Earlier this month, KrebsOnSecurity featured the exclusive story of a Russian organized cybercrime gang that stole more than $100 million from small to mid-sized businesses with the help of phantom corporations on the border with China. Today, we’ll look at the stranger-than-fiction true tale of an American firm that lost $197,000 in a remarkably similar 2013 cyberheist, only to later recover most of the money after allegedly plying Chinese authorities with a carton of cigarettes and a hefty bounty for their trouble.
 The victim company — an export/import firm based in the northeastern United States — first reached out to this author in 2014 via a U.S. based lawyer who has successfully extracted settlements from banks on the premise that they haven’t done enough to protect their customers from cyberheists. The victim company’s owner — we’ll call him John — agreed to speak about the incident on condition of anonymity, citing pending litigation with the bank.
The victim company — an export/import firm based in the northeastern United States — first reached out to this author in 2014 via a U.S. based lawyer who has successfully extracted settlements from banks on the premise that they haven’t done enough to protect their customers from cyberheists. The victim company’s owner — we’ll call him John — agreed to speak about the incident on condition of anonymity, citing pending litigation with the bank.
On Christmas Eve 2013, the accountant at John’s company logged on to the bank’s portal to make a deposit. After submitting her username and password, she was redirected to a Web page that said the bank’s site was experiencing technical difficulties and that she need to provide a one-time token to validate her request.
Unbeknownst to the accountant at the time, cybercrooks had infected her machine with a powerful password-stealing Trojan horse program and had complete control over her Web browser. Shortly after she supplied the token, the crooks used her hijacked browser session to initiate a fraudulent $197,000 wire transfer to a company in Harbin, a city on the Chinese border with Russia.
The next business day when John’s company went to reverse the wire, the bank said the money was already gone.
“My account rep at the bank said we shouldn’t expect to get that money back, and that they weren’t responsible for this transaction,” John said. “I told them that I didn’t understand because the bank had branches in China, why couldn’t they do anything? The bank rep said that, technically, the crime wasn’t committed against us, it was committed against you.”
SMOKING OUT THE THIEVES
In April 2011, the FBI issued an alert warning that cyber thieves had stolen approximately $20 million in the year prior from small to mid-sized U.S. companies through a series of fraudulent wire transfers sent to Chinese economic and trade companies located on or near the country’s border with Russia.
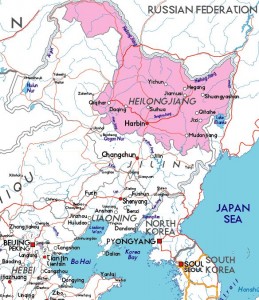 In that alert, the FBI warned that the intended recipients of the fraudulent, high-dollar wires were companies based in the Heilongjiang province of China, and that these firms were registered in port cities located near the Russia-China border. Harbin, where John’s $197,000 was sent, is the capital and largest city of the Heilonjiang province.
In that alert, the FBI warned that the intended recipients of the fraudulent, high-dollar wires were companies based in the Heilongjiang province of China, and that these firms were registered in port cities located near the Russia-China border. Harbin, where John’s $197,000 was sent, is the capital and largest city of the Heilonjiang province.
Undeterred, John’s associate had a cousin in China who was a lawyer and who offered his assistance. John said that initially the Harbin police were reluctant to help, insisting they first needed an official report from the FBI about the incident to corroborate John’s story.
In the end, he said, the Chinese authorities ended up settling for a police report from the local cops in his hometown. But according to John, what really sealed the deal was that the Chinese lawyer friend met the Harbin police officers with a gift-wrapped carton of smokes and the promise of a percentage of the recovered funds if they caught the guy responsible and were able to recover the money.
Two days later, the Harbin police reportedly located the business that had received the money, and soon discovered that the very same day this business had just received another international wire transfer for 900,000 Euros.
“They said the money that was stolen from us came in on a Tuesday and was out a day later,” John said. “They wanted to know whether we’d pay expenses for the two police guys to fly to Beijing to complete the investigation, so we wired $1,500 to take care of that, and they froze the account of the guy who got our money.”
In the end, John’s associate flew with her husband from the United States to Beijing and then on to Harbin to meet the attorney, and from there the two of them arranged to meet the cops from Harbin.
“They took her to the bank, where she opened up a new account,” John said. “Then they brought her to a hotel room, and three people came into that hotel room and online they made the transfer [of the amount that the cops had agreed would be their cut].”
