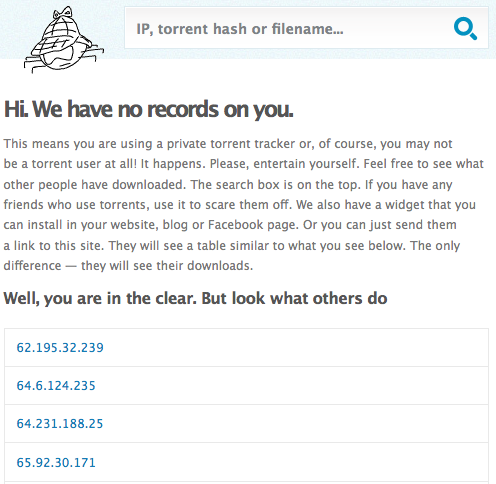
You may have never heard of youhavedownloaded.com, but if you recently grabbed movies, music or software from online file-trading networks, chances are decent that the site has heard of you. In fact, you may find that the titles you downloaded are now listed and publicly searchable at the site, indexed by your Internet address.
 In many ways, the technology behind the site merely recreates in a publicly searchable way what the entertainment industry has been doing for years: It tracks and records information that users share when they download and upload files on public peer-to-peer file-trading networks. But the free service does have the potential to make people think twice about downloading pirated movies, games and music, because it shows how easily this information can be discovered and archived.
In many ways, the technology behind the site merely recreates in a publicly searchable way what the entertainment industry has been doing for years: It tracks and records information that users share when they download and upload files on public peer-to-peer file-trading networks. But the free service does have the potential to make people think twice about downloading pirated movies, games and music, because it shows how easily this information can be discovered and archived.
So far, youhavedownloaded.com has recorded more than 50 million unique Internet addresses belonging to file-sharing users. The site is searchable by file name and by Internet address. When you visit, it automatically checks and lets you know if your Internet address is in the database.
Youhavedownloaded.com offers only limited information about its founders. One of them is Suren Ter-Saakov, a Russian native who now lives in a suburb of Philadelphia. I first interviewed Ter-Saakov for a story I wrote in 2009 about the Federal Trade Commission’s unprecedented takedown of troubled Web hosting firm Triple Fiber Network (3FN). The FTC alleged it was hard to find any customers at 3FN that had legitimate, legal content. Ter-Saakov, better known in the Russian Webmaster industry as Mauser, disagreed and successfully sued the FTC to retrieve his domains and servers.
Ter-Saakov said he believes youhavedownloaded.com indexes about 20 percent of the file-sharing activity on the Internet. He maintains that the site was created merely as a proof-of-concept, and that it doesn’t have any commercial application.
“The whole thing started with a theoretical discussion I had with some friends about what is possible to track through software and what is not possible,” Ter-Saakov said in a phone interview.
The database has some serious limitations. For starters, it may contain incorrect information because it doesn’t take into account that many Internet users have “dynamic” addresses that change from time to time. Also, many homes and businesses use routers that employ network address translation (NAT), which can hide multiple users behind a single public-facing Internet address, so that a single Internet address listed in the database may reflect file-sharing activity of multiple different users.
Ter-Saakov said his servers could store timestamps, machine/browser fingerprints and other data that might help more accurately identify individual users. But he said adding those enhancements would make the project more expensive, and that he and his friends had sought to put together the best system they could for less than $300 a month.
“If we wanted to make it more sophisticated or be able [to be able to track a greater share of file-sharing] users, it’s going to be more expensive, and we see no reason to do that.”
The feedback from visitors has been mixed. The site allows Facebook users to comment on their impressions, and the responses range from horror and anger to amusement. Ter-Saakov said he’s also received many emails from users whose information was listed but who deny having downloaded any files (he also said people can have their information removed on request).
“One guy claimed he downloaded stuff only because his grandmother was ill and he wanted to watch a Harold & Kumar movie to cheer himself up,” Ter-Saakov said. “Another kid wrote and said asked to have his information removed because he was downloading porn and was afraid his parents would be able to see what kind of movies he downloaded.”
I’m often asked whether I download movies, music and software from file-trading sites. My answer tends to be an unpopular one, but I believe most of this activity is simply wrong and unethical. I know plenty of people who would never dream of five-fingering items from a store, or walking out on a restaurant tab, but who routinely turn to file-sharing networks to download copyrighted content. Whether or not you agree with my views on this subject, it’s important to remember that file-trading networks are an extremely common and easy way to spread malicious software.



well, right and wrong of copyright infringement aside, it seems to me that this service subverts privacy. all of a sudden the techniques young billy is using to hide his proclivities from his mom and dad don’t work anymore.
come to think of it, since you can enter any IP address you want on that site, you can find out stuff about other people so long as you can get their IP address (like for example from email headers, or a blog comment).
proof of concept is all well and good, but why enable people to look up data for others? kinda creepy if you ask me.
thinking even further about this, for those whose data in this database is actually incorrect this presents a problem not unlike when one’s records of credit history or criminal history are incorrect.
people can make judgments about you believing they have accurate data and the onus is then placed on you to refute the accusations that data implies. you’re guilty until you can prove yourself innocent, and that may not be easy to do considering how much faith people put in databases.
sure you can have your information ‘removed’ (anyone willing to share the procedure?), but that presupposes you even know about the site in the first place. i’m going to go out on a limb and suggest most people won’t, especially if they have no business appearing in that database in the first place.
i’m starting to think maybe it doesn’t matter whether the information was already public. sharing other people’s information in this context seems ethically suspect.
