It may not be long before your mobile phone is beset by the same sorts of obnoxious, screen-covering, scaremongering ads pimping security software that once inundated desktop users before pop-up blockers became widely-used.
Richard M. Smith, a Boston-based security consultant, was dining out last Friday and browsing a local news site with his Android-based smart phone when his screen was taken over by an alarming message warning of page errors and viruses. Clicking anywhere on the ad took him to a Web site peddling SnapSecure, a mobile antivirus and security subscription service that bills users $5.99 a month.
“This particular ad takes over the entire screen on my Android phone, so it gives the impression of being rather ominous,” Smith said, noting that it was the second time in as many days that he’d encountered the rogue ad. He further explained that the ad just appeared when he browsed to view a new story, and that he hadn’t clicked on an ad or anything unusual.
Michael Subhan, vice president of marketing for SnapSecure, said the company traced the ads back to some rogue marketing affiliates that have since been banned from its advertising program.
“We did find out which affiliate was serving up the ad, and they will be blacklisted from the network,” Subhan said. “We have strict advertising policies, and do not tolerate rogue affiliates. Unfortunately, with the volume of advertising that we do, there are sometimes affiliates that try and get around our guidelines.”
Meanwhile, the ad linked to in the overlay image still appears to be live and redirecting users to the SnapSecure purchase page.
I am frequently asked whether mobile users should purchase anti-malware and security products. The short answer is, “no.” I tend to steer people toward Krebs’s 3 Basic Rules for Online Safety, which urge first and foremost, “If you didn’t go looking for it, don’t install it!” A corollary of this should be, “If you intend to install it, make sure you have researched it.”
Yes, I realize that this advice may seem fuddy-duddy and inconvenient for users of a platform that places a premium on instant gratification and access to information. But security software should never be viewed as a substitute for common sense and simple precaution. Anti-malware software is and always has been reactive, meaning it usually only detects a threat after some subset of customers have already been successfully compromised by it. And in the mobile space, the window of time during which malicious applications go undetected by mobile providers or the general public seems to be far narrower than in the world of desktop applications.



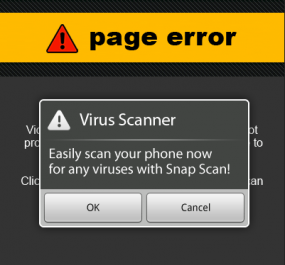
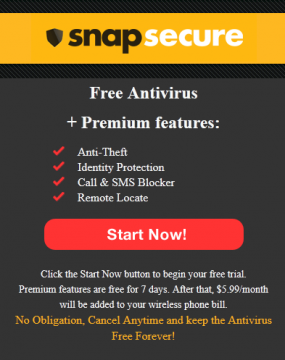

What is left unsaid in Brian’s post is that something promoted as “anti-malware” can in fact be malware itself — especially when scare tactics like this are used to promote it. There is no easy way for the user to detect what is good and what is bad. My personal rule of thumb would be, if a scare tactic is used to sell it to you, then it;’s probably up to no good. Anti-malware should be purchased or acquired only from a known, reputable site, and never from an ad coming from an unknown source.
Based on this narrative, I would now put SnapSecure in my list of software to be avoided at all costs.
While I appreciate the majority of the article, I have to question the position that security software for your mobile device is unnecessary. I have found virus on colleagues’ (IT professionals) Android phones, and they already have knowledge of information security beyond the standard user. Just because there are unknown exploits out there doesn’t mean we should let the known ones run around in the wild. While security software isn’t a replacement for best practices, best practices should certainly include malware detection. The trick then is finding a trustworthy vendor in the sea of solutions available for these emerging platforms
While there are undoubtedly free security apps for iPhone and Android (as mentioned by The Shark™ below), your observation about “exploits” doesn’t exactly line up with the facts as they are right now: Which is that probably 99 percent of the “bad stuff” out there attacking mobile users are backdoored apps or malicious programs disguised as apps. People have to go out and look for them and install them. Scareware ads designed for mobile devices take that a little further, pushing people to install apps of dubious provenance or utility even when they didn’t go looking for them.
As much as I appreciate your elaborate reasoning I’m confused why just point to “mobile providers” instead of naming those responsible for security vulnerabilities in their respective OS: Google and their ‘Open Handset Alliance’ (Andoroid), Apple (iPhone/iPad) and Microsoft (Windows Phone) etc.