Getting the leftover $166,000 back into the United States would entail another ordeal: John said his handlers were unable to initiate a direct wire back to the United States of such a sum unless his company already had a business located in the region. Fortunately, John’s firm was able to leverage a longtime business partner in Singapore who did have a substantial business presence inside China and who agreed to receive the money and forward it on to John’s company, free of charge.
I like John’s story because I have written over 100 pieces involving companies that have lost six-figures or more from cyberheists, and very few of them have ever gotten their money back. Extra-legal remedies to recoup the losses from cybercrime are generally few, unless your organization has the money, willpower and tenacity to pursue your funds to the ends of the earth. Unfortunately, this does not describe most victim businesses in the United States.
U.S. consumers who bank online are protected by Regulation E, which dramatically limits the liability for consumers who lose money from unauthorized account activity online (provided the victim notifies their financial institution of the fraudulent activity within 60 days of receiving a disputed account statement).
Businesses, however, do not enjoy such protections. States across the country have adopted the Uniform Commercial Code (UCC), which holds that a payment order received by the [bank] is “effective as the order of the customer, whether or not authorized, if the security procedure is a commercially reasonable method of providing security against unauthorized payment orders, and the bank proves that it accepted the payment order in good faith and in compliance with the security procedure and any written agreement or instruction of the customer restricting acceptance of payment orders issued in the name of the customer.”
Do you run your own business and bank online but are unwilling to place all of your trust in your bank’s security? That’s a sound conclusion. If you’re wondering what you can do to protect your accounts, consider adopting some of the advice I laid out in Online Banking Best Practices for Businesses and Banking on a Live CD.




Great story, good to hear the victim making some recovery. I live in China and can tell you that this could have easily gone the other way. The perps here were basically no one with no connections. Had they been someone with connections, the victim’s reps in China could have been arrested themselves, which would have cost even more to ‘fix’. If the perps had advance notice of the op, they could have outbid the victims and the cops would have went their way….
Moral of the story, always know how connected your enemy is before going after him. And be ready for a quick exit if things go wrong…
Great story, thanks. It brings to mind that when I was in the service in Italy, always broke and wanting to get somewhere, one pack of American cigarettes was always good for a cab ride or a beer.
Its amazing what a pack on cigs can do. It seems like the Chinese authorities are also reluctant to get involved. I wonder if there is an “unspoken rule of kickbacks” that goes to the government is some sort of fashion.
I think of it this way. If you have a laptop, fully patched and its only function is to provide communication with the banks, sits behind a NAT and is powered down more than up. Its total cost say for 5 or so years might be about 500 usd or so. It would save these companies millions of dollars if this simple plan would be taken into account.
People don’t want inconvenience. they rather have simplicity and risk. Now that this person has been bitten, and has shared their story with us, others that are prone to this type attack should begin by scribbling notes or drumming up an email to set a safeguard plan in motion. New technologies for most can be daunting, but once they take those steps to improve, they will feel good about it and most should say…. why haven’t I done this long before?
Ok, so there is a slight tug of good that comes out of a corrupt country every once in a while. Its going to be a LONG time before they are even considered slightly trustworthy, as a whole. That time will be many, many generations down the road.
I worked for a police department back in the ’90s. We had two computers at our workstation with a KVM switch to go between them, one computer was logged on as admin and one as a normal user. The admin computer had no internet access or email.
It was a bit of a PITA, but it was effective. And as you point out, the cost over time is pretty low. Yes, it is inconvenient, but a lot of things in life are inconvenient yet we do them anyway. If you’re a corp big enough to do wire transfers, you’re crazy not to greatly inconvenience your finance people and one or two people in the head office by putting as many layers of security as possible on such things, like required two person authorization for any transfers over X amount or going overseas.
Your idea of a two-person requirement for transactions over “X” amount of money or for overseas transactions is the best way to prevent a company from losing a large sum of money – IMHO.
they did have the second item on them (token key)
but really large “NONE REVERSIBLE” money transfers like this should be by Pre approved only and delayed by 3 days if done online (After the approval)
Brian: You wrote some days already about this issue. I just wonder: Why does one single individual (mostly accounting employees) have the right at all to make money transfers? I always thought the four eyes principle was a universally applied concept (with the exception of Germany, where banks do not accept it). I have seen the four eyes principle applied in countries such as Kazakhstan, Morocco, the U.S., and Singapore. This has everything to do with corporate governance (or: sticking to sound accounting principles) and nothing at all with IT.
I don´t know what your experience with corporate banking in Germany is? Having worked in that area for several years, I can assure you that the concept of A and B account authorities (any two A users together or any B user only together with any A user can jointly authorize transactions) is well established and the norm for any bigger business banking relationship.
And that was already the case when I started in that industries, a few decades ago.
