Online dating giant eHarmony has begun urging many users to change their passwords, after being alerted by KrebsOnSecurity.com to a potential security breach of customer information. The individual responsible for all the ruckus is an Argentinian hacker who recently claimed responsibility for a similar breach at competing e-dating site PlentyOfFish.com.
Late last year, Chris “Ch” Russo, a self-styled “security researcher” from Buenos Aires, told me he’d discovered vulnerabilities in eHarmony’s network that allowed him to view passwords and other information on tens of thousands of eHarmony users.
Russo first alerted me to his findings in late December, right after he said he first began contacting site administrators about the flaw. At the time, I sent messages to several of the administrative eHarmony e-mail addresses whose passwords Russo said he was able to discover, although I received no response. Russo told me shortly thereafter that he’d hit a brick wall in his research, and I let the matter drop after that.
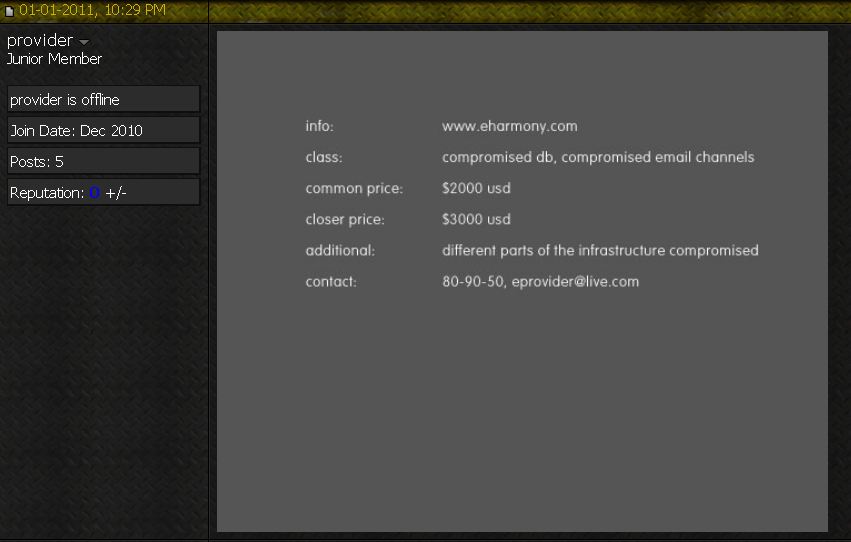
Then, about a week ago, I heard from a source in the hacker underground who remarked, “You know eHarmony got hacked, too, right?” I quickly checked several fraud forums that I monitor, and soon found a curious solicitation from a user at Carder.biz, an online forum that enables cyber crooks to engage in a variety of shady transactions, from buying and selling hacked data and accounts to the purchase and/or renting of criminal services, such as botnet hosting, exploit packs, purloined credit card and consumer identity data. The seller, using the nickname “Provider” and pictured in the screen shot below, purported to have access to “different parts of the [eHarmony] infrastructure,” including a compromised database and e-mail channels. Provider was offering this information for prices ranging from $2,000 to $3,000.
When I contacted Russo about this development, he initially said that he never did anything with his findings, although later in the conversation he conceded it was possible that an associate of his who also was privy to details of the discovery may have acted on his own. At that point, I contacted eHarmony’s corporate offices and shared a copy of the screen shot and information I’d obtained from Russo.
Joseph Essas, chief technology officer at eHarmony, said Russo found a SQL injection vulnerability in one of the third party libraries that eHarmony has been using for content management on the company’s advice site – advice.eharmony.com. Essas said there were no signs that accounts at its main user site — eharmony.com — were affected.
“The SQL dump contained screen names, email addresses, and hashed passwords for account login on the Advice site. Once we learned about the nature of the exploit, we obviously closed it on the network layer and offered the third party vendor help with patching the software, as we do not have access to their source code,” Essas said. “Despite his reports to you, we have found no evidence to suggest that Russo has successfully compromised at the network level our corporate email and eHarmony site environments.”
Essas said Russo approached eHarmony offering to sell security services to help the company fix the flaws, which eHarmony declined.
 “Russo’s fraudulent efforts to obtain money from us are most disturbing,” Essas said. “As such, we are exploring our legal rights and remedies as well.”
“Russo’s fraudulent efforts to obtain money from us are most disturbing,” Essas said. “As such, we are exploring our legal rights and remedies as well.”
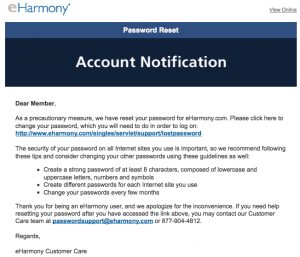
Essas added that “in addition to continuing to assess the situation, we are taking some proactive precautionary measures,” although he declined to say what those measures might be. However, on Wednesday evening, I heard from an eHarmony user who said she had just received an e-mail from the company urging her to change her password.
