A gaggle of young misfits that has long tried to silence this Web site now is taking credit for preventing millions of users from playing Sony Playstation and Microsoft Xbox Live games this holiday season.
The group, which calls itself LizardSquad, started attacking the gaming networks on or around Christmas Day. Various statements posted by self-described LizardSquad members on their open online chat forum — chat.lizardpatrol.com — suggest that these misguided individuals launched the attack for no other reason than because they thought it would be amusing to annoy and disappoint people who received new Xbox and Playstation consoles as holiday gifts.
Such assaults, known as distributed denial-of-service (DDoS) attacks — harness the Internet connectivity of many hacked or misconfigured systems so that those systems are forced to simultaneously flood a target network with junk internet traffic. The goal, of course, is to prevent legitimate visitors from being able to load the site or or use the service under attack.
It’s unfortunate that some companies which specialize in DDoS protection services have chosen to promote their products by categorizing these latest attacks as “herculean” and “sophisticated;” these adjectives describe neither the attackers nor their attacks. The sad truth is that these attacks take advantage of compromised and misconfigured systems online, and there are tens of millions of these systems that can be freely leveraged to launch such attacks. What’s more, the tools and instructions for launching such assaults are widely available.
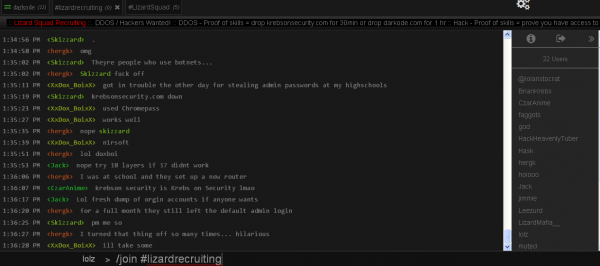
The LizardSquad leadership is closely tied to a cybercrime forum called Darkode[dot]com, a network of ne’er-do-wells that I have written about extensively. So much so, in fact, that the LizardSquad has made attacking KrebsOnSecurity.com and keeping it offline for at least 30 minutes a prerequisite “proof of skills” for any new members who wish to join their ranks (see the screen shot below).
Over the past month, KrebsOnSecurity.com has been the target of multiple such attacks each day. Prolexic — a DDoS protection firm now owned by Akamai — has been extremely helpful in poring over huge troves of data about systems seen attacking this site.
The majority of compromised systems being used to attack my site this month are located within three countries — Taiwan, India, and Vietnam. The bulk of attacks have been so-called “Layer 7” assaults — in that they try to mimic legitimate Web browsing activity in a bid to avoid detection.
But what’s most interesting about these compromised and/or misconfigured systems is how many of them are located at legitimate companies that have been compromised by miscreants. According to Akamai, most of the malicious sources were Windows-based servers powered by Microsoft’s IIS Web server technology. The top five industries where those compromised systems reside are in entertainment, banking, hosting providers, software-as-a-service providers, and consulting services.
Many of those associated with LizardSquad are wannabe hackers with zero skill and a desire to be connected to something interesting and fun. Unfortunately, many of the LizardSquad individuals involved in these attacks also are embroiled in far more serious online crimes — including identity theft, malware distribution, spam and credit card fraud. While most of the group’s acolytes are known to U.S. enforcement investigators, many are minors, and the sad truth is that federal prosecutors don’t really know what to do with underage felons except to turn them into informants. Meanwhile, the cycle of abuse continues.
Update, Dec. 30, 7:05 p.m. ET: A previous version of this story named multiple companies suspected of hosting compromised systems that may have been abused by LizardSquad members in attacks on this blog. Several of those organizations have reported being unable to find any evidence that their systems were used in an attack, and took strong exception to be included in this story. Since it is entirely possible that the traffic from these systems recorded in this site’s logs could have been mistaken for attack traffic during an active (and still ongoing) attack, I have omitted the names of those companies from this post. I would like to apologize for any confusion or misunderstanding this post may have caused.




Thank you, thank you, thank you for not calling them hackers.
What they did was mildly annoying. What the media did by treating them as anything more than script kiddies was the true annoyance.