My experience: Some 30 field internal audits in German companies, always checking out the four eyes principle and the bank’s confirmation (or: in that case non-confirmation) that it would respect the four eyes principle. You write: “the norm for any bigger business banking relationship”. This is too lofty. I specifially talk about every singly payment transaction and company signatures according to internal regulations, not some theoretical concept how it should be. In all other countries I have worked, the banks have sent confirmations re four eyes principle. Germany, of course (as usual…), being the exception. Their problem is that they cannot accept external authority (being Germans).
To the poster Allan Ewing.
Its not called “Four Eyes” its called “Dual Control”. All companies regardless of size need to have a procedure in place to have 2 individuals review and approve a wire transfer. While this wouldn’t have worked in this scenario, A separate wire transfer workstation with a live CD “see Krebs article” is highly recommended or if possible segregate this machine from the rest of the network with only permitting use of the internet to the specific banking website address.
It is highly recommended that all entities talk to their Financial Institutions about getting 2 factor authentication set up. Most offer it to commercial but don’t advertise that it can also be used with personal accounts.
JD
Dual control and four-eyes principal is the same thing. Different organizations call it different things.
It’s generally (depending on the bank’s regulators) only required that the bank offer dual authentication/dual control/four eyes principal. Not that they enforce it. It’s up to their customer to choose it.
In addition, (depending on the regulator) it’s generally required that banks offer a mandatory a malware scan to be performed in order to login to online banking functions.
As you said, it’s important to ask your bank about implementing these features as they are not required for the banks to implement for all of their clients, only that they have them available.
Interesting story and glad they got their money back. However, it might be worth flagging that the cut paid to the Chinese police sounds very much like a facilitation payment. I’m not a lawyer so I’ll defer to more learned persons than myself but on the face of it that sounds like a facilitation payment. Whilst I think such payments are not illegal under the Foreign Corrupt Practices Act, companies that have any sort of presence the UK should be wary as they’ll be covered by the UK Bribery Act, which *does* make facilitation payments illegal, even if they are done by other parts of the company that are outside the UK. Certainly my employer makes clear that any part of the company can be captured by the Bribery Act, just by virtue of us having a presence in the UK, and thus all facilitation payments are banned.
Interesting point, but the United Kingdom is irrelevant in the world.
Gmail Warning
Gmail says your latest email is suspicions and typically used to steal personal information. Is it legit?
Hah, I got that too. Specifically it says that text in this email is suspicious. My guess is that Google (or should that be Alphabet?) algorithms saw some similarities between Brian’s story and 409-style phishing emails.
By the way, did you know Brian is actually a Nigerian prince looking to quietly transfer money out of his country? 🙂
Ya he got me for 5 or ten bucks a while back…called it a donation or some such. I won’t fall for that again!
Gee he got me as well, but I like what I get back 🙂
Great story and fantastic to hear of even a partial recovery.
There is one error in the post though regarding Federal Regulation “E” where you state consumer victims must notify their FI of fraudulent activity within 60 days of the statement. In the case of a consumer reporting an unauthorized charge, section 6 of the regulation governs consumer liability and you are not limited to reporting errors in 60 days. Rather you can report unauthorized activity any time but the bank must only investigate the first statement of the activity plus 60 days from the date the statement was mailed by the FI. The FI then must investigation the error and unless they can prove otherwise, reimburse the consumer. Any activity that takes place outside of that timeframe is unlimited liability to the consumer as the FI could have prevented the loss if reported in a timely manner.
Section 11 of the Reg discloses the timeframe you mention about procedures for resolving errors but that only governs the timeframes of which the investigation must take place. If someone reports unauthorized activity from a year ago, the FI must investigate and reimburse but there is no timeframe under which that must comply under.
Hope this helps.
Brian- loved this story especially as hearing most of the money was recovered.
keep up the great reporting
No, they should not have been able to recover the money. As a punishment for not complying with the four eyes principle. This only is encouraging sloppy practices.
Isn’t this nice when people attack non regulated currencies like Bitcoin but then you have real stories like this where a bank will not move one finger to protect your money or help you out?
Banks and credit cards offer consumers none protection for online frauds when the amounts are big enough.
This story is absolutely true because I had a close friend that whent trough a similar story. The amount was half of that, but the procedure involved where he actually wired the money after the fraudsters intercepted an email from one of his Chinese providers.
He told him he changed bank accounts (which he did once before) but it was the attacker using a very similar email that got into the reply process in a previous communication. He actually was replying to the scammer for 2 months.
The bank left him dry and told him the same story, it was his fault.
