 Spamit, a closely guarded affiliate program that for years has paid some of the world’s top spammers to promote counterfeit pharmacy Web sites, now says that it will close up shop at the end of September.
Spamit, a closely guarded affiliate program that for years has paid some of the world’s top spammers to promote counterfeit pharmacy Web sites, now says that it will close up shop at the end of September.
Spamit administrators blamed the impending closure on increased public attention to its program, which interacted with affiliates via several sites bearing the spamit brand, including spamit.com, spamit.biz, and spamdot.biz.
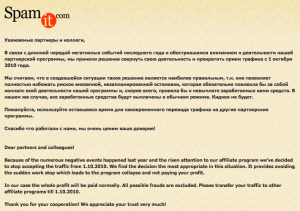
The program’s homepage was replaced with the following message (pictured above) a few days ago:
Because of the numerous negative events happened last year and the risen attention to our affiliate program we’ve decided to stop accepting the traffic from 1.10.2010 [Oct. 1, 2010]. We find the decision the most appropriate in this situation. It provides avoiding the sudden work stop which leads to the program collapse and not paying your profit.
In our case the whole profit will be paid normally. All possible frauds are excluded. Please transfer your traffic to other affiliate programs till 1.10.2010.
Thank you for your cooperation! We appreciate your trust very much!
Dmitry Samosseiko, senior manager of SophosLabs Canada, wrote last year in his excellent Partnerka paper (PDF) that Spamit affiliates are thought to responsible for managing some of the world’s most disruptive, infectious and sophisticated collections of hacked PCs or “botnets,” including Storm, Waledec and potentially Conficker.
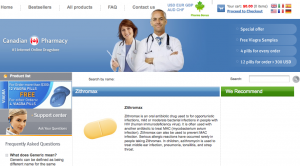
Spamit affiliates are best known for promoting the ubiquitous ‘Canadian Pharmacy’ Web sites, such as the one pictured to the left (zithmed.com). While at any given time there are thousands of these fly-by-night Canadian Pharmacy sites online selling prescription drugs without requiring a prescription, these pharmacies are about as Canadian as caviar: Experts say most of the drugs sent to buyers are made in and shipped from India and/or China.
But don’t expect Canadian Pharmacy sites to go away just because Spamit shutters its operation. Samosseiko and many other spam watchers believe Spamit is the sibling entity of a much larger pharmacy affiliate program known as “Glavmed,” which also promotes Canadian Pharmacy branded sites.
Through periodic statements on the Glavmed forum, Glavmed administrators have steadfastly maintained that their program does not tolerate spam, and that its affiliates only employ legal search engine optimization (SEO) techniques to help people find their sites when searching online for specific name-brand medications.
Anti-spam blog IKillSpammers suggests that one component of the unwelcome “increased public attention” cited in the Spamit goodbye message may be the program’s loss of the ability to process MasterCard payments in December 2009.
There have been other, more public, embarrassments for Spamit lately. For a brief period in late October 2009, the home page for spamdot.biz was changed so that it redirected visitors to the Web site for the Russian Federal Security Service (FSB), a move that suggested to many that the forum had been infiltrated by Russian investigators. A month later, the Russian Association of Electronic Communication (RAEC) declared it was launching a broad new anti-spam campaign.
Also in December of last year, a Newsweek Russia story identified a Russian businessman as the leader of Glavmed, although that story appears to have since been redacted to remove the man’s name after he sued the news organization in a Russian court.
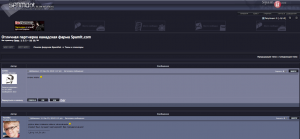
It remains unclear whether Spamit really will close its doors on Oct. 1, and whether the world can expect to see any less junk e-mail as a result. One source with access to the Spamit forum shared with KrebsOnSecurity.com several screen shots of the forum — one of which is pictured above — which show members discussing other pharmacy programs even as they lament the closure of Spamit.
Gary Warner, director of research in computer forensics at the University of Alabama Birmingham’s computer and information sciences department, said the most that can reasonably be hoped for is that some of the spammers affiliated with Spamit will lay low for a while.
“I assume that some [affiliates] will scatter, and a few probably are going to lay low for a bit on the spam side,” Warner said. “But the program’s leadership probably will do something leading in another area of spam, because it’s just too lucrative a business for them to walk away from.”




OT:
Krebs, please do an article on hardware/firmware rootkits (google: PCI rootkits) and how under reported these malware issues go.
I’m assuming that the article you reference is the same one on the front of Slashdot today.
http://dcs.ics.forth.gr/Activities/papers/gpumalware.malware10.pdf
Maybe more people would write about it if it weren’t more theoretical work suggesting interesting, sneakier new ways that malware writers *might* infect your PC.
“OT:
Krebs, please do an article on hardware/firmware rootkits (google: PCI rootkits) and how under reported these malware issues go.”