It’s disappointing that it took so long for Sony and Microsoft to respond. I’m sure both companies have plenty of tools in place to mitigate such attacks. (I’m ignoring lizard squad’s claims that Microsoft has no security in place, as that’s patently absurd and am obvious attempt at trolling.) Hopefully they’ll do a better job in the future of responding during holidays.
First, thanks to BK as always for the great article. I was finding it hard to get details on what type of DDOS attack it was.
Second, I wanted to comment on some of the other comments people have made. I’m a senior network engineer for a company of similar size to Microsoft / Sony. Whenever something like this happens everyone gets on sites like this and comments about how the “stupid” companies should go about fixing things. I admit…it’s a pet peeve. Not trying to offend anyone, but here are some of the problems with the things that have been suggested so far.
Mark – “On dailydot.com they claim this attack is using cabling and routers for 1.2Tbps. These ISPs are morons for not noticing this traffic on their network”
You’re thinking of ISPs like a home or small business would. Corporations like Sony and Microsoft usually don’t use ISPs–they ARE the ISP. I don’t know that for sure for these two companies, but in most cases global Enterprise networks have their own fiber and peer directly with global backbones. They have very little reliance on third party networks like ISPs. Usually just for backup circuits and the like. And the job of the global backbone providers is not to monitor traffic to see if it’s malicious. That’s literally impossible with current technology. The Snowden leaks show that even the NSA couldn’t pull that off. Even if they could do it we wouldn’t want them to. Talk about privacy issues….
Tim – “As a consultant, I love the fact that consumers can now purchase large amounts of upstream bandwidth. What I cannot understand is why said bandwidth is available by default. I mean seriously, you average home user has no need for anything more than 3-5Mbps upstream…Leave the potential to have the upstream bandwidth in the service contacts, but keep it throttled by default.”
Home users don’t have 100Mbps of upstream bandwidth. They have the ability to burst up to 100Mbps (or whatever the ISP is providing them). It’s called over subscription. Getting 100Mbps DEDICATED bandwidth is quite expensive. Metroethernet has brought the cost down but it’s still probably $1k+ a month if not more. With that said, throttling bandwidth for end users has very little, if any, effect on modern DDOS attacks. Bandwidth-based attacks like DNS amplification typically don’t max out the bandwidth of the unknowing participants of the attack.
Tim – “DDoS is caused by packets sent, not packets requested.”
Not quite true. Depends on the type of DDOS attack. Sounds like you’re thinking of DNS amplification (which would use unsecured DNS servers, not your mom’s computer). Either way, if this was a layer 7 attack then the bandwidth is largely irrelevant.
Boris – “I do think more IT consultants/MSP’s should take the extra time and configure firewalls/routers with features that watch and regulate broadcast storms alerts for irregular upload and download activities based on report for that business average activity”
Not to nitpick, but broadcast storms have nothing to do with anything being discussed here. That’s a layer 2 issue. I do agree with you that IT consultants have a responsibility to properly configure firewalls, routers, IDS/IPS, etc. Assuming the company is willing to pay for it. Unfortunately most aren’t. They think “it’ll never happen to them” so they send the consultant on their merry way as soon as they suggest dumping a few hundred thousand USD into devices the company doesn’t think they need.
Tim – “That’s when in dawned on me that the solution is so simple it is ridiculous. Sony has the MAC Address for the on-board NIC and the on-board Wi-Fi NIC. In order for all of the Peer-to-Peer and network enabled features to work, you have to forward a number of ports to your device, so for most users, the device’s MAC address is already exposed. Why not maintain a MAC ACL for all of their manufactured devices that protects access to core services. Users connecting to their account on the website or mobile phone will have to connect via reverse proxy and Sony could implement MAC Address tracking via cookies, etc just like your bank…Can the DDoS’ers MAC spoof?”
No offense, but it sounds like you’re just stringing a bunch of buzz words together without understanding how they relate. First, MAC addresses are only for your local LAN. They’re never transmitted over the Internet (unless you’re going to get into VPNs, tunneling, etc, but that’s not the point here). Second, port forwarding does not expose the MAC address of anything on your LAN. Only your router knows the MAC address of devices behind it. Third, DDOS attacks don’t spoof MAC addresses. DNS amplification uses spoofed IPs, not MACs. MAC address spoofing is typically used for sniffing traffic on a switched wired network (CAM table overflow) or breaking into wireless networks that are using MAC filtering (which you should never rely on by the way, it’s trivial to crack).