@ Kurt,
Just to make you even more worried there is a problem with the site based on it not understanding a single salient fact.
Smart phones and Mobile Internet USB modems share IP addresses.
That is because the mobile network operators have so few IP addresses and so many customers an IP address can be “overloaded” amongst as many as two hundred other devices…
So the site needs to record not just both the end IP addresses but both port numbeers as well as the actual time…
If it does not do that then it is being negligent in the extream.
—–BEGIN PGP SIGNED MESSAGE—–
Hash: SHA1
There’s other problems with this method. One of the No. 1 hacker privacy strategies is to do stuff like that through open or cracked WiFi. Then, you have standard proxies, botnets, library computers, misappropriated small business networks, etc. The identifying value of an IP address is very questionable on the modern Internet. Remember when RIAA was suing people without computers and MPAA networked printers for copyright infringement? Q.E.D. 😉
—–BEGIN PGP SIGNATURE—–
Version: GnuPG v1.4.10 (GNU/Linux)
iQEcBAEBAgAGBQJO6Mb5AAoJEFvQ0aBVJJxWK7wIAIWcyqSe/F/RbJnzCF18H79d
6aAJjHMkSHWz/xikAx29TjjlSuSmMLo3iFv8kEVaCWvMZf0t5KgzC0t9n/ZUtTuO
NdCr0JAzttsezOtBfZn2KeOj5s5rqSRxtxf8GQEW2uitBaAPUaJ8CspSfN9lOIOh
N24orwQVh8DVN5eijXMfmEAfq/pwLuUm1ZVxsNW0Z6hQ8HElYwt10rN0eeH7hfAy
iKFNDJy6Fq2NHpI86ShxlAG3kB59g0lqHaFivX3F9O13c+8JsAfKRcQc6Y/l7bU2
iVFpnU0fdd2eiABHPqcYK7JwfAfrKs/FGF8uzF7s+EBfBau/DjKq90MAdb670AE=
=UrSo
—–END PGP SIGNATURE—–
Google has stated that you need to get the idea of privacy out of your head. When it comes to computers this is very true. You don’t want others to know about it, don’t do it on a computer.
you are most likely thinking of google’s previous CEO, eric schmidt.
he did indeed say some unpopular things about privacy online – but what he said was self-serving (it makes google’s life easier if they don’t have to worry about difficult subjects like privacy so it’s better for them if you can be convinced to stop caring about it) and more than a little hypocritical since he proceeded to try and get information about himself taken offline.
personal privacy online is in some ways analogous to corporate security in the cloud. they both traditionally focus on controlling information, and strictly speaking that control is given up when the information goes online. but if people have to give up privacy online then corporations have to give up security – and nobody is willing to accept that. as such it has been deemed necessary for those online entities we entrust our information to (whether personal or corporate) to help us and facilitate the maintenance of that control that we would have otherwise had in the offline world. by extension it is reasonable for us to expect such entities to at least try to keep our information safe, and that’s why privacy violations are such a big deal.
Good thing Eric is a “former” CEO; I thought he was an @ss Hole!!!
I don’t know if somebody at Google said something like that, but the first CEO to say that was probably the CEO of Sun Microssystems, Scott McNealy. And that was in 1999.
http://www.wired.com/politics/law/news/1999/01/17538
“”You have zero privacy anyway,” Scott McNealy told a group of reporters and analysts Monday night at an event to launch his company’s new Jini technology.”
I think the biggest problem is that their data is inaccurate. I sampled 14 IP addresses from our Class B network and got only one hit: from an IP address that isn’t in use. And, when I say “not in use”, what I mean is “this IP address isn’t routed”. Despite how it is presented, the data is unverified and in no way represents the torrent activity (and inactivity I strongly suspect) of the IP address being “checked”.
I don’t think it “subverts privacy”. It should shine a bright light on something that more people need to understand: These things were never private to begin with. The sad thing is we’ve had easy access to genuine hard cryptography for a generation, but people choose not to use it, and don’t insist on it. They prefer to do things in the open, like browsing the web, sending and receiving email, and sharing torrents, as though all these things are somehow private. They are anything but private. Just because it’s not super-easy for random person A to simply browse random person B’s stuff, doesn’t mean random person B’s stuff is _private_.
Here here.
The news here is that we-the-public now have access to another tool that was previously in the hands of a few.
Progress 😀
If anything this may help expose how useless the current monitoring systems are.
your stance on privacy is very much in line with the knee-jerk response most security people have with regards to privacy online. i think it comes from seeing the world through security-coloured glasses.
sometimes that’s a good thing, but i think it’s creating some misunderstanding about privacy. this image of privacy that you present, this perfect (or darn near to it) privacy that encryption can provide – not only does that kind of privacy not generally exist online (as you rightly point out), it doesn’t generally exist offline either.
for example, let’s say you’re in your bedroom with your intimate partner. the door is locked and the curtains are drawn. traditionally one would consider that setting to be private, but with appropriate thermal or radiological imaging combined with a laser bounced off your window at an oblique angle i’d be able to see and here everything that went on in there. under normal circumstances we’d classify that as invading your privacy, but using your own standard for judging whether something is truly private i would have to say that just because the average person can’t source the hardware necessary to see into a locked room doesn’t mean what goes on in there is private.
a more pedestrian example can be found by going through the nude-a-tron at your closest airport. just because the average person can’t see through the coverings you place over your private parts in order to *obscure* them from view doesn’t mean your private parts are actually private.
therein lies the disconnect a number of security people seem have about privacy. although security and privacy share some commonalities, privacy as we know it works via the mechanism of obscurity – something which security folks have long eschewed.
information can private and secure, thanks to the wonders of encryption, but it can also be private and insecure – which is how things work most of the time.
now, i didn’t suggest that these folks invaded anyone’s privacy because, going by their own account, the information was public.
i also didn’t suggest that what these folks were doing was a privacy violation because nobody entrusted their info to them in the first place, so there were no privacy related expectations for them to violate.
instead i refer to it as subverting privacy because they’ve changed the technological landscape in such a way that privacy strategies that had previously been effective (such as those that kept a kid’s porn downloading habits secret from his technologically unsophisticated parents) all of a sudden aren’t, and most people wouldn’t even have realized that had changed.