& RE: “Slashdot article”
No, this is more to the point and these are real threats, I suspect the OP is down voted due to anti virus companies failing to protect against and scan for these dangerous threats:
http://securitywatch.eweek.com/rootkits/rootkits_on_a_pci_card.html
http://www.antirootkit.com/blog/category/pci-rootkits/
http://www.blackhat.com/presentations/bh-dc-07/Heasman/Paper/bh-dc-07-Heasman-WP.pdf
You aren’t hearing about them because they aren’t detected as easily and often mistaken for typical Windows OS glitches or a hardware failure.
More…
http://www.phrack.org/issues.html?issue=66&id=11
http://www.phrack.org/issues.html?issue=66&id=7
http://www.phrack.org/issues.html?issue=64&id=12
http://www.phrack.org/issues.php?issue=66&id=7&mode=txt
Many rootkit tools which find these attacks are less published but they do exist. Many publications fail to consider these real threats and push them as working concepts but little more.
No argument about them being real or potential threats but part of what makes advanced rootkits so dangerous is the fact that they’re undetectable from within mainstream OS and sometimes hard to detect even outside the OS – TDL rootkit for example.
The problem of firmware infections with rootkits or malware can be avoided by putting the necessary firmware (the minimum needed for booting) into ROM and having a hardware jumper that enables Flash memory to be accessed for other firmware functions. And a hardware jumper, that once set, disallows any writes to the Flash memory.
In other words, lockout any changes to firmware.
But people dislike having to go into their computers and mess around with jumpers as the jumpers are tiny, barely labeled with meaningful names, hard to find, easy to mis-jumper, and the jumpers are easy to lose when dropped.
And hotshot computer users want to be able to “Flash the firmware” on-the-fly without having to power down, fiddle with the hardware, and the power up again.
So the manufacturers make computers easy to flash and without jumpers that lockout easy changes to firmware.
I see the problem is still bigger than that – if the original firmware contains rootkits and malware, how is one going to detect it, how is one going to eliminate it ? Notice that China now manufactures most motherboards – in about 10 years organized crime or hostile elements in the government will have fully reverse-engineered the firmware for the BIOS or EFI and and will figure out where they can insert rootkits to enable them to control computers no matter what OS is on them.
It doesn’t help that Intel created their Active Management Technology – see Wikipedia article:
http://en.wikipedia.org/wiki/Intel_Active_Management_Technology
Brian, the Partnerka paper link is broken….
and you misspelled “Affiliate” in the headline 🙂
Whoops. Fixed both. Thanks.
University of Alabama and UAB are two different schools.
The University of Alabama is in Tuscaloosa, AL.
UAB is the University of Alabama Birmingham.
Gary Warner is at UAB!
http://www.askgar.com/aboutgar/
Saturday 9/25 there was a e-mail sent under my yahoo address to all of my contacts with a “CanadianDrugs” link. No message, just a hot link. How was that done and can it be prevented from reoccurring? Does this event have to do with your current report?
Seen it before. Most amusing case, I received one of those emails from my coworker while sitting right next to her! We beelined to her machine and checked her “sent” messages folder and sure enough, her entire contact list was spammed using her account. She sent a mass apology.
It was a free webmail account, three possibilities:
1. user accounts database compromised
2. password was stolen via keystroke logger
3. weak password was brute forced/guessed
Those are the most likely. We changed her password to something proper and she never encountered the issue again (so far).
Oh, I should mention that her account was also Yahoo. Coincidence or compromise? We may never know…
Re: coincidence vs. compromise — it’s neither. Yahoo is just very popular. It’s an attractive target because there are so many users to choose from. You don’t even have to try to guess the password for a particular account — you just pick one commonly used password and try it on lots of different accounts until you find one where it works.
My yahoo account got owned about 2 weeks ago. wtf?
Thanks for the update Brian, I was wondering what was up with linkedIn invites flooding the inbox.
Yahoo is now also accessible from Facebook, which means someone who is compromised on Facebook can also become compromised on Yahoo, maybe vice versa.
We gotta improvise against these compromises.
I notice the Eva Pharmacy people aren’t letting the grass grow under their feet — they’ve got a display ad on the Spamit forum page you’ve posted.
Thanks for the info. There were 4 e-mails in my sent folder, each with a variation of healthxtd.com.
http://www.jrow.healthxtd.com
.sias.healthxtd.com
.jtpz.healthxtd.com
.spjh.healthxtd.com
I have changed passwords and notified Yahoo Security.
Can I do anything else to help stop this kind of thing?
“But don’t expect Canadian Pharmacy sites to go away just because Spamit shutters its operation”
As long as there is demand for these websites, they will still exist along with spam affiliates that will continue to send out related junk e-mail.
I hate to beat on the same drum here, but where are the critical thinking skills? A few examples:
1. You don’t really know who runs the website or where the drugs really come from, so what recourse do you have if you get bad product or don’t receive what you ordered?
