By now, many of you loyal KrebsOnSecurity readers have seen stories in the mainstream press about the coordinated global law enforcement takedown of Darkode[dot]me, an English-language cybercrime forum that served as a breeding ground for botnets, malware and just about every other form of virtual badness. This post is an attempt to distill several years’ worth of lurking on this forum into a narrative that hopefully sheds light on the individuals apprehended in this sting and the cybercrime forum scene in general.
To tell this tale completely would take a book the size of The Bible, but it’s useful to note that the history of Darkode — formerly darkode[dot]com — traces several distinct epochs that somewhat neatly track the rise and fall of the forum’s various leaders. What follows is a brief series of dossiers on those leaders, as well as a look at who these people are in real life.
ISERDO
Darkode began almost eight years ago as a pet project of Matjaz Skorjanc, a now-36-year-old Slovenian hacker best known under the hacker alisas “Iserdo.” Skorjanc was one of several individuals named in the complaints published today by the U.S. Justice Department.
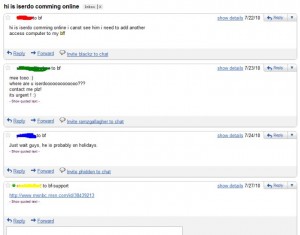
Butterfly Bot customers wonder why Iserdo isn’t responding to support requests. He was arrested hours before.
Iserdo was best known as the author of the ButterFly Bot, a plug-and-play malware strain that allowed even the most novice of would-be cybercriminals to set up a global cybercrime operation capable of harvesting data from thousands of infected PCs, and using the enslaved systems for crippling attacks on Web sites. Iserdo was arrested by Slovenian authorities in 2010. According to investigators, his ButterFly Bot kit sold for prices ranging from $500 to $2,000.
In May 2010, I wrote a story titled Accused Mariposa Botnet Operators Sought Jobs at Spanish Security Firm, which detailed how several of Skorjanc’s alleged associates actually applied for jobs at Panda Security, an antivirus and security firm based in Spain. At the time, Skorjanc and his buddies were already under the watchful eye of the Spanish police.
MAFI
Following Iserdo’s arrest, control of the forum fell to a hacker known variously as “Mafi,” “Crim” and “Synthet!c,” who according to the U.S. Justice Department is a 27-year-old Swedish man named Johan Anders Gudmunds. Mafi is accused of serving as the administrator of Darkode, and creating and selling malware that allowed hackers to build botnets. The Justice Department also alleges that Gudmunds operated his own botnet, “which at times consisted of more than 50,000 computers, and used his botnet to steal data from the users of those computers on approximately 200,000,000 occasions.”
Mafi was best known for creating the Crimepack exploit kit, a prepackaged bundle of commercial crimeware that attackers can use to booby-trap hacked Web sites with malicious software. Mafi’s stewardship over the forum coincided with the admittance of several high-profile Russian cybercriminals, including “Paunch,” an individual arrested in Russia in 2013 for selling a competing and far more popular exploit kit called Blackhole.
Paunch worked with another Darkode member named “J.P. Morgan,” who at one point maintained an $800,000 budget for buying so-called “zero-day vulnerabilities,” critical flaws in widely-used commercial software like Flash and Java that could be used to deploy malicious software.
Perhaps unsurprisingly, Mafi’s reign as administrator of Darkode coincided with the massive infiltration of the forum by a number of undercover law enforcement investigators, as well as several freelance security researchers (including this author).
As a result, Mafi spent much of his time devising new ways to discover which user accounts on Darkode were those used by informants, feds and researchers, and which were “legitimate” cybercriminals looking to ply their wares.
For example, in mid-2013 Mafi and his associates cooked up a scheme to create a fake sales thread for a zero-day vulnerability — all in a bid to uncover which forum participants were researchers or feds who might be lurking on the forum.
That plan, which relied on a clever watermarking scheme designed to “out” any forum members who posted screen shots of the forum online, worked well but also gave investigators key clues about the forum’s hierarchy and reporting structure.
Mafi worked closely with another prominent Darkode member nicknamed “Fubar,” and together the two of them advertised sales of a botnet crimeware package called Ngrbot (according to Mafi’s private messages on the forum, this was short for “Niggerbot.” The password databases from several of Mafi’s accounts on hacked cybercrime forums included variations on the word “nigger” in some form). Mafi also advertised the sale of botnets based on “Grum” a spam botnet whose source code was leaked in 2013.