What is amazingly strange is that in China someone took the money out from a business bank account 2 days later. Chinese authorities could not help out either.
So I would say, before wiring anything to China, confirm everything on the phone first because China is so big that once the money is there, its basically lost.
Its also no surprise that all of the frauds involve wiring the money to China.
So, didn’t the company violate the Foreign Corrupt Practices Act for bribing police with cigarettes and cash?
From the Justice Dept web site: “… The Foreign Corrupt Practices Act of 1977, as amended, 15 U.S.C. §§ 78dd-1, et seq. (“FCPA”), was enacted for the purpose of making it unlawful for certain classes of persons and entities to make payments to foreign government officials to assist in obtaining or retaining business. Specifically, the anti-bribery provisions of the FCPA prohibit the willful use of the mails or any means of instrumentality of interstate commerce corruptly in furtherance of any offer, payment, promise to pay, or authorization of the payment of money or anything of value to any person, while knowing that all or a portion of such money or thing of value will be offered, given or promised, directly or indirectly, to a foreign official to influence the foreign official in his or her official capacity, induce the foreign official to do or omit to do an act in violation of his or her lawful duty, or to secure any improper advantage in order to assist in obtaining or retaining business for or with, or directing business to, any person. …”
So my reading is that essentially the FCPA was not breached because the Law Enforcement Officers hired or awarded were not performing a portion of their officially described duty, which would have been to protect local Lawful Chinese residents. In this case they were simply acting as private citizen Bounty Hunters. Especially if one considers that the actual recovery was performed well outside of the Police Officers jurisdictional local.
They should have included a couple bottles of Jack Daniels along with some porn dvd’s to the local cops. They probably could have gotten ALL the money in the bank! Lol
Glad to see that they got most of their cash back. I do think they would have been screwed royally if they didn’t already have a business presence in China.
But to the bank, if someone uses the correct login, token, etc – then to the bank it IS legitimate and in this case the crime was against the company, not the bank.
It is not the banks business to “prove” that every transaction that seems legitimate actually is or isn’t.
Or am I missing something here?
Yes, it seems so.
Banks have lost the popularity vote since 2007/2008, but in this case I think they are not to blame and correct that the crime was comitted to tehc ompany. This is no different than the bookkeeper going corrupt and wiring money to their own account.
The only thing you might argue is that the money went to a different account and the bank might have done a follow up call. But depending on what sizes of money and what transfers they usually made, this may not have been odd. It all depends on the route the money took.
An interesting example of how the US firm was able to utilize the innate leverage of ‘guanxi’ in China to recover most of their purloined funds through the efforts and connections of the police who were incentivized by that finder’s fee offer…
https://en.wikipedia.org/wiki/Guanxi
So , basically police in China charge him 20 % for getting his money back …. What a Lucky guy 🙂 He got robbed not once but twice in a year.
After reading this, I’m now glad that my bank doesn’t allow web-initiated wire transfers of any significant amount.
When I bought my home last year, I bought it with a large mortgage because it closed before the sale of my old house. When the old house’s sale closed, I wanted to wire-transfer most of the proceeds (about $500K) from my account to the bank.
At first, I tried to use the bank’s web-based bill-pay system (which I used to make my normal monthly payments). It said it could not handle any payment over $75K. I then phoned my account representative at the bank. They said they could only initiate a wire transfer of this size with actual written authorization – a hand-signed letter (fax is not allowed), IN ADDITION TO a voice recording of myself giving them explicit authorization. (My representative knows me and would know if someone else’s voice claimed to be me.)
After hearing the procedure we decided it was easier to have a certified check made up for the payment, but even then, I had to go to the bank’s office in person to receive it.
I was a bit annoyed at the number of hoops I had to jump through to transfer that much money, but given what I just read here, I’m glad I had to. I don’t think there’s any way a piece of malware on my computer could ever get far enough cause that much damage. (If it tried to use the bill-pay mechanism for a payment less than $75K, I would be notified by text message, and the transaction is held for at least 24 hours before clearing, so I would have plenty of time to log-on or phone my representative and cancel it)
The headline and the article itself both sound dangerously close to being a description of modern divorce.
I’ve just been completing mandatory compliance trading (I do infosec at a financial services firm) and the bribery module was unequivocal that payments made to public officials to “grease the wheels” or ensure preferential treatment are bribes, and as such are flat out illegal.
Just saying.
Hi
I am regular reader of your blog. I had one question – Generally we read in news about Cards or SSN compromise. However, what actions does credit card companies or retailers take after breach identified are not reported. Is there any article or site which report this ?
Thanks and Warm Regards