Ordinary Internet users frequently are scolded for choosing weak, easily-guessed passwords. New research suggests that hackers in the cyber underground are also likely to pick lame passwords for their favorite online forums.
 Last month, KrebsOnSecurity was sent a massive database file that the source said was the user database of Antichat.ru, a Russian language hacker forum that has attracted more than 41,000 users since its founding nearly a decade ago. By matching the user names in the database with those listed in the public pages of the forum, I discovered that I’d been given a snapshot of all Antichat user information and private messages prior to June 2010, when Antichat.ru apparently experienced a forum compromise.
Last month, KrebsOnSecurity was sent a massive database file that the source said was the user database of Antichat.ru, a Russian language hacker forum that has attracted more than 41,000 users since its founding nearly a decade ago. By matching the user names in the database with those listed in the public pages of the forum, I discovered that I’d been given a snapshot of all Antichat user information and private messages prior to June 2010, when Antichat.ru apparently experienced a forum compromise.
I wanted to match the Antichat user names, associated email and ICQ addresses with those of other forums for which I’ve collected user databases. I also wanted to see how many of the passwords were easily crackable. To do this, I enlisted the help of an anti-spam source that has access to some serious hardware and software capable of cracking thousands of passwords per hour.
More than 18,000 of the 41,037 passwords in the database were crackable within a few days. 4,500 passwords were used by five or more individual users.
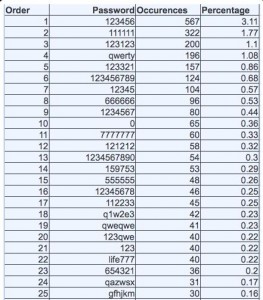
The most easily-guessed passwords were six characters long or less, and 75 percent of the top 20 most common simple passwords were uncomplicated number strings. More than three percent of Antichat users whose passwords were cracked (567) picked one of the simplest passwords, “123456”; 1.77 percent (322) chose “111111”; Just over 1 percent selected “123123”. Another 196 users opted for “qwerty,” a common meme easily typed from left to right across a keyboard. Sixty-five Antichat users picked a single-character password: “0.”
Although nearly half of the Antichat user passwords were crackable, the passwords aren’t useful for gaining access to Antichat user accounts: Forum administrators have changed the site’s login process to automatically tie the user’s credentials to his or her Internet address. However, the Internet address data tied to each account may be of interest to law enforcement investigators.
The Antichat database also included many private messages that forum users sent to each other. Most of these messages are short, banal or unremarkable (e.g., “How do I get this bot working right?”); others appear to involve more serious transactions, including the theft of sensitive personal and financial data from organizations and individuals.
The hardware used to crack the Antichat passwords was an EVGA GTX 295 graphics card running Hashcat software under CUDA. The Antichat forum runs on Vbulletin 3.0, which uses a salted hash to add complexity to stored passwords. Depending on the approach used, the number of hashed passwords processed in an hour ranges between approx 1,000 – 7,000, this compares with many billions of permutations per hour on unsalted hashes.
The number ‘cracked’ per hour depends on the complexity of the passwords and the method of attack being used. My anti-spam associate worked on this hash list for about 18 days, operating 24/7. The total number cracked is 18,225 of 41,037, or 44% of the total.
It may be that many Antichat users weren’t worried about picking strong passwords because they didn’t care whether their accounts got hacked. But it’s important that KrebsOnSecurity readers understand the basic principles for picking strong passwords and for avoiding practices that lead to weak and easily-cracked passwords. Take a look at my password primer for more information.




So if person registered on that internet forum then he automatically becomes hacker?
Of course not. What’s your issue with my use of the term hacker? Are you one of the greybeards in the community who still believes this word can only be used in some idealistic way to describe curious, talented geeks (and I use the term geek with the utmost affection). Or are you a Russian/CIS reader who is upset that I am somehow painting all Russians as bad hackers?
He’s actually got a point. If you look at a lot of hacker forums, most of them don’t know jack. Many are script kiddies, experimenters, absolute noobs or spectators who know real hackers on the forums. Binrev is an example, although white hat oriented. I subscribed to it with a semi-strong, quickly-typed password (account compromise didn’t matter) and participated for a while. There seemed to be about half a dozen very experienced people who posted there. The rest were folks with a wide range of knowledge and experience, mostly seeming a step up from lay people. Many asked extremely basic questions about both hacking tools and operating systems.