SP3CIAL1ST
Conspicuously absent from the Justice Department’s press release on this takedown is any mention of Darkode’s most recent administrator — a hacker who goes by the handle “Sp3cial1st.”
Better known to Darkode members at “Sp3c,” this individual’s principal contribution to the forum seems to have revolved around a desire to massively expand the membership of the form, as well as an obsession with purging the community of anyone who even remotely might emit a whiff of being a fed or researcher.
Sp3c is a well-known core member of the Lizard Squad, a group of mostly low-skilled miscreants who specialize in launching distributed denial-of-service attacks (DDoS) aimed at knocking Web sites offline.
In late 2014, the Lizard Squad took responsibility for launching a series of high-profile DDoS attacks that knocked offline the online gaming networks of Sony and Microsoft for the majority of Christmas Day.
In the first few days of 2015, KrebsOnSecurity was taken offline by a series of large and sustained denial-of-service attacks apparently orchestrated by the Lizard Squad. As I noted in a previous story, the booter service — lizardstresser[dot]su — was hosted at an Internet provider in Bosnia that is home to a large number of malicious and hostile sites. As detailed in this story, the same botnet that took Sony and Microsoft offline was built using a global network of hacked wireless routers.
That provider happens to be on the same “bulletproof” hosting network advertised by sp3cial1st. At the time, Darkode and LizardStresser shared the same Internet address.
KMS
Another key individual named in the Justice Department’s complaint against Darkode is a hacker known in the underground as “KMS.” The government says KMS is a 28-year-old from Opelousas, Louisiana named Rory Stephen Guidry, who used the Jabber instant message address “k@exploit.im.” Having interacted with this individual on numerous occasions, I’d be remiss if I didn’t explain why this person is perhaps the least culpable and yet most interesting of the group named in the law enforcement purge.
For the past 12 months, KMS has been involved in an effort to expose the Lizard Squad members, to varying degrees of success. There are few individuals I would consider more skilled in tricking people into divulging information that is not in their best interests than this guy.
Near as I can tell, KMS has worked assiduously to expose the people behind the Lizard Squad and, by extension, the core members of Darkode. Unfortunately for KMS, his activities also appear to have ensnared him in this investigation.
To be clear, nobody is saying KMS is a saint. KMS’s best friend, a hacker from Kentucky named Ryan King (a.k.a. “Starfall” and a semi-frequent commenter on this blog), says KMS routinely had trouble seeing the lines between exposing others and involving himself in their activities. Here’s one recording of him making a fake emergency call to the FBI, disguising his voice as that of President Obama.
KMS is rumored to have played a part in exposing the Lizard Squad’s February 2015 hijack of Google.com’s domain in Vietnam. The message left behind in that crime suggested this author was somehow responsible, along with Sp3c and a Rory Andrew Godfrey, the only name that KMS was known under publicly until this week’s law enforcement action.
“As far as I know, I’m the only one who knew his real name,” King said. “The only botnets that he operated were those that he social engineered out of [less skilled hackers], but even those he was trying get shut down. All I know is that he and I were trying to get [root] access to Darkode and destroy it, and the feds beat us to it by about a week.”
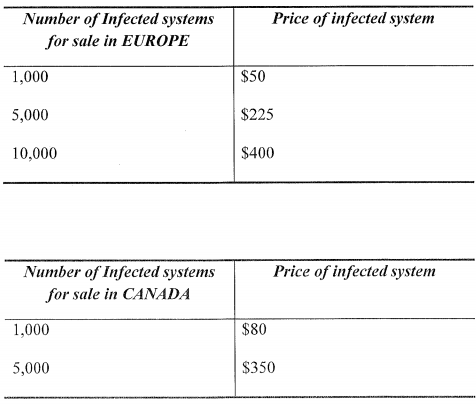
The U.S. government sees things otherwise. Included in a heavily-redacted affidavit (PDF) related to Guidry’s case are details of a pricing structure that investigators say KMS used to sell access to hacked machines (see screenshot below)
Many other individuals operating under a number of hacker names were called out in the Justice Department press release about this action. Perhaps some of them are mentioned in this subset of my personal archive of screen shots from Darkode, hosted here. Happy hunting.
One final note: As happens with many of these takedowns, the bad guys don’t just go away: They go someplace else. In this case, that someplace else is most likely to be a Deep Web or Dark Web forum accessible only via Tor: According to chats observed from Sp3c’s public and private online accounts, the forum is getting ready to move much further underground.