Achbed – “If ISPs would simply stop accepting packets for transit that contain a source address could not have possibly come from that port, we would be much better off as spoofing becomes instantly harder.”
As commented above that’s not as easy as it sounds. However, I do agree that RPF should be more widely implemented where possible.
Jerry – “The blame needs to be put on the ISPs and corporate entities for allowing this traffic. The ISPs should be moniring for and stopping these attacks, and the corporations should be implementing better security.”
Corporations, yes. ISPs, no. As was said above, corporations the size of Microsoft and Sony usually are their own ISP. Even if they aren’t, it’s not the job of the ISP to stop this sort of thing. As a matter of fact, that’s the exact OPPOSITE of what we want. Do you really want worldwide ISPs to be doing deep packet inspection on all of your traffic? Your banking, text messages, VOIP calls, etc? No? Didn’t think so.
Jerry – “Actions like this can always be traced to their roots, given access to all necessary logs. It is just a matter or time before one in the group gets caught, then the rest will follow.”
Actually they can’t always be traced. The US, Brits, and Chinese have all spent enormous amounts of time and money trying to trace the origin of traffic being sent through TOR or similar services. They’ve had very limited success even with their practically unlimited resources. The kids probably will be caught, but it’ll be because they mess up. Generally they make a technical error and leak their real identity (IP, email, etc) or they just get cocky and brag to the wrong person. BK has exposed several hackers because they use their real name or email somewhere. It’s amazing how stupid that smart people can be.
Tim – “Interestingly, greater and faster adoption of IPv6 will solve many of the problems for the Internet of Things.”
Quite true. People tend to focus on the # of IPv6 addresses and forget about the other benefits. Adoption of IPv6 will have enormous positive benefits. Built in IPSEC, etc. Unfortunately it will probably be a long, long time before it’s adopted globally. Too many people are relying on NAT as a security mechanism. In the long term IPv6 is the right solution. In the short term it would cause a drastic change in the way both users and corporations have to handle network security.
One final comment on MACs: They ONLY apply to the local LAN. They’re never transmitted over the Internet. Also, they only apply to certain types of media. Ethernet, WiFi, ATM, etc. MAC addresses are just one form of layer 2 addressing. Other types of media don’t know or care about MAC addresses, and they certainly don’t know or care about YOUR MAC address unless they’re directly connected to you.
Again, not trying to be an arrogant jerk here, but I do hope that this post has helped some people. I’m a network engineer so I have very little to say about layer 7 attacks. I usually deal with layer 3 and below. But I do know that the solution to them is not easy and it’s certainly not anything that was suggested here. DDOS mitigation for all layers is hard and requires a multi-layered approach. You don’t just flip a switch and fix it.
Great post. Thanks for taking the time to write that.
I was not implying that the MAC is part of the TCP/IP packet structure. I was implying that the capability is there, in this scenario, to utilize this extra piece of information as part of the communication authentication process. It could be easily added to the payload of the auth packets. They have the MAC of all of the devices that they manufactured. They already have the information required to build a functional access control list that functions similarly to on-LAN network devices. My device’s hardware profile is attached to my account when I register the device. My device is actively listening for inbound connections and reports status to the vendor in demand. Sony/Microsoft are perfectly capable of restricting access to core services to only known and registered devices. Any unknown client connection originating from a PC, server or mobile device would be denied access by default and have to connect via offloaded / proxied authentication. This would keep legitimate consoles online. The DDoS’ers aren’t attacking from game consoles, so the would be directed to separate Layer 7 authentication services. If they want to take down the proxy servers, then have at it. We won’t be able to connect from web browsers, but the consoles will still function.
Again, not a concept aimed at the problem as a whole. That is pretty clear given that MAC is not included in a TCP/IP packet. It is a solution aimed at this particular problem.
