Recently I came into possession of a series of documents showing the financial books of an organization that orchestrates the distribution of rogue anti-virus attacks or “scareware,” programs that hijack victim PCs with misleading security alerts in an effort to frighten the user into purchasing worthless security software. I found many interesting details in this data cache, but one pattern in the data explains why scareware continues to be a major scourge: Relatively few people victimized by it dispute the transaction with their bank.
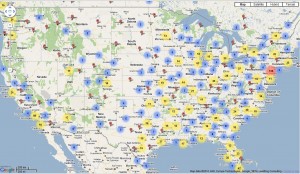
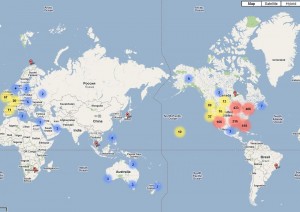 The documents list the amounts charged to more than 2,000 people around the world (the screen shots show the distribution of victims globally and in the United States). Victims paid anywhere from $50 to $100 for the fake anti-virus software. The file lists the amounts charged, partially obscured credit card numbers, and the names, addresses and e-mails of all victims.
The documents list the amounts charged to more than 2,000 people around the world (the screen shots show the distribution of victims globally and in the United States). Victims paid anywhere from $50 to $100 for the fake anti-virus software. The file lists the amounts charged, partially obscured credit card numbers, and the names, addresses and e-mails of all victims.
More importantly, they show that only 367 victims — fewer than 20 percent — bothered to contact their bank or the scammers to reverse the fraudulent charges after the fact.
A second wave of attacks apparently conducted by the same malware gang in early April shows that only 163 out of 1,678 victims – fewer than 10 percent — initiated chargebacks or disputed the sales (the geographic distribution of victims of this second wave is not included in the Google Maps graphics shown here).
I interviewed more than a dozen victims of the first scareware attack, which occurred between April 12 and April 15. All said their computers became unusable and that the only way they could figure out how to regain control of the machine was to surrender and purchase the software. In each case, immediately after the victims submitted their payment information, the hijacking program disappeared, leaving no trace of itself, and no hint of any fake security program on the victim’s machine.
 Some victims reported receiving a follow-up e-mail thanking them for their purchase, and directing support inquiries to support@browsing-solutions.com. Others never got an e-mail, but only saw a charge on their credit card statement from Browsing Solutions, Moscow. Other victims saw charges from an EBD-Software.com.
Some victims reported receiving a follow-up e-mail thanking them for their purchase, and directing support inquiries to support@browsing-solutions.com. Others never got an e-mail, but only saw a charge on their credit card statement from Browsing Solutions, Moscow. Other victims saw charges from an EBD-Software.com.
None of the victims I was able to track down had successfully reversed the charges with their credit card provider, although a few did have the charges canceled after contacting the phone number listed in the customer support e-mail. Some said they had tried to contact their credit card provider or the scam company but got the runaround and simply gave up; others said they were confused because they were in the process of trying to purchase legitimate anti-virus software when their computers were hijacked.
Raymond Zens, a generator technician from Jamestown, N.D., said he had just typed in a search for Symantec Internet Security when his computer was hijacked. Zens said that at the time he thought he had purchased the protection he was seeking from Symantec. It wasn’t until he was contacted by this reporter this week that he realized the computer wasn’t protected with a real anti-virus product.
Brad Pierson, a clinical social worker from Austin, Texas, knew he’d been scammed but said he declined to contest the charge out of shame.
“The embarrassment and feeling of degradation that goes with that made me want to blow it off,” Pierson said. “I just kind of thought, ‘That’s the price you pay for being had.’ I didn’t try to do anything about it. I was just glad to have my hard drive and data intact after the whole thing.”
Clearly, few of the victims of rogue anti-virus would describe themselves as computer experts or even intermediate computer users. Still, it’s remarkable that so few people would bother to dispute the charges, said Gary Warner, director of research in computer forensics at University of Alabama at Birmingham.
Warner said he was in San Diego for a conference earlier this year and was staying a hotel when he noticed one of the hotel’s business center computers was running a notorious rogue anti-virus product. Warner said that he alerted a hotel staff member to the infection, then watched in amazement as the staffer right-clicked on the program’s icon in the Windows task bar, selected “update,” and then proceeded to run a scan and declare that nothing seemed to be amiss.