The Justice Department press release on this action is here, which includes links to charging documents on most of the defendants.
Update, 8:55 p.m. ET: Removed a sentence fragment that confused Iserdo with other individuals connected to his indictment.






Yes! Use crimeflare to host evidence for others to use to identify, analyze, and prosecute criminal activity! 🙂
Turnabout is fair play. And, yes, they were gracious enough to host my content, which will in all likelihood get them more traffic than I can handle.
Hey Nicholas! Nice to see you here! How’s your academic researching going on? Pays well?
Cloudflare can’t police everything. As far as I remember, Darkode wasn’t even CF-protected. Furthermore, it’s NOT hosting content at all, in any case, aside from their own website.
Brian ,I don’t understand the Computer Science . But I do understand the deep understanding you have of the work at hand . I enjoy reading all that you have written on this subject as I have to go and look up the nomenclature. I also like that you run these thugs down.. You have the direct connection of right and wrong… conscious
Sincerely
C
Aww, they redacted all the good stuff about the informant.
Brian, I have your book “Spam Nation” which was a fascinating read.
Your article on Darkode Cybercrime, if details were to be expanded and more background included, would also be an excellent choice for a full book. Please consider this possibility.
Thanks, Richard. Consider it considered 🙂
I’m with Richard, definitely requires at least one chapter.
As always, good job.
Hey Brian. Nice work, as always! Bigger things are in store for Sp3c, I’m sure.
This Starfall and KMS guy are both criminals, lock them up. “I were trying to get [root] access to Darkode and destroy it, and the feds beat us to it by about a week.” Sounds like destroying evidence on an on-going case. These kids need to be taught a lesson.
They likely intended to leak the information, such as the database, files, etc, even send it to police, feds, etc. I think they meant to rm the box. You are misinterpreting this.
If they want to do that they need to become officers of the law. WE dont need vigilantes.
And there will be more arrests to come as the miscreants turn on one another to save their own skins.
They obviously had good intentions. What should be done is a public acknowledgement of the good intentions but an explanation of why it wasn’t ideal in this case.
As far as I know, they weren’t raiding banks or trying to get copies of valuable Intellectual Property to sell. Treating miscreants/vigilantes as if they were hardened criminals deserving of a felony conviction is among the type of conduct that scares away talent from working for Feds/LEAs.
Think of the greater good for society. Steering the well-intentioned to more palatable outlets for their skills would have a more desirable outcome than the standard “put their head on a pike and show it to the world” methodology.
If I must be locked up then so be it. I didn’t touch Darkode with a 50ft pole and the one who did on my behalf is now facing a court case. I feel very guilty for that.
However, destroying that board, as I would envision it, did include giving all the data to the feds.
the feds dont need you obviously. you and your friend just complicated the case. gtfo…
No need to be rude about it. If I have to face charges for interfering in an undercover operation I had no idea about, then I will do so. I can admit when I’m wrong.
Your best bet would have been to give the Feds the root password, or other access. Tampering with evidence in any form will get you behind bars. If you are who you say you are, openly admitting that your interfering with a federal case can place you behind bars.
When you tamper with evidence in any way, your allowing the slightest crack in that door, allowing the criminals to leave the courtroom with less than desired sentences. If you dive into stories and truly read and comprehend what Brian has written here, as well as look at the results of many years of investigations and the costs and efforts to do so – Your actions only add to that time.
You honestly think you simply handing over something to the FBI is going to be considered legit? They will not take your word that you didn’t tamper with anything. In the Feds minds you are far from a superhero and even farther than being trusted…..
With what you practice, the trust isn’t there. The feds probably seen you screwing around and decided it was time to act before some one botched up the ability to use the evidence at hand.
The feds don’t need your help other than pointing them in the right direction. If they thought you had significant ties to other hard targets, they would have hired you by now. Believe me, at this point, they know you better than you know yourself.
Riding somewhere between the good and evil only brings a few things to mind; one is untrustworthy, loves attention, has no true direction and is unorganized. What people like you do is really simple and crude – but it creates more harm than good.
Thanks for the input, and we had nothing except the trust of an admin. No evidence was touched because we couldn’t yet do so, and if it were to be touched, it would have been imaged and handed off.
Actually.. I have to make one more reply to this.
I understand you see me as a vigilante, and I probably am, but people drag me into things. I don’t involve myself until someone involves me, and I certainly don’t enjoy this kind of attention. I use this kind of attention to get information out and then try my best to go back to living my life. My reasons for doing what I was doing were petty beyond attention. If you want to criticise me for what I tried to do, then at least know that I did what I did so that I could rid myself of certain very annoying criminals in my life, and move on. It was not for attention.