In the same carder.biz forum, the hacker calling himself “Provider” also is advertising data from other popular Web sites, ostensibly those that he or an associate hacked. For example, one post offers to “1,500,000 American usernames, passwords, emails and more” allegedly taken from the database of small business services provider diversitybusiness.com, for $1,500. In addition, this miscreant also is selling access to the customer database for online electronics store pixmania.com and computer game vendor eidos.com, for similar amounts. Neither diversitybusiness.com nor pixmania.com responded to requests for comment. The general counsel for eidos.com, a division of the Square Enix Group, said the company was investigating the claim but declined to comment further.




This begs 3 questions.
1. Does this mean Russo’s approach to PoF equally self-serving? (Although that doesn’t absolve the amusing nerd-rage from their CEO…)
2. How far can a security research go to sell security services? If you handle landscaping gigs, would you check out various locations for opportunities to improve such landscaping? I’d consider this question more interesting than many will take it at first glance…
3. In this situation, what would Gregory D. Evans do?
I was wondering about your second question as well myself. Russo’s approach is substantially different from my own. If I happen to discover a vulnerability in a site, I make an effort to contact the responsible party and offer the information at “no cost and on contact”. Meaning I do so anonymously because I want nothing from them, and in the case of PoF I don’t want the attention if they choose to go crazy. Most of the time I don’t hear anything back, but I do get the occasional thank you note.
I think Russo’s approach is well intended, but potentially unethical. I have a hard time seeing it as extortion, but it doesn’t exactly come off squeaky clean either. Interesting question to consider though.
I don’t think it’s that complicated. I mean, the reputation issue is there but that’s what PR is for. 😉 People talk about ethics like there’s one definition of ethics and selfish usually equals unethical. This country is a capitalist system, or the social theory of profit maximization. According to it, everyone should act selfishly and social, psychological and market forces will balance things out. Most companies, including eHarmony, act in this fashion. Just like Russo…
eHarmony provides a service, minimizes cost, and tries to maximize value for itself. They externalize or ignore most issues, including some security problems, like most companies. Users may suffer or be totally devastated as a result. One of the few people who are motivated to find/fix security flaws are people like Russo. Is it ethical to charge for company’s services or pay for products/services that help the company, but not pay Russo for his contribution? Why should security be a burden on volunteers that labor tirelessly for free? Why not have companies pay for this highly skilled, difficult work that primarily benefits them and their users?
Capitalist ethics suggest that eHarmony should try to let others (e.g. Russo) find/fix their security problems, but would also say people like Russo should try to make money off it. Sometimes it works out well for one party, sometimes another (see Cleanroom or Fagan process). eHarmony has the resources to pay people like Russo to ensure the security of its apps or implement a low defect development methodology. They didn’t and flaws result. Russo found them and demanded payment for his efforts. They wanted the result of his work, but didn’t want to pay.
Russo is definitely selfish, but so is capitalism (and eHarmony). I find the carelessness of eHarmony and the third-party developer to be more unethical than Russo. After all, it was their actions that caused the problem in the first place & they didn’t want to pay anyone to fix it. They put customers at risk to make more profit, then lie about their commitment to security. That seems a bit… off.
Over the course of the past seven months a certain Mercedes Benz dealer in CA has sold a record number of automobiles and has been duly paid for those cars. The owner of this particular dealership, Mr. Ginolli, has a long standing practice of making duplicate ‘original’ keysets for each automobile his dealership sells. He does this so that he can make available those duplicate original keysets to the car buyers should they lose the keysets they took home when they purchased the car. It is on thier behalf he always copies the keysets. On one unfortunate night, Mr. Ginoli’s nephew, Anthony dropped the entire group of duplicate original keys to ALL the cars that had been sold in the past, record setting seven months. Since he was making a deposit to the Safe Deposit box of Mr. Ginolli and was carrying quite a load of things like money and contracts and loan documents, he failed to notice that he dropped the keysets and they remained lost for some time even though nobody was aware of thier absence from the safe deposit box. Until one day when Mr. Ginolli recieved a visitor to his dealership from a man, Neal Case who claimed to have found the bundle of keys. He explained to Mr. Ginolli how he earns his living by finding metallic treasures on Huntington Beach with his metal detector. He claims to have found hundreds of pieces of jewlery, gold and platinum with diamonds as large as four carrots. He tells how he runs his metal detector over every inch of sand at the beacch before the sand grooming equiptment comes by and prepares the beach for the coming day. He has found many engagement rings and family heirlooms and he has a buyer to whom he sells these treasures every day. But the keysets he found are something he has never before excavated from the sand and he wants to be sure they don’t end up in the wrong hands. Of course he already has a buyer who really want the keysets and is willing to pay $100k for the 121 sets of keys. These keysets are particularly valuable since they are individually tagged with the name and address of the buyer together with the type and color of the car and the VIN number. He tells Mr. Ginolli that he want’s $250k for the keys or he is going to sell those keys to the criminals who offered $100k. He says that the cars will all be in shipping crates by morning on thier way to the Ukraine and to China if Mr. Ginolli is un willing to pay;
You think that this is legal? You think that this is moral? Do you think that you would feel that way had you been one of Mr. Ginolli’s customers and just purchased a brand new $70,000.00 car that is about to be stolen?
