1,200 worth of hotel reservations.
I did a bit of sleuthing on my own and was able to find plenty of sellers on shady forums offering them for about three to five percent of their actual value. As this ad from the online black market/drug bazaar known as Evolution Market indicates, the points can be redeemed for gift cards (as good as cash) at points.com and other locations that convert points to currency. The points also can be used to buy items from the Hilton shopping mall, including golf clubs, watches, Apple products and other electronics.
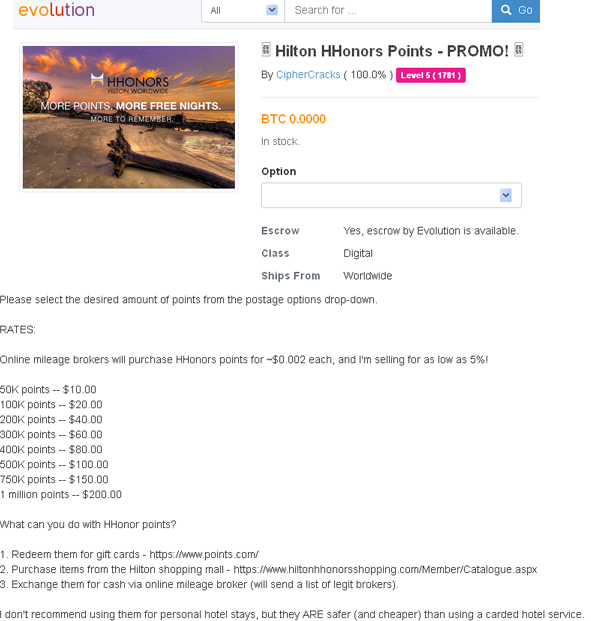
A merchant on the Evolution black market hawking hijacked Hilton points for a fraction of their value.
“I don’t recommend using them for personal hotel stays, but they ARE safer (and cheaper) than using a carded hotel service,” the Evolution seller advises, referring to the risks associated with using purloined points versus trying to book a stay somewhere using a stolen credit card.
Hilton Honors is hardly alone in allowing logins via account numbers and 4-digit PINs; United Airlines is another big name company that lets customers log in to view, spend and transfer points balances with little more than a member number and a PIN. These companies should offer their customers additional security options, such as the ability to secure accounts with multi-factor authentication (e.g. via Security Keys or Google’s Authenticator mobile app).
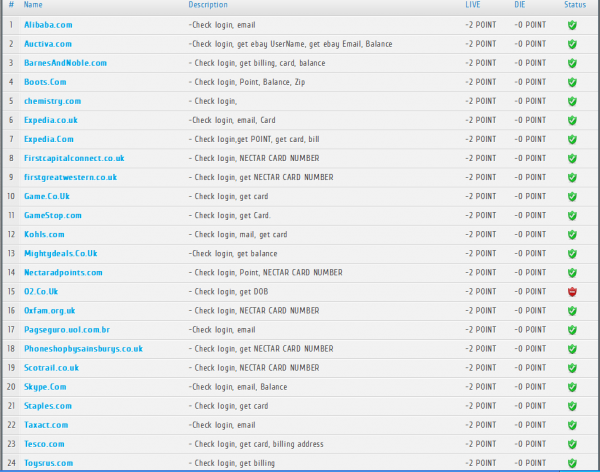
If it wasn’t already painfully obvious that a lot of companies and their customers could benefit from adding multi-factor authentication, check out the screen shot below, which shows an underground site that offers automated account checking tools for more than two-dozen retail destinations online. Some of these tools will help streamline the process of dumping available awards and points to a prepaid card.
Stolen points and miles would be a great way to fund a criminal-friendly travel agency. By the way, that’s actually a thing: Check out this story about services in the underground that will book stolen flights and hotels rooms for a fraction of their actual cost.




Good article, Brian! Let’s not forget with the proliferation of rewards accounts, that everyone has multitudes of these and tend to re-use the same password. One account breach and voila!
“check out the screen shot below, which shows an underground site that offers automated account checking tools for more than two-dozen retail destinations online. Some of these tools will help streamline the process of dumping available awards and points to a prepaid card.”
Hi Brian,
Do these tools test from harvested credentials from malware infections and successful phishing emails?
The tools in the screen shot are made to test large lists of credentials. So, yes, credential lists culled from phishing attacks or botnet logs would probably be the most common form of data input into these checking services.
Personally I SQL inject databases to grab thousands to hundreds of thousands email/pass combo’s. You can generally rely on a hit rate of about 2-5% being valid Email Logins, depending on the relative age of the databases entries, and the demographic that the website is frequented by.
Also common is for the Passwords themselves to contain conspicuous 4 digit strings nestled within – awfully convenient for harvesting points accounts. Anyone care to take a stab on the chances of this being their ATM PIN also?
Probably about 90 to 95 percent.
Yes, good point I overlooked about SQL injection as indeed do quite a few website developers.
Yes PIN reuse I would imagine is pretty high.
Its horrifying how many Sites still store Passwords in plain text. But even hashing and salting is futile when faced with the sheer bruteforcing strength of a consumer graphics card, a copy of oclhashcat and the devastatingly effective rockyou.txt wordlist.
SQLi is without a doubt the largest threat to your login credentials that exists on the web. And there’s nothing you can do to prevent it from happening.
that’s the combination to my luggage!
Why do you always make it seem like this is some blackmarket underground thing? You can download sentry mba in hundreds of places which is a free cracking software and download configs for just about any site on multiple sites that are hosted in us, gb, canada, etc.
tldr; this isn’t some blackmarket fraud it’s happening on hundreds of clearnet sites.
agreed lsx has threads full of this
I have long histories with both United and Hilton rewards plans. Both of those accounts are set up with user IDs and complex passwords. While I could have left at the default, I chose not to.