Good post for sure however AFAIK (I don’t follow the area of intelligence or military advances closely so feel free to point out that I’m wrong as I may well be) but technology to see into rooms using any sort of radiation just doesn’t exist atm.
However seeing as it’s possible (though as I understand it very difficult) to reproduce keyboard strokes and what is displayed on a monitor from some distance away through measuring changes in EMR I think you’re point is valid to be certain. One can could come up with many other examples.
I think it comes down to community expectations – for example your mailbox at your house is not private in the sense that anyone can walk up to it and rifle through the contents within but this isn’t acceptable to most people and hence legislation directs that stiff penalties apply to anyone that does such a thing.
The same expectation would definitely apply to the bedroom. What torrent files you share … I don’t know. Maybe the principle of clean hands applies – since most torrents are links to material that infringes copyright which is illegal in most (but not all) countries should people expect privacy when carrying out this activity?
BTW, just as an aside: not only is non-commercial filesharing legal in Switzerland monitoring of users in swarms has been made illegal through legal precedent as I understand it.
I don’t have the level of detail or references that I think you’re looking for, but I can give you my assertion that Kurt’s bedroom example is grounded in reality. If it gave you the impression of full-color video and Dolby audio, then yes that’s still a bit beyond us.
I’ve read of instances of thermal imaging being used by police to find heat lamps that would imply marijuana plants are being grown. The controversy there is whether a search warrant is needed to permit the use of thermal imaging, or whether perhaps the thermal images could be used as evidence to obtain a warrant. I don’t know how good their cameras would be, but the ones I work with give much more detailed video than the red-green pixels I seem to remember from the movies.
I’ve heard of the laser “microphone,” too. For what it’s worth, Wikipedia has an article about it: http://en.wikipedia.org/wiki/Laser_microphone
As far as that goes, the Wikipedia article on thermal imaging also mentions surveillance under applications (but without a separate article): http://en.wikipedia.org/wiki/Thermal_imaging
Getting offtopic here but when law enforcement uses thermal imaging to detect hydroponic setups they aren’t seeing through walls.
Each situation is different but what basically happens is parts of the structure that the hydroponic setup is contained in heat up in ways that are not normal.
For example if heat energy from the lamps that are being used is striking a concrete foundation then after some weeks the foundation will heat up. Or if the setup is in a basement the air within the basement will heat up the visible base of the house even if light is not striking. Some people even constantly vent warm air out of basement windows etc.
Jane, the case you refer to went to the supreme court and the defendant won. They must obtain a search warrant to use the thermal imaging.
http://en.wikipedia.org/wiki/Kyllo_v._United_States
@ Neej,
All objects have charecteristics defined by their physics that interact with electromagnetic (EM) radiation.
The EM spectrum goes not just from DC to Daylight but well beyond into ionising radiation etc. Some forms of radiation are parts of an atom, Electrons, protons and neutrons these also interact with physical objects.
A physical object can reflect, absorb or transmit all of these depending on the frequency and energy levels and the physical properties of the material.
Further all objects in our normal environment also radiate energy at various frequencies and energy levels.
So by the process of selectivly tuning a recieving device and or a transmitter one of the four proocessecs (radiation, absorbtion, reflection or transmission) will alow a physical object to be “seen” in it’s environment. Even when it is behind another object the frequencies that the obscuring object alows to pass through by transmission will more than likely not be transmitted in the same way as the object of attention. Thus a brick wall can become effectivly translucent to certain EM freuencies whilst the human body is not. Thus the human body will either reflect it or absorb it and this can be used to display the human body.
The important thing to remember is that the ability to resolve detail is dependent on the frequency involved, so low frequencies provide poor definition whilst high frequencies high definition. As a rough rule of thumb anything below one sixteenth of a wavelength is not resolvable. This is why some of the Rapeiscans cannot show hair or the threads in cloth, and effectivly they become translucent and can be seen through.
I could go on to describe other spectrum based techniques where sepectral information is translated into coloured display images to alow the human minds patern matching abilities see minute differences as images but I think I’ve probably said enough for now 😉
Though I agree with you about file sharing, there is no iTunes Store in Russia and legal digital distribution in Russia is still in its infancy. For example, several months ago Steam started listing game prices in Russian rubles. However, some games were removed from the shop as there are official distributors in Russia who offer localized content (all Bethesda Softworks games were removed as well as some other titles). But I’m not interested in Russian versions, I want same content that people in Europe or US can buy and I’m willing to pay the same price which is usually higher than what people pay in Russia (standard edition of TES V: Skyrim is $20 in Russia and $60 in US).
Some companies (like Activision-Blizzard) make special editions. When StarCraft II was released, Blizzard made two cheap editions for Russia ($20 and $30) which had limited subscription to Battle.net (no subscription in Europe or US). Eventually I bought a digital version for the full price ($60).