So, he might be sarcastic, but his claim is valid. How many of these people are verified hackers who understand the attacks and can perform them? How many had verified instances of using black hat tools or offering services you commonly report on? Or was it just a bunch of user accounts with no confirmation of who has done what? In that case, the weak password thing would be no surprise: they’re NOT hackers.
Most hacking forums are 70%+ B.S. and full of ego-centric morons with above average PC knowledge reciting crap they read on the web. You can tell when they say nonsense like “Linux is secure.” Real hackers might say “Linux is better” because know that *some* Linux systems are secure against *some* types of attacks and believe their control over source & configuration, versus a windows install, reduces risks.
What percentage of Antichat were verified, skilled hackers? This is an important detail if it’s truly a “hacker” site whose “hacker” credentials got compromised… versus a site geared toward hacking that had a small percentage of hackers for users. Big difference there, Brian. A difference worth exploring in an analysis.
The last entry in this list (25th one) is pretty funny cause its could look strong for 6-letter password but this is well known russian dictionary word “password” -> “пароль”->gfhjkm . Generated by typing “пароль” while switched to eng language, instead of russian. 😉
Clever. Nice catch. It goes to show that being clever isn’t better than being truly random. A random, high search space password is mathematically provable to take a huge number of steps if no implementation flaws exist. A clever, but nonrandom, password depends entirely on the luck of the user, as the attacker might be equally clever. You’ve demonstrated this principle quite well. 😉
I guess most people registering on such a site enter once to “see what’s going on”, thus not requiring a safe password.
give me link on db and short private messages.
thanks comrade! (Спасибо братуха за списочек! 🙂
ГЫ =)
аналитик хренов =)
I did a antichat.ru
That fucking shit forums with many lamers.
Best regards from Russia
I think most people do not take a serious consideration in creating password for forums account. Just like what Gorge said, they might just want to have a look at the forum. It is still surprise to see the usage of 123456 password occurred so many times. It had been stressed many times and still people just listen and forget.
A few years ago I saw a news clip (probably CBS news) where John Roberts was testing a password-cracking program. He entered his password and the program cracked it in less than 5 seconds.
The password? konichi-wa [a Japanese greeting], complete with hyphen.
Now, are you sure YOUR password is strong enough? 🙂
Well, it’s a dictionary word, all lower-case, no symbols…what would he expect? Especially on today’s hardware…
Any chance you’ll publish just the cracked passwords? Or just the hashes? I would like to do some analysis on that data set myself, especially comparing it to some of the US forum breaches such as the PHPB list.
Same goes for anonymous. Here are some of their passwords
AnonRyUk -> nickserv: identify MyLif3Rulz
AnotherAnon -> NickServ: IDENTIFY asdfjkl
Bastion -> NickServ: IDENTIFY lanterne
Bastion -> NickServ: identify lanterne
