A Wikileaks-style war of attrition between two competing rogue Internet pharmacy gangs has exposed some of the biggest spammers on the planet. The latest casualties? Several individuals likely responsible for running Grum, currently the world’s most active spam botnet.
In the summer of 2010, hackers stole and leaked the database for SpamIt and Glavmed, sister programs that paid people to promote fly-by-night online pharmacies. According to that data, the second-most successful affiliate in SpamIt was a member nicknamed “GeRa.” Over a 3-year period, GeRa’s advertisements and those of his referrals resulted in at least 80,000 sales of knockoff pharmaceuticals, brought SpamIt revenues of in excess of $6 million, and earned him and his pals more than $2.7 million.
A variety of data indicate that GeRa is the lead hacker behind Grum, a spam botnet that can send more than 18 billion emails a day and is the primary vehicle for more than a third of all junk email.
Hackers bent on undermining SpamIt leaked thousands of chats between SpamIt members and Dmitry Stupin, the co-administrator of the program. The chats show daily communication between GeRa and Stupin; the conversations were usually about setting up new spamming operations or fixing problems with existing infrastructure. In fact, Stupin would remark that GeRa was by far the most bothersome of all the program’s top spammers, telling a fellow SpamIt administrator that, “Neither Docent [Mega-D botmaster] nor Cosma [Rustock botmaster] can compare with him in terms of trouble with hosting providers.”
Several of those chats show GeRa pointing out issues with specific Internet addresses that would later be flagged as control servers for the Grum botnet. For example, in a chat with Stupin on June 11, 2008, GeRa posts a link to the address 206.51.234.136. Then after checking the server, he proceeds to tell Stupin how many infected PCs were phoning home to that address at the time. That same server has long been identified as a Grum controller.
By this time, Grum had grown to such an established threat that it was named in the Top Spam Botnets Exposed paper released by Dell SecureWorks researcher Joe Stewart. On April 13, 2008 – just five days after Stewart’s analysis was released – GeRa would post a link to it into a chat with Stupin, saying “Haha, I am also on the list!”
Around the same time that SpamIt’s database was leaked, hackers plundered the networks of ChronoPay, one of Russia’s biggest online payment processors. The company’s top executive, Pavel Vrubelvsky, was reputed to have been a co-founder of SpamIt’s biggest competitor — a rogue pharmacy operation called Rx-Promotion. The data that hackers leaked from ChronoPay included emails showing ChronoPay executives passing credentials to Rx-Promotion’s administrative back end database.
KrebsOnSecurity.com obtained a comprehensive data set showing all of the sites advertised by Rx-Promotion affiliates in 2010, as well as the earnings of each affiliate. That information was shared with several University of California, San Diego researchers who would later incorporate it into their landmark Click Trajectories study (PDF) on the economics of the spam business. The researchers spent four months in 2010 observing the top spam botnets, keeping track of which pharmacy affiliate programs were being promoted by different top botnets.
The GeRa-Stupin chats show that by the time the researchers started recording the data, GeRa had defected from SpamIt to work for Rx-Promotion. Indeed, the UCSD researchers found that Rx-Promotion and Grum were synonymous. Each RX-Promotion pharmacy includes a “site_id” in its HTML source, which uniquely identifies the store for later assigning advertising commissions. The researchers discovered that whenever Grum advertised an Rx-Promotion site, this identifier was always the same: 1811. According to the leaked Rx-Promotion database, that affiliate ID belongs to a user named ‘gera.’
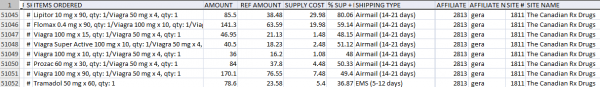
A tiny snippet of GeRa’s sales from Rx-Promotion sites, which all bore his affiliate ID 1811 in the source.
“It doesn’t prove that GeRa owned Grum,” said Stefan Savage, a professor in the systems and networking group at UCSD and co-author of the study. “But it does show that when Grum advertised for Rx-Promotion, it was for sites where commissions were paid to someone whose nickname was ‘GeRa’.”
WHO IS GERA?
