A growing community of private and highly-vetted cybercrime forums is redefining the very meaning of “targeted attacks.” These bid-and-ask forums match crooks who are looking for access to specific data, resources or systems within major corporations with hired muscle who are up to the task or who already have access to those resources.
A good example of this until recently could be found at a secretive online forum called “Enigma,” a now-defunct community that was built as kind of eBay for data breach targets. Vetted users on Enigma were either bidders or buyers — posting requests for data from or access to specific corporate targets, or answering such requests with a bid to provide the requested data. The forum, operating on the open Web for months until recently, was apparently scuttled when the forum administrators (rightly) feared that the community had been infiltrated by spies.
The screen shot below shows several bids on Enigma from March through June 2015, requesting data and services related to HSBC UK, Citibank, Air Berlin and Bank of America:

Enigma, an exclusive forum for cyber thieves to buy and sell access to or data stolen from companies.
One particularly active member, shown in the screen shot above and the one below using the nickname “Demander,” posts on Jan. 10, 2015 that he is looking for credentials from Cisco and that the request is urgent (it’s unclear from the posting whether he’s looking for access to Cisco Corp. or simply to a specific Cisco router). Demander also was searching for services related to Bank of America ATMs and unspecified data or services from Wells Fargo.
Much of the information about Enigma comes from Noam Jolles, a senior intelligence expert at Diskin Advanced Technologies. The employees at Jolles’ firm are all former members of Shin Bet, a.k.a. the Israel Security Agency/General Security Service — Israel’s counterespionage and counterterrorism agency, and similar to the British MI5 or the American FBI. The firm’s namesake comes from its founder, Yuval Diskin, who headed Shin Bet from 2005 to 2011.
“On Enigma, members post a bid and call on people to attack certain targets or that they are looking for certain databases for which they are willing to pay,” Jolles said. “And people are answering it and offering their merchandise.”
Those bids can take many forms, Jolles said, from requests to commit a specific cyberattack to bids for access to certain Web servers or internal corporate networks.
“I even saw bids regarding names of people who could serve as insiders,” she said. “Lists of people who might be susceptible to being recruited or extorted.”
Many experts believe the breach that exposed tens of millions user accounts at AshleyMadison.com — an infidelity site that promises to hook up cheating spouses — originated from or was at least assisted by an insider at the company. Interestingly, on June 25, 2015 — three weeks before news of the breach broke — a member on a related secret data-trading forum called the “Gentlemen’s Club” solicits “data and service” related to AshleyMadison, saying “Don’t waste time if you don’t know what I’m talking about. Big job opportunity.”
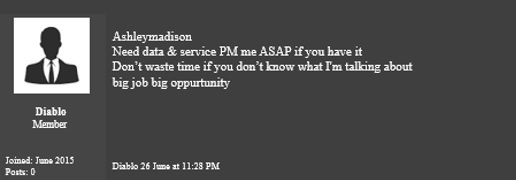
On June 26, 2015, a “Gentlemen’s Club” forum member named “Diablo” requests data and services related to AshleyMadison.com.
Cybercrime forums like Enigma vet new users and require non-refundable deposits of virtual currency (such as Bitcoin). More importantly, they have strict rules: If the forum administrators notice you’re not trading with others on the forum, you’ll soon be expelled from the community. This policy means that users who are not actively involved in illicit activities — such as buying or selling access to hacked resources — aren’t allowed to remain on the board for long.
BLURRING GEOGRAPHIC BOUNDARIES
In some respects, the above-mentioned forums — as exclusive as they appear to be — are a logical extension of cybercrime forum activity that has been maturing for more than a decade.
As I wrote in my book, Spam Nation: The Inside Story of Organized Cyber Crime — From Global Epidemic to Your Front Door, “crime forums almost universally help lower the barriers to entry for would-be cybercriminals. Crime forums offer crooks with disparate skills a place to market and test their services and wares, and in turn to buy ill-gotten goods and services from others.”
 The interesting twist with forums like Enigma is that they focus on connecting miscreants seeking specific information or access with those who can be hired to execute a hack or supply the sought-after information from a corpus of already-compromised data. Based on her interaction with other buyers and sellers on these forums, Jolles said a great many of the requests for services seem to be people hiring others to conduct spear-phishing attacks — those that target certain key individuals within companies and organizations.
