Underground Web sites can be a useful barometer for the daily volume of criminal trade in goods like stolen credit card numbers and hijacked PayPal or eBay accounts. And if the current low prices at one of Underweb’s newer and more brazen card shops are indicative of a trend, the market for these commodities has never been more cutthroat.
Badb.su is distinguishable from dozens of underground carding shops chiefly by its slick interface and tiny domain name, which borrows on the pseudonym and notoriety of the Underweb’s most recognizable carder. It’s difficult to say whether “Badb” himself would have endorsed the use of his brand for this particular venture, but it seems unlikely: The man alleged by U.S. authorities to be Badb — 29-year-old Vladislav Anatolievich Horohorin — has been in a French prison since his arrest there in 2010. Authorities believe Horohorin is one of the founding members of CarderPlanet, a site that helped move millions of stolen accounts. He remains jailed in France, fighting extradition to the United States (more about his case in an upcoming story).
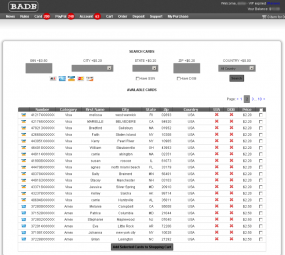
Badb.su’s price list shows that purloined American Express and Discover accounts issued to Americans cost between $2.50 and $3 apiece, with MasterCard and Visa accounts commanding slightly lower prices ($2-$3). Cards of any type issued by banks in the United Kingdom or European Union fetch between $4-$7 each, while accounts from Canadian financial institutions cost between $3 to $5 a pop.
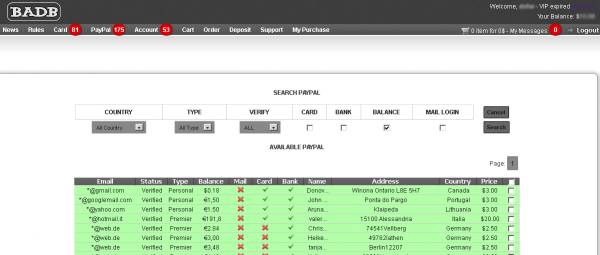
The site also sells verified PayPal and eBay accounts. Verified PayPal accounts with credit cards and bank accounts attached to them go for between 2-3$, while the same combination + access to the account holder’s email inbox increases the price by $2. PayPal accounts that are associated with bank and/or credit accounts and include a balance are sold for between 2 and 10 percent of the available balance. That rate is considerably lower than the last PayPal underground shop I reviewed, which charged 8 to 12 percent of the total compromised account balance.
Ebay auction accounts are priced according to the number of positive “feedback” points that each victim account possesses (feedback is the core of eBay’s reputation system, whereby members evaluate their buying and selling experiences with other members). eBay accounts with fewer than 75 feedback history sell for $2 each, while those with higher levels of feedback command prices of $5 and higher apiece, because these accounts are more likely to be perceived as trustworthy by other eBay members.
But don’t count on paying for any of these goods with a credit card; Badb.su accepts payment only through virtual currencies such as Liberty Reserve and WebMoney.
Badb.su, like many other card shops, offers an a-la-carte, card-checking service that allows buyers to gauge the validity of stolen cards before or after purchasing them. Typically, these services will test stolen card numbers using a hijacked merchant account that initiates tiny charges or so-called pre-authorization checks against the card; if the charge or pre-auth clears, the card-checking service issues a “valid” response for the checked card number.
But Badb.su’s card checking service, which costs an extra 20 cents per card, may not be all that sophisticated: Site administrators urge customers to quickly test the cards by making real purchases online. Rather, the administrators of the site implore customers to use the checking service only to verify cards that are declined by merchants, and thus as a way to verify on-site that the cards are invalid and to qualify the buyer for a refund.
“You have 10 minute to Check just buyed CC, before check option will be expired,” the site explains. “We don’t offer PayPal account checker atm. Please always make sure you USE card before you check it here. We don’t accept complains about 3rd party checker.”
