If you receive an email this holiday season asking you to “confirm” an online e-commerce order or package shipment, please resist the urge to click the included link or attachment: Malware purveyors and spammers are blasting these missives by the millions each day in a bid to trick people into giving up control over their computers and identities.
Seasonal scams like these are a perennial scourge of the holidays, mainly because the methods they employ are reliably successful. Crooks understand that it’s easier to catch would-be victims off-guard during the holidays. This goes even for people who generally know better than to click on links and attachments in emails that spoof trusted brands and retailers, because this is a time of year when many people are intensely focused on making sure their online orders arrive before Dec. 25.
According to Malcovery, a company that closely tracks email-based malware attacks, these phony “order confirmation” spam campaigns began around Thanksgiving, and use both booby-trapped links and attached files in a bid to infect recipients’ Windows PCs with the malware that powers the Asprox spam botnet.
Asprox is a nasty Trojan that harvests email credentials and other passwords from infected machines, turns the host into a zombie for relaying junk email (such as the pharmaceutical spam detailed in my new book Spam Nation), and perpetuates additional Asprox malware attacks. Asprox also deploys a scanning module that forces hacked PCs to scan websites for vulnerabilities that can be used to hack the sites and foist malware on visitors to that site. For an exhaustive and fairly recent analysis of Asprox, see this writeup (PDF) from Trend Micro.
Malcovery notes that the Asprox spam emails use a variety of subject lines, including “Acknowledgment of Order,” “Order Confirmation,” “Order Status,” “Thank you for buying from [insert merchant name here]”, and a “Thank you for your order.”
If you receive an email from a recognized brand that references an issue with an online or in-store order and you think it might be legitimate, do not click the embedded links or attachment. Instead, open up a Web browser and visit the merchant site in question. Generally speaking, legitimate communications about order issues will reference an order number and/or some other data points specific to the transaction — information that can be used to look up the order status at the merchant’s Web site. I know I’m probably preaching to the choir for the loyal readers of this site, but I’m sure most of you have friends and relatives who could use a reminder about all of this. Please feel free to forward them a link to this story.



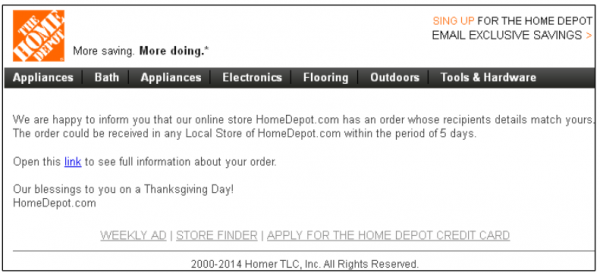
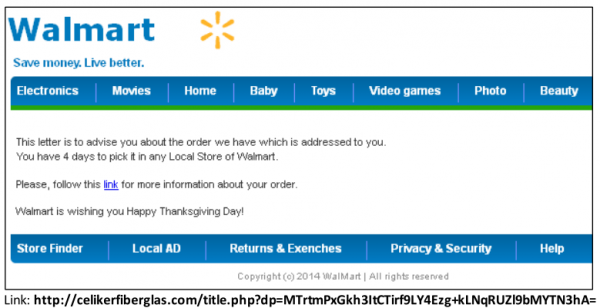
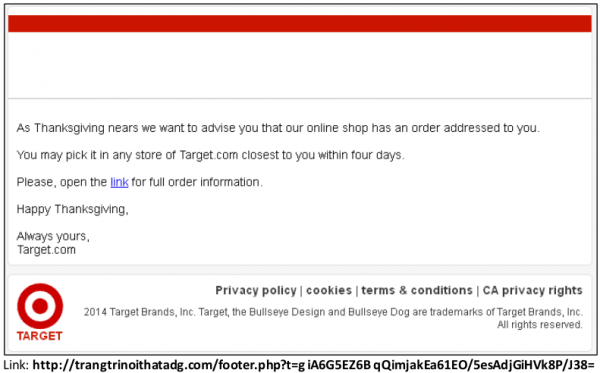
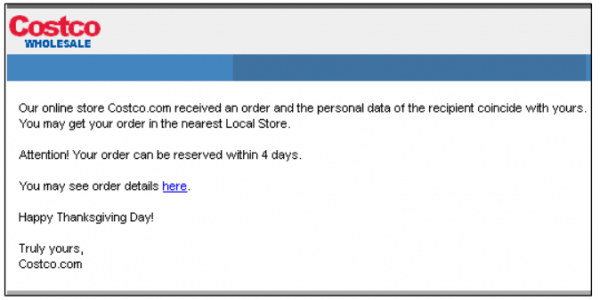

Got this kind of emails almost every day, which all of their techniques. 🙂
Usually being sent to sales@, info@, or other generic email addresses.
Perhaps using one unique email address for every online account is better option, but it give hassle creating it one by one. 🙁
I noticed that some say you can pick up your order at “any local store.” I would expect an order to be shipped to one particular store.
It appears the crooks aren’t as smart as they think they are.
I also received a similar email from Fed Ex that looks like this: http://goo.gl/ZyedNl
The email claims that it missed delivery and you need to claim your package. This might get a few people considering all of the Holiday gift buying and traveling.
Ditto on this. My ‘Junk’ e-mail folder is loaded with these types of messages. FedEx, USPS, UPS, etc…
I can see how people would be fooled by this, even though the evidence that it’s a fraud is readily apparent (FedEx’s domain isn’t zenith-kyoto.co.jp).
