Employee and financial records leaked from some of the world’s largest sponsors of spam provide new clues about the identity of a previously unknown Russian man believed to have been closely tied to the development and maintenance of “Bredolab,” a massive collection of hacked machines that was disassembled in an international law enforcement sweep in late 2010.
In October 2010, Armenian authorities arrested and imprisoned 27-year-old Georg Avanesov on suspicion of running Bredolab, a botnet that infected an estimated 3 million PCs per month through virus-laden e-mails and booby-trapped Web sites. The arrest resulted from a joint investigation between Armenian police and cyber sleuths in the Netherlands, whose ISPs were home to at least 143 servers that were used to direct the botnet’s activities.
Dutch and Armenian investigators have long suspected that Avanesov worked closely with an infamous Russian botmaster who used the nickname “Birdie,” but so far they have been unable to learn the Russian’s real identity or whereabouts.
“He was a close associate of Gregory A.,” Pim Takkenberg, team leader of the National High Tech Crime Unit in the Netherlands, said of the hacker known as Birdie. “Actually, we were never able to fully identify him.”
According to records leaked from SpamIt — a pharmacy affiliate program that was the victim of a data breach in 2010 — Birdie was an affiliate with SpamIt along with Avanesov. Neither affiliates earned much from SpamIt directly; they both made far more money selling other spammers access to Bredolab.
Birdie was also the nickname of a top member of Spamdot.biz, a now-defunct forum that once counted among its members nearly all of the big names in Spamit, as well as a dozen competing spam affiliate programs. Birdie’s core offering on Spamdot was the “Birdie Load System,” which allowed other members to buy “installs” of their own malware by loading it onto machines already infected with Bredolab.
So successful and popular was the Birdie Load System among Spamdot members that Birdie eventually had to create a customer queuing system, scheduling new loads days or weeks in advance for high volume customers. According to his own postings on Spamdot, Birdie routinely processed at least 50,000 new loads or installs for customers each day.
“Due to the fact that many of my clients very much hate waiting in line, we’ve begun selling access to weekly slots,” Birdie wrote. “If a ‘slot’ is purchased, independently from other customers, the person who purchased the slot is guaranteed service.”
Using Birdie’s Bredolab load system, spammers could easily re-seed their own spam botnets, and could rely upon load systems like this one to rebuild botnets that had been badly damaged from targeted takedowns by anti-spam activists and/or law enforcement. Bredolab also was commonly used to deploy new installations of the ZeuS Trojan, which has been used in countless online banking heists against consumers and businesses.
Below is a translated version of Birdie’s Dec. 2008 post to Spamdot describing the rules, prices and capabilities of his malware loading machine (click the image below twice for an enlarged version of the Spamdot discussion thread from which this translation was taken).
One country (customer’s choice) – $150.
Stats
Every order gets a unique link, which shows:
a) Time to order execution
b) Number of loads in real time
c) Exe change
Rules
1. Prices are non-negotiable
2. No discounts for large orders
3. FTP grabber is not allowed to be loaded
4. No affiliation schemes
5. Loads are counted according to running exe, if your exe is pristine you earn very much. Loss of “call home” can reach 50% if exe is “dirty”.
6. You cannot switch your position “in line” to a better one for any money.
7. I do not encrypt exe in any circumstances.
8. If your exe has not “called home” it is not because of our software, it’s because of yours. Therefore, no complaints are accepted.
Taking orders over Jabber! Do not think it is e-mail.
I am taking care of technical issues and taking orders — mind@contactmedialife.com
If I am not available, knock here only to place your order – diesel@contactmedialife.com
WHO IS BIRDIE?
Birdie left behind a trail of clues that all lead back to the same place and identity. It is worth mentioning that Birdie may have intentionally left this clue trail as part of an elaborate ruse to throw investigators off of his tracks should the SpamIt and Spamdot databases someday fall into the wrong hands (as they both have). I should also mention that I sought responses from the individual named below via several methods, but received no reply.
Birdie registered with Spamdot using the email address trudyuvmq@aol.com. An online search for that address produces a single result: A transportation industry Web site advertisement for mkadr.ru, a Russian GPS tracking services firm based in Moscow. The ad, placed in March 2009, displays the trudyuvmq@aol.com address next to a phone number (495) 649-69-07, and the name “Alex.”
Birdie was paid for his spamming services by SpamIt via deposits made to a WebMoney purse belonging to WebMoney ID 458269734041. That same WebMoney ID is listed as an acceptable way to pay for digital maps sold by a site called track4maps.com. According to cached versions of mkadr.ru at archive.org, track4maps.com and mkadr.ru appear to be the same company.
That same WebMoney account was used by another affiliate of SpamIt, someone who used the nickname “Lex” and the email address almale@yandex.ru. Spamit records show Birdie was a referral of Lex. The two accounts may have been created by the same person; leaked records indicate that it was very common for SpamIt affiliates to use multiple aliases and nicknames. WHOIS records show that the almale@yandex.ru email address is the one originally used to register track4maps.com. A search for that email address in Google produces few results, including a listing at an electronic business card Web site called copi.ru that says the address belongs to a Muscovite named Alexander “Lexandro” V. Maksudov. Another site indicates that the mkadr.ru employee also used the last name or alias “Maximov.”
A Google search for the WebMoney ID used by both Lex and Birdie produces on the first page of results a listing at icq-uin.ru, a site where people can auction off unused or unwanted ICQ instant messenger IDs. That posting, made in August 2008, indicates that the seller was an Alexander who listed his business Web site as mkadr.ru.
Although the Bredolab botnet has been dismantled, there are strong indications that Birdie has rebuilt a massive loads system and is again selling it on the underground. But that is a topic for a future post.



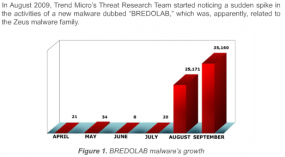

I actually am surprised that this hasn’t been told anywhere.
Bredolab was sold, just like ZeuS, SpyEye, Carberp and all those other bots.
It was sold by S??a???0 under the name of BManager.
Maybe it was only sold once or twice but I am sure the coder is still free and maybe still actively producing malware.
“If a ‘slot’ is purchased, independently from other customers, the person who purchased the slot is guaranteed service.”
Such impressive business ethics!!!
thanks for another very interesting article, Brian.
Any evidence bredolab resurrected through C&Cs at Leaseweb B.V. someone?
.oO(I assume they have – but have no evidence for the C&Cs myself and leaseweb still isn’t cooperative…)
:
27.02.2012: Backdoor.Win32.Bredolab.yuw
10.03.2012: Backdoor.Win32.Bredolab.zjf
19.03.2012: Backdoor.Win32.Bredolab.zji
Pretty sure Brian could find parallels between some dates of Bredolab-outbreaks and attacks to his site in the last years; even though the exact dates are hard to determine… (And I bet at least one responsible for the attacks or for new variants of Bredolab listened to him at Govcert 2011.)
Просто это классный программист, который зарабатывает на своих умениях. В рунете таких валом
“trudyuvmq@aol.com. An online search for that address produces a single result”
Seems like being a high flyer in the email spam business has at least one advantage then other than money money money – avoiding spam yourself.
When I Google my gmail address the first 6 results are .txt files with my email, one amusingly named poorbastards or something like this.
Not that it’s too much if a hassle, I prolly get one unsolicited message a month in my inbox … gotta love Googles crowdsource approach to spam.