I hit submit by accident on the previous response by accident 😉
“Do you really want worldwide ISPs to be doing deep packet inspection on all of your traffic? Your banking, text messages, VOIP calls, etc? No? Didn’t think so.”
Contrary: Yes, I do! Inspect. Block KNOWN maliciousness. “Don’t humanly read.” It’s not snooping, it’s machine inspecting and machine blocking–once the blocklist is implemented by humans the human not snooping and see nothing else.
Well, if everyone was honest, that would work, untouched by human ears, but the whole point is that they aren’t. ;^)
It’s really not that hard: Put some “honest”/good people in place, we’ve already got some–running networks like Sprint, AT&T, etc.
“It’s really not that hard: Put some “honest”/good people in place, we’ve already got some–running networks like Sprint, AT&T, etc.”
Even if that were actually possible, the issue is that once they had the capability to inspect it, less scrupulous people could make requests for it. Surely, you’ve seen the types of the requests the three-letter agencies already make of the telcos? Why make it even easier to obtain data they don’t need to have, and which will not automatically stop many kinds of DDoS attacks, anyway?
Disagree:
I’d prefer a three-letter agency over what’s happening now. I’ll take three-letter agency control vs malicious packets (from LizardSquad, etc) traveling from known malicious locations; I don’t trust LizardSquad. No three-letter agency was involved in these DDOSs (and never to my knowledge); it’s malicious packets that no one is controlling. I disagree with giving LizardSquad (etc) free reign of the global internet “highway” infrustructure.
It’s somewhat similar to the open interstate highway system–it’s not without highway patrolers.
As far as I know highway patrollers are not checking every trunk and inspecting every traveler…
blbu, still overall, I’m not referring to human eyes on traffic or even aware of what data is flowing. I’m referring to inspection by digital systems–blocklisting is implementing inspection criteria and blocking known badness (my first response to Rufus said this).
It’s done at some companies now.
I posted another version of this earlier, but it seems to have been moderated out. Admittedly, I was a bit aggressive in my initial response, so I’m assuming BK gave me the thumbs down. I toned it down this time. Lol!
I disagree with a number of your points, but the disagreement is rooted in context, not knowledge or content.
First of all, my mother lives in Seattle and she has a 100Mbps fiber connection in her home. Sure, it isn’t synchronous, but it can still consistently maintain 100Mbps in either direction. Should someone choose to utilize said bandwidth, it is there and readily available. I live in Chicago and both Cogent and ATT offer fully synchronous 100Mbps Metro-E starting at $600/mo. They will gladly bump that up in increments of 100Mbps for an additional $400/mo per 100Mbps up to 1Gbps.
Second, the PlayStation’s MAC addresses are absolutely exposed when ports are forwarded via NAT. No, this is not a native function, it is a built in function of the listening device (PlayStation or XBox). The ports are forwarded because there is a service on the device that is listening for requests. When Sony’s systems connect to these services, they report all of the hardware and software information about the device back to Sony’s management systems. Most large companies, such as yours (and certainly MS), leverage mobile and desktop management systems that report diagnostics back to your NOC operators. They could be using countless management tools such as SCCM, MBAM, DirectAccess, NAP, and/or any other number/flavor of device and network monitoring systems to manage client configuration, health, and connectivity capability. PSN and XBox Live are giant corporate networks that have all of these capabilities baked into the OS. Beyond that, PlayStation and XBox Live are peer-to-peer services. MY PlayStation could be the server for any given game. Once the user is authenticated on Sony’s network, connections from other users come directly to my WAN IP and are forwarded to my PlayStation.
I think the disconnect is a result of my comments addressing this issue in particular and your rebuttal was focused on networking in general.
That being said, even if I were speaking in a more general sense, port forwarding can and does expose any number of sensitive pieces of information about the device on the other side. That is the entire point of the function, otherwise all communication would have to be client driven and operate through proxy services. NAT allows for direct access to systems behind the firewall on a port-by-port basis. At that point, anything could be divulged once a connection is established. The information transmitted is completely dependent on the machine and service fielding the connection requests. This is the entire reason why firewalls exist, to prevent external access to sensitive services that may provide elevated access to sensitive information. Go ask one of your systems admins if you can forward 135, 5985, 3389, and whatever subset of the DCOM port range that they are using for WMI to your company’s Domain Controllers and let me know how they respond.