“On the one hand, it’s amazing that these [scammers] can make so much money,” Warner said. “But the fact is that they’re able to sell something that’s fraudulent and not have people complain either because they think it’s real or they’re embarrassed to say something. The real crime, of course, is that many of these people also think this worthless product is going to protect them.”
Warner said he believes rogue anti-virus will continue to be a scourge as long as banks do little to identify the merchant accounts associated with these rogue anti-virus companies.
“The other side of this is, maybe people just don’t know how to report this kind of fraud,” Warner said. “Truthfully, who are you going to get to take law enforcement action against these scammers? In each of these situations, you’re looking at victims who each lost between $80 and $100, which isn’t exactly grounds for a big federal investigation.”




And embarassment is not only personal. A business’ reputation and stock can be harmed if word gets out that they’ve been scammed, even though the monetary amount is small.
Case in point: would YOU want to give the above hotel/hotel chain your credit card information?
I would think part of it could also be because they did authorize the charge. I would question a charge I didn’t approve in a heartbeat – one I approved, scammed or not, less likely. Much like Pierson said, ‘That’s the price you pay for being had.’ You fell for it, you authorized it, so you pay it.
On the other hand, they didn’t receive the product they paid for… and with that in mind I would question the charge (IF I knew I didn’t get antivirus software). However, I think most people think they did get antivirus software since there is something downloaded which appears to scan their system. So regardless of how well it works – they got something in return for their payment… simply not being satisfied with the product is not a reason to go back to the bank and dispute the charge – it’d be a reason to go back to the company purchased from.
Let’s grant that the charge is legitimate because you did authorize payment.
If you do learn you’ve given your credit card number to criminals, don’t you still call your provider for a replacement card? Your information’s compromised, even if you owed the first charge.
I can understand Pierson’s shame but what has “they did authorize the charge” got to do with anything? These scareware victims authorized payment because they were tricked or blackmailed into doing so to remove fictitious malware. Criminal lies to victim, victim pays criminal, and the victim has to honor the transaction? Makes no sense to me.
Seriously? You’re out of luck because you believed the lies that were meant to make you part with your money for a product they knew was bogus? Are we REALLY back in the age of “Caveat Emptor”?
I voted your comment up T. Anne because I hope it doesn’t get buried, not because I agree with you.
People should absolutely dispute a charge if they believe they got shafted and what they received was not what they ordered and they can’t get satisfaction any other way.
One thing to bear in mind is that most of these rogue AV operations are here today and vapor tomorrow. You’d be lucky if the 800-number is even answered after a few days of ordering from one of these firms. Then what are you left with?
Every single person who gets scammed by rogue anti-virus has a right — no, I would say obligation — to dispute the charge, with their bank, and if that doesn’t work with Visa, Mastercard or whoever the network is.
I spoke today with a gentleman from Visa to find out if they planned to include Rogue AV in this new program they’re rolling out with FTC and BBB, to go after the nutraceutical industry
http://www.coactionmedia.com/compliance-update-changes-to-visas-merchant-chargeback-monitoring-program/
The reason they’re doing that is plainly because that industry has a huge percentage of customers who are unhappy and initiate a chargeback. I asked the guy from Visa why they didn’t include rogue AV in that list, and he said they’re just not seeing anywhere near the number of chargebacks.
By no means am I saying if you know you got scammed don’t report it – what I’m saying is I can see two reasons why it’s not reported as much as it should be: 1. I don’t think many report it because they authorized it and have difficulty disputing a charge that is there by their choice; 2. I don’t think many report it because they don’t really know they were scammed.
So for 1, I could see someone reporting a charge they didn’t approve – but if nothing other than that one charge ever shows up I can totally understand why no one would report it. They approved the charge and don’t see any other side effects – I could see the thought of “well that’s $25 wasted” and not much else in that case. If there aren’t unapproved charges they’re not thinking their credit card information was stolen – if anything they only think they made a one time payment and their information is still secure.
For 2, if you’re not a computer expert and you think you got antivirus software or something that fixed the immediate problem – how would you know you were scammed? Like in the hotel example when they went and ran the fake scan and said nothing was wrong – they didn’t know they were scammed.