Pro hackfoums skid turned wannabe informant? Your trying to justify your actions by telling yourself that “they included me” even though in the end it’s still your decision to help them commit crimes, you don’t personally have to hack anything but if you guided or helped someone do it your still guilty. You and all of your buddies are nothing but attention seeking e-whores whether it’s from a bunch of 14 year olds from hackforums or from the government. If you want to cut these types of people from your life then just walk away, it’s that simple im sure a genius hacker like you could have thought of it. You have to choose a side of the law you wanna be on you can’t be both without ending up in jail at some point. It’s always the people seeking e-fame that end up being the snitches when they get busted, I hope all your little buddies know that as well when they ask you for help hacking a site.
I think you misunderstand. When I say “they involved me” I mean they chose to bother me and try to victimize me, not ask me for help.
Starfall, I just added you on Jabber(I hope the address I know for you is still active). My jabber address is ****follower@*******. I know some things and would like to speak to you privately.
I like how your comment is much worse written and immature than the so-called 14yo skid you’re trying to insult.
Trust me, you can learn a lot more from a person by having a decent conversation and respecting what they have to say than simply trying to flame them.
Don’t be a child.
Oh, don’t worry. I get worse from the peanut gallery every day.
Reposting this higher up so that maybe HFsec will see it
The government did not need me.
I needed me. I did what I did out of entirely selfish motives, to help myself get away from the spotlight placed on me by people who I was once similar to. The LizardSquad kids could not keep my name out of their mouths. The only reason I continue to involve myself in this community is so that I can finally see them gone and leave it in peace. When they’re gone, I’m gone.
I did not do what I did “for” the government, or “against” the government. I did what I did so that maybe I would get to return to my life a bit quicker than if I had done nothing.
to me, you seem just like an attention whore.
Depends, are you still the retarded kid you were on thegibson xero? or have you grown up?
In order for it to be considered tampering with evidence, he would have to know there was an ongoing investigation into the forum.
It isn’t tampering to try and stop criminal activity. It may be the act of a vigilante, as you say, but it is not criminal tampering.
Personally, I don’t believe the word vigilante applies here. If we limit the fight against online criminals to only those who are in law enforcement, then we will be fighting a losing battle from start to finish.
While I don’t believe it should be lauded, I certainly do not believe it should be punished, either.
Sorry, but I agree with starfall. The government must of needed him. Just because one can obscure or open a trail that needs to be followed. Just because you are law enforcement doesn’t mean you are on the right trail. And they could have used an interloper as a shield, or a Patsy. And once involved, sf was a Patsy, for some reason, he/s got a bone to pick with the bad guys, surprised he hasn’t gotten cred’s and hired by the good guys, to rehab.
This is the same government that would try Snowden as a traitor and lets Arne Duncan give billions to corrupt schools for decades while punishing millons of young people for life with debts they can’t escape. Whether what these guys did is wrong or not, their chances of a fair trial or benefit of the doubt are not very good in this country.
They can attack the banks but once they attack The Bible they have gone too far.
The government did not need me.
I needed me. I did what I did out of entirely selfish motives, to help myself get away from the spotlight placed on me by people who I was once similar to. The LizardSquad kids could not keep my name out of their mouths. The only reason I continue to involve myself in this community is so that I can finally see them gone and leave it in peace. When they’re gone, I’m gone.
You really have no idea what you’re talking about, be quiet.
wow nice job you sure convinced me with those hot opinions faglord
let’s face it, you’re a bandwagoner that has no idea what s/he is talking about. tbh gender is irrelevant as you have already revealed yourself to be a subhuman
you have no place nor no clout to back your opinion up, you may as well be jerking yourself off with a fleshlight and a horsetail buttplug while screaming about ddos, anonymous, legion, fullz, the NSA, and truecrypt.
go away
Very good read worth waiting for. Post more information about Darkode (dot) com
Hey Brian, any thoughts as to why “Sp3cial1st” was not included in the indictment?
Jeff
Well, I’ve got a few ideas but none of them are popular.
The main one is that sp3c is involved with LEA in some country or another, and KMS’ indictment seems to corroborate that.
Who is Sp3c?