Of course the market for legal software, movies and music in Russia might be very limited compared to other countries, sometimes it’s hard to find a seller, so there is no other option, but to steal as ordering physical copies doubles the price because of delivery fees.
The Steam region lock thing also affects Europe, especially Germany. With the little difference, that you pay 50 to 100 % MORE than in the US or UK, not less like in east europe.
And the problem with the Bethesda titles is the same: Most of them aren’t available (like the complete id Software catalog), some of them only exist as crippled “low violence edition” with low quality German voice-over (and no other languages to choose). This is a problem, if you live in Germany, but don’t play localized games, because German is not your native language.
Solution: Move out there or download the stuff by other means…
The most disgusting factor in all this is that even legitimate customers are forced to buy or download cracked content, because they can’t get their device to play past the stupid Digital Rights Management embedded in their device. The industry is shooting itself in he foot!!
I can’t begin to relate the hell I go through trying to keep honest customers devices operating DRM for consuming legal content! It can be done, but I can’t blame folks for bypassing the headaches!
Too bad the info on that site is inaccurate as hell.
Is that you “kid who downloaded porn”?
Any mention of how the site works? Where does it pull data from? I assume it uses torrent trackers, but how does it find the torrent trackers to use?
It’s magic 🙂
This is probably the same way the RIAA and MPAA get this data. They participate in the network (though probably without downloading and certainly without uploading) as if they were a peer and they log the requests that they see.
(Most bittorrent clients let you see peer information to a degree. The more advanced ones let you see a lot more. Think of it like a group of people circle kicking hacky sacks; you have to know how to join the circle, then once you have a sack, how to see others to pass it to them.)
This is actually pretty trivial to do; all you need to do is log the information you already have into a database. The whole point of youhavedownloaded.com is highlighting this simplicity.
oops, I didn’t read the whole question.
I presume they do it the old fashioned way: search engines, BT forums, mailing lists, etc.
They claim to have data from private BT networks too, though they don’t publish that freely (because they would get kicked from those networks for it).
I find it amusing that this site also gives links to torrents which other people are downloading.
linking to copyrighted material is criminal contributory copyright infringement!! Sic the Feds on ’em!!
Not all copyrighted material is forbidden to be shared by the copyright holder. This is the fundamental misunderstanding of copyright. I would go as far as to suggest that there are as many copyrighted works being distributed with consent of the author, as there are where the author limits distribution. Consider open source software. It’s generally copyrighted content. It’s also generally allowed to copy and distribute it. Think of the creative commons license, which probably has as much artistic material released under it as all other distribution licenses put together. Much, and possibly _most_ copyrighted material is not a crime to distribute.
@ James M,
Copyright is an awkward thing as it’s legal definition changes from jurisdiction to jurisdiction.
And one thing is clear in most places is that every thing you say, write or do is effectivly copyrighted including derivative works (ie if I read a poem out loud I’m effectivly performing it and have rights over the performance, whilst the author of the poem has rights to say if I can perform it or not).
Three important notions have come up with time,
1, Doctorine of first sale.
2, Fair rights.
3, Presumed consent.
The doctrine of first sale means that a copyright holder relequishes some rights over an individual copy of their work when they sell it. This is so the buy can then sell it on as second hand etc when they have finished with it. Sadly software producers belive that this right does not apply in the case of their product, because they hid behind a faux licence.
The right of fair use, is somewhat nebulous but it alows someone who has purchased a copyrighted work some lattitude of reproducing the work in part. This is important otherwise it would be virtually impossible to produce accademic and other works where quoting small parts is needed.
The last point is very very contentious and applies in all sorts of situations and is the faux notion that if you do something others have a right to assume it applies to them.
For instance this post I’m making on this blog, is copyright to me, the blog is copy right to Brian Krebs and both of us have allowed you to read my comment. However you may not re-publish it on your own site even if you attribute it because by so doing you exceed the fair use doctrine and you require proper permission to make a derived work. You thus cannot “presume consent” by either myself or Brian to do so.
Now the site in question is republishing information about peoples “performance” so it is a derived work, which requires permission, which the site most definatly does not have so it is itself in breach of copyright because it is “presuming consent” where consent has not be given for the site owner to make a derived work of individuals performances.
What the site owner is falsely relying on is that by using an IP address he can obscure the fact he is republishing without consent a derived work of other performances. In many juresdictions if this was brought to court he would receive significant censure.
Sadly the US has some peculiar laws that indicate that if a person collects the data and produces a derived work they can then sell it on etc. Such laws make a mokery not just of privacy, but copyright as well…
When I checked the site it recognized my IP address and listed 20 downloads during November & December. A few were music sites, most were porn, and none of them were sites that I had visited. My internet connection is Hughesnet satellite and my download allowance is 1mb/24hours. Several of the downloads shown were in the 1-3 mb range which could only have been downloaded between 2-7am when Hughes permits unlimited downloads. I checked the Hughes usage page for my account for November & December and there were no downloads anywhere near 1mb either during the day or between 2-7am. I clicked the Remove button on the site, but after 1 hour the erroneous information is still there.
Doesn’t bother me, but the site obviously ain’t worth (you-know-what).
1mb is awfully low… Do you mean gb?
Even with images turned off, just leaving that one comment here used up a third of your download quota for today.
Why do you even bother having the internet?
You re exactly right, Brian Krebs. People should think twice about downloading pirated movies, games, softwares, musics etc. from these sites and pay attention to protect their privacy.