I could see it being more of a “I think I got a bad product, and I think that’s my fault for not researching” type of siutation. I may try to go back to the company I purchased from (and if I couldn’t reach anyone, I might cue into the fact that I was scammed and then go report it)… but if I don’t reach out to the company and I don’t know I was scammed, why would I report it or dispute the charge? And if I have something that I actually think is working well (like the hotel example again), why would I report it or dispute the charge?
I agree with your #2 but your #1, as stated, is illogical. Agreement to pay for scareware removal is based on complete misrepresentation of the facts, e.g., the scareware told the victim his machine was infected (typically) with a horde of malware — this is a complete lie and any agreement the victim entered into with the criminal (scareware removal for a fee) is invalid and unenforceable in court regardless of how willingly the victim authorized the charge then. If you’d written a k$100 check to Ponzi and found out 2 hours later he was running a scam, would you call your bank to kill the check or would you let Ponzi keep the money since you’d willingly authorized payment (wrote the check) then? If it was a $25 instead of a k$100 check, it might not be worth your while to deal with it and you might adopt a “well that’s $25 wasted” attitude in which case your not killing the check would then be based on the best economic use of your time going forward and not on prior willing authorization. #1, as stated, is illogical. Hence I do not believe willing authorization is a reason why victims don’t try to recover losses. Shame, yes. Unaware they’ve been scammed, yes. Best economic use of time, yes. But not prior willing authorization.
If I realized that I had been scammed into paying for fake antivirus with my credit card, not only should I dispute the charge, but cancel the card since it’s been compromised by a shady operation.
I would also worry about any lingering, unseen malware hidden on my computer.
I’ve worked on machines after the victim paid… there is usually at least one suspicious executable or driver left behind, as well as Registry keys that mark .exe files as “low risk” in Internet Explorer.
You mean malingerware? :))
> In each case, immediately after the victims submitted their payment
> information, the hijacking program disappeared, leaving no trace of
> itself, and no hint of any fake security program on the victim’s
> machine.
That might be another hint why the victims didn’t protest too much. Their machine went unstable, they took (blind, ill-advised) action to make it better, and lo it got better. Instantly. I wonder how many of the victims actually had the thought, “There, I fixed it” before moving on with their life.
While the old axiom “You reap what you sow” comes to mind or Ron White’s “You can’t fix stupid” as these people allow themselves to be victimized, I can’t help but get a bit angry thinking about how their inaction of not fighting back actually emboldens the bad guys and keeps them in operation so they can continue to victimize others. It’s as if they’re condoning not only their own bad behavior, but the perpetrators as well! Can they really be that ignorant? (Rhetorical question)
As to fraudulent charges overall, it pays to balance your accounts to the penny to ensure fraud doesn’t slip through unnoticed (a small charge may be a test only to turn larger later). Years ago, I got a $9 dollar and change fraud charge reversed on an old debit/check card (got a new card as well to be safe). The fraud probably came about from some brick and mortal merchant I had used that probably had a compromised system. Like the ignorance of the hotel clerk to rogue AV, you can’t completely trust others to look out for your best interests (it’s also why I NEVER use “shared” computers to access anything of sensitive nature, not even my e-mail accounts!). It’s also why a credit card, that’s not tied to your checking account, is better practice for many things as it provides better fraud protection, as well as, any fraudulent charges don’t come directly out of your checking account. To me, it’s part of the mindset, “An ounce of prevention…”
Brian;
What does the color coding on the maps indicate?
Canoer —
Blue = 1-9 victims
Yellow= 10-99 victims
Red=>100 victims
At first glance, you might say, “What is the relevance of a five-year-old post on computer safety today?” In this case, Brian Krebs is introducing his Washington Post blog on computer security and an overall view of what his readers should expect.
Interesting enough, five years ago I subscribed to a Managed Internet Security Service, developed for the end-user like myself, just for the reason Brian made reference to: “Securing your computer can be confusing at first glance, but taking steps to remain informed about the latest online threats is good first step to protecting yourself.”
I found it simpler to have the professionals take care of the IT security functions for me, which allowed me additional time to become more familiar with Internet security.
