Malware Found Matches Code Used Vs. Defense Contractors in 2012
Cyber espionage hackers who broke into security firm Bit9 initially breached the company’s defenses in July 2012, according to evidence being gathered by security experts investigating the incident. Bit9 remains reluctant to name customers that were impacted by the intrusion, but the custom-made malicious software used in the attack was deployed last year in highly targeted attacks against U.S. Defense contractors.
 Earlier this month, KrebsOnSecurity broke the story of the breach at Waltham, Mass.-based Bit9, which involved the theft of one of the firm’s private digital certificates. That certificate was used to sign malicious software, or “malware” that was then sent to three of the company’s customers. Unlike antivirus software, which tries to identify and block known malicious files, Bit9’s approach helps organizations block files that aren’t already digitally signed by the company’s own certificates.
Earlier this month, KrebsOnSecurity broke the story of the breach at Waltham, Mass.-based Bit9, which involved the theft of one of the firm’s private digital certificates. That certificate was used to sign malicious software, or “malware” that was then sent to three of the company’s customers. Unlike antivirus software, which tries to identify and block known malicious files, Bit9’s approach helps organizations block files that aren’t already digitally signed by the company’s own certificates.
After publishing a couple of blog posts about the incident, Bit9 shared with several antivirus vendors the “hashes” or unique fingerprints of some 33 files that hackers had signed with the stolen certificate. KrebsOnSecurity obtained a list of these hashes, and was able to locate two malicious files that matched those hashes using Virustotal.com — a searchable service and database that lets users submit suspicious files for simultaneous scanning by dozens of antivirus tools.
The first match turned up a file called “media.exe,” which according to Virustotal was compiled and then signed using Bit9’s certificate on July 13, 2012. The other result was a Microsoft driver file for an SQL database server, which was compiled and signed by Bit9’s cert on July 25, 2012.
Asked about these findings, Bit9 confirmed that the breach appears to have started last summer with the compromise of an Internet-facing Web server, via an SQL injection attack. Such attacks take advantage of weak server configurations to inject malicious code into the database behind the public-facing Web server.
In an exclusive interview with KrebsOnSecurity, Bit9 said it first learned of the breach on Jan. 29, 2013, when it was alerted by a third party which was not a customer of Bit9. The company believes that the trouble began last July, when an employee started up a virtual machine that was equipped with an older Bit9 signing certificate which hadn’t been actively used to sign files since January 2012.
Harry Sverdlove, Bit9’s chief technology officer, said the company plans to share more details about its investigation into the intrusion in a post to be published Thursday on Bit9’s blog. For instance, he said, the control server used to coordinate the activities of the malware sent by the attackers traced back to a server in Taiwan.
Sverdlove said Bit9 will not reveal the identities of the customers that were apparently the true target of the breach; he would only characterize them as “three non-critical infrastructure entities.” Sverdlove said although it is clear now that Bit9 was hacked as a jumping-off point from which to launch more stealthily attacks against a handful of its customers, that reality hardly softens the blow.
“Although it doesn’t make us feel any better, this wasn’t a campaign against us, it was a campaign using us,” Sverdlove said. “We don’t take any solace in this, but the good news is they came after us because they weren’t able to come after our customers directly.”
It’s not clear why the attackers waited so long to use the stolen certs, but in any case Bit9 says the unauthorized virtual machine remained offline from August through December, and was only turned on again in early January 2013.
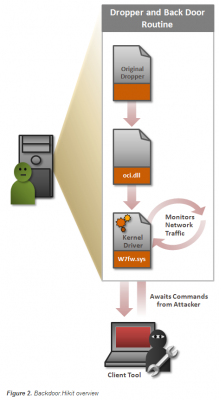
The company said the SQL injection vulnerability was used to plant HiKit, a sophisticated “rootkit” program designed to hide the presence of other malicious files and to open a backdoor on host systems. HiKit was first detailed in August 2012 by Alexandria, Va-based security forensics firm Mandiant, which said it uncovered the custom tool while investigating targeted attacks against a small number of defense contractors in the United States. Mandiant’s initial analysis on HiKit is here.
