Last week, I learned about a vulnerability that exposed all 866 million account credentials harvested by pwnedlist.com, a service designed to help companies track public password breaches that may create security problems for their users. The vulnerability has since been fixed, but this simple security flaw may have inadvertently exacerbated countless breaches by preserving the data lost in them and then providing free access to one of the Internet’s largest collections of compromised credentials.
 Pwnedlist is run by Scottsdale, Ariz. based InfoArmor, and is marketed as a repository of usernames and passwords that have been publicly leaked online for any period of time at Pastebin, online chat channels and other free data dump sites.
Pwnedlist is run by Scottsdale, Ariz. based InfoArmor, and is marketed as a repository of usernames and passwords that have been publicly leaked online for any period of time at Pastebin, online chat channels and other free data dump sites.
The service until quite recently was free to all comers, but it makes money by allowing companies to get a live feed of usernames and passwords exposed in third-party breaches which might create security problems going forward for the subscriber organization and its employees.
This 2014 article from the Phoenix Business Journal describes one way InfoArmor markets the Pwnedlist to companies: “InfoArmor’s new Vendor Security Monitoring tool allows businesses to do due diligence and monitor its third-party vendors through real-time safety reports.”
The trouble is, the way Pwnedlist should work is very different from how it does. This became evident after I was contacted by Bob Hodges, a longtime reader and security researcher in Detroit who discovered something peculiar while he was using Pwnedlist: Hodges wanted to add to his watchlist the .edu and .com domains for which he is the administrator, but that feature wasn’t available.
In the first sign that something wasn’t quite right authentication-wise at Pwnedlist, the system didn’t even allow him to validate that he had control of an email address or domain by sending him a verification to said email or domain.
On the other hand, he found he could monitor any email address he wanted. Hodges said this gave him an idea about how to add his domains: Turns out that when any Pwnedlist user requests that a new Web site name be added to his “Watchlist,” the process for approving that request was fundamentally flawed.
That’s because the process of adding a new thing for Pwnedlist to look for — be it a domain, email address, or password hash — was a two-step procedure involving a submit button and confirmation page, and the confirmation page didn’t bother to check whether the thing being added in the first step was the same as the thing approved in the confirmation page. [For the Geek Factor 5 crowd here, this vulnerability type is known as “parameter tampering,” and it involves the ability to modify hidden parameters in POST requests].
“Their system is supposed to compare the data that gets submitted in the second step with what you initially submitted in the first window, but there’s nothing to prevent you from changing that,” Hodges said. “They’re not even checking normal email addresses. For example, when you add an email to your watchlist, that email [account] doesn’t get a message saying they’ve been added. After you add an email you don’t own or control, it gives you the verified check box, but in reality it does no verification. You just typed it in. It’s almost like at some point they just disabled any verification systems they may have had at Pwnedlist.”
Hodges explained that one could easily circumvent Pwnedlist’s account controls by downloading and running a copy of Kali Linux — a free suite of tools made for finding and exploiting software and network vulnerabilities.
Always the student, I wanted to see this first-hand. I had a Pwnedlist account from way back when it first launched in 2011, so I fired up a downloadable virtual version of Kali on top of the free VirtualBox platform on my Mac. Kali comes with a pretty handy vulnerability scanner called Burpsuite, which makes sniffing, snarfing and otherwise tampering with traffic to and from Web sites a fairly straightforward point-and-click exercise.
Indeed, after about a minute of instruction, I was able to replicate Hodges’ findings, successfully adding Apple.com to my watchlist. I also found I could add basically any resource I wanted. Although I verified that I could add top-level domains like “.com” and “.net,” I did not run these queries because I suspected that doing so would crash the database, and in any case might call unwanted attention to my account. (I also resisted the strong temptation to simply shut up about this bug and use it as my own private breach alerting service for the Fortune 500 firms).
Hodges told me that any newly-added domains would take about 24 hours to populate with results. But for some reason my account was taking far longer. Then I noticed that the email address I’d used to sign up for the free account back in 2011 didn’t have any hits in the Pwnedlist, and that was simply not possible if Pwnedlist was doing a halfway decent job tracking breaches. So I pinged InfoArmor and asked them to check my account. Sure enough, they said, it had never been used and was long ago deactivated.
Less than 12 hours after InfoArmor revived my dormant account, I received an automated email alert from the Pwnedlist telling me I had new results for Apple.com. In fact, the report I was then able to download included more than 100,000 usernames and passwords for accounts ending in apple.com. The data was available in plain text, and downloadable as a spreadsheet.
