On Monday, I profiled asylumbooter.com, one of several increasingly public DDoS-for-hire services posing as Web site “stress testing” services. Today, we’ll look at ragebooter.net, yet another attack service except for one secret feature which sets it apart from the competition: According the site’s proprietor, ragebooter.net includes a hidden backdoor that lets the FBI monitor customer activity.
This bizarre story began about a week ago, when I first started trying to learn who was responsible for running RageBooter. In late March, someone hacked and leaked the users table for ragebooter.net. The database showed that the very first user registered on the site picked the username “Justin,” and signed up with the email address “primalpoland@gmail.com.”
That email address is tied to a now-defunct Facebook account for 22-year-old Justin Poland from Memphis, Tenn. Poland’s personal Facebook account used the alias “PRIMALRAGE,” and was connected to a Facebook page for an entity called Rage Productions. Shortly after an interview with KrebsOnSecurity, Poland’s personal Facebook page was deleted, and his name was removed from the Rage Productions page.
Ragebooter.net’s registration records are hidden behind WHOIS privacy protection services. But according to a historic WHOIS lookup at domaintools.com, that veil of secrecy briefly fell away when the site was moved behind Cloudflare.com, a content distribution network that also protects sites against DDoS attacks like the ones Ragebooter and its ilk help to create (as I noted in Monday’s story, some of the biggest targets of booter services are in fact other booter services). For a brief period in Oct. 2012, the WHOIS records showed that ragebooter.net was registered by a Justin Poland in Memphis.
I “friended” Poland on Facebook and said I wanted to interview him. He accepted my request and sent me a chat to ask why I wanted to speak with him. I said I was eager to learn more about his business, and in particular why he thought it was okay to run a DDoS-for-hire service. While we were chatting, I took the liberty of perusing his profile pictures, which included several of a large tattoo he’d had inked across the top of his back — “Primal Rage” in a typeface fashioned after the text used in the Transformers movie series.
“Since it is a public service on a public connection to other public servers this is not illegal,” Poland explained, saying that he’d even consulted with an attorney about the legality of his business. When I asked whether launching reflected DNS attacks was okay, Poland said his service merely took advantage of the default settings of some DNS servers.
“Nor is spoofing the sender address [illegal],” he wrote. “If the root user of the server does not want that used they can simple disable recursive DNS. My service is a legal testing service. How individuals use it is at there [sic] own risk and responsibilitys [sic]. I do not advertise this service anywhere nor do I entice or encourage illegal usage of the product. How the user uses it is at their own risk. I provide logs to any legal law enforcement and keep logs for up to 7 days.”
The conversation got interesting when I asked the logical follow-up question: Had the police or federal authorities ever asked for information about his customers?
That was when Poland dropped the bomb, informing me that he was actually working for the FBI.
“I also work for the FBI on Tuesdays at 1pm in memphis, tn,” Poland wrote. “They allow me to continue this business and have full access. The FBI also use the site so that they can moniter [sic] the activitys [sic] of online users.. They even added a nice IP logger that logs the users IP when they login.”
When I asked Poland to provide more information that I might use to verify his claims that he was working for the FBI, the conversation turned combative, and he informed me that I wasn’t allowed to use any of the information he’d already shared with me. I replied that I hadn’t and wouldn’t agree that any of our discussion was to be off the record, and he in turn promised to sue me if I ran this story. That was more or less the end of that conversation.
As to the relative legality of booter services, I consulted Mark Rasch, a security expert and former attorney for the U.S. Department of Justice. Rasch said companies hire stress testing services all the time, but usually as part of a more inclusive penetration testing engagement. In such engagements, Rasch said, it is common for the parties conducting the tests to insist upon and obtain beforehand a “get out of jail free card,” essentially a notarized letter from the customer stating that the testing firm was hired to break into and otherwise probe the security and stability of the targeted Web site.
“This is also why locksmiths generally force you to show ID that proves your address before they’ll break into a house for you,” Rasch said. “The standard in the security industry is not only to require proof that you own the sites that are going to be shut down or attacked, but also an indemnification provision.”