Interestingly, according to a writeup from Symantec, the version of HiKit that it examined also installed itself to host machines using a stolen digital certificate. Symantec didn’t say which firm the certificate was stolen from, but it did say the certificate in question had expired almost a year earlier — in Nov. 2011. That suggests that the stolen cert used in the HiKit attacks documented last year used someone else’s certs: According to Bit9, their stolen certificate was not set to expire until May 2013. (Update: The stolen cert referenced by Symantec appears to have been taken from a Japanese game maker YNK Japan Inc.).
The disclosure comes amid heightened public and U.S. government anxiety over targeted espionage attacks aimed at siphoning intellectual property from American corporations, government contractors and the military. Much of this conversation has centered around repeated allegations of state-sponsored hackers in China, from which a huge amount of these sophisticated, pinprick attacks are thought to emanate.
The Chinese government has vehemently and consistently denied any sponsorship or encouragement of such attacks. Responding to a story about Chinese hackers suspected of breaking into networks of The Washington Post (another story first featured on KrebsOnSecurity), the Chinese Defense Ministry was quoted as saying, “It is unprofessional and groundless to accuse the Chinese military of launching cyber attacks without any conclusive evidence.”
Apparently taking that as a personal challenge, Mandiant on Tuesday released a 73-page report detailing the activities of Chinese hacking collective known as the “Comment Crew” (a.k.a. “Comment Group”). In that analysis, Mandiant presents evidence purporting to show that more than 140 targeted cyber intrusions attributed to The Comment Crew since 2006 trace back to a single building in a run-down neighborhood on the outskirts of Shanghai that serves as the headquarters of the People’s Liberation Army Unit 61389.
The Mandiant report is chock full of fascinating details and is a good read. It’s worth mentioning that one of the two public cyberattacks that Mandiant and others have attributed to the Comment Crew was the breach last year at Telvent, a company that designs software that gives oil and gas firms and power grid operators remote control over their systems (the Telvent story also first broke on KrebsOnSecurity.com).
It remains unclear whether Chinese hacking groups were involved in the attack on Bit9, but initial analysis of the malware left behind in the breach points back to East Asia, if not China. The malicious media.exe file was compiled using Simplified Chinese characters. Also, when installed on a test machine, it beacons home to an Internet address in Singapore (180.210.204.227).
Asked what his company might have done differently or might do differently going forward, Bit9’s Sverdlove emphasized greater vigilance and more closely following one’s own security procedures. He also expressed hope that a broader and more open information sharing about these targeted attacks and threats may make things harder on attackers and help unite defenders.
“On one level, this is just more evidence that we are dealing with motivated, well organized attackers and long-term campaigns that are being waged in terms of cyber espionage,” Sverdlove said. “On another, it’s a reminder that all of us — even security companies –need to remain diligent and deploy a layered defense-in-depth. It’s a bitter pill, and it doesn’t feel good, that is the truth. But we’re strong believers in threat intelligence sharing, and I think as a security community we need to share intelligence and come together on this, because we’re facing enemies that are definitely doing that.”




Will these companies ever learn? Security is critical. You are supplying software and other services to the US government. How could you miss a data breach for more than 6 months? You should be fired for your lackadaisical practices!
i. Should “early January 2012” be “early January 2013”?
ii. Should “virtual machine was equipped” be “virtual machine that was equipped”?
I don’t think the description of the location where Unit 61398 (not 61389 as referenced above) is housed as “a single building in a run-down neighborhood on the outskirts of Shanghai” is really accurate for a number of reasons, and although I’ve not been to that specific locale I am very familiar with Shanghai from many years’ of working there and in a number of other Chinese cities in the past 3 decades.