Dear Andrew, would you agree that developers could pay more attention to security and safety, block security holes themselves faster then any third party and hence any AV software is just a workaround for the laziness of some of the wealthiest companies in the world?
With the greatest of respect having worked in the software development field and still taking an interest in matters regarding it your assessment is simply too black and white.
Computer programs can be thought of as a series of decisions that a machine makes depending on some condition. The number of possible paths that can arise increases exponentially to unimaginably large numbers. Add to this the fact that software must operate with other programs that the developers have no control over. This makes it impossible to forsee every security hole that exists and to attempt to would mean no software would be released owing to the time and resourced involved.
Granted there is plenty of grey area: sometimes more could have been done or practices weren’t followed that should have been.
However the fact remains that while it’s theoretically possible to test for and all fix vulnerabilies in practice it is not.
Not to mention that most mobile security apps for Android (Lookout, Norton, Eset, McAfee, etc.) are, in fact, free.
It makes me a little angry when any company thinks it is ok to use my devices, computer, phone or otherwise, to deliver their advertising for free. It’s not free. I’m paying it, and it is not ok. Perhaps we should be billing them for using our devices and services.
What bothers me THE MOST is that all these companies have decided that it is okay for them to use MY computer to store THEIR information for free – any info, any time [can you spell “cookie” or “flash”?]. Now if I want to store my information on their servers, *I* have to pay for that privilege. Why do THEY get to do it for free?
Basically because you are the product that many services sell to advertisers in order to fund the service you are using (often without paying anything) and make a profit which is after all what many businesses exist to do.
I know it seems like all this internet stuff just appears out of nowhere trivially but the truth is that hosting and development has to be paid for by someone usually and people don’t create these things entirely out of the goodness of their hearts and a love for humanity – they want to make a profit.
No one is forcing you to use these services should you not like the model. Part of that model is ads being served using your bandwidth but you can avoid this by not using the service.
In fact people agree to ads and use of data accepting terms and conditions, paying for ads (at least with product fees) and cherish the system buying their stocks: triple-fail. 😉
.oO(Guess Facebook stocks could be profitable after hundred years if they defend their market share… what a deal! :-P)
I think it partly depends on the distribution environment and partly on the notion that it’s legal to run “intrusive advertising”.
In terms of the distribution arrangement, on Windows you generally have to find out about software on the Web, then go find the Web site and download and install.
Smart people of course wait for a review by a site they trust and then download the utility from a site known for doing malware scanning before allowing it to be downloaded.
On Linux, you get most of your software from your distro’s repository, which is unlikely to have a lot of malware allowed in it. A smattering of software from very small developers gets installed via own built packages or from source code directly from the developer – which makes it a little harder to install malware directly.
I don’t know much about these smartphone/tablet “app stores” but if they work more like repositories it would be better than the Windows method. In other words, someone needs to be watching and testing the apps.
As for “intrusive advertising”, it should be banned wholesale. The only ads allowed should be those embedded in a Web page (and possibly HTML5/Flash components also more or less embedded in the Web page.) No JavaScript, Java HTML5 or Flash pop ups AT ALL.
Or mandate the OS/browser builders embed something equivalent to NoScript rather than having to install it separately (while still allowing enhanced versions by third parties.) The problem with this approach is many users will assume their device is “broken” since it can no longer do what it used to do, i.e., run wild in their browser…
“User education” doesn’t work until the problem is nearly totally out of hand (like spam), so forget that approach.
The best “user education” approach is to start emphasizing to people – especially people who store confidential info such as nude pictures of themselves on phones (Scarlett?) – that smart phones ARE computers and thus totally insecure just like their home computer. Don’t trust your computer and don’t trust your phone.
It’s my impression (anecdotally) that the vast majority of malware laden software that makes it onto Windows takes “unofficial” paths of distribution.
This most often means people downloading software bundled with means to circumvent it’s copy protection through unsafe warez distribution channels.
