Millions of PCs sickened by a global computer contagion known as DNSChanger were slated to have their life support yanked on March 8. But an order handed down Monday by a federal judge will delay that disconnection by 120 days to give companies, businesses and governments more time to respond to the epidemic.
 The reprieve came late Monday, when the judge overseeing the U.S. government’s landmark case against an international cyber fraud network agreed that extending the deadline was necessary “to continue to provide remediation details to industry channels approved by the FBI.”
The reprieve came late Monday, when the judge overseeing the U.S. government’s landmark case against an international cyber fraud network agreed that extending the deadline was necessary “to continue to provide remediation details to industry channels approved by the FBI.”
DNSChanger modifies settings on a host PC that tell the computer how to find Web sites on the Internet, hijacking victims’ search results and preventing them from visiting security sites that might help detect and scrub the infections. The Internet servers that were used to control infected PCs were located in the United States, and in coordination with the arrest of the Estonian men in November, a New York district court ordered a private U.S. company to assume control over those servers. The government argued that the arrangement would give ISPs and companies time to identify and scrub infected PCs, systems that would otherwise be disconnected from the Internet if the control servers were shut down. The court agreed, and ordered that the surrogate control servers remain in operation until March 8.
But by early last month, it was becoming clear that more than 3 million PCs worldwide — including at least 500,000 in the United States — were still infected with DNSChanger. The company that released those estimates, security firm Internet Identity, reported that 50 percent of Fortune 500s and about half of all U.S. government agencies were still struggling with infections.
Updated infection figures released last week indicate that the government has made great strides in scrubbing the malware from its networks, but that more work is still needed. On Feb. 23, 2012, Internet Identity found that 94 of all Fortune 500 companies and three out of 55 major government entities had at least one computer or router that was infected with DNSChanger.
Internet users can quickly see if their PCs are infected with DNSChanger by visiting one of several “eye check” sites, including this one. DNSChanger also infected Mac OS X systems and home routers; go here if you need instructions for checking those systems for infections. A larger network owner can find out if any PCs on the local network are infected by reaching out to one of the entities in the DNSChanger Working Group.
A signed copy of the court order extending the deadline until July 9, 2012 is available here (.PDF).




I was actually a little disappointed by the news that the deadline had been extended. I understand that the sudden disconnection of the remaining affected systems might have caused problems for the affected organizations, but there is the very real possibility that the infected computers have other, still-active infections. The fact that they are still infected suggests an inadequate security posture. We don’t know what the duties of the infected systems are, but they could very easily be leaking information or causing other problems.
As soon as the infected systems have their DNS service cut off, the fact that they need service should become immediately apparent to their operators. That would get these systems some of the attention that they desperately need. Hopefully, the overall security posture where these infected systems remain will be improved as a result of this incident.
I am pleased that such great progress has already been made toward cleaning up the affected systems. Upon hearing the initial report of how many systems were still affected, I expected those numbers wouldn’t decline quickly until the DNS servers were shut down. That such good progress has been made makes me feel a little better about the deadline extension.
“As soon as the infected systems have their DNS service cut off, the fact that they need service should become immediately apparent to their operators.”
I totally agree with that, but the problem is that call centers can’t handle the volume if even only a small percentage of customers are infected and suddenly they can’t resolve domains.
Those customers aren’t likely to benefit from the extended reprieve – they’ll probably still be infected when the new deadline expires. Similarly, most call centers won’t likely be any more prepared then than they are now. Yes, it’s going to hurt, but pushing back the deadline isn’t going to make much of a difference to them.
The push to clean up enterprises and government agencies won’t do much for end-users and service providers. I doubt the help desks at affected organizations are going to be overwhelmed by calls when the DNS servers are shut down, but as long as good progress is being made, I do not object to giving them a little bit more time to clean things up before that happens.
Wonderful… Any bets on another extension after this?
I know Comcast, for one, is actively notifying their customers of infections. This past weekend I helped a friend and her daughter get the daughter’s router cleaned up and secured. They notified her on Feb. 29th. Better late than never, I guess.. and now people have more time to put it off.
How are you doing it for the home routers? Our individual PC’s(one Linux)are fine, but I’d like to be able to check my Verizon FiOS home router too. I guess I could look at the admin page and take it from there…
The one I did was a Linksys. The DNS servers had been statically assigned. I just did a factory reset on it and then set the wireless network back up.
I can see the management re-distribution of workload now changing focus to other issues for 115 days.