Billlybot -> nickserv: identify billybot budgie69
Billlybot -> nickserv: identify budgie69
Billlybot -> nickserv: identify help
Billybot -> nickserv: identify budgie69
Busirako -> nickserv: identify Chaosium
Cr1SA1 -> NickServ: IDENTIFY crisao09*
CrimsonKing -> nickserv: identify 123456789987654321
Deadward -> NickServ: IDENTIFY wutlol
Der_Bluthund -> NickServ: IDENTIFY endemoniada
DocEvil -> NickServ: IDENTIFY bbc199421
Echelo -> nickserv: IDENTIFY p455w0rd1q2w3e
Emperor_Whimsical -> NickServ: identify blaze11
Emperor_Whimsical -> nickserv: identify blaze11
EsPeJiSmO -> nickserv: identify c4rolin4
Hajiki -> NickServ: IDENTIFY 1337h4x
Hajiki -> NickServ: IDENTIFY anxpv189@$
Joe_Yabuki -> nickserv: identify azazel
Kashiwaba_Tomoe -> nickserv: identify tomoenewed
Kashiwaba_Tomoe_ -> nickserv: identify tomoenewed
Kl4us -> NickServ: IDENTIFY c0p0clephile
LoBot -> NickServ: IDENTIFY pass4egg
M4C -> NickServ: IDENTIFY M4C P455w0rd
M4C_ -> NickServ: IDENTIFY M4C P455w0rd
MacGyver -> nickserv: identify azazel
Mugen -> nickserv: identify sepialoca
Muskui -> nickserv: identify skariot&darkness
Mutiny -> NickServ: IDENTIFY bros4lyfe
OpNoPro -> NickServ: identify batman1927
Piruco -> NickServ: IDENTIFY icaro2011
Psycho -> nickserv: identify Marlene
Radiation -> nickserv: identify nuclear
Ryonymous -> nickserv: identify alpha1010182198
Sabit -> nickserv: identify lawlawl
Sam-L -> nickserv: identify 123456
Shinigami -> NickServ: IDENTIFY 1337#4x0r
Silivrenion[away] -> NickServ: IDENTIFY homework6
SmilingDevil -> nickserv: identify owk426wi
Swahv -> nickserv: identify leinad298198
TheFizz -> nickserv: identify hibillymays
UnrealPancake -> nickserv: identify keepout1
Vertigo -> nickserv: identify 01326fr
Yamajun -> nickserv: identify escarabajo
aKnox -> nickserv: identify pornoM
aldiyen -> nickserv: identify Yay1nt3rN3ts!2
anolio -> NickServ: identify okm09889
anon-ymous -> nickserv: identify logitech123
anon-ymous32 -> nickserv: identify logitech123
anon_weqtq4fgkjrfk -> nickserv: identify foobar
anonemous -> NickServ: IDENTIFY Anonymous
anteaterz2 -> nickserv: identify derzderz
antitodo -> nickserv: identify julio1889
arash -> nickserv: identify paganihuayra
brainsh -> nickserv: identify hxcbmxn1
cooljack -> NickServ: IDENTIFY kekse123
crapulia -> nickserv: identify hispano
d3t3r0k -> nickserv: identify l0r3n1t4
daboogieman -> nickserv: IDENTIFY r2d2c3po9021
daboogieman -> nickserv: identify r2d2c3po9021
dpsi -> NickServ: IDENTIFY dar1997ien
drp -> nickserv: identify metalgear
e -> NickServ: IDENTIFY lolpass2
edgey -> nickserv: identify blackhatcatmakesmehard
gailo -> NickServ: IDENTIFY passwerd
gtn -> nickserv: identify hockey14
hacknwheeze -> NickServ: IDENTIFY Anonymous
halcy -> nickserv: identify iluvero
heyguise -> nickserv: identify p@ss4anon
kk -> nickserv: identify hockey14
kzanon -> nickserv: identify viertel
mR_doigO -> nickserv: identify jojojo**
maximus -> nickserv: identify 12345
moe -> nickserv: identify 1234
nawcom -> nickserv: identify nawben123
opensourcerer -> NickServ: IDENTIFY fajita3a
opoze -> NickServ: IDENTIFY nolimit13
packetfl0 -> nickserv: identify .4n0n0ps!
packetfl0 -> nickserv: identify 4n0n0ps
packetfl0 -> nickserv: identify 4n0n0ps!
packetfl0 -> nickserv: identify 4n0n1rc
packetfl0 -> nickserv: identify 4n0n1rc!