One can, if you aren’t aware, make the process of using circumvented protections very safe provided you are a member of or (far more likely) have access to software directly from “the scene” distribution channels (through private bittorrent trackers that use auto-uploaders for example). However most people obtain the “warez” they download from public sources such as public bitorrent trackers where anyone can upload or cyberlockers which means the uploader can add anything they wish to the software release. And indeed this is a major infection vector as I understand it still.
Obtaining software through “normal” channels is very low risk eg. you use it legally after obtaining it through legitimate channels.
As far as “app stores” being similar to repositories – sort of. As I understand it (mainly through reading various security outlets) Apples provides significant monetary barriers to joining their little operation in the form of significant cash payments. A PITA for devs but also a great way to prevent bad actors from entering to start with and certainly discouraging repeat offenders. They also check applications.
Whereas Google (disclaimer: I love my Android device) on the other hand have a trivial entry cost and do little checking making it a significantly easier target for a bad guy.
While it’s true that it is slightly more costly to be an Apple developer, an individual or small company with only $100 can publish apps to the store.
This isn’t a significant barrier to illegal activities that make them much greater money, but I believe the checking that is done to be more in-depth on Apple.
I still don’t trust everything from the Apple store, but I admit that I don’t look as hard as I would if it was off a random website.
As long as legitimate (hell, even not-so-legitimate) software vendors have paid affiliates pushing traffic to their sites and thus increasing their sales this is going to happen because greed trumps beats ethics any day. That model is broken by design.
AVG Mobilation FREE antivirus has so far kept my android phone out of trouble.
Supposedly BitDefender is currently working on an antivirus product for android, but who knows for sure.
Apps are what is needed to make your smartphone smart and unique.Im fond of app creating and find it really helpful to use site like Snappii where i can build apps in minutes.
Brian, first off let me say that I am a Symantec employee. Next, the questionable, even unethical advertising methods you bring up certainly are concerning and I’m glad you’ve called them out. I also completely agree with your “If you didn’t go looking for it, don’t install it!” best practice. It’s spot on. However, the unfortunate truth is that relying on end-users to always make the right decisions related to IT security is not a good idea. They might get it right some of the time, but not always. This isn’t a slight against end-users…I’m an end-user myself! The fact of the matter is, however, that people – no matter how tech savvy they are – simply can’t be expected to be perfect all the time. In addition, the bad guys are constantly getting better at tricking users into thinking something is legitimate when it is in reality malicious. Combine all this with not having the ability to determine if a bad decision has been made (i.e. not using mobile anti-malware to detect and remove threats) and you’ve got a recipe for disaster. For these reasons, mobile anti-malware is very important. One final thought, it’s important to remember that good mobile security software typically not only provides anti-malware capabilities, but other tools to help keep mobile devices and the information on them safe. For example, functionality to remotely locate a lost or stolen device, and to remotely lock or wipe such a device if necessary.
Spencer Parkinson
Symantec
Hi Spencer. Don’t Android and Apple mobile devices have that remote wipe and location capabilities already built in? I know that my iPhone, for example, gives me the option to wipe the data on the phone after a variable number of unsuccessful attempts at entering my screen lock PIN.
Hi Brian. Good question. Android and Apple mobile devices do have some remote wipe and location capabilities already built in, but they are somewhat limited. For example, iPhone users generally need a MobileMe account (requiring a yearly paid subscription) or a similar service to locate their iPhone and securely wipe the phone’s data if they need to. As for Android, it’s my understanding that that platform doesn’t come with remote wipe capabilities as a default feature, but that there are third-party apps that enable remote wipe. The other thing to consider is the ability to wipe some of the settings and apps while leaving others untouched. Selective wipe capabilities allow companies to wipe just enterprise settings and apps without touching the personal settings and apps.
Maybe he should have paid full attention to whomever he was dining with, and not looking for news with his smart phone. Were they/he/she that boring? Maybe karma intervened….
Why do you assume he was dining with anyone? What difference does that make to the crap ads that were foisted on his phone.
If I could mod you down 100x I would.
Fuddy-duddy advice is the best kind when dealing with security. 🙂
The increase in volume of mobile applications development brought a critical issue to our attention: security. I recommend reading further security considerations about the explosion of mobile application development in this blog article http://blog.securityinnovation.com/blog/2012/01/security-considerations-for-the-explosion-of-mobile-application-development.html
Has anyone pinpointed the adserver / adnetwork these ads are using to popup?