Miscreants who control large groupings of hacked PCs or “botnets” are always looking for ways to better monetize their crime machines, and competition among rival bot developers is leading to devious innovations. The SpyEye botnet kit, for example, now not only allows botnet owners to automate the extraction of credit card and other financial data from infected systems, but it also can be configured to use those credentials to generate bogus sales at online stores set up by the botmaster.
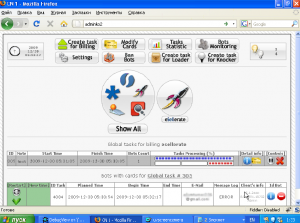 As I noted in a post in April, SpyEye is a software package that promises to make running a botnet a point-and-click exercise. A unique component of SpyEye is a feature called “billinghammer,” which automates the purchase of worthless or copycat software using credit card data stolen from victims of the botnet.
As I noted in a post in April, SpyEye is a software package that promises to make running a botnet a point-and-click exercise. A unique component of SpyEye is a feature called “billinghammer,” which automates the purchase of worthless or copycat software using credit card data stolen from victims of the botnet.
The SpyEye author explained this feature in detail on several hacking forums where his kit is sold, even including a video that walks customers through the process of setting it up. Basically, the scam works like this: The botmaster acquires some freeware utility or legitimate program, renames it, claims it as his own and places it up for sale at one of several pre-selected software sales and distribution platforms, including ClickBank, FastSpring, eSellerate, SetSystems, or Shareit. The botmaster then logs in to his SpyEye control panel (picture above), feeds it a list of credit card numbers and corresponding cardholder data, after which SpyEye opens an Internet Explorer Window and — at user-defined intervals — starts auto-filling the proper fields at the botmaster’s online store and making purchases.
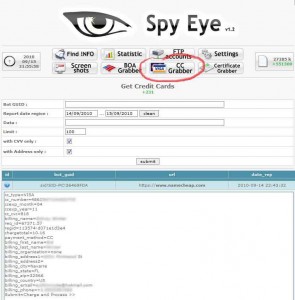 The billinghammer module also is set up to evade anti-fraud controls at the online software stores, by funneling each transaction through a SpyEye-infected system whose Internet address traces back to a geographic location that approximates the cardholder’s street addresss.
The billinghammer module also is set up to evade anti-fraud controls at the online software stores, by funneling each transaction through a SpyEye-infected system whose Internet address traces back to a geographic location that approximates the cardholder’s street addresss.
In the video that shows how to use this portion of the bot kit, it appears that SpyEye customers have the option either to make sales at their own stores, or to use some that are apparently set up by the author of the bot kit himself.
In an e-mail to KrebsOnSecurity.com, FastSpring’s chief customer service officer Ken White said: “We understand what this system tries to do, and how the bad guys attempt to use it to convert stolen cards into cash. We haven’t yet been exploited successfully and believe we have a good system in place to prevent it.”
All other software sales and distribution systems coded into the SpyEye bot kit are entities operated by Digital River, which did not respond to repeated requests for comment. It’s not clear how many — if any — SpyEye customers are using the billinghammer plug-in. But assuming that there are some scammers out there abusing these services through SpyEye, it seems that it would be a great way to catch botmasters in the act. After all, the check or wire transfer for any bogus software sales has to be sent somewhere.




Very interesting article, BK. While it seems to make it easier for fraudsters to turn their ill-gotten info into cash, it also seems to allow law enforcement a place to start looking for the botmasters.
Of course, a smart criminal will also have thought of this, and will use money mules to create and run their “software store.”
“Make money at home! Sell our software online to our already loyal customers. Use our free and easy-to-use tools and keep 8% of the money for yourself as your commission. Simply wire the rest of the money (after taking your commission) to the entity below:”
Nice article that skims the surface of how hackers monetize the hack and try to circumvent anti-fraud tools of the various companies.
For the readers, a tool like this can be used to run traffic and sign ups through affiliate networks to cost per action (CPA) advertising campaigns. In the past, given that the networks get a % of the CPA price for the traffic, networks did little to monitor this. Now a number of the networks, realizing in order to stay active in the industry and win the big clients are hiring in experts/firms to address fraud and abuse of the tracking systems. (full disclosure- My firm Online Intelligence is one such group)
Though affiliate networks do not have access to the credit cards being used to make purchases, they do have data to see a pattern of fraud. Even though a package like this rotates through various IP’s, the time and date of the clicks/leads, the user agent of the computer behind the click and the duration on site are all patterns that indicate a automated/bot is responsible for the leads.