2. What about giving your payment information to an unknown entity, especially a debit or checking account? Again what recourse do you have if you’re scammed?
3. Why risk your health using drugs that are of unknown quality and/or content just to save some money?
At least with a local brick and mortar pharmacy, you have a known legitimate company to deal with that has a reputation to uphold and which provides you full legal recourse should something go awry.
fyi., never was a mail order drug customer.
i receive a lot of good information, help and advice from my local pharmacist who also has a degree in molecular biology. am with you on your comments, thanks.
I always wondered why international governments are quick to censor political debate on the web but often do not use similar means to halt medical and pharmacologically illicit or minimally credible websites as well as money laundering.
As often stated that if you follow the money its going to get mobbed up or wind up into somebodies account that some government did not get taxes.
How deep are “affiliate programs” hooked into legitimate banking systems?
Wouldn’t that be the place to really stop these guys– stop it from having it being so easy _and_ lucrative.
Last I heard in US its near impossible for a normal guy to open an credit card processor account without a good set of business documentation.
How are so many fly by nights getting credit card processor accounts?
The conclusion is obvious — there are blind eyes and corruption on the “legitimate” banking side.
Which credit companies & banks are reaping all those transaction fees and all the time avoiding the penalty of fraud by passing those write offs onto customers.
How far does it penetrate?
If every credit card company had to put even 1% out of pocket as a penalty for their total write-offs of wire and internet fraud into a general fund to Interpol and in USA, the FBI, I think that much of this would go away.
The financial sector would quickly tighten up their business practices rather than see profit go to .gov
@Steve: You have to strongly consider the possibility that you have malware on your own computer which is stealing passwords as often as you type in new ones. It’s beyond the scope of comments here, but you could visit spywarehammer.com for help checking your computer. (If you use Internet Explorer to surf the internet, you’re probably infected.)
@JS: Wow, don’t get me started about clueless financial institutions that give merchant accounts to the same criminals that are stealing from them and their customers.
Case in point: One of the Spamit affiliates who was sending me distinctive spam has now shifted to Eva Pharmacy. ksihvolzyg.com and izqupzoapra.net are two of their websites. I happen to know that the Eva Pharmacy websites with those not-quite-pronounceable domain names are registered with stolen identities and credit cards. You just contact the person whose name is in the registration, they confirm they didn’t register any domain names, and you go to the registrar to have the domain shut down.
But when I called for those two domains, registered 9/20, I found that the victims already knew about the charges, and the banks had identified them as fraudulent. In one case the bank called the victim rather than the other way around, so the bank’s anti-fraud mechanisms were capable of identifying the charges as highly likely to be fraudulent.
Yet the domain registrars, who apparently got chargebacks on these registrations, haven’t shut the domains down. And Visa is allowing them to process payments through their payment processing domain, securepaymentshaus.com (registered 8/10/10). And Equifax has issued securepaymentshaus.com an SSL certificate.
Notice that Eva Pharmacy sites don’t accept Mastercard. Mastercard stopped dealing with them years ago when they were called Bulker.biz. Mastercard also recently stopped processing payments for Glavmed/Spamit. So it’s certainly possible for financial institutions to get a clue and stop feeding the criminals who are ripping them off, but only a few do so. (Visa’s representative informed me that they weren’t interested in information about how the same people stealing their card numbers are using Visa accounts to process illegal payments for prescription drugs, because he felt they have a very good anti-fraud department. )
Another case: medicineni.com. Brian covered a LinkedIn spoof spam yesterday. The spam links to a pages on hacked websites that have a redirection to a pharma website, medicineni.com. They also had an iframe which used an SEO Exploit Pack to infect people with ZeuS trojan. Since ZeuS is used to rob banks, and since at least in the case of personal banking accounts, the banks have to eat the losses, you would think they would not want any business relationships with those same criminals. It’s one of the “Pharmacy Express” websites run by the Mailien affiliate program. Brian also mentioned them in his article about their head guy, Leo Kuvayev, being jailed on 50 counts of child rape. But not only hasn’t eNom shut down the domain medicineni.com, the scammers are accepting Visa, Mastercard, Amex, JCB, and Diners Club via their payment processing domain, onlinetransservice.com, also registered with eNom on 8/28/10. None of those companies ought to be having anything to do with an affiliate program whose website display forged pharmacy licenses spoofing the name and address of one of their legitimate merchants. How obvious is that?
If a volunteer like me can find all that information in my spare time sitting at my home computer, what are their very good anti-fraud departments doing?
i got some mail from my contact’s name it was like some reply with the canadian family pharmacy’s link n there was written Read here:then the link was mentioned i dont know weather that contact has sent me that mail or it was something spam because i dont think so that ,my contact will ever try to mail me taht kind of disguesing mail the problem is i cant ask them of it beacuse of some reason but i want to the real matter.