The interesting twist with forums like Enigma is that they focus on connecting miscreants seeking specific information or access with those who can be hired to execute a hack or supply the sought-after information from a corpus of already-compromised data. Based on her interaction with other buyers and sellers on these forums, Jolles said a great many of the requests for services seem to be people hiring others to conduct spear-phishing attacks — those that target certain key individuals within companies and organizations.
“What strikes me the most about these forums is the obvious use of spear-phishing attacks, the raw demand for people who know how to map targets for phishing, and the fact that so many people are apparently willing to pay for it,” Jolles said. “It surprises me how much people are willing to pay for good fraudsters and good social engineering experts who are hooking the bait for phishing.”
Jolles believes Enigma and similar bid-and-ask forums are helping to blur international and geographic boundaries between attackers responsible for stealing the data and those who seek to use it for illicit means.
“We have seen an attack be committed by an Eastern European gang, for example, and the [stolen] database will eventually get to China,” Jolles said. “In this data-trading arena, the boundaries are getting warped within it. I can be a state-level buyer, while the attackers will be eastern European criminals.”
ASK FOR THE SAMURAI
Jolles said she began digging deeper into these forums in a bid to answer the question of what happens to what she calls the “missing databases.” Avivah Litan, a fraud analyst with Gartner Inc., wrote about Jolles’ research in July 2015, and explained it this way:
“Where has all the stolen data gone and how is it being used?
We have all been bombarded by weekly, if not daily reports of breaches and theft of sensitive personal information at organizations such as Anthem, JP Morgan Chase and OPM. Yet, despite the ongoing onslaught of reported breaches (and we have to assume that only the sloppy hackers get caught and that the reported breaches are just a fraction of the total breach pie) – we have not seen widespread identity theft or personal damage inflicted from these breaches.
Have any of you heard of direct negative impacts from these thefts amongst your friends, family, or acquaintances? I certainly have not.
Jolles said a good example of a cybercriminal actor who helps to blur the typical geographic lines in cybercrime is a mysterious mass-purchaser of stolen data known to many on Enigma and other such forums by a number of nicknames, including “King,” but most commonly “The Samurai.”
“According to what I can understand so far, this was a nickname was given to him and not one he picked himself,” Jolles said. “He is looking for any kind of large volumes of stolen data. Of course, I am getting my information from people who are actually trading with him, not me trading with him directly. But they all say he will buy it and pay immediately, and that he is from China.”
What other clues are there that The Samurai could be affiliated with a state-sponsored actor? Jolles said this actor pays immediately for good, verifiable databases, and generally doesn’t haggle over the price.
“People think he’s Chinese, that he’s government because the way he pays,” Jolles said. “He pays immediately and he’s not negotiating.”
The Samurai may be just some guy in a trailer park in the middle of America, or an identity adopted by a group of individuals, for all I know. Alternatively, he could be something of a modern-day Keyser Söze, a sort of virtual boogeyman who gains mythical status among investigators and criminals alike.
Nevertheless, new forums like The Gentlemen’s Club and Enigma are notable because they’re changing the face of targeted attacks, building crucial bridges between far-flung opportunistic hackers, hired guns and those wishing to harness those resources.





While the point about the missing databases is good, any (such as OPM) which involve likely state actors would be hilariously stupid to use that data for anything less than subverting the targets’ personnel for covert operations.
I assume you were alluding to that with the article at least partially, but there was plenty of room to draw the obvious conclusion yourself, no?
This is really interesting, knowing Chinas cybercrime activities I believe “King” could definitely be state-sponsered.
Knowing the web is world wide, and interconnected, and you can spoof, again what state?
Great story.
It’s not hard to extrapolate to people requesting names, email addresses and even credentials of engineers with remote access to water, gas or electric ICS in countries x, y and z.
Well, are there similar forums for “good guy” types to help them gain access to information/personnel who can help to increase their security or extend security skills?
Regards,
Like all legal goods and services, security contractors, services, and courses are widely available and easy to find. No secret forums needed.