Points to Badb.su for knowing its customer base: The site boasts its own bug bounty program, offering to pay hackers who discover and report flaws in the site’s machinery. It also warns users away from browsing the site with Internet Explorer.
“Find a bug? Any innovation idea? Contact with us! We will pay you!” reads a message on the site’s “readme” page. “Please don’t use IE – it’s not fully supported.”





you are good for nothing , u did same for raihan’s other site but nothing happend, he knows how to secure his shit.
Ah, well, then Mr. Raihan should have nothing to fear from another review in my little blog, should he? 🙂 He did request reviews on his site, even offered to pay for them. Come to think of it, I should check my account balance now….
From the site: “We need reviews! Post your review of BadB shop and get $2 Gift bonus on balance. We have threads on many forums. Just place your reviews and create ticket with link, we add bonus.”
well i will ask him on icq today or on facebook although he is rarely online on facebook, you must know bangladesh kids have bit language problems too
So what good is an ebay account? Is it so the fraudster can “purchase” (but of course not actually pay) items through that account?
They could do that, sure: taking a trusted account and auctioning a high-priced item and absconding with a wire transfer. Alternatively, they may use these accounts to move hot/carded merchandise.
More likely to sell but not actually ship an item, supposedly from a seller with an established reputation.
yes, actually i have been a victim myself. somebody using a highly rated account is above suspicion on ebay, and the person was offering bundles of iphones and hp touchpads a lot cheaper.
of course we figured out before we made the payment, we told ebay it was a fraudulent account and they suspended right away. but the same person was selling these items with many other usernames. this happens a lot.
Has the United Kingdom secretly left the European Union, or did you mean the ‘United Kingdom or the Eurozone countries’?
“but do you know how to check and is there any point checking when we already know NSA/KGB, etc etc have the globe encircled with satellites?”
try lining your windows with tinfoil and check it after a few months. You’ll discover straight LINES and DOTS (tiny peep holes). This is with the tinfoil on the inside of the windows’ surface, in-house/apartment. What causes this?
I believe most, if not all consumer computers and devices are, if not monitored, swept and mirrored by big bro using satellite technology.
One anonymous poster to pastebin, claiming to be representitive of Mossad, fired a shot across the bow of Anonymous and other hackers by saying, paraphrased, “All of your hard drives are mirrored in (locations A,B,C as I forget which countries were mentioned) certain places on Earth anyway.
I find this to be true, I’ve used Microsoft’s SysInternals programs to monitor processes and discovered my drives being swept, a chat program running I never installed and could find no trace of, files where they had the most interest were mp3 and graphics files, but they scraped the whole drive, and an iso creator/mirroring utility was running.
You only make it easier for them if you willingly install video streaming programs (VLC) with command line counterparts, music programs with command line counterparts, Office programs, which I noticed PDF files were being made in the background, and all of this activity was happening when I was monitoring a computer isolated from any wired/wireless/LAN network(s).
Google: Subversion Hack archive for a glimpse into this mysterious activity
It’s all about the waves.
==
“Well, if this is true or not, I cannot tell, because I use GNU/Linux,”
The same is true for *nix, you just have to have the right monitoring tools and know what to look for inside binaries which are easily messed with by injecting malware into them and tools used by “THEM” to obscure the code injected into the ELF binaries so as to avoid being picked up as malware.
One simple command you can use to check for modifications to your files:
sudo find /usr/bin -mtime -60
That will search /usr/bin for files modified within 60 minutes, adjust the command as needed for other directories and time frames.
ALWAYS generate sha256sums or better (NOT MD5 or SHA1) of your initial install and the LiveCD and store them on a READ ONLY media like a once writable CDROM. The free utility known as “md5deep” offers more than md5 checksum generation and unlike the simple tools like sha256sum, sha1sum, etc., md5deep’s options offer RECURSIVE and directory stripping options, perfect for backup on CDROMs.