One can argue the companies should require more robust log in credentials. as we are talking about things with value, but there should also be some onus on the end user. Any account with which you have a credit card associated, you should take steps to protect the card as well as you can.
Totally agree, we all need to take responsibility to use a secure password. However, I’m not seeing a way with either Hilton or United to disable to PIN based login method. Limits the value of a very secure password it the 4 digit pin login cannot be disabled. Anyone sees a way to do this please speak up!
Even if prepaid with points, checking into the hotel very likely still requires a CC and ID. Do you know how the criminals get “money” out of this? Actually spending a couple nights in a hotel in the US after paying for it with traceable stolen funds sounds like a fast-track to soon earn hospitality points in jail?
From what Brian was saying it would appear that they redeem many of the points for goods, such as golf clubs, then sell those for a profit. Some rewards can be traded in for gift cards that are virtually untraceable.
I get that part. But the original story says “The thieves reserved rooms at more affordable Hilton properties”. Room reservations don’t strike me as a loot that can easily be fenced?
Why not steal a vacation to someplace warm in the winter? Many criminals like to make it a hobby to never pay for anything if they can help it.
Also, If you have a job to do somewhere out of town, I’d imagine this is safer than using a stolen card (as mentioned) or using your own card (easier to trace later).
Why on earth would the changing of the email accounts by the criminals not send an email to the original accounts stating that the contact info had been changed? Almost every site I have used has some from of notice that your contact email changed and to click a link or call if it did not. Shame on hilton for not having such a system in place if that is indeed the case and not something that may have been overlooked by Brothers and his travel agent.
To be fair the majority of these sites were developed when the internet was a more innocent place, and largely escaped the arms race between hackers and financial service providers that occurred in the last 5 years.
The hackers, battle-hardened, trained and resourceful, turned attention to less fortified systems that were ill-equipped to deal with this. It doesn’t excuse the websites from being so slow to act to the increased threat, but it does offer an explanation.
Low hanging fruit eh?
I guess also to say a 1960s Mustang was developed in the 60s but it doesnt mean I cant put a bigger engine in it for better performance and disc brakes all around to make it safer. I guess my point is that companies need to get with the times and not rely on older technologies or security through obscurity anymore and it becomes painfully obvious when they goof up now more than ever.
but you can’t retrofit your 1960’s mustang with 00’s era passive security features
Sure you can. It’s just a shell, you can stick whatever you want inside. There is a substantial cost to doing so, since you’re doing a ground-up build instead of just tacking features onto the existing infrastructure.
This is why companies haven’t bothered to update their systems, despite the obvious risks – it would require a large expense to implement reasonable security. It’s far more important that companies give their executives large bonuses and raises, otherwise how ever will they retain their executives (who often do little worthwhile except receive large bonuses and raises).
The best part of this article is the link back to the conversation between Brain and the guys running a site he used to show the activity. Gosh I miss those lippy Russians and their silly threats. Whatever happened to “I’ve got a 500k bot army ready to conquer your web presence?”
Always good for chortle.
It seems to me that these type of websites needs to move towards better online security measures like using two factor authentication with a users cell phone.
Very good article , by the way.
Interesting. I just visited the site to see if I’ve been compromised. Although I rarely stay at Hilton’s anymore, I know I have some points accumulated. Would hate to lose them. In any event, the site is now reading “Customer Profiles are Unavailable. Due to technical issues we cannot access your customer profile right now.”
So, I called and got through to the HHonors customer service desk and confirmed that my points were still there. However, she had no idea why I would not be able to get to the portal. My call was the first she had heard about exploit. She was aware of the exploit, however, and indicated that the Captcha was implemented as a response.
Interestingly, I can use their 800 number with my Hhonors account number and PIN to get in and do all sorts of mischief to my account. This is quite disheartening.
Airmiles rewards are also using a simple four-digit code here in Canada – no captcha either. Simply amazing how simple they make things for those with bad intentions!
Delta in the US is in the process of switching over to passwords only and phasing out PINs. Don’t know about other airlines or countries.
Until recently USPS employee personnel accounts were available by on line access with only a four digit PIN and employee ID #. These accounts contained scans of all employee related documents including original employment application with SS# work and address histories etc. Fortunately the USPS recently changed to password protection. Seems that rewards sites are not the only sites that still “protect” with PIN numbers.
“United Airlines is another…”. People still fly with them? You know they break guitars.
KLM, the Royal Dutch Airlines, also has only a 6-digit PIN on its loyalty account website. And they even suggest to use only 4 digits.
I tried to contact someone responsible, but the only reply I got was of the kind “we take security very seriously”.
When would they realise that their strategy is completely stuped in a scenario where their password database gets stolen? One even might start to wonder whether they even have bothered to hash the PINs….
You leave your points in these accounts too long or fail to visit their hotels after a certain period of time and you discover Hilton steals the points back.
Great article Brian. On the screen shot of the automated account checking tools, what do the column headers “Live” and “Die” refer to?
thanks, Dan. They’re just the site owner’s way of saying whether the credentials are active or dead.
I received an email from Capital One last night that my email address and password had been changed, something I hadn’t done. Someone had obtained access to my Capital One credit card and stolen 235,000 points by requesting Best Buy gift certificates which they received to print via email. Capital One is going to restore my points but I checked online to see if I could find any other reports of reward point theft. This was the only post I came upon. Not sure if this is a new thing or not. The woman I spoke with in Capital One rewards told me it was the second issue like mine she’d had I a few hours. The lack of security that permitted someone to take over my account alarms me.