I don’t think it is right at all – HOWEVER, that’s for a few reasons… 1) there is a serious price mark up; 2) he knows the key sets will be used for fraud/theft.
Russo, as I understand the situation, is different because 1) he finds the flaw and reports it, apparently offering his services to help fix the flaw. yes, this is for a price – but he’s not threatening to sell his findings to someone else with malicious purposes either. The company can take his findings and go to someone else to have it fixed… and 2) he’s not trying to start a bidding war between the parties to get the most money out of the situation… he’s offering to help and is requesting to get paid for his services. He’s not asking to be paid for finding the flaw, only if they’d like his help in fixing it.
The two situations, while sounding similar, to me are quite different. Do I think the way Russo may be doing it may be causing some questions – yes… but do I think he’s doing anything wrong is asking to get paid for his services – no… if he were saying he’d sell the information to someone else if they wouldn’t hire him, it’d be a completely different story and much closer to the situation you are comparing it to…
EDIT: The (see Cleanroom or Fagan…) part was supposed to be after “low defect development methodology.” I guess revising, multitasking and drinking shouldn’t be combined. lol 🙂
@NickP, better the revising combined with drinking be textual posts not code commits! 🙂
Seriously, you make a good point about the dynamics of capitalism. Some of us are fortunate enough to have jobs that pay well for doing this stuff and allow us time to indulge in some wanderings off the reservation, like this. Others are not so lucky and need to support themselves with freelance activities. Monetizing the hack of a popular website or service can be done in relatively few ways. One is on the black market, another is selling back to the site owner. The sites could view it as hush money, or they could view it as a legitimate service fixing their flaws. That’s really their choice, but is not what they are doing by proclaiming it extortion punishing the hacker for approaching them instead of selling on the black market?
Another way to look at it might be that they should be hiring vendors to fix their security flaws, right? How is it better to hire a firm who is ignorant of their network instead of hiring someone who has demonstrated knowledge and ability to find flaws in their specific installation?
I’m not entirely sympathetic to Russo, I think he is clumsy in his marketing efforts, but I also think there is a strong element of “shoot the messenger” in the reaction of those firms he has hacked.
@ InfosecPro
I pretty much agree with most of your reply, especially the code commits lol. Although, the few times I’ve been drinking doing code commits it was a personal project, the problem was solved, and I still don’t know how the hell it works lol. I ended up rewriting it for maintainability (and to increase my confidence in it 8).
His marketing approach surely draws him criticism. Are there any alternatives, though? He could ask them to pay him plenty of money to go over their software, but they’d probably decline. He could give it to them free, but there’s no benefit to him there. I’m genuinely curious if there is a method of doing this that doesn’t look like extortion. Maybe one’s public, professional reputation could prevent the negative reaction. Idk. The thing I know for sure is that most vendors will take the reaction you pegged: shoot the messenger.
At first, I was inclined to see Russo as this misunderstood vigilante who was really only working to help protect these companies. I appreciate the fact that he is not the one who put the vulnerabilities in place, but if he hopes to build a reputation as an honest businessman, he needs to learn a bit about protecting his reputation.
For one thing, if you have a friend who you think might “take things into his own hands” and sell the product of your research to criminals, you should not share information with that person.
If you wish to assist a company with a security problem, offer them the information on how to fix the problem for free, and THEN offer to assist them in finding and correcting anything else which may be flawed.
I think that reputation is the most important part of the security industry, and Russo’s cutting a dangerous path with his by not being cautious enough when approaching these companies. Putting your finger in the eye of large companies and allowing the situation to be colored so that it appears as though you are extorting money will make it hard to make a living.
I occasionally inform merchants that I do business with, of mis-configured SSL certificates or other problems I see. But I offer it as information only, and of course, I’m a customer who has a right to be concerned with the web-site’s security.
I’m not interested in cracking a site; but who else is going to let web-masters know there is a problem? It’s a dirty job, but how is it going to get done right?
LOL u are on cbiz too
Plenty of STDs, I’ll pass on online dating, TYVM.
These attacks against large websites are getting real crazy, it’s like a play by play, day by day, who’s gonna get pwned next?