The location lies in the north part of the Pudong New Area which is entirely occupied with buildings newly constructed over the past 20 years after a high-level decision to establish a new “world class” financial district across the Huangpu River from the traditional Bund (‘Waitan’ in local parlance) by converting that entire area to the east between the Huangpu and East China Sea coastline from an agricultural and low-rise industrial backwater into a new city that would become the dominant urban center of East Asia and rival Tokyo, London and New York (and definitely eclipse Hong Kong).
The video imagery shown on BBC World News (picked up by other networks) of the site their reporter scouted is well to the north of the ultra-high rise financial center in the Pudong CBD and close to the confluence of the Huangpu and Yangtze Rivers. He and his camera crew were apparently confronted by Army representatives after they had stopped to film outside the entry gate, and forced to turn over some (but evidently not all) of the video they had taken of the site — it clearly is a walled compound with a number of buildings inside, with the 12-story central building dominating the compound and surrounding neighborhood skyline. None of the features depicted in the video indicate to me that the site or neighborhood has become unusually decrepit or has suffered from really poor maintenance since its construction, and the white-tile facades of both the outer wall and the buildings inside appeared to be in normal condition for the ubiquitous architectural style employed.
The exterior landscaping appeared to be well-kept and the streetscape depicted as the reporter’s vehicle approached the compound also appeared quite normal for any “modern” urban setting, and while some might consider all Chinese cities “run down” by comparison with some in other countries, that particular neighborhood (and Pudong in general) appears not to merit that description.
“the good news is they came after us because they weren’t able to come after our customers directly.”
Uhm, I don’t see how that necessarily follows. Sounds like more “PR speak” about how wonderful their software is at protecting their customers from “everything”.
Getting hit by SQL injection doesn’t exactly speak well for their operation, either. They ARE a SECURITY company! 🙂 If a security company doesn’t check its Web site for SQL injection vulnerabilities, who does?
Whilst sometimes I agree with you when you repeat this over and over unless you can point to a case of Bit9’s software being breached isn’t he right?
Also based on this quote he’s not making the claim that it protects customers from everything.
No, he’s not right.
Because he’s saying that the reason the hackers went after Bit9 is because his customers could NOT be breached by those hackers.
We simply don’t know that. That is a supposition on his part. Unless he can prove that the hackers who hit him ALSO tried to hit customers AND FAILED DUE TO HIS SOFTWARE, he has no proof of his contention.
It’s simple logic.
And while he’s not making the claim HERE that his software protects from everything, the IMPLICATION of previous statements DID make imply that claim.
RSH is right about him overstating the importance of Bit9’s software. They *might* have compromised it for this reason. They might have not. That they got in via one of the most common and easily beaten vulnerabilities isn’t saying much. Plus, I’ve said before that the critical signing system should have been guarded from untrustworthy parts of their network.
@ RSH
RSH, did you read that report by Mandiant that Krebs reference? I really liked it. They did a good job on attribution, mapping out capabilities, identifying some specific people, etc. Doesn’t nullify the threat, but it’s bounds above the normal approach: “A chinese IP! Omg, state hackers, cyber war, blah!”
Hi Brian,
Did you see your investigative work was referenced in the latest Mandiant report which exposes the secretive cyber espionage “Unit 61318” of the Chinese People’s Liberation Army?
http://intelreport.mandiant.com/Mandiant_APT1_Report.pdf
Kudos!
Thanks, yes, there is a whole section in the story above that deals with the report.
About that microsoft driver file (php_sqlsrv.dll) , that name sounds bad . I have a problem when downloading a video from bitshare 2 weeks ago instead of my 520mb file with the original name sunshine.rar I got the wrong name download.php so i deleted the file and now the problem is fixed maybe a wrong file extension don´t know . About Facebook,Ny Times , and finally Apple hack i think is serious they say that no data stolen but i think tons of data have been stolen . what antivirus is a good choice Brian? I use G-data 2013 i think is good and waiting for the new antivirus technology G Data CloseGap . I found some pictures of the 2014 beta gdata http://malwaretips.com/Thread-G-Data-Total-Protection-2014-BETA
The Bit9 malware is definitely Chinese APT. The one on VirusTotal is MC RAT / Mdmbot / Naid. This is an APT similar to the Hydraq and Aurora malware and threat groups.
bit9 site seems to be still vulnerable to sql injection,they use an wp plugin out of date 🙂
227.204.210.180.ds.sparkstation.net = result of ping -a reverse DNS lookup, for those using hosts files to block out madness of this nature. Between that and using firewall rules on the ip address itself, you have a double-layer of protection. When you folks do articles please do try to include that type of information along with ip addresses of botnet C&C servers please. Thank you, sincerely, a Concerned Citizen.
