Two young Israeli men alleged to be the co-owners of a popular online attack-for-hire service were reportedly arrested in Israel on Thursday. The pair were arrested around the same time that KrebsOnSecurity published a story naming them as the masterminds behind a service that can be hired to knock Web sites and Internet users offline with powerful blasts of junk data.

Alleged vDOS co-owner Yarden Bidani.
According to a story at Israeli news site TheMarker.com, Itay Huri and Yarden Bidani, both 18 years old, were arrested Thursday in connection with an investigation by the U.S. Federal Bureau of Investigation (FBI).
The pair were reportedly questioned and released Friday on the equivalent of about USD $10,000 bond each. Israeli authorities also seized their passports, placed them under house arrest for 10 days, and forbade them from using the Internet or telecommunications equipment of any kind for 30 days.
Huri and Bidani are suspected of running an attack service called vDOS. As I described in this week’s story, vDOS is a “booter” service that has earned in excess of $600,000 over the past two years helping customers coordinate more than 150,000 so-called distributed denial-of-service (DDoS) attacks designed to knock Web sites offline.
The two men’s identities were exposed because vDOS got massively hacked, spilling secrets about tens of thousands of paying customers and their targets. A copy of that database was obtained by KrebsOnSecurity.
For most of Friday, KrebsOnSecurity came under a heavy and sustained denial-of-service attack, which spiked at almost 140 Gbps. A single message was buried in each attack packet: “godiefaggot.” For a brief time the site was unavailable, but thankfully it is guarded by DDoS protection firm Prolexic/Akamai. The attacks against this site are ongoing.
Huri and Bidani were fairly open about their activities, or at least not terribly careful to cover their tracks. Yarden’s now abandoned Facebook page contains several messages from friends who refer to him by his hacker nickname “AppleJ4ck” and discuss DDoS activities. vDOS’s customer support system was configured to send a text message to Huri’s phone number in Israel — the same phone number that was listed in the Web site registration records for the domain v-email[dot]org, a domain the proprietors used to help manage the site.
At the end of August 2016, Huri and Bidani authored a technical paper (PDF) on DDoS attack methods which was published in the Israeli security e-zine Digital Whisper. In it, Huri signs his real name and says he is 18 years old and about to be drafted into the Israel Defense Forces. Bidani co-authored the paper under the alias “Raziel.b7@gmail.com,” an email address that I pointed out in my previous reporting was assigned to one of the administrators of vDOS.
Sometime on Friday, vDOS went offline. It is currently unreachable. Before it went offline, vDOS was supported by at least four servers hosted in Bulgaria at a provider called Verdina.net (the Internet address of those servers was 82.118.233.144). But according to several automated Twitter feeds that track suspicious large-scale changes to the global Internet routing tables, sometime in the last 24 hours vDOS was apparently the victim of what’s known as a BGP hijack. (Update: For some unknown reason, some of the tweets referenced above from BGPstream were deleted; I’ve archived them in this PDF).
BGP hijacking involves one ISP fraudulently “announcing” to the rest of the world’s ISPs that it is in fact the rightful custodian of a range of Internet addresses that it doesn’t actually have the right to control. It is a hack most often associated with spamming activity. According to those Twitter feeds, vDOS’s Internet addresses were hijacked by a firm called BackConnect Security.
Reached by phone, Bryant Townsend, founder and CEO of BackConnect Security, confirmed that his company did in fact hijack Verdina/vDOS’s Internet address space. Townsend said the company took the extreme measure in an effort to get out from under a massive attack launched on the company’s network Thursday, and that the company received an email directly from vDOS claiming credit for the attack.
“For about six hours, we were seeing attacks of more than 200 Gbps hitting us,” Townsend explained. “What we were doing was for defensive purposes. We were simply trying to get them to stop and to gather as much information as possible about the botnet they were using and report that to the proper authorities.”
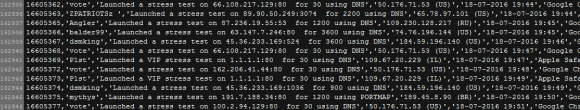
I noted earlier this week that I would be writing more about the victims of vDOS. That story will have to wait for a few more days, but Friday evening CloudFlare (another DDoS protection service that vDOS was actually hiding behind) agreed to host the rather large log file listing roughly four months of vDOS attack logs from April through July 2016.
For some reason the attack logs only go back four months, probably because they were wiped at one point. But vDOS has been in operation since Sept. 2012, so this is likely a very small subset of the attacks this DDoS-for-hire service has perpetrated.
The file lists the vDOS username that ordered and paid for the attack; the target Internet address; the method of attack; the Internet address of the vDOS user at the time; the date and time the attack was executed; and the browser user agent string of the vDOS user.




I think it’s pretty amazing that they started this service since they were 14 (since they’re 18 now, and started in 2012). I know there’s a lot of “hackers” that are 16 years old etc, but for them to have fully functioning business entity that early is pretty impressive.
give these guys a job in cyber security and let them workd for Mossad etc…… do not waste their talents.
So maybe someone else helped them?
Their parents, naturally.