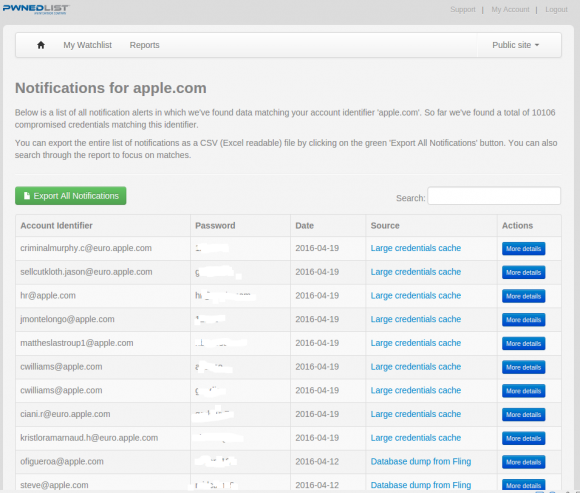
Some of the more than 100,000 credentials that Pwnedlist returned for me in a report on all passwords tied to email addresses that include “apple.com”.
It took a while for the enormity of what had just happened to sink in. I could now effectively request a report including all 866 million account credentials recorded by the Pwnsedlist. In short, the Pwnedlist had been pwned.
At this point, I got back in touch with InfoArmor and told them what Hodges had found and shown me. Their first response was that somehow I been given a privileged account on Pwnedlist, and that this is what allowed me to add any domain I chose. After all, I’d added the top 20 companies in the Fortune 500. How had I been able to do that?
“The account type you had had more privileges than an ordinary user would,” insisted Pwnedlist founder Alen Puzic.
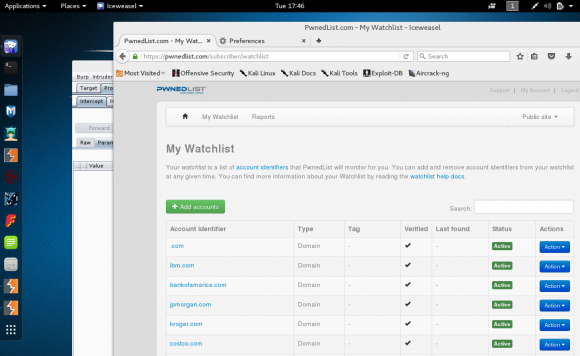
After validating the bug, I added some other domains just for giggles. I deleted them all (except the Apple one) before they could generate reports.
I doubted that was true, and I suspected the vulnerability was present across their system regardless of which account type was used. Puzic said the company stopped allowing free account signups about six months ago, but since I had him on the phone I suggested he create a new, free account just for our testing purposes.
He rather gamely agreed. Within 30 seconds after the account was activated, I was able to add “gmail.com” to my Pwnedlist watchlist. Had we given it enough time, that query almost certainly would have caused Pwnedlist to produce a report with tens of millions of compromised credentials involving Gmail accounts.
“Wow, so you really can add whatever domain you want,” Puzic said in amazement as he loaded and viewed my account on his end.
It’s a shame that InfoArmor couldn’t design better authorization and authentication systems for Pwnedlist, given that the service itself is a monument to object failures in that regard. I’m a big believer in companies getting better intelligence about how large-scale everyday password breaches may impact their security, but it helps no one when a service that catalogs breaches has a lame security weakness that potentially prolongs and exacerbates them.
Update, 12:30 p.m. ET: InfoArmor downplayed the problem on Twitter, noting that “The data that was “exposed” has already been “compromised”- there was no loss of PII or subscriber data.” Also, a new notice is up on Pwnedlist.com, stating that the site is being shut down in a few weeks. The pop-up message reads:
“Thank you for being a subscriber and letting us help alert you of any risks related to your personal credentials. PwnedList launched in 2012 and quickly become the leader in open-source compromised data aggregation. In 2013 PwnedList was acquired by InfoArmor, Inc. a provider of enterprise based services. As part of the transition, the PwnedList Website has been scheduled for decommission on May 16, 2016. If you are interested in obtaining our commercial identity protection, please go to infoarmor.com for more information. It has been our pleasure to help you reduce your risk from compromised credentials.”




Well played, Brian! Love the irony – great article.
They should audit all accounts for this activity and disclose who had what and notify the victims.
…Yes, potentially all 866M of them 😉
This would be the right thing to do.
It might also serve to mitigate against their incompetence and reduce the size and number of lawsuits they are sure to receive as a result of this.