Also if the merchant/advertiser runs the input credit cards and notifies the affiliate network of declinations within 48-72 hours rather than retrying the cards over and over in the hopes the sale will go through, the affialite accounts involved in these schemes can be identified and stopped.
Here is the progression, Hacker steals cards and creates bot network, hacker works with friend or becomes an affiliate marketer himself, hacker runs tracffic through affilaite account to offer using stolen cards. Hacker makes between $2-$50 per bogus sign up.
If the affiliate network and the end merchant work together to review the data collected during the clickthru order path, these fraudsters will be ferreted out.
For those readers attending the DOD cyber crime conference, I will be doing a presentation that walks the audience through the full monetization of the hack form data to cash and how to detect and track the money makers.
Fascinating article… thanks for continually investigating and writing on botnet-based crime. It’s interesting to see how existing vulnerabilities are leveraged in entirely new ways. More of this please!
Just a thought… it might be interesting for readers (myself included) to read a sort of summary of botnets, their associated crimes, the perpetrators arrested and convicted. I get the feeling that almost all the people behind the botnets have gotten away with it. Not just the creators (in most cases), but people who buy a slice of the pie, as well.
Dear Ned;
Along the left side of this page are links to many past articles; just click and see. Brain has done just the thing you suggest before. Keep coming back if you like what you see!
I know I will! 🙂
Pardon me – the RIGHT side of the page. Excuse my dyslexia! 🙁
Your last comment (“…the…wire transfer…has to be sent somewhere”) prompts a thought.
All articles (not just yours) on botnet fraud tend to focus on the sophistication of the trojan malware, the methods for recruiting the money mules and the sometimes devastating impact of the crimes.
However, I never see much discussion or focus on the one link in the chain without which the bad guys could not continue their frauds…and that’s the wire transfer companies such as Western Union.
Surely government agencies and law enforcement must be talking to WU and other similar money transfer companies about how their cash transfer services are the key link in the chain in this epidemic of cybercrime?
Do you have any insight in this area in terms of what WU and others are doing to combat the cybercrims and whether law enforcement are in discussions with them to try and get this under control? Enquiring minds are keen to know!
In 2005, the Western Union was taken to task over fraudulent wire transfers by the states. Check this link for some very interesting reading on this (you will need to edit to get it to work):
http: // doj.nh.gov / publications / nreleases2005/111405western. html
WU was supposed to use an $8.1 million dollar fund for a “national consumer awareness program.” At the time, 58 percent of the total dollars transferred were fraud-induced.
“it seems that it would be a great way to catch botmasters in the act. After all, the check or wire transfer for any bogus software sales has to be sent somewhere.”
Hmm, it does make you wonder if the whole easy-to-use package is one big sting operation.
If I were a criminal, I would steer clear of a product that is too easy to use, because it would mean many more potential competitors using the same product. The more scammers who are using the same method, the faster victims will get wise and find a way to defend themselves. In addition, the criminals that need a very easy interface will be the same ones making mistakes that help law enforcement. You don’t want someone killing the goose that’s laying your golden eggs through careless noobiness.
That is just it; you are too smart to be a criminal. The mind set of a criminal is not to look for legitimate ways to make a living, even though the legitimate work is easier and usually results in more reward in the end.
It (web-crime)is just a lazy way to make a fast buck, and end up in jail; or dead – like some of the web-mafia in Russia that I read about all the time!
Greed always ends up getting the best of them. Even in the mafia, you rarely hear of a successful criminal who gets to retire to Florida and live out life in peace.
I am curious to the reason a product being marketed by a criminal (s) intended for criminal activity, and has no other useful purpose, is not being torn into by the Internet Crime force and FBI? This is not the same as marketing instructions to build a WMD. Whereas, the actual weapon is not being marketed by the vendor.
Hey, Krebs, why does your screenshot feature “unactivated copy of Windows” sign in the system tray?
And why had you disguised browser address string to “adminko”, are you Russian or some?