On Monday, I pinged Mr. Poland once more, again using Facebook’s chat function. I wanted to hear more about his claim that he was working for the feds. To my surprise, he gave me the number of a Memphis man he referred to as his FBI contact, a man Poland said he knew only as “Agent Lies.”
The man who answered at the phone number supplied by Poland declined to verify his name, seemed peeved that I’d called, and demanded to know who gave me his phone number. When I told him that I was referred to him by Mr. Poland, the person on the other end of the line informed me that he was not authorized to to speak with the press directly. He rattled off the name and number of the press officer in the FBI’s Memphis field office, and hung up.
Just minutes after I spoke with “Agent Lies,” Justin dropped me a line to say that he could not be my ‘friend’ any longer. “I have been asked to block you. Have a nice day,” Poland wrote in a Facebook chat, without elaborating. His personal Facebook page disappeared moments later.
Not long after that, I heard back from Joel Siskovic, spokesman for the Memphis FBI field office, who said he could neither confirm nor deny Poland’s claims. Siskovic also declined to verify whether the FBI had an Agent Lies.
“People come forward all the time and make claims they are working with us, and sometimes it’s true and sometimes it’s not,” Siskovic said. “But it wouldn’t be prudent for us to confirm that we have individuals helping us or assisting us, either because they’re being good citizens or because they’re somehow compelled to.”
Update, June 1: A little Googling shows that there is in fact an FBI Agent Lies in the Memphis area. Many of the public cases that Agent Lies has testified in appear to be child-exploitation related, such as this one (PDF).
Original post: I tried to imagine a scenario in which someone in Poland’s situation would make up a story like that, or — if the story were true — might be bold enough to brag about it. I went back over some of the screen shots I’d taken from Poland’s Facebook account before it was deleted, and discovered a saddening discussion where Poland says he is depressed because he can’t quit his habit of smoking marijuana incessantly. In one post he admits to spending more than $1,200 a week on pot. I’m not sure if $1,200 worth of weed is even humanly possible for one man to consume on his own in a week and still function, but it would certainly explain his erratic behavior. Anyway, apparently business is good.
 I had a lot of help on this research from Brandon Levene and Allison Nixon, two security consultants who have been digging into the booter scene for some time now. Levene and Nixon said they happened on ragebooter.net after a generic search for other booters indicated it was one of the top three results.
I had a lot of help on this research from Brandon Levene and Allison Nixon, two security consultants who have been digging into the booter scene for some time now. Levene and Nixon said they happened on ragebooter.net after a generic search for other booters indicated it was one of the top three results.
“What made things interesting, however, were the top advertisements for this service from a forum poster using the name ‘Primal Rage,'” Levene said. “The contact information across multiple forums included the email Velocitypro@liv
Levene said the biggest break in their research came from a fawning post on a slightly less public site — leakforums.org — a forum dedicated to sharing information on, well, leaked forum databases for one thing. In a twist that makes this already odd story even weirder, Primal Rage/Justin says in his application for membership on leakforums.org that he is starting a new company called “Booter Be Gone,” which he said would be all about “leaking booters online and there [sic] databases.”
The short CV he posted to the leakforums application said he had experience as a computer repair technician and “Ddos mitigation specialist.” Translation: Eliminate the competition by leaking their databases, and then sell DDoS mitigation services to businesses besieged by attacks of the sort launched by his booter services. What could go wrong?
“Justin’s cross-contamination of online personas led me to dig deeper,” Levene said. “Simply by drawing focus he made himself a target. The whole thing with his service being for ‘legitimate stressing’ is silly. Even the news updates from the login panel are discussing ways to target users.”
Nixon said her research on ragebooter.net showed it to be a booter under active development and one that seems to average more than 400 attacks per day.
Oh, and that backdoor Poland claims he added for the FBI? Nixon may have found at least one of them:
“The booter has some information leakage problems too,” Nixon said. “The victims can see the ragebooter.net username of the logged in attacker because that info is, bizzarely, sent within attack traffic.”