Maybe they could turn their database over to haveibeenpwned dot com.
Yeah, I doubt there is any liability here. They were a service disclosing publicly available information. That would be liking suing me if I put up a website where I regularly described the weather outside my window.
Why not? The government made it illegal for government workers to view any websites of anyone who released publicly-available leaked classified documents (so they literally blocked lots of news sites at their offices)… Look, laws don’t have to make sense or be the least bit reasonable nor even remotely limited… Look at Feinstein trying to outlaw deleting files, paper shredders and throwing away garbage! Ridiculous.
Bob, you’re ignorant whereof you speak. The ban on cleared Feds reading public classified spills maks good sense, it is part of terms of use for government networks, addressing an operational concern about identifying and tracking spills. But idiots like you want to make the authorities look bad, so you go talking through your hat about stuff you don’t understand. There are plenty of times it’s illegal to shred documents too, like during SEC investigations of insider trading, but I guess you think that’s wrong too? Sorry guy, your post should be in the first trash thrown away. You need to up your game a lot. Please start by explaining what your anti-government rant has to do with the topic at hand?
So it’s perfectly reasonable to ban government workers from reading public news? And it’s perfectly reasonable to ban ALL paper shredders (unless every paper shredder scans and saves a copy just in case big brother someday wants a copy), because there are a few cases where people are not allowed to shred documents?
Let’s go back to the news thing. So, because of leaked classified docs, government workers are banned from reading all news released by certain news organizations who dare to defy their leaders wishes and release such docs. This effectively is a ban on government workers becoming educated on how their own employer/government is misbehaving. Can there be anything that is more anti-democratic and pro-totalitarian than a ban on education of misdeeds of those in power? Which of those powerful people are you the mouthpiece for?
It’s scary how many small steps can be skipped while throwing together a website or software that eventually lead to these events…
Looks like pwnedlist.com now shows they’re shutting down May 16, 2016?
There is a new message up at pwnedlist.com –
Website Shutdown Notice
Thank you for being a subscriber and letting us help alert you of any risks related to your personal credentials. PwnedList launched in 2012 and quickly become the leader in open-source compromised data aggregation. In 2013 PwnedList was acquired by InfoArmor, Inc. a provider of enterprise based services. As part of the transition, the PwnedList Website has been scheduled for decommission on May 16, 2016. If you are interested in obtaining our commercial identity protection, please go to infoarmor.com for more information.
It has been our pleasure to help you reduce your risk from compromised credentials.
I was just about to make a similar post…
It’s rather poor form that after they exposed all this authentication data over these years that they appear to be just shutting it down without offering concerned individuals to find out if they had been exposed and reexposed.
This would seem to multiply their original incompetence.
Probably just figured it was cheaper not to bother fixing it, stop offering it for free, and restrict it to enterprise paying customers only.
hmmm… i bet that decommission was put on a higher priority now :0
Kudos to Brian for contacting the site’s owners and not trying to profit off allowing a continuing breach.
Of course Brian disclosed this, it his “job”… but how many others knew about it is the question that we will never have an answer to.
What are the common elements between all these compromised websites?
they’re on the Internet.
First rule of security, if you care about it don’t put it on the ‘net.
As a geek my first response is a smile and a nod.
On a more intellectual level, that’s a cop-out. That’s the easy way out and leads nowhere.
Scissors the ultimate network security tool.
Darn, another investigative list down. Getting to be fewer all the time. Just too bad they couldn’t spend part of their monies on upkeep of what they owned. Personally never found their site. But an open tracker of pwned logins. Now gone dark, dang.
“(I also resisted the strong temptation to simply shut up about this bug and use it as my own private breach alerting service for the Fortune 500 firms).”
Haha! I understand the temptation, but always remember, Brian, that integrity is its own reward
Sleeping at night with a clear conscience is the immediate benefit.
And where is hack? It is data which is available on public, why can’t you check other domain names, of they already have been compromised? I think it is lame story, Bryan
For personal use a free service by Troy Hunt can also be used:
https://haveibeenpwned.com/
This is BS, he doesn’t have 860 million creds 200%
Simply having 800 million creds in itself is no useful feature. That’s because they are (most likely) not validated.
Take a look at https://www.troyhunt.com/heres-how-i-verify-data-breaches/ to see how Troy does that.
I’m a big fan of Troy’s site. In addition to providing a valuable service, he also offers excellent insight on how to deploy an Azure SQL Server configuration.
He also responds to emails at a VERY fast rate.
And what is the story about?