pipe1143 -> nickserv: identify pipe88
plato -> NickServ: IDENTIFY throw1away
pnook|awy -> NickServ: IDENTIFY k27p9f3x
pnook|awy -> nickserv: IDENTIFY k27p9f3x
pr0ject -> nickserv: IDENTIFY mynewpassw0rd
pr0ject -> nickserv: IDENTIFY password
pr0ject -> nickserv: IDENTIFY password1
pr0ject -> nickserv: IDENTIFY pw1
psycho_ -> nickserv: identify nototetremor
sleinad -> nickserv: IDENTIFY lolol
stonedguise -> NickServ: identify p@ss4anon
sylvian -> NickServ: identify 52522704140608
toxin2 -> NickServ: IDENTIFY 21121983geb
turen365 -> nickserv: identify Behemoth0089
xyz -> nickserv: identify FUCKYOU
younghero` -> NICKSERV: IDENTIFY chronic
younghero` -> nickserv: identify chronic
zaiger -> NickServ: IDENTIFY password
zaiger -> nickserv: Identify password
zappe -> nickserv: identify mosquito
ME, I don’t know where you got that list, how it was generated, but if valid, it’s interesting that several on the list appear at first glance to be a nice mixture of numbers, letters and symbols, and relative length. Yay1nt3rN3ts!2 for example, while clearly readable “geek,” one wouldn’t think would be in the typical dictionary. If it and some of the others on the list were retrieved from a salted hash, it makes me wonder if it is possible for the average user to create a memorable password and still be able have it not cracked. If these truly were so retrieved, yet more evidence passwords are dead. That is the user really can’t possibly pick a good enough password, so why try. Ever try to get an average user to use a password safe much less a pseudo-random list of 64 characters including upper and lower case letters, numbers and symbols.
I logged into a forum the other day, and it limited me to letters and numbers and less than ten digits hardly encourages users to pick a good password. Still I think the best thing I can do is encourage users to use different passwords on each system they use. That will at least slow them down and keep folks from logging into your bank after they figured out your password on some bulletin board.
Carl,
Yes there are many “strong” passwords in the list, however there are several weak ones as well. It only takes one password to open the door. I did not have to run these against hashes, I found them in a plain text dump about a month ago. I doubt the are still good. (Although I imagine one or two might be.)
I don’t think passwords are dead, but I do agree that they are dying. I don’t believe that you can create a memorable password that cannot be cracked given the time and resources. Couple that with the ability to use the cloud (it has been done with the amazon loud) to do you computing, as well as being able to use you GPU’s the time factor is shortening.
And for your last point, I completely agree that any site that uses a password needs to open the character set a little more. I say that but it may be for security reasons that they don’t allow those characters. (XSS and such)
The biggest problem in my view is that the sites themselves limit what characters a user can use to make a password secure. Until sites allow the user to choose what characters THE USER wants to use, then those sites will continue to be problematical as far as password safety is concerned. I realize that passwords are all breakable, but strong passwords are less likely to get hacked than easy ones, and until the sites allow really strong PWs then the problem will continue. Kind of like car theft…why waste time with one that’s locked, when others aren’t?
Excellent point, Henry. If you allowed full Unicode passwords, with a mixture of Greek, Cyrillic, Latin and (for the hell of it) Tengwar, it would be nigh-impossible to crack by brute-force attack.
I think this limitation arises not with the site, but with lack of imagination of the coders. “Passwords that aren’t ASCII? Too hard!”
Hello , Barin.
Pls sent me that baze to kodzero@gmail.com
Thnx , best regards .
Why I’m not surprised – tupical antichat users are schoolboys.
What do you want from child?
So this research is useless – better use your graphic card for mining.
that’s one of the reasons why i hate VBulletin. and other open source forum software’s. VB is paid but still its source is easily available on other nulled scripts sites/forums.
Of course, with limitless tries one can eventually guess ANY password that’s short or not completely random.
It would be more secure to limit the number of tries, then lock down the account after, say, three falied log-in attempts. However, a malicious hacker could disable an account if he or she wanted by trying 3 times, but I think most of them want access to your data, not to disable your account.
Is it technically possible to lock out an account when access is attempted outside the range of IP addresses belonging to the legitimate user?
@Gary
A common malicious activity is to purposely fail login attempts in order to lock someone else out of their account. Anyone could do this in their own web browser, not necessarily a ‘hacker’.
Regarding your question, one approach would be to spoof IP and do a login attempt . Use a script to spoof a specific IP in a likely geolocation (Russia), do the # of password attempts required for lockout, have script check for lockout (since you will not receive the responses from your login attempts, IP spoof side effect) and then if it didn’t work go to the next subnet in that geolocation. Once the lockout works, the script can record the subnet that provided success. Then if the user unlocks the account, it can be easily re-locked.