Thanks for sharing; nice finding.
Just visited the site. It said I downloaded one movie (a Tamil Hindi film) using ThePirateBay.com last month.
FWIW, it’s wrong — I never downloaded that movie. Since I don’t have a static IP address, I’m guessing — assuming the site is accurate — that movie was downloaded by the last person to have my IP address.
Interesting article. Here is Sur-Taakov’s profile on Crutop, the forum started and run by your buddy Pavel Vrublevsky:
http://crutop.eu/forum/members/4387/#postings
Am 73 yr old ret financial advisor…tried the site…said I’d visited all sorts of hot babe sites …not sure if they’re porno…all wrong, not anything correct…but it knew I was away from home and up North in our little cabin-in-the-woods by the town name that popped up….How Scare Is That? Must be from the dsl site we use up here. Still Scary! And about the “Free Stuff”…everything is “Free” this time of year and half the other time…free shipping, buy one get one free, sign-up and get free….you can’t blame people of searching for “free”. What’s also funny is that I do download (and pay for) music from some commercial, legal sites and their list did NOT include any of those legitimate ones. So what does that tells you?
People always dispute login information to be correct. Most times it turns out they’ve been hacked or that their WLAN was wildly open…
Plz check the following:
[_] You use something easy to guess as a password, i.e. “password123”, “JimE1938″…
[_] A friend, neighbor, grandchild etc. installed your connection… (and uses grandpa-proxy to rule the interwebs)
[_] Your WLAN is insecure or your router is hacked…
[_] OS, iTunes, Adobe Flash etc. sometimes have been not up to date…
[_] Your IP isn’t static (check with your provider), NAT or you checked internal/local IP…
[_] The PC is infected with backdoor trojan (meebrot/torpig etc.)… [“But my AV-software said everything is clean…” ;-)]
…
Uzzi—none of those seem to apply—I am reasonably certain, without getting overly technical, that site just wishes you would provide more information supposedly to get removed, which of course, they (whoever that is) would never do. They just add whatever additional info is submitted to remove yourself and then use that to hack more into your world. These people must sit up endless nights buring the midnight oils (and probably literally depending upon what country they are doing this from) wasting away their meager existence for whatever value they receive. All I can do is feel very sorry for them and their obviously discarded lifestyle build around misguided inferences and delusionary concepts. Yugggh!
Well – at least if your in a ‘cabin in the woods’, it is unlikely any one popped your WLAN. Doubtful they’d be in range.
I think this is a crashing of cultures.
If someone like Mark Zuckerburg posted this type of data collection there would be mainstream media outrage at privacy issues being if not breached then encroached upon.
In Soviet Russia it was taught to snitch on the other guy by the politbureau; simultaneously _not_ to snitch on the other guy if he paid up tribute as taught by the mob. A few people learned to live off the “in between-ness” value of these positions.
This has the tainted smell of a blackmailware project that can’t yet be used yet either for political or monetary reasons.
I’m sure the founder is right; the project has no legit commercial use, it has only criminal economy potential.
I here you. This was the warning shot.
I’ll get corporate legal ready for the blackmail requests to flow in from the corporate IP space’s “taintedness.”
Persons have already compared the list to Law enforcement and content provider’s IP blocks. Thus my second theory is sparked from discussion at /.
Having a secret or closed P2P network means additional collusion and conspiracy charges on top of copyright violations. The method is an excellent way to have an open P2P network with the snitch nodes from Law enforcement and Content Providers quietly excluded.
Basically its a mechanism to develop a kind of DNSBL for torrents. By monitoring and analyzing IPs and traffic across all trackers you would eventually identify the static sensors deployed by Law and other organizations which are used to monitor activity. I suspect from these snitch nodes the legit cause to request ISP records is made.
These sensor sites would stick out as a heavy weighted node in the P2P graph; have high uptimes, probably have a particular pattern of requesting UL/DL, have big storage; as well as having other attributes like being geo located to commercially hosted data center not a residence or dorm.
In addition with advanced analytics it could also provide a way to feed back by crowdsourcing bad torrent seeds of content which are low quality, rickrolled, or intentionally broken by content producers to damage torrents reputation.
By hooking a torrent client into a filtered torrent tracker list like email uses DNSBL you could instantly screen out static sensors, “suspicious snitch” sites and bad content from the p2p network. The site would be a self maintaining system in a lawless jurisdiction.
Law enforcement and content providers would then be forced to mask their static IP blocks and outsource to hop around IP space. This escalates criminal economy arms race for copyrighted material.
This constant hopping could weaken the quality of prosecution in that it would generate doubt in the minds of juries that the collected data was still valid.
The fall back would be to ISP records of bandwidth and connections which are hopefully for privacy reasons will be retained less and be harder to get for such prosecutions.
In a full IPV6 world this makes even more sense as the NAT world having ended, pirates lost their “feature” which masked much of the activity.
If the stupid MPAA would simply lower the price and get rid of DRM, we wouldn’t be having this discussion. As far as that goes, the entertainment industry doesn’t even try to add value to their products.
When I was a kid, we weren’t interested in copping free recordings (cartridge type). The stores had all kinds of gimmicks that made buying the original content appealing. They don’t even try that now. I’ve pretty much given up buying music at all – and I don’t steal it. I feel I should get the video along with the music – after all I’m an MTV baby!
Is that site’s facebook commenting plug-in a security concern, or is it a third party application that the website’s owners do not have access to?
I had the same concern, just *why* do these people need my friends list, my physical home address when authentication is mandatory to query their database (where the integrity is unknown) and Facebook is the only login method.