The real irony of all this? Poland admitted in one of our Facebook chats that his own site was recently breached, leading to the leak of ragerbooter’s user database; the attackers broke into his Skype account, and then rifled through his Skype chats until they found login credentials to his servers. Was it the work of hackers allied with competing booter services? A spurned FBI agent? Or Justin himself? One thing’s for sure: If Poland’s “booter be gone” soon, it is nobody’s fault but his own.
One final note: Services like ragebooter.net would not be nearly as usable or profitable if they were unable to accept payment via PayPal. A Paypal spokesperson declined to comment on this particular booter service, but said the use of its service for DDoS-for-hire sites would violate its terms of use agreement.
“While we cannot share specifics on our customers’ accounts due to our privacy policy, we can confirm that we will review suspicious accounts for malicious activity and work with law enforcement to ensure cyber criminals are reported properly. We take security very seriously at PayPal and we do not condone the use of our site in the sale or dissemination of tools, which have the sole purpose to attack customers and illegally take down web sites.”





Excellent research! But there is much more work that needs to be done….
Last October, ragebooter.net was claiming a direct-connect IP address behind CloudFlare of 74.125.227.128. Sometimes CloudFlare users set up a spoofed direct-connect in their CloudFlare control panel. That’s probably the case here, because it looks like Google owns the 74.125.0.0/16 netblock.
Our software discards entire netblocks from our database of listed IPs behind CloudFlare if they are clearly bogus. For example, 127.0.0.0/8 and 192.168.0.0/16, as well as addresses such as 8.8.8.8 and 8.8.4.4 that are used by Google’s public nameservers. Obviously, we do not catch them all.
In fact, I think I’ll keep the data in this case, because for this particular netblock at 74.125.227.0/24 our site shows dozens of domains. For a domain to be listed here, it means that it uses CloudFlare nameservers, which in turn means that the domain must have been registered somewhere so that the nameservers made it into DNS.
Take a look: dozens of these domains are booter sites, judging from the domain names:
http://www.cloudflare-watch.org/cgi-bin/cfdom2.cgi/us74.125.227
This is food for research if you can dig out domain name registrations, even though Google most likely has nothing to do with them.
Paypal and Cloudflare are the companies to blame that make the booter scene possible. If it weren’t for Cloudflare, all booters would be ddosed into oblivion by their competitors. Paypal provides convenience and ease of use for the vast majority of booter customers, who in my analysis are mostly casual ddosers.
Ragebooter takes payments via paypal email billing@rageproductions.net, but I don’t think his service is worth it. Half the functions on his booter are broken, and even though the article mentions reflected DNS attacks, ragebooter is not capable of executing them. I think Paypal should shut his account down along with all the other paypal accounts that are publicly used on ddos-for-hire websites.
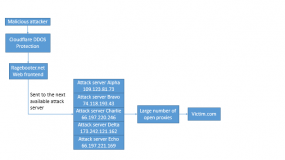
Brian (Allison), thanks for the flowchart. They always help understand the technical path of these attacks better.
No problem. This is generally how most booters work, with a simple top-down command structure. Also, want something else amusing? here’s a sample of their POST flood traffic, complete with x-forwarded-for leakage. Assume it’s sent from ragebooter account names “test123”. Yes, the account name is the data payload. Amazing:
POST / HTTP/1.0
Host: victim.com
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)
Accept-Encoding: gzip, deflate
Content-Length: 7
Content-Type: application/x-www-form-urlencoded
Via: 1.1 IENGINE:3128 (squid/2.6.STABLE21)
X-Forwarded-For: 66.197.220.246
Cache-Control: max-age=259200
Connection: keep-alive
test123
Totally agree with you. It makes me wonder why/how the FBI didn’t burn all these services yet.
And Cloudflare should be ashamed, they do not block them as they say that it’s “free speech” and needs a “court order” but that’s only because it brings them more customers. They should be prosecuted for this too.