Like Brian, I also approached the problem of dealing with security through technology. “This blog will offer pointers on how to do just that, updating you on computer security developments as they arise — Internet scams, innovative viruses and worms, useful security tools and resources, and important security patches for popular software titles.” The thought being, if we can get everyone to lock down his or her PCs, we could get handle on Internet security.
It was not until a few of years later, during a radio interview on CHWradio, when Winn Schwartau answered a question that I proposed to him on how to effect change while keeping the end users safe on the Internet. Winn’s immediate response was, “behavioral modification”. Ever since then, The CyberHood Watch partners, Dave & Bill, are now mindful of the importance of empowering the end users behavior online with common sense practices. Real digital security and safety stems from an ethical understanding on how to behave online, while following a set of common sense, best practice guidelines on how to conduct his or her digital live on the Internet safely.
Communication and awareness coupled with good parenting, technology, and best practices to guide and develop ethical behaviors are today’s current messaging.
david c ballard
Personally, I think that everyone who pays for one of these has the right to dispute the charge. In fact disputing the charges would put a hit on the developers as the banks would catch on to the rogue developers and cancel their merchant accounts.
A major problem is that many of the people who are infected with these types of rogues are not technically savvy people. When they see these alerts, they think its either their current software or something from Microsoft trying to protect them. I receive numerous phone calls from friends and family stating that their AV software is telling them they are infected and what should they do? Then when I see their computer I find its a rogue trying to scam them.
I get emails every day from people who contact me asking for a refund for the rogue they purchased. The fact that they are contacting BleepingComputer because we show up in a search result gives a clue that they are struggling to understand what they are dealing with and are essentially reaching out to anyone they can find. I have also heard many times from these people, after I ask them why they thought that they should contact me, that their credit card companies stated that I had to give the refund. This is even a bigger issue. The credit card companies do not even understand these scams.
With legitimate web sites being hacked, malicious ads being injected into legitimate ad streams, and the quantity of morphs these rogues go through, the only true way to defeat these types of infections is through education. Sadly, I don’t see that happening any time soon.
Brian – interesting story – thanks.
Did anyone raise concerns or fears about challenging payments?
Kind of like if a couple of thugs mug you as you walk out of your house. Prosecutor isn’t real interested in the case, the perps wouldn’t go away for long if at all, do you push for prosecution? “they” know where you live. (even if you use your second amendment rights you still can’t be there or awake 24/7 – do you accept being a victim?)
someone intrudes into your computer, seizes your files, demands a cheap ransom. You pay it and get your PC back unharmed. They have your credit card & IP address (if you even know what that is) – they know where you are. Why piss them off?
I’m not saying this is right or smart. If you’re a PC dummy and this happens, you SHOULD get your credit card reissued, challenge the blackmail payment and IMHO buy a Mac (since you’re unlikely to get up to speed on a PC).
Just curious Brian
If you’re asking whether anyone expressed fears for their personal safety? No.
not for their personal safety
does anyone think along the lines of…
These guys already proved they could lock up my files – if I contest the payment, what’s to say they won’t wipe out my computer?
That’s why backing up your data (on a regular basis) is considered a layer of security in a defense in depth strategy. You can then tell the bad guys to go pound sand because you still have backups of your data and don’t have to be held hostage to their demands. 🙂
Oh, I see. I misunderstood your question. My gut tells me most of these users aren’t thinking that way because they haven’t made the connection between what’s happened and who/what is likely responsible for this industry. That would take a level of awareness on cybercrime matters that is probably beyond most of the users who are victims of this scam.
The problem is the muggers here often leave behind a kind of siphon on your “wallet” – not just in stolen money – but stealing your computer (read “bot”).
Also – please don’t fall into the trap in thinking that Macs are completely safe. There is known malware for macs including bots and rogue AV programs. As of yet they’re not common but as Macs gain market share and the community continues to deny its vulnerable, this is going to change.
““The embarrassment and feeling of degradation”
Is that a real quote? I find it hard to believe. It’s not like someone posted a video of him being pee’d on something.
Of course it’s a real quote. I thought he was being pretty honest, and I’d imagine his feelings describe the way many people feel about getting scammed: Like a sucker. It’s not unreasonable at all for people to not want to call attention to themselves for doing something they believe others will perceive as stupid.