It’s just another phishing scheme to match your current dynamic IP with a physical address.
Encrypted VPN to Canada, encrypted proxy into Sweden. My dynamic IP never touches a peer-to-peer network.
Brian, I noticed that like many other recent posts, this one was on slashdot. Could you give us some hit stats? I’m sure many here would be curious to know:
– maximum 5-minute avg number of hits per second to this post (roughly)
– sitewide file reqs for a day like today (html, css, images, etc.)
– total reqs today for a post like this one
Very very curious. 🙂
On topic: the site has no info on me, probably because I don’t torrent stuff. That said, I think such a site will make some people think about their actions, while potentially harming innocents. Concerning dynamic IP addressing: Imagine if every day, everyone in your town drew a number from a hat. All crimes commited that day will be forever entombed into the criminal’s number of that day. So if someone carrying number 171 steals donated groceries meant for a family whose house burned down, then 171 is forever tainted. If you draw it out of the hat later, just imagine the repurcussions! As a lot of posters have noted, the site has incorrect info. Perhaps the site designers should have noted this in testing and either fixed the application or shelved it.
My favorite part of this article is when I got to copy and paste the url of the site being discussed instead of clicking on a standard hyperlink.
“Liked” for your name. 🙂
Little known secret – this site doesn’t work if you use tethering or wifi hotspot through your phone/tablet to access it. When I visited the site using this method, it gave me a HUGE list of stuff I supposedly downloaded that i’ve never seen before.
From this article’s interview:
“Ter-Saakov said he believes youhavedownloaded.com indexes about 20 percent of the file-sharing activity on the Internet. He maintains that the site was created merely as a proof-of-concept, and that it doesn’t have any commercial application.”
From youhavedownloaded.com’s “Data Base Access” page under “What we can do” (accessed 2011-12-12 11p UTC):
“We are also trying to apply this database to advertising. About 10% of all online shoppers, in the US, are torrent users as well. Knowing what they download might be useful market research.”
hmm…
Because the Captcha *NEVER* works you are lured into providing your FaceBook credentials !!!
This is a freak’n phishing SCAM that is preying on your own insecurity and curiosity.
Do *NOT* provide your FaceBook credentials to suspicious sites.
Brian wrote at the end of this article,
“I know plenty of people who would never dream of five-fingering items from a store, or walking out on a restaurant tab, but who routinely turn to file-sharing networks to download copyrighted content.”
This is not a disconnect.
If you teach me to fish, you have shared an idea with me. If I then teach my son to fish, I have shared that idea with him. There is no limit to the supply of this idea, so you do not feel robbed. In fact, you might (nay, should) feel proud that it was your technique I shared, reflecting the time and effort you put into developing it and demonstrating it to me.
Media is just that, an idea. It is not a physical piece of merchandise and downloading it neither incurs costs nor consumes resources of any distributor. No money (or merchandise) is “stolen” by a download.
The giant leap that media companies want us to subscribe to is that sharing “their” content is a “theft of service” and that it “steals” money that would otherwise have been earned by them through one of their approved mechanisms. This is a faulty assumption because people who download this content probably would *not* have purchased it.
Copyright was formed as a tool to “promote the Progress of Science and useful Arts, by securing for limited Times to Authors and Inventors the exclusive Right to their respective Writings and Discoveries” (US Constitution, Article 1), though these days, it is the distributors that secure these rights (for values of “limited Times” tending towards infinite). This storied history has given distributors a sense of entitlement to this suspension of public access rights, a privilege they have abused to such a degree we have forgotten why we have it. Where is the progress? In those days, “progress” was merely the spread of this information: sharing, facilitated at the time by publishers, now no longer needs publication incentives. Even Fair Use seems to have been discarded. See http://remix.lessig.org for a compelling case on this front.
These are the death wails of a dying industry. We no longer need intermediaries like record companies, book publishers, and movie distribution firms. Sure, they still have their place in many aspects, but we need to recognize that their main competition is not just another player at their game but instead a new game altogether: releasing direct to customers, often for little or no cost.
We may be struggling as a capitalist society to figure out exactly what model fits best, but until then, the current model –selling through stores to people that want to support their favorite artists– works pretty well. Some things will slip through the cracks, which will bankrupt the distributors too invested in the old model (Blockbuster, Borders, Tower Records, etc) while propping up those that could handle the transition (Redbox, Netflix, Amazon, iTunes), but even those are just bridging the gap (Netflix is in trouble, Redbox is still fully physical, Amazon is beginning to find its computing services more profitable, and Apple has lost its muse). We don’t know where this is heading. Maybe YouTube and the Participatory Culture Foundation (Miro) are glimmers of the future, maybe they are dead ends.
I still go to the movies and concerts, I still buy merchandise like posters and tee shirts, and when it comes to media companies that are not associated with takedown notices and frivolous lawsuits, I also buy their CDs and DVDs. I also download.
There is no disconnect.
I do not “steal” and I am not a “pirate” (after all, where’s all the rape and pillaging?)
Amen!!
In my experience, most people who have no problems downloading the latest movies, music and software for free off file-sharing networks fall into two camps: Those who have never really given much thought to whether what they’re doing is right or wrong, and those who have settled on a series of rationalizations that make them feel okay doing it. I have no idea what the split is between these two groups, but it is clear that no amount of arguing with those who fall in the second category will change their minds.