This sounds like the behavior of an undercover operative: trying to get others to join, while pretending to weed out agents:
“Better known to Darkode members at “Sp3c,” this individual’s principal contribution to the forum seems to have revolved around a desire to massively expand the membership of the form, as well as an obsession with purging the community of anyone who even remotely might emit a whiff of being a fed or researcher.”
It is a racist article. I think US authorities should sue Krebs for racist words. And keep him for a little 20 years in prison for that.
no offense but what is wrong with you?
Troll detected
Starfall if being honest and has been upfront about his wrongs.
Now I would give him a break. He obsiously has a soul unlike most.
I’m curious if you Brian, as a reporter and investigator have ever overstepped your boundaries and gotten too involved in something? You do work in a world where you play with dangerous people and otherwise unsavory places. Do you ever worry you may be subject to an investigation because of it? I’m sure you have deep connections with cyber criminals, how would you have the amount of knowledge you do otherwise?
I see that attitude a lot and pretty much no major crime could take place without a lot of scared chickens who won’t speak up or investigate. I think Brian does a vital job in exposing a lot of things that would otherwise fester or defraud millions before the inevitable hammer of justice can catch up. How many people remember seeing or being bullied in school and not having the power or guts to do anything about it? Brian isn’t the problem here, people taking advantage of other people are the problem.
In considering malware, such as the Dendroid, the skill and cleverness of its design may mask the terrible damage that such malware can do when employed as a spy tool against a person. I have a legal client whose life has been extremely interfered with and harmed for quite some time. She came to me many months ago because she was being spied upon. She knew by whom, but she did not know by what method. We narrowed it down that it had to be her phone, and yet a scan by one of the very rare knowledgeable law enforcement officers showed her phone to be free of malware. This is what sets Dendroid apart, that it binds itself to an app and hides from scanning. I figured this was what was happening to her, and this new information verifies this as likely.
I was aware for several years of phone programming that could control the camera, audio and data, since I first found such a thing was being distributed on an app that was part of a popular website. The element added by Mr. Culbertson, if any, was making it scan resistant. I do think he will probably have a defense that he was simply making a product for sale and that how it may have been used was improper, but not under his control. However, the damage to one’s life when spied upon by such a device is terrible, and in particular because the sort of person who employs a phone spy device against another is likely to be the most virulent sort of stalker.
Take the most stalkerish, control freak, invasive, manipulative type of person and allow them to see and hear everything you do: this is what happens with phone spyware.
Is it acceptable to use spyware as a form of marketing analysis? That is how I first saw such phone spyware employed several years ago. Is it acceptable to place such a spy app onto a phone without the person being blatantly informed and aware? In the instance I saw where such spyware was being deposited onto phones, the only notification was hidden deep in the terms of service.
I have seen the terrible damage done by an outright illegal use of a product such as Dendroid, or a very similar malware, as it harmed the life of my client. The people spying on her were formerly in her life as spouse and business associate. They were able to harm her business terribly by knowing in advance what her business moves were, and beating her to the punch. They invaded her relations with her family, by knowing what was said and done between them in private.
The people flaunted that they were spying on her, and yet she was unable to figure out the means. Her house and car were searched for hidden cameras or transmitters. She had her phone scanned by a knowledgeable cyber police officer. By process of elimination of what was known by those spying on her, we knew it had to be the phone that was bugged. As many people do, she used her phone for many purposes, including business, personal, and entertainment.
My client got rid of almost all of her electronics and her phone and even moved to a new home and was careful to leave no traces of where she was going. Her new phone seemed “clean” for a while, and then the spying picked up. Those spying on her learned her new location. People may have thought she was “crazy;” I knew she was not. I am glad I stood by her during this hellish time.
Hopefully, things will now eventually get sorted for her. She can never recoup all this time when her privacy and peace of mind were stolen from her. Her business and finances and personal relationships have been extremely damaged.
People gotta have their Facebook/Twitter, Xbox/Playstation, smart phone/smart tv, and Nest thermostat.
It’s all to the point where people will not only accept but demand the “bugs” in their home from the cable co. with their microphone built in the cable box remote to the use of WiFi cameras.
etc. etc. etc.
Amazing people responding to these e-whores postings as though they are the real miscreants in Kreb’s article w/o any verification.
I am slayed Brian !
To the readers:
Krebs is just paying attention. It’s something that few people seem to be doing. There is research. There are fact-finding trips across the web and it does garner some attention back to him from others. But, that is mainly due to the very public podium from which he speaks. It’s all a kind of reporting that I am very glad to see. It’s rather disappointing that I can’t get this from too many people that call themselves “reporters”. This is the biggest reason I keep coming back here.
