AshleyMadison.com, an online cheating service whose motto is “Life is Short, Have an Affair,” is offering a $500,000 reward for information leading to the arrest and prosecution of the individual or group of people responsible for leaking highly personal information on the company’s more than 30 million users.
The bounty offer came at a press conference today by the police in Toronto — where AshleyMadison is based. At the televised and Webcast news conference, Toronto Police Staff Superintendant Bryce Evans recounted the key events in “Project Unicorn,” the code name law enforcement officials have assigned to the investigation into the attack. In relaying news of the reward offer, Evans appealed to the public and “white hat” hackers for help in bringing the attackers to justice.
“The ripple effect of the impact team’s actions has and will continue to have a long term social and economic impacts, and they have already sparked spin-offs of crimes and further victimization,” Evans said. “As of this morning, we have two unconfirmed reports of suicides that are associated [with] the leak of AshleyMadison customer profiles.”
Evans did not elaborate on the suicides, saying only that his office is investigating those reports. The San Antonio Express-News reported Friday that a city worker whose information was found in the leaked AshleyMadison database took his life last Thursday, although the publication acknowledges that it’s unclear whether the worker’s death had anything to do with the leak.
Evans warned the public and concerned AshleyMadison users to be on guard against a raft of extortion scams that are already popping up and targeting the site’s customers. On Friday, KrebsOnSecurity featured an exclusive story about one such extortion scheme that threatened to alert the victim’s spouse unless the recipient paid the attacker a Bitcoin (worth slightly more than USD $250). The Toronto Police posted this image of a similar extortion attempt that they have seen making the rounds.
“Criminals have already engaged in online scams by claiming to provide access to the leaked web site,” he said. “The public needs to be aware that by clicking on these links, you are exposing your computer to adware and spyware and viruses. Also there are those offering to erase customer profiles from the list. Nobody is going to be able to erase that information.”
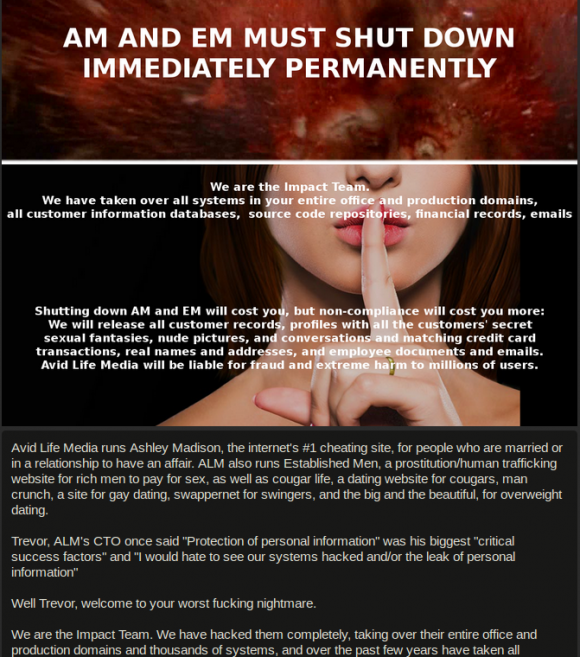
Evans said AshleyMadison employees first learned of the intrusion when they arrived at work on the morning July 12, 2015. Evans said employees powered on their computers and were presented with the initial message from the Impact Team — the hacker group that has claimed responsibility for the breach — accompanied by the song “Thunderstruck” from rock band AC/DC playing in the background.
The Toronto Police Department is encouraging anyone with information about the attacker(s) to contact them via phone or Twitter. Likewise, the department is asking victims of extortion attacks tied to the data leak not to pay the ransom demands, but instead to report the crimes at the addresses and/or numbers listed below.





You can also search the database by email at http://www.cheaterscout.com
The problem is, all those sites just allow you to check for an email address. If you actually want to find out anything more, you need some software to do that. I found this site that seems to do the trick:
http://www.AshleyMadisonUncovered.com/
This site releases Malware!!! Do not click on that link…
Avid Life claimed from the outset that they not only knew who the hacker was, but they had a “file” which contained all of his information.
The hackers (or, more likely in my opinion, leakers) called his bluff and the rest is history.
Meanwhile, the list apparently is fair game, per the SCOTUS: http://consumerist.com/2015/08/25/why-the-stolen-ashley-madison-data-is-legally-fair-game-for-the-internet/