But let me try anyway, and answer if you will a few hypothetical questions. A contemporary author spends 3 years of their life researching and writing a book, and they make it available as an eBook for steeply discounted price off the hardcover. But you find a free copy. By your reasoning, it’s not stealing because the publisher can in theory make unlimited number of copies, and therefore exerted near zero resources in producing that extra PDF, and therefore it’s not theft, because the author and the publisher still have unlimited copies of their book to sell. Right?
I employ a team of developers, software writers, and script writers to put together a new best-selling video game that retails for $29.95. You find a “free” version of this same game on the torrents that comes with a crack or a serial. By your reasoning, your downloading and using this software without paying for it is okay because the maker of that game didn’t have to spend any extra money for the copy that you got. After all, it’s just ones and zeroes, and the game maker can simply create new copies of his product just like copying a file on a computer. Is that about right?
By your rationale, this is “infringement,” but not theft, right?
Do you not see any moral or ethical problems, or at the very least intellectual dishonesty with this way of thinking?
“A contemporary author spends 3 years of their life researching and writing a book, and they make it available as an eBook for steeply discounted price off the hardcover. But you find a free copy. By your reasoning, it’s not stealing because the publisher can in theory make unlimited number of copies, and therefore exerted near zero resources in producing that extra PDF, and therefore it’s not theft, because the author and the publisher still have unlimited copies of their book to sell. Right? ”
Right. No theft has taken place.
Your disconnect is that it is not supporting the author, so it must be theft. Is it theft to go to a concert and stand outside because you can still hear it? What about borrowing books from the library? Is it “theft” when you pass by a busker on the street rather than throwing some coins in the hat?
The key is that if everybody downloads it for free, the author might lose the incentive to write more. This is why it is important to support authors and artists financially. This isn’t mandatory unless you’re consuming something (a seat, a product, etc), though it is strongly encouraged, just like for the street busker.
“I employ a team of developers, software writers, and script writers to put together a new best-selling video game that retails for $29.95. You find a ‘free’ version of this same game on the torrents that comes with a crack or a serial. By your reasoning, your downloading and using this software without paying for it is okay because the maker of that game didn’t have to spend any extra money for the copy that you got. After all, it’s just ones and zeroes, and the game maker can simply create new copies of his product just like copying a file on a computer. Is that about right?”
Yes, again you are correct (ignoring the DRM issue). This free version lacks a physical manual and the other niceties of the physical medium (though these are becoming less and less useful), and its use without compensation to the distribution studio means the authors get fewer royalties. Users actually recognize this. Take a look at the Humble Indie Bundle for evidence of another model’s success: http://games.slashdot.org/story/10/12/15/0130257/Humble-Bundle-2-Is-Live
Many games /do/ consume resources; they connect to servers online. MMORPGs are a good example of something that would be a theft of service if one were to play without paying. I’m actually surprised more of them aren’t giving their software away for free since it is mostly (if not entirely) useless without a subscription.
Serious Sam 3 had a good mechanism to encourage downloaders to pay: a giant speedy –immortal– scorpion attacks you until you are dead. Assuming they made the freely available with this caveat, they have an amazing viral marketing model which will end up selling a LOT more of this title, even though most users will only fight the scorpion and then give up.
“Do you not see any moral or ethical problems, or at the very least intellectual dishonesty with this way of thinking?”
Of course I do. Support the artists you like. Just don’t penalize people who don’t. Very few people can afford to support every artist they have material from, so it’s just a matter of selecting the ones you think are most worthy of what you have. This isn’t morally or ethically wrong. Think of the last time you tipped a busker for example. It felt good. Now think of the last time you /didn’t/ tip a busker. Did it feel bad? Was it theft?
“We no longer need intermediaries like record companies, book publishers, and movie distribution firms. Sure, they still have their place in many aspects, but we need to recognize that their main competition is not just another player at their game but instead a new game altogether: releasing direct to customers, often for little or no cost.”
Sorry, Sori, but this is a load of horsepucky, and I think it goes a long way toward rationalizing the theft (yes, theft) of intellectual property (yes, property). This way of thinking says, hey, it’s not theft because it’s published by a big published conglomerate that’s just another cog in the big corporate machine, or hey this is just another product of the record industry, which more money that it should anyway and doesn’t deserve to be relevant anymore, so it’s okay.
You can rationalize downloading music and movies for free that you would otherwise have to pay for till you’re blue in the face, but it won’t change the fact that real peoples’ livelihoods depend on this income stream.
People who espouse the ideas you’re promoting often think that most things should be free, and that placing value on everything leads to a materialistic society. There’s a name for this ideal: It’s called socialism.
Sure there are many, many people in a variety of industries selling direct and bypassing the middleman or the big distribution outlets. That’s wonderful. But guess what? Those people get just as screwed by the “it’s not stealing” excuse as the big record companies and publishing houses when people choose to download pirated versions of those works.
I think actually people on both sides of the debate here are painting a very black and white picture when taken as a whole there’s all sorts of shades of grey in between two extremes.
So I’ll just add to this that many people pirate content simply because it’s convenient. Multiple studies have shown that people who use P2P in fact do not spend less on intellectual property as a whole – they have shifted *what* type of IP they spend their money on however – and in fact are prepared to pay for the same level of convenience that is provided by piracy *if it’s available*. For example Spotify and iTunes are making people millions despite much of the content that these services serve being available as illegitimate versions.
Calling it stealing is absurd, much like calling it piracy. It’s using emotive terms that are pre-laden with negative connotations to describe an activity that IP owners don’t like -guess who pushed to have these terms in the common parlance of today?