That was my thought; if this was some sort of industrial sabotage, wouldn’t the bigger players in their respective fields have people on payroll that could handle this sort of set up in private and away from the prying eyes on such public forums?
Great article,tks. Would be interesting to know more about the logistics behind the transactions,(Kings aside) i.e. how coins are transfered and methods of delivering the data.
State-sponsored, yes, but by whom?
I wouldn’t be surprised if “The Samurai” is NSA or some other Western intelligence operation.
Chinese don’t like to pay.
The Chinese who won’t pay are in a buyer’s market, where the supply is greater than the demand. Commodities commonly go through boom and bust cycles. From what I have read on Brian’s reports, the carder market pays very little per card these days, so it is a buyer’s market.
While the information these criminals seek is probably easily available, the time cost of getting that information is what pressures them to not negotiate. The mobility of the US work force means information about people and their employers has to be fresh to be useful.
These cybercriminal end-operatives are competing with each other to be the first to the punch … er, penetration.
Regarding databases of people, information comes from scraping the websites of LinkedIn, Facebook, various professional engineering organizations, and industry groups. Time-consuming to gather so the bad actors can’t justify obtaining the information themselves.
I wonder if there is a Ferengi Rule of Acquisition that applies to this type of activity?
Good one Soy! Love the Ferengi angle! 😀
Yes, Ferengi Rule of Acquisition number 7:
Keep your ears open and your eyes on the mark.
“China does not pay”
Oh no, China pays. I have had their intelligence solicit me for zero day vulnerabilities which I had access to through my work and company. And, I have heard from peer security researchers in China, that their government, does, indeed pay.
However…
What you may be speaking of is the fact that Chinese intelligence does not work like much Western intelligence. They do not normally hire and pay “agents”, whereas Western intelligence, human intelligence anyway, relies heavily on an “agent model”… where agents typically are very well paid.
This has strong disadvantages: paying agents means that there is a huge chance they may merely be playing the case officer for cash. Which happens all the time. They are also unreliable in many other ways. Western nations tend to be very, very poorly invested in “illegals” operation (overseas, deep cover officers entirely off the books and with zero diplomatic cover or even embassy affiliation).
How did Jolles confirm “The Samurai” is from China? Does it also imply “The Samurai” is Chinese?
According to the article, it is Jolles’ sources who claim The Samurai is from China.
It is possible they are correct, despite the seemingly flimsy cover as it would appear to Westerners. Japan and Taiwan are actually China’s number one targets, so this would actually be seen by them as a strong cover. Japan does engage in extensive intelligence operations.
Westerners often can hardly tell Chinese from Japanese, so it does surely appear as a very flimsy cover from their perspective.
Usually a cover, you want to have some knowledge of the area you are pretending to be from. Otherwise, your cover will collapse.
This is a very good article. As you said, the dollar amounts are going down as there’s so much hacked data, it is a buyer’s market. What I brought up a while back was the repackaging impact here as well. I said think Blue Cross. If the price on the black market is going down, well what’s next, repackage and sell it like new data. We don’t license or index data sellers at all (and I have a campaign for a law to do that as who in the heck are they as relates to privacy) so hey there’s a lot of mathematicians hacking out there. A short while back one of the Anonymous guys was quick on Twitter to make me aware of the talent on the other side and I feel it’s a good idea to take that seriously.
They can scrub data, reformat and denormalized and get a product of stolen data for sale that looks like legit data. Nobody’s watching and the price for good data as well as flawed data today with all the data mining and selling in the legit world being worth $180 Billion a year, nobody’s looking.
http://ducknetweb.blogspot.com/2015/02/anthem-data-breachcrooks-want-to-sell.html
We have too much excess scoring of consumers in the US with flawed data and that’s another issue in itself as we are tagged with risks and data that doesn’t even belong. I’m very much against the last Executive Order as it has given companies and banks a license to mine, harvest and sell whatever they want about us. So as long the money bag are there for the legit, the other side will figure out how to get in and get some of that money too, the way it works. I really about ripped the fact off the White House with how I felt about that as they have done nothing for privacy at all.
http://ducknetweb.blogspot.com/2015/09/excess-scoring-of-us-consumers-us.html
I think that buying stolen information like this would be an excellent investment for China. They could take personal info, bank records, social media comments and see who would be ripe for espionage recruiting. A power station attendant, a satellite engineer, a military intelligence officer…needs money, closet pedifile, passed over for promotion. All ripe for bribery or blackmail!