And yet, last I know, Spamhaus is using Cloudflare for its DDoS mitigation service provider.
http://www.spamhaus.org/news/article/695
Hummmm Paypal. Heh. This is like the scenario of a Hitman getting paid cash by the person who hired them.
Paypal will have payment records of all who use these type of services. It shows malicious intent on both ends. It shows accounts used, credit card numbers, note to the service and more.
If the Feds get (or currently have) that information, they may have all of these blockheads standing in front of a judge. But, the Feds will probably gather as much intel on these individuals before bustin’ in their door.
FYI – http://www.robtex.com is an excellent research tool.
I’m always amazed that these people can’t successfully separate their social media profiles from their more dubious online activities.
I’m equally amazed that many of them even have Facebook profiles, Twitter accounts, and whatnot to begin with. You’d think they would shut up online and try to keep a damn low profile. Oh well.
Their “hardware” is slow.
Back in the day that was called wetware.
Though I think the term went out of fashion around the same time William Gibson went out of fashion.
Interesting read 🙂
I would love to get more into the sort of work you do Brian.
Security and the research you do is very interesting
I don’t get it, why would Cloudflare allow ragebooter.net to hide behind their DDoS protection when in the fact the booter site always anyone to attack other websites or internet infrastructures with large amounts of malicious data ? Am I missing something here? Yet another very interesting article
First CloudFlare provides shelter for the marauders, which encourages them to attack the villagers. Most of these villagers are bloggers with cat pictures, and not qualified to see through CloudFlare’s hype. Even the marauders don’t care about villagers with cat pics, come to think of it.
But the mainstream media is alarmed; eveyone seems to be under attack these days. The next thing CloudFlare knows is that they are signing up more and more nervous villagers who are afraid of the marauders, by offering them a free “protection” service at a very basic level. Even more advanced customers sucked into CloudFlare’s paid options, which offer slightly better protection.
It’s an effective business plan, actually, if you don’t mind the ethical implications.
Here is a list of some domains that use CloudFlare nameservers and have the term “booter” or “stresser” in them. This is just a quick sample. There must be several times this number of booter sites using CloudFlare, but they don’t bother using those terms in their domain name.
http://www.cloudflare-watch.org/booters.txt
This Pastebin post just came to light. I dug up a lot of dirt but this wasn’t something I was previously aware of.
http://pastebin.com/hqJz8tYg
——————————————————————————————————————————————————
justin is an official FBI informant now. He will give all information to the FBI about you in order to not go to jail for 20 years. This was the deal made.
He has been raided by the fbi a month ago. He carded without using a VPN, and he never cared about his protection.
His home was his dump and he thought he was invincible.
He is now an FBI informant. Even if you didn’t do anything yourself and you’re talking to him, he will give information to the FBI about you if needed. I highly recommend to stay away from this person, for your own protection.
Information about him: He threatens people whenever he’s not happy. He does shit that doesn’t make sense. Don’t be afraid because he has a few servers and he’s gonna threaten you for your connection to be down. Stand up for yourself and I would suggest to block him and remove anything completely about him.
[INFORMATIVE ONLY]
Photos of him: http://imgur.com/JgNAev8
https://i.imgur.com/T5zv1JF.png
Names on the internet: Primal rage, Justin Poland, DISCO
his facebook: https://www.facebook.com/PRIMALRage
his skype: toxicrager
He’s threatening to ddos anyone so anyone who is good can report him to the FBI, it’s illegal in the states and also he’s being watched by the fbi so if you can find a way to report him. = good.
Copy paste this as much as you can if you know anyone related to him, for your own security and your friends.
——————————————————————————————————————————————————
If anyone can shed some light on this, or wants to contribute any new booter database information, please let us know. my twitter is @nixonnixoff , also contact Brian Krebs.
Sir for one you dont know what the hell your talking about and you must be talking to someone who is way off. However you got the image from omni and you post this stupid shit on ever forum. Get a life, find a girlfriend and get off my nuts fucker. Your clearly wrong.