Real AVs know that there are so many Fake AVs. They have to do something to block this websites immediately.
Because the money each user lost is not huge. But the total money snatched from people all around world is really huge. I don’t know why AVs just want to secure only their users.
Acctually Real AV love these “bandits” since they are in the end forcing the users to buy a real av software.
So why stop someone that is generating business?
If they are based in Russia, we won’t have much hope either since they are getting more “dollars” into Russia.
Which makes the Russian government very reluctant to stop it. (they love dollars in their country since it makes their economy stronger).
FBI and other agency’s should take a look into this from a organized crime perspective….
But as usual it takes them a couple of years until they get effective and shutdown the rouge server. (as last time)
The key is the credit card company’s, but they do business and they earn on every transaction..so they like small payments that “only 10%” complain about.
It is the same process as they use when they accept payment for pedophile websites…
They know about it and does nothing unless someone hit them on their head.
Any thoughts on the relative hotspot at the Jersey/NYC vicinity?
People are too narrow minded about this threat. These numerous companies are fake fronts for a few organizations just as the $8 domains are fake fronts too and one of the main reasons is because they commit just enough fraud, charge-backs and complaints to make money but stay under the authorities radar.
If the authorities would wise up and treat the threat & fraud rather than the lost as the important factor we’d see a lot more of these organizations dealt with.
Once in a while, when fed and overwhelming case, something good happens.
http://lastwatchdog.com/wp/wp-content/uploads/100527_Reno_indictment.pdf
My
father-in-law just got hit with one of these right before July 4th. What shocked me most was the difficulties he had getting the chargeback issued and that the card company didn’t automatically re-issue his card.
I think it would be VERY interesting to diccover how the major card issuers would handle the situation and examples of what people had to do in order to get their money back.
In my father-in-law’s case, I had to write a letter to the card company explaining that I was a security expert, that I examined his computer, and that I found a fake anti virus program. How many people would be able to get such a
letter? If it weren’t for my stern prompting, they wouldn’t even have asked for a new card.
Thanks for another interesting post.
It’s unfortunate that credit card users have to jump through hoops to get charges reversed when they are based on a fraud claim.
As Brian has often described, the internet is like the Wild West, and everyone there has to be vigilant, card issuers as well as card holders.
The card issuers themselves are frequent targets of abuse and crime, and have set up complex procedures to protect against fraudulent use of their services. For example, my credit union requires notarized affidavits when a card holder claims that a charge is “fraudulent.” Some other banks require that the card holder file a police report if the charges exceed a certain amount. (Been there, done that, and it’s a real pain, but I understand where they’re coming from.)
Lenders generally don’t issue new cards, or block the old ones, without a specific request, because the majority of requests to reverse charges are not based on fraudulent use, but rather on such things as clerical errors or a merchant’s failure to post a credit.
On further review….
The AV/Computer industry shares much of the blame here.
The idea that all you need is a “Security Suite” and you’re protected from all the bad stuff out there is pure marketing fluff and a complete false sense of security! AV software has NEVER been and never will be a good primary or heaven forbid ONLY defense. These victims and computer users overall would be better served learning about and implementing defense in depth techniques wherein AV software is but one “layer” of security. That alone would drastically cut down on malware infections that cause these rogue AV popups to begin with! (An ounce of prevention! :P)
Also, I strongly believe, despite the attempt to increase security with UAC (User Account Control) in Windows Vista and Windows 7, Microsoft has actually made the overall issue worse. Vista’s overly chatty UAC desensitized people to security pop-ups and conditioned people to just click “Ok” to get rid of the prompt without really understanding what they just did. The same can be said of many of these “Security Suites”. I also believe all the user interface redesigns (or what I call dumbing down eye candy) has further compounded the issue by hiding a lot of the systems underlying functionality and preventing users from learning/understanding some basics on how their computer really functions. While you don’t need to be a computer expert, some basic knowledge of how things work is empowering and allows you to have more control over things so you’ll be less likely to become a victim. Knowledge is power after all. 🙂
I’m not sure its so much the prompts from security suites or UAC thats the problem – as the completete lack of up front – in your face education about what those prompts mean and how to evaluate them.