Brian why do you report on these communities or sites after they have become ‘defunct’. I want to read about communities that are up, running, and active NOW so we can go and see what’s going on for ourselves!
If I ran a site dealing in illegal transactions and it appeared in one of Brian’s posts, I’d shut it down ASAP because I’d know I suddenly had a huge target, no pun intended, on my back.
What Bob said. Which would kill any ongoing investigations and allow the scum to get away. I have zero empathy for those that participate in and fund human trafficking (including indirectly). Execution by slow burning should be the only punishment for these scum.
Because this isn’t good OPSEC, as this would kill any current operation (including it’s intelligence)
people in Eastern Europe are low educated I don’t think they can do this things I think USA UK countries blame everything Russia and Eastern Europe Eastern Europe people are good they work hard and live honest life I don’t think Eastern Europeans can do this sophiscated stuff !! Eastern Europeans work construction why they need to steal !?
Well, most people are good hard working people. But few (doesn’t matter where you are from) are scum and have no problem taking from others. Anyone, yes anyone who wants to learn hacking, programming, physics, engineering can with internet access or some good books and mentors. the EU has lots of very smart people, just like everyplace else. A little opportunity will let people do as they wish.
<>
There is a lot of negative Russia talk in many circles of Western Europe, the US, these days. This is only have the Ukrainian situation, and I do believe it continues because that is still “up in the air”.
However, Russia has gone even far more to the extreme in anti-US talk since Ukraine (especially).
And they have a state controlled media, so that at least appears to be partly an official line.
Gallup, Russian Views of Europe, US, across timeline:
https://www.unzcloud.com/wp-content/uploads/2015/06/russia-opinion-on-nato-countries-gallup.png
etc
http://mobile.nytimes.com/2015/09/13/sunday-review/why-russians-hate-america-again.html
Eastern Europe, just has some very active criminal groups online. That is actually a compliment, of sorts. It isn’t because their criminal groups are stupid, it is because they are smart.
Personally, I normally see activity on logs from Eastern Europe as really being Russian, where they are just using Eastern European countries as launch points.
There is some sophisticated and substantial crime in Eastern Europe, but nobody looks at Eastern Europe as invested in doing significant damage to much of anyone else. As they may suspect about the bigger players, like Russia, Israel, US, China, UK, France, and so on.
Eastern Europe has fast internet and poor people. That’s all you need.
If data is “disappearing”, and is not being exploited for financial gain then I would start looking at it being exploited for it’s intelligence/counter intelligence value. I would say the Samurai is a nation state intelligence gathering operation, though whose is a great question. Could be a hidden behind a false flag, or perhaps they are actually Chinese.
Really, I must say this is an astounding article from a site that regularly does perform extremely good investigative journalism in the field. Despite that, on just reading the first paragraph – and even being used to obscure blogs by intelligence and law enforcement insiders – I was really taken back by the level of detail.
It was sourced quickly, to the Shin Bet, and they are a formidable organization.
However, I am disappointed in the traffic relying merely on “sophisticated social engineers” and experienced phishers. I am surprised there is not zero day trading going on, or accomplished and unique rootkit work.
Still, this article, even by its’ self, puts a very good peg in the jigsaw puzzle of “what is going on currently”. Typically, when we see attacks from, say, eastern europe, or criminal oriented attacks from Russia, it is easy to attribute actually to the FSB/SVR.
Historically, likewise, the FBI used to rely on the mafia, and China has relied on street hackers for some level of plausible deniability.
Of course, the forum system has a significant flaw for law enforcement and intelligence agencies. While they ensure trading must go on, both the buyer and seller could be working on the same team, merely generating meaningless traffic to stay on the forum.
On my other point, I do wonder what sort of plausibly deniable channels these sorts of open market opportunities can create for intelligence agencies?
Seems like an all too lucrative market for a patsy mill for national intelligence agencies. Normally, how would you get such groups to do your bidding? Infiltrate them, turn them, you have to get close to them. That is a lot of risk, a lot of money, and a lot of resources.