Read the story again, it says what it’s about.
If you still cannot understand it, in short it’s about a website that catalogs user/password breaches and gives and sells that info to others. That catalog site itself stored the data in a way that may have been breached.
If you still don’t understand that, don’t worry about it.
Just follow this important rule:
DO NOT USE THE SAME PASSWORD IN MORE THAN ONE PLACE ON THE INTERNET.
Here’s a story of a sweet skimmer spy-camera teardown. The skimmer was found and “liberated” from an ATM in Bali, Indonesia by Matt South of Trust Foundry.
https://trustfoundry.net/reverse-engineering-a-discovered-atm-skimmer/
Thank you Brian & Bob Hodges. It never never ends, IT security that is.
Oh wow. That was such a good read and a good find on Bob Hodges part! Great article as always!
They are taking the site down:
As part of the transition, the PwnedList Website has been scheduled for decommission on May 16, 2016. If you are interested in obtaining our commercial identity protection, please go to infoarmor.com for more information.
Brian,
Recognizing the temptation, and then resisting it through conscious thought is the essence of character.
Writing of it further demonstrates your credentials as one of the good guys. So thanks are not high enough praise, yet ‘thank you’.
That said, sounds like they piled all the data into a giant silo, then they didnt lock the silo. The excuse that it was already compromised presumes that compromised data was fully exploited. If that were the case, there would be no value to their ‘service’. Thus they pretend the data has value until they lose it and then pretend it had no value. This faulty thinking is faulty accounting…an asset valued whimsically positive valuation one moment, worthless the next, when in fact it was asset and liability the entire time. (One can make an argument, similar to Buffett’s comment on Saturday about derivatives). I suspect that as long as we allow the funny accounting for these types of ‘assets’, we are creating incentive for this nonsense.
Thank you Bob Hodges for the discovery and thanks Bryan for this great article. Certainly brings up the element of “duty of care” on infoarmor’s part. You both have done yours. Would be an interesting case for cyberlaw.
Great ! Quick question from legal point of view if you had downloaded the whole DB, would that lead you to jail even if this info at some point is publicly out ? another thing i just don’t get one thing !! do you really need to download KALI to get burp lmao !
IANAL
The computer abuse act thing means that any breaking of TOS is illegal. So theoretically, a yes is possible.
I doubt they will bother to track anyone down though, and if they did, if one didn’t abuse the list I doubt any consequences would be levied.
I just heard the voice from upstairs. “Just make it work!”
“(I also resisted the strong temptation to simply shut up about this bug and use it as my own private breach alerting service for the Fortune 500 firms).”
Ahh, integrity. ’tis a rare thing these days.
They have a shutdown notice on their site, put up in the past day or two. I wonder what happens to all that data.
I hope someone copied the database and passes it to Troy Hunt.
ok, its just dip of the iceberg i guess so shoukld some hidden hand there,
a real life example of what I’m always talking about, and why what these so called “white hats” is doing is no better and should be illegal.
hmm, he found 200k Apple IDs compromised….. I wonder how….
VERY ironic, how on the right bottom of the page they advertise, that they have been featured on Forbes, WSJ, PCworld….and Krebs!
I received an email from an individual claiming to be an HR recruiter a couple of weeks ago. The individual said he had a job in my professional field and in my local region (he acquired my resume info from LinkedIn or Indeed). The individual’s email domain matched the website that he provided a link to. Doing a little quick search led me to believe that he is a scammer who has contacted others with the goal of getting a hold of victim’s social security number and date of birth.
More than likely this scammer has been collecting SSNs so he could file false return to steal refunds.
I did further research and found that the scammer has created more than twenty fake staffing companies with all the information on the web sites being identical but for the HR directors’ names.
As a warning to others I created a blogger web site with all the information I gathered. It seems the scammer likes using one particular hosting company in Brea California that has let him continue to operate even though I warned them. I think the hosting company likes getting money from criminals since it spends just as well.
You can see the list here:
http://fakestaffing.blogspot.com/
Hey John,
This is Bob from Brian’s pwnedlist article. I’d love to talk to you about the fake staffing scam if you don’t mind. If you read this message, will you contact me via twitter @NanoBob?
Thanks
Bob Hodges
Interesting information plus crappy programming = Hackers dream site, every day of the week. Too bad we don’t have more competent programmers…….
Senor Krebs,
I”m somewhat surprised you don’t know Kali Limux inside and out. But parameter Tampering is easily done using TamperData for troglodyte Windows users wishing to be somewhat capable of security research.
Cheers.