I agree that Security Suites are not complete protection but more of a problem is that there are many more who only purchase AV only software or worse – go with free AV only software and then say that “they’ve never had a problem”. Those products should be removed from the shelves.
I think you missed the point. Whether it’s Security Suites or stand alone Antivirus, neither should be used as a primary defense! They are “part” of what should be a layered defense! When used as such, they can be effective against known malware should it get past your other defenses, that is as long as they have been configured to get definition file updates on a daily basis since they use signature based detection.
Also, I completely disagree with your statement on AV only or free AV products. Like I said above, they DO provide a level of protection. I myself prefer to use an AV only product as I don’t like Security Suites. First, I think they’re bloatware, second, I don’t need or want all the various “features” they include, and third, they give a false sense of security because of all the “features”. For me, I think a solid Antivirus product that does that function well is more effective. As to those other “features” of security suites, I either don’t need them or want them outright or have better methods of protection for those related functions I do use.
While the AV only product I use isn’t a free one, there certainly are some very good ones out there. AVG, Avast, Clam, BitDefender, Microsoft Security Essentials!
That brings up another point, how do people fall so easily for these rogue AV products when it is rather quite easy to learn about known legitimate ones like I listed above? Answer: via social engineering! 🙁
http://isc.sans.edu/diary.html?storyid=7144
I didn’t miss the point – security suites aren’t a complete answer either as I said earlier – but far better than just installing av alone and leaving it at that. You or I may be able to put together the various defenses from separate sources but the average Joe on the street doesn’t have the resources put in front of him and doesn’t have the knowledge about where or how or even that he should go looking for them in the vast sea of information we call the Internet. He instead relies on the same thing that he was told 20 years ago – AV only.
I admit that yes the security suites do throw in features that are unrelated to good security (looking for tracking cookies from the ad companies, parental controls and my favorite junk – registry cleaners and performance optomizers) However to date in my time since the retailer I work for started doing software repair services in house I have yet to find somone running free av only software who isnt showing multiple signs of infection. I can’t in good concious recommend the free av or any AV only product to average Joe customer I see every day.
And yes I do recommend setting up defense in layers whenever I can get away with it. (The management and corpoprate offices feels that that is not a good use of salesmen’s time to educate customers).
The most sensible comment here.
I worked on a laptop that was infected by that cr@p.
I did a system restore to a point a week before the infection. The trickiest part of the exercise was getting to the system restore function.
But it worked.
I’ve worked on countless machines where this stuff has happened. So far, I haven’t run across anyone that has paid, but I’d bet dollars that there are still files on the machine. On top of that, almost half of the machines with FakeAV on it have rootkit activity that makes it more difficult to remove.
Clean up of an infected machine is pointless – because of rootkits you’ll never confidently say you’ve gotten it all. Format and dig out the mfr’s restore disks is your best option.
ouch – looks like I’m getting beat up on here. – whats the harm in a format that takes an hour with the manufacturer’s recovery discs vs 8 spent on maybe or maybe not getting all of the threats because you couldn’t see them because of a rootkit?
Observation: the US has disproportionately high numbers, given the number of computer users. Is this due to low tech-savvy? Alarmist responses to warnings?
High reliance on Internet Explorer in comparison to Europe where Firefox has higher % representation? Why? Any theories or ideas?
RFI: It would also be instructive to know if any of the areas delineated had higher or lower rates of ‘fight-back.’
When I encounter customers who have paid for Fake Antivirus software, one of the first things I tell them is to call their Credit Card Company’s and dispute the charges. I also recommend that they have the CC company assign them a new card# as well.
While some of these Fake AV scammers may just be trying to make a fast buck, there could be some who will sell your CC# etc. or attempt to make unauthorized charges with it. Better safe than sorry.
Lookup on browsing-solutions.com:
– http://centralops.net/co/DomainDossier.aspx
… shows some interesting info. ‘Same for EBD-Software.com, too.
.
I was fine with this article until the end where you say to buy a mac…like this couldn’t happen on a mac?
@Gary – Where in article do I tell people to buy a Mac?
Reading about all this makes me so glad I shit-canned windows some 4-5 years ago and went to the Penguin. The penguin and its FOSS apps are great, fast, stable secure, NO CRAPWARE. The latest distos Lucid Lynx, Mint9, and PCLinuxOS even out-Mac the Mac….