Here’s one example out of many mysterious *nix trojans floating about:
– Linux/Bckdr-RKC
—- http://caffeinesecurity.blogspot.com/2012/02/linuxbckdr-rkc-still-undetected.html
“For those who aren’t familiar with this trojan, an anonymous internet user has taken the time to put together a Pastebin post highlighting my research on this trojan”: http://pastebin.com/DwtX9dMd
More questions without answers:
– Malware for Windows, *nux (and MacOSX?) which HIDES in FIRMWARE on routers, PCI and AGP cards and devices (including CD burners), system BIOS, MBRs, ethernet (nic) cards most if not all surviving hard drive wipes/formats and preloaded again and updated “through-the-air” mysteriously or when you’ve plugged into the net.
– Ethernet cards using packet radio modules/protocols
– Linux distributions including LiveCDs including more modules than they need to run, especially for LiveCD purposes, including build essentials, dpkg-dev, ISDN drivers/modules (sometimes in multiple places, as binary files and as modules) and other modules including ham radio modules
– PCI and AGP rootkits which never leave (no antivirus scanner scans firmware on these cards and devices where most of the really serious malware resides)
Google on these topics for whitepapers and documentation up the yin yang, including ever popular DEFCON talks, papers, etc.
Also Google: Subversion hack archive (it’s a website detailing mysterious trojans reinfecting computers NOT plugged into the net).
There are probably a ton of non-detectable Linux exploits in the wild. Many of the freely offered ones on some of the more whitehat/popular sites aren’t detected. More are made and uploaded every day.
In my opinion, no electronic device is safe, especially not those whose builders FORCE your motherboard to have a preinstalled, unremovable network (nic) card, sound card (both can be exploited by ham radio modules/drivers/malicious related programs), video card, etc.
One possible solution to this madness would be to purchase ANCIENT computers (Apple II or Cmdre for example) and use open source networking code. Much of these older systems did not have a lot of built in networking devices and storage devices.
The ultimate solution is to avoid electronic devices completely (even TV and radio) and learn to love books and libraries again, but for most people that would be as painful as slitting their own necks like a chicken, they lust after their Facebook, smartphone, iphone, ipad, Twitter, Angry Birds, and other diversions.
Google the article: The Mind Has No Firewall (written by a solider, unless I’m mistaken), to expose how weak our minds are to (electronic) attack.
Visit: TheHiddenEvil.com : to learn more about ‘the big game” which we’re all enrolled in by birth.
Thank you for taking the time to use an hysterical sounding name complete with caps and exclamation marks – sometimes curiosity gets the better of me and I look at buried comments but in your case the name was enough to stop me looking.
Well you missed a few moments of hilarity.
Microsoft Security Bulletin Advance Notification for March 2012
Published: Thursday, March 08, 2012
Version: 1.0
This is an advance notification of security bulletins that Microsoft is intending to release on March 13, 2012.
https://technet.microsoft.com/en-us/security/bulletin/ms12-mar
Brian, do you ever try to use Dermometr for crime in internet?
If to check your site. It will be 100%.
HUGE Security Resource
– version 5000 – 03/06/12
http://pastebin.com/Cm2ZHuz3
As previously featured on Cryptome.org’s front page for security resources.
Yeah, I saved it. I don’t know where to begin on a list this big lol. Much of it won’t be new to me or will be irrelevant. Makes it trickier. Some things caught my eye immediately, such as “acoustic cryptanalysis.” I doubt I’ll understand it, but it sounds cool & prolly other cool stuff in the list.
Finally site is down now 😀 good job, btw you should check following site also.
kurupt.su
maza.su
carderprofit.cc
I am attorney on file for Mr. Horohorin criminal case in DC and GA. My client is currently incarcerated in Nice, France. He denies all accusations and fights his extradition. For more information, please contact my office (Bukh Law Firm, P.C, 14 Wall St, New York NY 10005, (212) 729-1632).
Of course he denies all charges. Anyway, what evidence are the US and France claiming to have on him warranting the arrest? So far, all readers have to go on is…
US: “Our investigation shows he’s guilty. Trust us.”
France: “We arrested him b/c we know he’s guilty. Trust us.”
Defendant: “I’m not guilty. Trust me.”
It’s hard to make an informed opinion about this, although I’m leaning toward thinking he’s guilty for now. After all, the authorities have been getting many of these people.