Brian,
Love your security research.. Regarding this one, the attack service used BGP Hijacking technique; this is not outside the realm of even what some ISP’s in the US are using to ‘defend’ against and otherwise pro-actively attack the attackers. So what one is wrong, using the bad guys techniques against bad guys? Or just ignoring the threat or “letting them win” by null routing the IP range, and reporting the attacker to the authorities… Is there a win-win in this one? The internet has still some evolution to contend with in an international community. DNSSec, etc. Things that are being used but not as much… and even some of the more basic fundamental pieces of the internet. The IP protocol(v4, v6) are still affected by the other pieces in the chain.. What I have to ask is … What would be an internationally acceptable form of “defense” against DDOS, etc without the null routing of your own IP range. I admit appliances and App Layer Firewalls are getting smart, but … Still takes resources ($$$). What do ya think? -Jason
Your comment started out intelligently enough, but then you question whether businesses getting attacked be a criminal are justified in defending against it. That’s asinine. What wouldn’t someone be justified in defending themselves against criminal activity? Would someone in the military let the enemy just shoot them dead because they aren’t allowed to use the same technique (firearm) to defend themselves? This sounds like something right out of the dark chasm of political correctness poison.
John, I think you missed the point here – and a little too quickly to be calling someone asinine.
Null routing yourself, I agree, is not a defense. It’s just turning the other cheek.
But attacking the ISP of a suspect, taking all other clients of that ISP down as collateral is more than just an attack. That’s just carpet-bombing the general location of an attacker. There may still be “civilians” there that you’re taking out.
Sure, attack – but there has to be some internationally acceptable forms of attack as Jason suggests.
We can’t be committing war-crimes in retaliation and call that “defense”.
Just wanted to say thanks for the information, it is powerful.
Oh vey it’s another Shoah.
“Huri and Bidani were fairly open about their activities,”
Because they’re the chosen ones hahaha.
I bet you a dozen bagels they don’t go to prison, Brian.
So at least I hope your snitch hacker stole some of their Shekels.
Hi Brian
Have the logs been removed from CloudFlare now?
Typical Millenial hackers…. They feel ENTITLED to take down websites.
Where are their helicopter parents NOW? Hmm?
Are you people kidding me? Give them a job? What kind of message are you sending to the rest of the kids out? Do some big crimes and you will get hired? This guys, regardless of their age knew exactly what they were doing. They did it for money and knew it was wrong.
The fact they blacklisted their own country shows that they don’t want to be victims of what they do to others. They should be jailed for at least 25 years but since they are in Israel they will probably pay a fine and nothing else.
That country has become a safe haven for cyber criminals lately because their government is so soft with their own citizens. It would not surprise me one bit if local researches knew for a long time who they were and who was running that criminal enterprise. They just look the other side since it’s a nice tool they can use as a cyber weapon in the future against other countries. It required, like usual, an American reporter to expose them.
If this guys don’t land in jail, it will show what a joke of a country it really is. They are already free and at home running their next criminal business.
In every other place in the world, even a third world country, they would get at least 5 years minimum if not extradited to the US. The FBI should request extradition immediately. The damage they caused is probably in the billions of dollars. This type of criminals is the reason we can’t have nice things and they are a real danger for the Internet as a whole. People running DDoS services should be punished with the biggest sentences of all since they are a threat to every single citizen in the planet that connects online or depends on the Internet. They are the equivalent of running an organization that sells nuke bombs to extremists. This is exactly what they were doing online.
Are you people kidding me? Give them a job? What kind of message are you sending to the rest of the kids out? Do some big crimes and you will get hired? This guys, regardless of their age knew exactly what they were doing. They did it for money and knew it was wrong. The fact they blacklisted their own country shows that they don’t want to be victims of what they do to others.
They should be jailed for at least 25 years but since they are in Israel they will probably pay a fine and nothing else. That country has become a safe haven for cyber criminals lately because their government is so soft with their own citizens. It would not surprise me one bit if local researches knew for a long time who they were and who was running it. They just look the other side since it’s a nice tool they can use as a cyber weapon in the future. It required an American reporter to expose them.
If this guys don’t land in jail, it will show what a joke of a country it really is. In every other place in the world, even a third world country, they would get at least 5 years minimum if not extradited to the US.
The damage they caused is probably in the billions of dollars. This type of criminals is the reason we can’t have nice things and they are a real danger for the Internet as a whole.
People running DDOS services should be punished with the biggest sentences of all since they are a threat to every single citizen in the planet that connects online or depends on the Internet. They are the equivalent of running an organization that sells nuke bombs to extremists. This is exactly what they were doing online.
Life in prison along with a highly visual campaign in the media that DDOS-ers will be hunted down and made an example of.
These scum hurt real people for profit. I have a friend who runs a small hosting business. Lost half his customers when the datacenter he was running in was constantly getting DDOS’d. This is hurting his family. They are seriously struggling now.
These guys are like mafia. Make an example of them. Be sure script kiddies know whats coming if they keep exploring this area and try to profit from DDOS.
I doubt they are the real force behind it. These kids are just a front for the real admins of this site, their youth is now their defense and they won’t suffer getting caught. All of the carelessness is too obvious.