Whilst it’s undoubtedly the case that some people would have bought whatever IP is concerned if they couldn’t pirate it there’s no way of knowing who would and who would not in any case.
infringement is not stealing. it’s infringement.
if i steal your money, you don’t have your money anymore.
if i walk out on a restaurant tab, you’ve lost your food and wasted time serving me that could have been spent serving other customers.
if i copy your data without your permission, you still have your data.
this is not meant as an evaluation of the moral status of infringement. but infringement and stealing are different things.
They have me downloading one item. The one item is a crappy show I hate. So they missed some ebooks and didn’t get the one right they did get.
They show I downloaded a cd 2 months ago, but I have only had this internet service for 3 weeks and have never heard of that band it says I downloaded.
Since most household internet changes IP addresses several times a year I don’t see this being very useful.
This guy’s opinion on copyright is evil and thus the site was born. No one owns and idea. No one owns videos and music just like no one owns the land or water. It is no wonder such a hypocritical site would get created from a hypocritical mind. He uses torrents to find information on other torrent users and then relates stealing food to watching television. He is an idiot the likes of which god would be ashamed of.
Amusing. I am not from Japan I am from the U.K. NTL/Virginmedia.
Japan (JP)
Hi Pirate IP 210.xxx.xxx.xx5! We got you! (In our database). You like torrents, don’t you? At least someone in your house does. It looks like you are from Japan. We are not sure about which part though. According to our records, you have downloaded a couple of files. Below is a table with examples. You can click on any filename to get more details. Of course, we are sure that you didn’t violate any laws of Japan and downloaded only legal stuff, right?
Downloaded filesName Date
[Zero-Raws] Digimon Xros … EX 1280×720 x264 AAC).mp4 (392.36 MB) Dec, 2011
[Zero-Raws] Mawaru Pengui … BS 1280×720 x264 AAC).mp4 (241.38 MB) Dec, 2011
Call Of Duty Modern Warfa … Incl. Multi-player Crack (13.77 GB) Dec, 2011
Spy Kids All The Time In … .BRRip.Xvid.AC3- SiNiSTER (2.22 GB) Dec, 2011
The Debt 2011 720p BRRip x264 vice (2.37 GB) Dec, 2011
Removal request
We only aggregate publicly available information.
Thus, we don’t have to accommodate
requests for removal. But we are nice people.
Remove Me!
Authors
“Remove Me” ???
Nothing happens. Just a page to get you to click further in …. a fraud page on a fraud site.
Good lick trying to finger Tor users!
Good lick trying to download at any speed above 10 kB/s 95% of the time as well.
I know no one can do anything to stop you using the TOR network for downloading torrents however it’s really an abuse of the network that’s run by volunteers and donations. For some dissidents its the only safe way they have of enjoying what freedom of speech the internet provides.
You can get full speed downloads and full anonymity by using any one of a number of p2p-friendly VPNs that charge a pittance to use their services – please consider doing this.
“easy way to spread malicious software.”
You mean the way download.com is doing, while we all thought they were a legitimate site? Anything you download could contain malicious software.
The only way to stay 100% safe is to unplug your computer from the internet, and never put a floppy / usb / external hard drive onto it. Good luck with that!
Actually no, get onto any private scene tracker with auto-uploads for any categories that contain executables and that also disallow uploads by anyone. Or get onto a decent topsite. Poeple in the warez scene (“The Scene”, not P2P users) don’t spread malware so you won’t encounter it if you as a P2P user only download scene content that’s added by a bot directly from a scene ftp. If a human adds it you cannot be sure.
You will not get malware doing this. Unless you happen to forget to untick installation boxes on installers of course. Not that this is really that malicious compared to rootkits that run downloaders that install botnets etc tbh …
The database on that site is far from being correct.
I just read about this article in some rss-feed. So I tried the site and much to my surprise I was supposed to having downloaded some torrents I never heard of before.
I happen to be connected through an ISP that hands out variable IP-addresses. I rarely get the same IP-address I got in the past.
This is common practice in my country. Many people don’t have a permanent connection. So every time We connect to the internet, our ISP assigns us an IP-address that is free at that moment.
So I might as well get the IP of some nasty torrent downloader, or I can get the IP that some piratehunter living a couple of villages away from me had yesterday.
Oh yes, I download torrents too. Linux ISO’s and stuff… which is not illegal as far as I know.
I pity the poor fools who down voted the user making the Tor post, you won’t take us Tor users alive! AAHAHAHAHAHAHAHAHAHHAHA
I’ll post this again if it’s downvoted, and follow up again and again so your quest to downvote Tor users HAS AND WILL FAIL!
Tor: a comfy condom for internet use INDEED!
I love it!
A problem with their service/site is that it assumes that the visitor has a (semi)-static IP address, not a shared IP address behind a router as is done in the some of the third-world countries like the Philippines.
I currently have a 10.x.x.x IP address as my connection is in this slow boat, and I don’t use torrent software on my computer as their page indicates that the Internet IP address (which is the outward side of the router here) does.
The problem is, they may not have a way to determine which users are behind such a router built into their software…
Cheers!
My apologies, I did not state that the router is not in my possession or location, but is used by my ISP for all it’s 3G users – of which there are a LOT here…
I would totally download a car if I could.
So, if you went to that site, on purp0se, but never downloaded anything, you’re automagically piled into the same group as a pirate? misleading website is misleading, and makes me thing that the US gov’t has a hand in this somewhere….sort of like one of those “don’t click here” type things….knowing that everyone will click it. Redundant, and inaccurate.