It doesn’t help that legit companies often use obscure or unrelated names, or outsource Internet billing to unknown entities, when billing arises from Internet transactions.
This name obfuscation translates to uncertainty on the part of the victim, and so many people are overwhelmed with incoming electronic data, that a natural ‘background noise’ level is created, and low value transactions are simply ‘dropped’ form the radar.
The difference in the rate of chargebacks for the diet scams vs the fake AV scams shows that it has a lot to do with people’s lack of confidence in their own computer knowledge.
For the Acai pills, they went to a site advertising diet pills. They were promised they could get a full refund if they weren’t satisfied. They weren’t satisfied, they couldn’t get a refund, so they reversed the charges. The average person feels confident calling up the credit card company and asserting that the website made false claims and that they are due a refund. They have a clear idea of what they were promised and what should have happened.
With rogue AV products, even if they know they were scammed, they may not know how they got the infection (or may be afraid they got it from browsing a site they don’t want to admit to visiting). They may have downloaded it because they believed they already had an infection. The program confirmed their suspicions, they paid the money, and their program said their computer was cleaned. What evidence do they have that the product did not perform as advertised? How do they convince the customer service rep at the bank that it was a scam? While some people are willing to call up and shoot their mouths off complaining about something they don’t understand, most other people consider such behavior inappropriate.
At my retail repair shop, I’ve watched the rogue AV crap “mature” over the past 1-2 years. Early, I could manually track down the infection and rip it out. As the business model proved it’s effectiveness, the rogues became more virulent.
Now, just about every one of these beasties comes in behind a rootkit. And even though I can usually stop the rogue from autoexecuting (some of them still leave their files/registry keys in plain view – script kiddies?), rootkit scans with gmer and radix invariably show the depth of the infection. I can’t empirically prove that the rootkit came from the rogue (or did the rootkit bring in the rogue – chicken/egg), but the degree of infection (rogue being the final straw) is significant.
I’ve marveled at the ability of hackers to have complete control of a computer and leave it with enough speed and functionality that the user has no clue about the presence of the infection. Only when they experience some problem or symptoms, do they bring it in for diagnostics. With a bit of sleuthing, we can usually spot the cause even though it may have nothing to do with the users perceived symptoms.
Internet fraud has taken on many forms. Rogues are an obvious form as discussed in depth all over the internet. But there are other rogues, masquerading as legitimate companies offering repair utilities, registry boosters, ad infinitum, that operate in the open offering snake oil solutions to problems caused by hackers.
Instead of creating the perceived problem with popup scan and holding the user hostage to the fee, the snake oil vendors offer their free scanner that must be downloaded, usually in response to a search.
Heavily advertised as free on the internet and now television, the bait-n-switch tactics then kick in requiring the user to buy the software to fix the problems detected. When the paid solution doesn’t fix anything, exercising the “money back guarantee” becomes nearly impossible.
I’ve completed the first edition of a section on my Malware Removal Guide site dedicated to exposing and educating users about these scams. (Sorry for the self promotion, but this stuff is driving me crazy). Rather than educating each of my customers one-on-one, I want to give them a resource that will help them protect their computers.
http://www.malware-removal-guide.com/internet-fraud.html
Thanks, Tom
These rogue programs infuriate me. In fact I think the people behind them should get the death penalty. I have had like 5 of these infections, some crippling the system so bad malwarebytes and safe mode wouldnt work. Computers are so important to us, someone behind a blatant scam to defraud as many people as possible… i almost think should be tortured!
Anyways, I have been through 5 without doing a reinstall of windows, but it wasnt until this last one, when i worked with a support guy from malwarebytes, does my computer truly feel completely infection free.
My computer was hijack by one of those rogue antivirus program. This happen to twice. I am getting sick and tire of these scam artist! I didn’t buy their stupid software! for the latest one, I went into safe mode and manually remove their scamwere! I wish that homeland security people start cracking down on those scammers!
These rogue scumbags deserve a lot more than the death penalty. They deserve to be tortured for not having the balls to really identify themselves, but like terrorists, hide behind women and children while they do their dirty deeds. Where in the hell is the FBI? These dirtbags deserve to be arrested and thrown down a snakepit pending the start of their trials.