Third, these guys are using either purchased or self-manufactured botnets. The botnets in question a collection of compromised systems that are centrally controlled by an attacker to launch choreographed attacks of any number of flavors on any number of target types. It is extremely unlikely that 5,000+ node botnets do not include thousands of home and small business PCs. These are the unmanaged, unmonitored systems that are the softest targets for hackers looking to build large botnets because they can leave their package on the victimized machine and there is a high probability that it will still be there, actively reporting in, when they are ready to launch their attack. That is exactly how they caused this outage. Bandwidth saturation via coordinated botnet attacks. Read the Daily Dot Com interview article. You will notice this quote from one of their members, “If I was working [at Microsoft or Sony] and had a big enough budget, I could totally stop these attacks,” Cleary claimed. “I’d buy more bandwidth, some specific equipment, and configure it correctly. It’s just about programming skill. With an attack of this scale, it could go up to the millions. But that’s really no problem for Sony and Microsoft.”
The bottom line is that this was a simple bandwidth saturation attack that originated simultaneously from thousands of compromised nodes and the sum total of the upstream bandwidth from those nodes overwhelmed any combination of the network infrastructure, the authentication services, and/or the ingress bandwidth capability of the Colos housing said systems.
The gaming systems are highly managed, single OS, single manufacturer, single hardware profile, and in many cases are actively available, listening external communication via port forwarding. Given all of this information, it is reasonable to assume that both Sony and Microsoft have the functional and technical capability to create relatively stable, secure communications procedures that can prevent this type of attack. They have chosen to forego best practice security and network design in favor of increased profit. Proving that point is exactly why these guys launched the attack on the first place.
Fourth, Sony and Microsoft are not their own ISPs. They surely have some dedicated lines for critical function and internal operations, but they both heavily rely on 3rd party providers like Akamai (and others) for client content delivery. Akamai has delivery centers locally/regionally located throughout the world. They use the regional Tier 1 providers like Level 3, Cogent, ATT, CenturyLink, XO, etc, etc, just like everyone else in the world. Fast content is regionally distributed content. Meaning if Microsoft wants to deliver content in Brazil, it is hosted in data centers Brazil, and I promise you that Microsoft is not the ISP.
So yes, in your own words, you came off a bit like a jerk. Not because of a lack of knowledge, but a lack of context in this particular situation.
Thanks for the very clear & to the point response, Tim.
I believe Rufus may have said that no one had access to the Mac addresses unless you are connected to them.
That seems to be what you are saying, also.
It’s not clear to me whether the end user has control over whether a malicious attacker makes that connection or not.
While the networking details are very important, technical issues are an effort to play defense & some offense is necessary to win any contest, whether it’s against cybercrooks/juvenile cyberdelinquents/hackers, malware authors/foreign government cyberspies/cyberpaparazzi, or an opponent in just about any sport that involves combat.
Playing only defense uses your resources while giving the attacker time to plan his next move without worrying about being attacked himself.
This is part of the problem: The offensive response to cyber attacks is to try some legal solution, which is problematic as I mentioned earlier because of lack of golbal cooperation. This is not likely to change soon.
Perhaps, it should be legal to counter attack any source that attacks your system. If the hijacked computers on botnets were brought down by one of the systems that they are attacking, it would wake up those whose machines have been hijacked.
It might start a cyberwar, but we are already at war, and the miscreants are getting paid to attack us when we cannot effectively fight back.
Someone should point out that everyone except the government, who have their hands tied by national borders, seems to feel that it’s someone else’s fault/responsibility.
Lots of finger pointing, very ineffective responses, and a big payoff for the cybercriminal is a recipe for disaster over time.
We might as well mail the crooks a check & be done with it. But, of course, blackmail never ends. ;^)
Weren’t there a couple of competing malware vendors & one was able to uninstall the other’s malware (a rootkit, it may have been) & install his instead?
There’s a way to fight back. Make it legal to protect yourself by counterattacking.