For that, I thank you Brian Krebs.
——————————–
I can’t get away from the fact that without all those thousands of computers being infected, things like this wouldn’t even be possible. Everyone from IT admins to individual home users that are perfectly happy to allow their machines to be used in such a way essentially become the “johns” to Darkodes’ prostitution ring. I’m not justifying anything or defending anyone. But it’s something that I just can’t divorce from articles like this.
How many of “these” machines were fully “up-to-date” software wise?
Is there a way to get all the names of people that were arrested? Aliases I mean I want to see how many I recognize
I wonder at what point the Government will decide that it is more expedient to ‘deal’ with cybercriminals the same way that it ‘deals’ with terrorists or those we suspect of being or becoming terrorists. It would be hard to argue that the threat to infrastructure, the banking system and the economy is no less significant with the former over the later.
KMS should have a strong chance of working with the feds now.
So long as the american justice system sees him for who he truely is. He adopts different personalities and will make you think what he wants you to think. A true genius. Master troll. Wide range of skills and putting someone like that in prison is just such a waste. Some only know him for his freestyles on tinychat and Skype. He has made a lot of people laugh and has quite a few fans.
KMS Rapping on Soundcloud
https://soundcloud.com/kronklz
KMS vs. Security Expert
https://www.youtube.com/watch?v=BQyvYlUJ4w0
I will not forget this dude. I hope you beat your case brother.
I agree with you, FREE KMS.
Wow Krebs. I just found this blog and you got sooo many interesting and cool posts. Thanks for sharing your knowledge with everyone.
I have one question. I read about this Darkode site on the news. But I am wondering… You say it was hosted on a Bulletproof hosting provider. Well, how come it got shut down then if it was supposed to be bulletproof?
What country was the website hosted in?
I would think these “hackers” would know a lot more about this. I.e how to stay anonymous (not get arrested and not get servers seized?!). Please reply Krebs 🙂
Have a nice day,
Jacob
Rory was responsible for ddosing several conspiracy websites as well as doxxing multiple members of the community. Mp3s where made available of him swatting moderators. He and several other master manipulators in his circle socially engineered a lot of people and wrecked havoc. I for one am glad to see the law has caught up with him!
Rory didn’t do anything bad to anyone who didn’t deserve it.
He has only swatted people who he has been social engineering and gathering evidence on. Yes, he has done illegal things before… But that has always been in a Skype call with others listening. He is a master at gaining peoples trust and not only gaining there trust but taking them down. With the FBI or with out, he is a good guy.
Anyone claiming that he is a bad person has probably been trolled by him before.
Chkval .
wait and see
Hi Brian, There is no such thing as “Sp3cial1st” in case you didn’t notice after the KMS and Mafi’s affs.
This whole character was a sting operation, and they used you as a perfect bait, to keep the small fish like you trolling, blogging and whining around while letting the big fish in and profiling. Wake up.
/Julius
Thank you for your participation, Rory.
You’re welcome.
Love, Jacqueline
Do you ever stop to think, hey if it wasn’t for these sites the security industry would be out of buisness?
In todays day in age there are a lot of very tallanted people out there. Yet there is a massive shortage of jobs for these people.. Is it any wonder tallanted coders find there way into this kind of life?
The banks fraud the people every day. The credit card companys fire cards out to people with no real backing of the “credit” on the cards.. so really no one is “stealing” from anyone..
the goverment start illegal war’s kill inocent children in airstrikes but yet a site like darkode gets world wide attention for what? a few cyber crooks infecting computers and stealing money that has no real backing in the real world?
Do you think Visa and mastercard are sitting on 1000’s of tonnes of gold to back it up? nope..
You want to unveil real crooks then go after the goverment they are the real crooks..
In my view they wanted to get darkode shutdown as a publicity stunt! after the american goverment lost 25million peoples records they had to show force againt hackers..
The real truth is they wanted to see what they could uncover.. what new software could they “steal” from the hackers to use in there own cyber warfare programs against china and other countrys..
Darkode might be gone for now.. but it will be back.. and Im sure next time it will be far more secure.. so well done you lot, you just made cybercrime move to the serious underground..
Mr-TCP-220
Could not have said it better myself.
Very well put.
Darkode.me > darkode.cc
(Some takedown. International law enforcement, took down a digital entity. In the the physical realm–real life– it didn’t takedown the organization.)