Just one note about inspecting the DNS info for Mac OS X: they left out the step that you have to click on “Advanced” after clicking on “Network” to see your DNS settings
While I know how to change the DNS settings (follow instructions on the referenced web page, then enter correct values) and I’m aware that correct values might come from your network administrator or your ISP or from OpenDNS (if you use OpenDNS), is there risk of the DNS settings changing back once you’ve manually corrected them?
I’m betting that there is and that one might take normal precautions to prevent this, for example doing normal work using a standard user account (not an administrator) and, on Mac OS X, locking the System Preferences.
On Windows, can you lock Control Panel settings?
I doubt the “Control Panel” or “System Preferences” GUIs are being used. At least on Windows, I’m sure it’s just registry keys being poked into place, and those registry keys should not be changeable unless the DNSChanger is able to run as some sort of administrator.
in Mac OS X the DNS changers have been a process that runs that overrides the normal DNS entries, and a crontab entry that checks every minute that the process is running.
So locking system preferences likely wouldn’t block this particular item.
Your web site is throwing a javascript error every time I attempt to scroll (line 7, unable to get the value of the property ‘top’). Makes it incredibly annoying to read the page.
It’s working fine for me in Firefox, Chrome and IE9…
The next question is how do the feds ensure that everyone knows what to look for when their users suddenly can’t get any internet service.
If I didn’t read this blog, I wouldn’t have heard about this problem, and my experience dealing with professional IT support people is they know so much less than me about malware that they think I’m a paranoid nutcase when I complain about security vulnerabilities on their systems. Anything they categorize as one of the mysterious “networking problems” is often just left unsolved, with users who are unable to connect to printers being told to go print from a different computer, for instance.
I have real doubts how many of them would have any idea why their users’ computers stop working.
Easy instead of the web you get a big bright red web page telling you why you have been cut off and instructions on how to fix it.
They could do that now.
bingo.
I cannot believe that this is even being considered. The right thing to do would be for ISPs to highjack the DNS requests going to these malicious servers and redirect them all to a web page that explains that the user’s computer is infected and that they cannot provide service until the infection has been cleaned up.
Pair this with a message on the 1-800 tech support number that says if you have seen this message on your screen you are infected and that the ISP is not responsible and cannot help you, you must take your PC to be cleaned of the infection.
That’s the easy solution, the problem comes up with whether or not we want to endorse it as the standard solution.
Malware sites already pop up nasty screens informing the user that their computer is infected “Please click here” to fix the problem. There’s already enough people who fall for that trick without asking someone they already know and trust for help. By using this solution, we encourage more people who might not have fallen for it, to fall for it. “I knew someone who was told to go fix their computer and it worked, so I did the same thing.”
And yet, it’s also the only solution that’s guaranteed to reach all the infected users and direct them to get help with the minimum amount of fuss. “Damned if you do, damned if you don’t.”
It’s why I endorsed killing the servers. Instead of a warning screen, they get no connection at all. It’s going to hurt, but it’s the safest way in the long run.
… I can check if I am infected by “CLICKING HERE” ?
if my DNS is broken, cant the trojan re-direct me to a BAD site that shows the “you are OK” picture ?
wow. unless I am wrong, this has NOT been thought thru.
“if my DNS is broken, cant the trojan re-direct me to a BAD site that shows the “you are OK” picture ?”
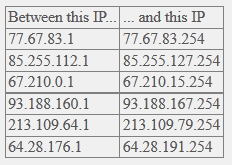
No, it can’t. It’s a trojan, not a bot that can take remote commands. This article clearly states that all of the DNSes that the DNSChanger trojan can direct you to have been replaced by good fill-ins.
So yes, that part has been thought through.
Is´nt it possible that a modified DNS setting could direct your http://dns-ok.us/ to a rouge website? I believe it could. I agree that the Trojan itself cannot redirect you, but if the “damage is done” I cannot see how results from this test can be trusted. Please correct me if I´m wrong. ( I was surprised that it was´nt SSL enabled..)
@Ola, it’s a lot simpler than you think. Every single rogue DNS server IP address that the trojan might possibly redirect you to has been replaced by a good fill-in. So any DNS query will now return a good result.
Now those fill-in servers do resolve dns-ok.us to an IP address that is one number different (38.68.193.97) than a “real” DNS server resolves it to (38.68.193.96). This is so that you are sent to a web server that serves up a page with a red background rather than green.
That’s it. Simple as that. No SSL needed. It’s just DNS resolution, not web redirection in a sense that the trojan or DNS query knows what the query is going to be used for. It doesn’t.
I’m assuming the reason the redirect to a help page idea wasn’t used immediately is because there are legal or ethical problems from doing that.
I don’t know much about DNS caching, either — is it possible unifected computers on a network would be given the IP address of that help screen if the query from an infected machine were cached locally?
Yep i agree with you.