It would be interesting if companies could utilize Castle doctrine to defend themselves from attacks. Since a computer network could, potentially, be viewed as a space of residence, seeing as most of these companies utilize their computer networks for large amounts of work processing, AND the fact that, in the US at least, a corporation is considered a person/citizen with certain rights.
I just think that would be an interesting avenue of law to pursue for justification of self defense by companies.
Although, personally, i feel it is only a matter of time before companies/corporations take the matter into their own hands and start dropping large amounts of money defending and attacking each other, if they aren’t already. I feel this way based off of spectating the past few events that have made news lately (the hacks of target, home depot, etc.) and the revelation to the senior execs at sony that what they thought were personal emails can be released to the public, exposing any sort of wrongdoing. Not that I automatically assume all corporations to be evil machines of soul crushery, but I do not have faith in people not abusing laws when they think they can get away with it.
Good old Sony charge for a a arm and a leg for there products. And turn around and thirteen year olds take out there security…nice guess North Korea won’t have any problem. Hacking them
Thanks for taking the time to clarify networking security. A very informative and helpful comment. Thumbs up!
Oops! I posted a response below that was supposed to go to Rufus.
Thanks for taking the time to clarify networking security, & debunking the idea that managing it at a large company involves simple solutions.
Everyone’s a critic & usually comes up with simple & unworkable solutions.
Thanks again.
Very well stated, Rufus.
I found myself looking for the upvote botton after reading this. ( I guess I’m spending too much time on reddit)
Cowards sounds a bit harsh. Not really all that in character with the more neutral reporting you normally do.
Is it because they target you specifically? And have an emotional reaction to this script kiddie group? Or are you trying to get them to react and do something stupid?
(Or is this normal and I have not encountered this kind of namecalling on the blog before).
It’s not unprecedented on this blog. E.g.,
http://krebsonsecurity.com/2013/03/the-world-has-no-room-for-cowards/
To answer your question, it has already prompted a reaction. More soon.
How is it harsh? What would you call people who attach behind aliases and target children? Cowards might be a bit too soft of a word, IMO.
They were rolling attacks on Christmas day.Im part of the gamer community on ps4,Xbox and Internet.
I knew when I had internet but no game access something was afoot.
Fortunately us gamers are pretty tech savvy and rode out the storm instead of laying blame on the game or tech companies.
Screaming on a forum or blog gets you nowhere.Always has always will.
Thank you Bryan for continuing to provide a forum on happenings like this.
My mom told me something when I was a young boy that had profound impact on my life, “Do you see that cow? It has neither the power to be really good nor really bad. You are going to be a man someday and you must choose because you will truly have the power to be really good or very bad.”
I feel like there’s been a strong trend in literature aimed at younger readers lately. Divergent, Hunger Games, Ender’s Game, and many more highlight protagonists who are children that change the world. Comments on this story depict the typical response many young people feel about society’s emphasis in their role in shaping the future, which is why those books tend to appeal to young readers. Underestimated, ineffectual, were very real messages I battled as a 20 yr old. The young people who coordinated these attacks are neither children nor typical bored adolescents. They are quite likely the same age as those who stormed Normandy, or, for an even better analogy, those who enlisted as part of the code breakers at Bletchley Park. Mavis Batey, 18. Alan Turing 27. That’s most likely the age range of those in charge of the attacks, and they are desperate to be a part of something bigger than themselves, to have a cause to get behind.
Their actions were barely more sophisticated and thought out than yelling “Fire” in a crowded theater though, and only slightly less apprehensible. I understand that they wanted to highlight security flaws, or infrastructure shortcuts used by multinational companies who are trusted by millions of people, but there are other ways to go about that. Not necessarily easier ways though which brings me to my primary concern. I hope they find the better way to be world changers before it’s too late.
I’ve worked in infosec at tech companies like those mentioned.
I’m curious how you know that theses systems are really participating in the attack? Do you see more than the IP of their gateway and the user agent strings from the browser? Their enduser systems are likely very homogeneous, so the user agent strings are likely the same. Are you using unique cookies? Or is the request frequency not human?
Perhaps people at those companies are being sent links to recent articles and are reading them at the same time.