Here’s the lat/long for the “alleged” Unit 61318 – 31.349413,121.573484
That certainly looks like the building shown in the BBC video.
Re the Mandiant report: Read this morning that someone called a phone number alleged in the Mandiant video to be a “hacker” – and got a 90-year-old Chinese farmer.
Make of that what you will. 🙂
Also, as someone else pointed out, “APT0 happens to be the United States”, i.e., Stuxnet et al.
It was probably a bogus number. Indicates nothing. The Stuxnet job was joint US and Israeli work. Different sources say different things about who did the main job. The network might be ours, might be theirs. We know they do espionage against their allies. Why not an APT infrastructure that *might* be them and *might* be a third party “acting on their own’? 😉
According to the article, the offending software was “compiled then signed”, meaning it’s not the original software that was used. Is the article claiming that this is what happened or are they claiming Microsoft’s signed driver was compromised and redistributed?
I don’t know about “media.exe”, but the PHP driver used is open source and can be downloaded and compiled by anyone. However, Microsoft provides a version for download that is signed by their own certificate.
I get accused of being anal-retentive, but I would really like to see a stop to the phrase “theft of private digital certificates” for 2 reasons: 1) digital certificates are public, not private, and they are meant to be public 2) the thing that was stolen that was of use in this case was the “private signing key”. It is important (well, at least to anal-retentive me) to be clear on this point as there is an extremely cheap security mechanism to protect against private key theft – it’s called a Hardware Security Module (HSM). Had Bit9’s staff had the presence of mind to put the private key on an HSM it would have been impossible for it to be stolen (short of walking into the server room and physically taking the HSM and doing a Vulcan mind-meld on the Bit9 sysadmin to get the activation PIN). HSMs were once considered rocket surgery, but no longer. They are cheap enough they can be bought on a credit card, come in USB-attached models, and easy to install. So wake up security geeks – stop trusting the OS to protect the real keys to the kingdom.
Thanks Terry, I was going to say the exact same thing. The distinctions between keys and certificates still seems to be lost on some folks…
“The Chinese government has vehemently and consistently denied any sponsorship or encouragement of such attacks. Responding to a story about Chinese hackers suspected of breaking into networks of The Washington Post (another story first featured on KrebsOnSecurity), the Chinese Defense Ministry was quoted as saying, ‘It is unprofessional and groundless to accuse the Chinese military of launching cyber attacks without any conclusive evidence.'”
That’s not t vehement denial. That’s a “non-denial denial.
And here I thought that the Mandiant report was as close to “conclusive evidence” as one could get. The Chinese denials are quite laughable. Do they expect us to think they are completely innocent?
The Chinese government (at all levels) adheres to basic principles in the delivery of propaganda and countering any truthful revelations which expose the inner workings of their security organizations, and among the most basic of principles is the one below:
“…the rank and file are usually much more primitive than we imagine. Propaganda must therefore always be essentially simple and repetitious. The most brilliant propagandist technique will yield no success unless one fundamental principle is borne in mind constantly…it must confine itself to a few points and repeat them over and over.”
— Joseph Goebbels, Nazi Propaganda Minister.
In the West, they’re usually referred to as “talking points”.
I don’t believe anything I read or hear anymore. For all we know, Mandiant, et al, could be a US Government (read NSA, CIA) front company fingering those “Chinese” as a cover story and distraction for their own intense domestic surveillance programs against US and other “western” citizens.