Is that a booby trapped link?
Every one of the examples contains odd English that is pretty easily identifiable as such. The scammers need to “offshore” some help from North America to generate the text.
Knowing the kinds of people they’d attract, the grammar would probably get worse. Have you read comments on YouTube lately?
Unfortunately they will continue to improve their grammar and ability to make these emails look more authentic. It will only make things worse.
Hey, at least if you’re pretending to be Target.com, put :
Truly Yours,
#AlexFromTarget
Those messages are so vague! A real emailed receipt would include an order number and a list of items purchased.
Not 2 hours after reading this, my inbox loaded the COSTCO email. I sent links to this article to all my family.
Thanks,
Joe
Alas, even hovering over the link to doublecheck the address is vulnerable to phishing deception, officially known as an “IDN homograph attack” or Unicode URL hack. See:
IDN homograph attack – Wikipedia, the free encyclopedia http://en.wikipedia.org/wiki/IDN_homograph_attack
PayPal vs Fake PayPal: Can You Tell the Difference? [PIC] http://mashable.com/2010/01/01/idn-phishing/
Schneier on Security: Unicode URL Hack https://www.schneier.com/blog/archives/2005/02/unicode_url_hac_1.html
FAQ – Security Issues http://www.unicode.org/faq/security.html
Apparently, the only way to be TOTALLY SURE it’s the REAL site is if you type the letters yourself… And, you don’t even know if the links above are real or phished! 😉
The day your newsletter came out about these types of spoofed emails, I got 2 from Amazon. I notified their security department, who acknowledged that it was NOT from Amazon. But they don’t comment on any investigative process involving their company.
The emails purportedly from Amazon (whom I order from very frequently) were using my old Amazon account name, and said that I was going to get a 40″ Samsung TV delivered to my address. It was simply a typical Amazon order confirmation, but I observed it was from a non-Amazon email address with a .net domain.
I noticed that there were many clickable meta-tags throughout the document.
As you pointed out in your excellent article, it is best not to click on any of them.
Alas, even hovering over a link to doublecheck the URL address is vulnerable to phishing deception, officially known as an “IDN homograph attack” or Unicode URL hack. (I’ll put some links below, but maybe you shouldn’t click on them, either? 😉
IDN homograph attack – Wikipedia, the free encyclopedia http://en.wikipedia.org/wiki/IDN_homograph_attack
PayPal vs Fake PayPal: Can You Tell the Difference? [PIC] http://mashable.com/2010/01/01/idn-phishing/
Schneier on Security: Unicode URL Hack https://www.schneier.com/blog/archives/2005/02/unicode_url_hac_1.html
FAQ – Security Issues http://www.unicode.org/faq/security.html
Apparently, the only way to be TOTALLY SURE it’s the REAL site is to NEVER click on the embedded links and type the letters yourself… I sure wish society didn’t have evil-doers scamming the Internet!
While the best practice is to not fall for any of these scam messages, a backup effort can be to pin the System Restore to your Start Menu and create a Restore Point every morning before you touch the browser. Takes less than a minute. Then if anything untowards happens all you do is revert the system to that morning…
Sandboxie or a similar sandbox program is excellent for opening suspect packages…this program can protect browser and email programs ..I definitely do not trust anti virus software to do the job..
Hotmail does a great job of filtering spam ..hardly any arrives in the Inbox …junk folder has a lot, but I never open these.
I foolishly just clicked on one of the links in the fake Target email on my iPhone… Why should I do?? Nothing seems to be going awry yet…
Excuse the error– I meant to ask what should I do?
I did this, too, from my computer. I clicked the ‘link’ and a new webpage opened up but it was taking a bit to load – I closed the tab before the page could load. I’m hoping I closed before any damage was done. I was thinking my husband ordered something I wasn’t aware of – at the last second it occurred to me it stated ‘with Thanksgiving approaching.’ Well, it’s Dec. 10. At this moment, I hate myself.
I received a similar email from “Best Buy”. I tried numerous calls to BB to get clarification. BB was totally frustrating to try to get to any person other than a floor salesperson. In one case the store operator would not give me her name. We got disconnected. Tried to call back and couldn’t get an answer. Tried on my cell phone and immediately got through. Connected to floor salesperson and was told to speak to the Geek Squad. Dead end. Clicked on “Download” and couldn’t download. Called iYogi and they couldn’t get anything. Hope I didn’t screw up. DON’T RELY ON BEST BUY FOR ASSISTANCE ON ANYTHING!!!
Texts are coming to my phone saying that a Walmart order is ready for pickup, which says to reply a particular string of characters to find out which store to pick the order up at. Another order pickup text saying “see email”. A third text saying “You will now receive pickup alerts for Walmart” “reply STOP to opt out”. All obvious scams since I haven’t placed any Walmart orders for store delivery.
Aha, I love those emails. The best is when they send the email, but the image header for example Walmart shows up as Target yet it’s a walmart email, amirite?
Opened an WalMart email and then the link which went to a blank page. I see that others have done the same and have asked “what do we do now? I also need advise of any steps that should be taken now that the cat’s out of the bag.
Hello,
here is available list of C2 servers of the Asprox botnet with the status:
http://atrack.h3x.eu
I also received one from Walgreens
Make another thing for the community