The initial lockout will take a large amount of time until you find the target’s subnet. After subnet is found locking them out again would be trivial.
http://en.wikipedia.org/wiki/Spoofing_attack#Spoofing_and_TCP.2FIP
By the way – the solution to account lockouts is CAPTCHA. That is why Gmail for example have implemented this after a few failed login attempts.
The tools were generally called “Freezers”, and allowed a user to input a target address. The application would then launch continuous login attempts to the target e-mail address with a bad password. Such freezers exist(ed) for Windows Live/MSN/Hotmail, Facebook and many other sites.
https://imageshack.us/photo/my-images/825/antichat.jpg/
“To do this, I enlisted the help of an anti-spam source that has access to some serious hardware and software capable of cracking thousands of passwords per hour.”
A single GTX 295 is not serious hardware, it can be purchased by any Joe Blow for ~300$ and put in their home PC. This is amateur stuff, and in fact there are thousands of kids with home computers that put a single GTX 295 to shame. Not to mention the HashCat tool is publicly available free tool.
Otherwise an interesting article, but don’t overstate the resources you and your associates have… it looks silly.
I bumped your comment. Many of the geeks that spend all their time hacking put thousands into their gear. A $300 graphics card isn’t “serious” hardware today. What the EFF spent to crack DES was serious hardware and they paid enough for it to buy a house. Today, FPGA’s, cryptoaccelerators, Cell processors and GPU’s all make it easier to crack things on the cheap. Serious hardware implementations utilize these and divide the work among many nodes in a cluster, much like the ongoing attacks on RSA algorithm.
An investment of a few grand and some smarter tools could have burned through way more of them in a shorter period of time. The hardware that was used is inferior to what’s in many gaming and video editing PC’s priced under $2,000. A “serious” GPU-based solution would start with a few Tesla boards due to their larger number of cores, huge onboard memory, and superior IO bandwidth. Not to mention the price: a serious attack usually comes with a seriously high price tag.
> By the way – the solution to account lockouts is CAPTCHA. That is why Gmail for example have implemented this after a few failed login attempts.
I’ve seen Russian spammers advertise that they can defeat CAPTCHA
FYI,
Basic CAPTCHA has been broken for years.
Newer more complex revisions are substantially more effective.
It wont help if you can outsource captha solving to some kind of farms or any popular porn resource – you can transparently show captcha to other users who will enter correct answer in order to access other resource. And you just pass their answer to your own script. Its just a bit harder than simple bruteforce. Captcha is not the solution imo. Throtling could work – with exponential delay lock, but this also could be avoided
About the 65 users with the password “0”, if you look at the original data the password was probably something like 000000. From your screenshot it looks like you put them into excel and it truncated the leading zeroes and made it just “0”. I have made the same mistake before!
its not O, its 0.
basically excel doesnt show six zeroes, and replace it with only 1.
000000 -> 0
Seems strange that such website didn’t put simple password strength check during signup process..
I was screwing around and have an account on that site. I remember using one of my throw away passwords I use on sites that have a high likelihood of getting compromised.
Can this list be downloaded somewhere?
44% passwords, 18 days on CUDA?
how about 77% passwords, 8 hours on a regular hardware?
🙂
http://habrahabr.ru/blogs/infosecurity/122633/
While I’m sure most of the members on a site with so many registrations will not be serious hackers (and many will be repeated registrations — with the same password — by people/bots that have been banned), some of the members are “official” representatives of spam affiliate programs who use it as a platform to recruit new members.
Interesting that there is a lot of numeric-only passwords … a lot more than is usual for a generic (english language) user base for example.
However the top used password (123456) is also the No. 1 most common password of all time according to this list here:
http://www.whatsmypass.com/the-top-500-worst-passwords-of-all-time/
I think this post is a nonsence .Brian running out of REAL storys))). why would anyone use a strong password for a FORUM/WEBSAIT/BLOG if they only wanted to visit it once ???
It makes sense doesn’t it? It’s the whole concept of someone having the upper ground on an opponent. Taking advantage of them in every possible way until the underdog finds the metaphorical ladder and attacks from behind. In this case its the “hacker” forums.
Maybe they should invest in a password manager. Couple suggestions for the “hacker” in need.
mylok.ii2p.com
lastpass
roboform
keepass