Curious, Kapu
The are very real questions if you did not manage the design and build of the client systems from the ground up. Most normal web services would have no way of quickly identifying which traffic is real and which is malicious. The traffic would have to be inspected and tested with some form of DPI and then moved along to the auth servers. The frustrating part of this particular issue is that Sony and Microsoft manage every aspect of these game consoles forever, from the initial design, to build, to forced patching, and eventual sunset. There is nothing unpredictable or random about any of them and they are highly specific, customized operating systems. The only thing they don’t know about them is what public IP addresses they will use to connect to their services. They have both direct and proxied client access to the systems core information whenever the system is connected to the network. They can activate/add and deactivate/remove features at will. Given this incredible level of intimate knowledge and heavy control over the devices, they can include whatever information they want to include in the connection strings. Unfortunately, they have not done this and the consoles authenticate using the same mechanisms as my mobile phone. This is the flaw in the design. They have total design, build, and management control over the ecosystem and have failed to leverage that control to their advantage. The process used to generate valid authentication tokens for the actual consoles should be completely different and independent from the rest of the client authentication processes. Each device should have a completely unique connection string / authentication payload that bears no resemblance to the general authentication mechanism utilized by the public web services. I’m not putting a name to it because there are a number of possible solutions, but they could technically create global ACLs / ARP tables, they could establish any number of VPN type connections, they could utilize a clientless system like Microsoft’s DirectAccess. The possibilities are quite limitless. I think the issue here is that people continue to think about this problem solely within their own experience scope. That is not necessary. Remember, they control everything except for the public IP that I am connecting from. It’s funny to actually admit this, but their integration level is tantamount to what BlackBerry has with BES and their mobile devices. They control or can control every bit of the user experience. The connectivity and authentication system for PlayStation should be practically identical to BES. In fact, I think MS or Sony should go out and buy them right now lol! Either that, or some Exec at BB needs to begin development for BES console edition lol!
remember that the console has to connect first before any of these handshakes can take place. The connection is even more expensive if it is SSL. All an attacker needs to do is create many spurious connections, and all the information Sony and Microsoft have won’t help to decide which connections are legitimate and which aren’t.
wonder how Microsoft would react if they knew one of the attackers responsible was the son of an employee?
Probably not long until they find out, if they don’t know already.
Terrible way to wake up on Christmas morning…
you should try cloudflare or verisign, prolexic can’t do anything with layer 7 traffic.
Hi,
We never let our kids now 19,17 and 13 into chatrooms or online forums. Never bought them the xboxes etc. adults marvel at their conversational abilities compared to most. While waiting for our table,we observed a 10 month old baby holding a digital device with a video on it. Awful.
My son an MMA fiend/fan read this to me during a family outing. It suggests other breaches.
http://www.mmamania.com/2014/12/27/7455291/report-hackers-release-user-info-credit-card-details-following-ufc-fight-pass-data-breach-mma
I referred our IT gurus to your site. Great work- I don’t follow all the intricacy and fine points, but appreciate the legwork, integrity and above all, the civilized and respectful remarks in your blog community.
I had all of these things and yet, I don’t get complaints about my conversational skills. Reading your post only made me feel sorry for your kids. You think that somehow xboxes are responsible for poor social skills. I’m baffled.
I will say it again, the people behind all these DDos attacks are immature narcissistic criminals
Here is Lizard Patrol Public Facebook Profile (is it really them ? )
https://www.facebook.com/LizardPatrol
Why Facebook allow them to be public ? Why didn’t they censor it ?
Nice
“While most of the group’s acolytes are known to U.S. enforcement investigators, many are minors, and the sad truth is that federal prosecutors don’t really know what to do with underage felons except to turn them into informants. Meanwhile, the cycle of abuse continues.”
I’ve got an idea….
ARREST THE SOB’s. Just because they are minors do not mean that they are exempt from the law.
Yes, I will agree that throwing them in jail doesn’t work. I’ve got a better idea. Community service, fining the parents for lack of oversight, and putting a restraining order on the minors that prevent them from using online services.
Dont leave the sentence up to a judge either, make it MANDATORY and unmodifiable that if convicted then X, Y, Z.
I love the fact that Brian was logged into their chat room as “BrianKrebs” 😛
yep def Cowards . sad one at that