GeRa uses the alternative nickname “Ger@” on Internet forums, including the now-defunct Spamdot.biz, where top spammers from SpamIt and competing programs used to gather. Google’s search engine largely ignores the “@” character, which makes searching for that nickname difficult. But infiltrate enough invite-only cybercrime communities and eventually you will find a user named Ger@ who announces that he is buying traffic.
GeRa routinely purchases traffic from other botmasters and malware writers who control large numbers of hacked PCs. As he explained in the following post to an exclusive forum, victim browsers sent his way are typically funneled through sites hosting a gauntlet of exploits designed to install a copy of his spam bot (see below).

Ger@ writes: “We continue to buy all your traffic which goes to Eleonor (Exploit Pack) to load the spam bot…”
GeRa did not respond to multiple requests for comment sent via email and ICQ. He appears to have been much more careful with his identity than other top SpamIt botmasters, but he did leave several tantalizing clues. GeRa appears to have used a number of separate affiliate accounts for himself on SpamIt (possibly to make his earnings appear lower than they really were. Among his personal accounts were “GeRa,” “Kostog,” “Scorrp,” “Scorrp2,” “Scorrp3,” “UUU,” and “DDD.”
GeRa received commission payments for all of those accounts to a WebMoney purse with the ID# 112024718270. According to a source who has the ability to look up identity information attached to WebMoney accounts, that purse was set up in 2006 by someone who walked into a WebMoney office in Moscow and presented a Russian passport #4505016266. The name on the passport was a 26-year-old named Nikolai Alekseevich Kostogryz.
One of GeRa’s most successful referrals was a SpamIt affiliate who used the nickname “Anton,” and the WebMoney ID 186103845227. The information on the Russian passport used to open that account was Vasily Ivanovich Petrov. According to SpamIt records, Anton was the 18th most valuable affiliate overall, bringing in sales of nearly $1 million and earning commissions above $422,000.
Looking at the earnings of spammers from both SpamIt and Rx-Promotion, it’s difficult to ignore the remarkable asymmetry between their incomes and the global cost of dealing with junk email. In the United States alone, spam has been estimated to cost businesses more than $40 billion annually in lost productivity, anti-spam investments, and related costs. By comparison, the entire SpamIt program produced revenues just above $150 million over a four year period, while Rx-Promotion spammers generated a fraction of that revenue.
This is the latest in my Pharma Wars series. In case you missed them, check out my profiles of other top botmasters, including:
Mr. Waledac: The Peter North of Spamming
‘Google,’ the Cutwail Botmaster
Mr. Srizbi vs. Mr. Cutwail
Chats with Accused ‘Mega-D’ Botnet Owner?
Rustock Botnet Suspect Sought Job at Google






I don’t know how you keep me so hooked on this blog! Nice job Krebs I loved this article.
The GeRa guy is living the life haha!
Fantastic research job… I never read War and Peace because I could never keep all the names straight… LOL.
Thanks, Brian!
i know all about info he in real life and grum coder and botnet !
959.0899@gmail.com
Hey bot, you’re welcome to comment here just like everyone else, but please leave the malware download links out of your Website name. Thanks.
d:\Work\Malware\Gera-projects\Spam-bots\Bottt_v4.d01 (rambler with LE skeleton)\ ^^
it’s old but powerfull
Will sell the same data as “bot” has two times cheaper, because of low actuality 😉
It is remarkable how much money they can make from this, the research for this post is so thorough.
i know because i exploited they ^^ and research about it’s!
80k sales over 3 years seems low. That’s less than 75/day. At a $45cpa it’s only ~$3k/day. I used to bring in half of that and I paled in comparisson to other rx affiliates.
Looks like “b” is “bot,” BK. There’s a link attached to his name, too.
Fascinating stuff. Brian, aren’t the WebMoney guys a bit suss at your ability to source owner’s information from their WM accounts?
“that Rx-Promotion and Grum were synonymous” ?
may be “GeRa and Grum were synonymous”?
18 000 000 000 * 365 * 3
80k sales
lol
+
*facepalm*
(link attached to user name here, too)