Right or Left Hand is the best and cheapest date around! Only a bottle of lotion and no accidental preggers, no child support checks to write out every month as the beastly women bleed your bank account dry so they can gamble away your hard earned money, no whiny parasite who wants more and more game systems and games, let’s hear it for the one true safe sex route: The Hand!
Hai big boi….
Did you ever think you would make a better criminal than a security researcher ?
Wow, that jsut does not make ANY sense at all dude.
http://www.anonymize.edu.tc
Who uses these sites anyway? It’s the fastest way to spread disease since disco and cocaine. I say congratulations to provider, maybe I will see less of their unrealistic dating commercials.
eHarmony is for losers anyway; everyone knows it. ]: )
If “ethical hackers” is a term with enough meaning that the government can actually advertise to hire some (as it has), then it’s too bad that no informal code of ethics has been created so people can point to it and say, “That action was justifiable, ” or “That was over the line.”
Confidentiality is an important ethical principle, as it protects the site’s users’ personal data — so long as the hacker believes she is the only one utilizing an exploit to access to the site. But at some point, the exploit is already known to criminals and the information on the site has been fully compromised. At that point, after notifying the site owner and giving him a chance to take action, the more ethical choice may be to go public if the owner is taking no steps to notify his users himself.
The devil is in the details. How would an ethical hacker even know what’s for sale on carder sites? Is it likely that an exploit would be found by exactly one person in the entire world, or should we assume the site is fully compromised the moment anyone finds an exploit? How much time after notifying the site owner is a sufficient interval to wait before concluding he is unresponsive and the users need to be notified about their risk via the news media? If the hacker has the skills to help the site owner, how much can the site owner demand she do on a volunteer basis without accusing her of withholding assistance to obtain money (“extortion”)?
@ AlphaCentauri
Off topic. Alpha Centauri was one of the best turn-based strategy games I ever played. The incredible depth of the technology tree, diplomacy, and variety of strategies were nice. I think the winning strategies were somewhat unbalanced though.
The vulnerability we reported to eharmony.com have no relationship with this potential flaws on the entire website.
However I would honestly suggest eharmony.com to make a full penetration testing at this moment of their systems.
Cmon its clear that this guy is just a 2 bit money hungry blackhat trying to look white to maybe get a “gig” and a pay day. First he tries to extort money out of PoF owner by hacking into their site and exporting some of the records, after they dont reach a settlement he threatens to public the database. Now this eharmony thing breaks loose and who knows for how long he had access on their systems and what data he could access / export.
He’s found to be on a known carder forum looking to sell the database, i mean how white hat does that look ?
Not to mention eharmony database must be HUGE, millions and millions of records and he’s selling it for 3k ….
Honestly if i were a prosecutor from argentina i would have a case opened on this guy right now for hacking related felonies.
“prosecutor from argentina”? surely you jest!
http://www.amnesty.org/en/news-and-updates/former-argentine-president-found-guilty-crimes-against-humanity-2010-12-23
They are too busy going after public officials for crimes against humanity to worry about two-bit cyber exploits outside their borders. Besides, if Russo gets a gig it helps their balance of trade!
Maybe if eHarmony and Plenty of Phish worried more about getting their technical flaws fixed and less about looking bad to their customer base there wouldn’t be anything for anyone to hack?
Entertaining to see that all of the discussion revolves around the question what was the reasons and motives of Russo , so I guess the fact that multi-million cashing website implemented sloppy policies in using 3rd party products is ok and acceptable or at least not worth complaining 🙂 ?
Hi,
You mentioned you have track underground forums. I wanted to do the same also but I dont know if those are legitimate underground forums.. Do you have any tips on how to go to real underground forums?
It took me a while to recognize that I cannot depend on somebody to insure my online privacy. During last year I received 3 notes from credit card companies that they experienced breach and …
Currently I am using beHidden.com for my online browsing.
Chris Russo is also known as: s.pusher, blackmamba, bmamba.
”
He has been scamming people for a lot of money over the years and rather than calling him a “Security researcher” I’d give him the title “Professional scammer”.
”
This is the real story… Chris is a degenerate that tried to scam many people on ‘blackhat forums’ selling his worthless impassioned framework exploit kit for thousands of dollars.
When he couldn’t sell it he resorted to using the piratebay hack as a promotion tool to get sales from idiots who were unaware of his previous failure to sell the exploit pack outright.
There is little doubt in my mind that he had nothing to do with the actual exploitation of plentyoffish(or eHarmony) and probably had the vulnerable information handed to him and then took full credit (this is what happened with thepiratebay).
When all his efforts have failed miserably it makes perfect sense he would resort to selling the databases and if it isn’t him directly there is no doubt he is involved.
This moron should be purged from existence, he is the essence of bullshit and not a white-hat or security researcher by any stretch of the imagination.
You couldn’t have said it any better TheTruth!