You’re a highly narcissistic, delusional person who blames others , for your own selfish and malicious actions. You just made my day, LOL !
And your a fat ass with no life? Along with the rest of the people on this site. At least I make money doing what I do and I have a life. Go do something besides playing games online and talking shit.
Brian needs to put up a “do not feed the booter trolls” sign on this site
I’m confused. I thought you gained a hundred pounds in the last year?
I guess the guys who stab grandmothers in the back to steal their purses can use Justin’s rationale as a defense. “Hey, at least I’m making money!”
I think Justin is still living with his parent , has very few responsibilities and lives a cogitative reality that most of us truly can’t understand or comprehend .
You know the young kid in his bedroom with his overclocked gaming machine , lurking in the dark shadows of the internet trying to make himself look better then what he real is by making outlandish and or grandiose claims of intellectual superiority.
My guess is he is highly paranoid , and is seeking attention by making a “booter site” to obtain access to the hidden criminal underground by providing online tools .
But that is just my opinion…..
Hello,
Actually I have my own duplex with two kids and a girl?
I really am sorry but whoever has been posting on this site acting like me this whole time is not me. I swear to god its not me.
Kind Regards,
Justin Poland
I forgot every reader of this blog is not gainfully employed :p
Ahhhhh shut your moronic Pilehole.
The guy who knocks people off playing games is telling all of us to stop playing games, so he has less business. Thats an awesome business strategy !
You brought this “sighting” upon yourself. You showed your cards without much effort by an excellent reporter and your pissed off at us? Look in the mirror and say the following phrase over and over again……DOH.
No I’m Justin. You stop impersonating me now!
Hi Justin. I’ll make a note to find a girlfriend at some point, thanks.
I think I found your picture but I’m not sure if it’s you. I’m terrible with faces and this one looks a lot different from your dating profile. Is this you?
http://www.justmugshots.com/mississippi/desoto-county/13549104
Allison is the name of a female.
You clearly do not understand the difference between “your” and “you’re.” Perhaps you should return to high school to graduate.
And speaking of nuts …
Q: What does one call a male with a 1″ penis?
A: Justin.
Wow… I really hope that you know that this wasn’t even me the whole time posting on this site till just now. If Brian Krebs wants to confirm it he can view my ip. I am in WV and just saw this for the first time today.
Kind Regards,
Justin Poland
Yeah… good thing nobody can use a proxy, vpn, mirror, spoof… to change the IP that would show up on his site. Excellent logic for someone who supposedly knows something about how to manipulate IP
The young man just needs an honest relationship with Jesus.
He needs an honest relationship with Bubba in a federal penitentiary more though.
You have hit the heart of the matter. Well said, Kirk!
Good job Brian as usual, had a good laugh reading all the way through this one. I really do question if this young man Justin Poland is perhaps mentally retarded. Hack Forums surely is a breeding ground for the next generation of script kiddy cyber criminals!
They say that these types of people have some type of autism ( Asperger Syndrome) like in the case of Ryan Cleary, one of the U.K. miscreants who was one the Lutzsec 4
Aspergers has been taking the rap for a lot of people’s bad behavior.
Sometimes, people thought to have Aspergers – are just jerks.
No signs of [autism] spectrum disorders from Justin.
He’s just an idiot with a weed addiction.
His hooked on the wacky Chronic. Maybe he should change his online name handle to “Tommy Chong”
Kind of interesting the title of this page:
http://www.leakforums.com/file_that_doesnt_exist.php
Title: RAGE BOOTER – 404 PAGE
Conclusion: leakforums.com = Ragebooter ???
Leakforums.com was sold on HF by the member “Philly”.
vipleakforums.com/newreply.php?tid=675
I have not yet been to this site. If his so-called booter script was “leaked” maybe this is a way for all future booters to be tracked by the FBI should they be lazy enough to use this “product”.
Great Story Brian! haha. You talk to alot of hackers Brian, is it me? or are most of them pathological liars by nature. I mean I’ve only met two in real life. I’ve seen them pressing credit cards on chinese equipment, with numbers they bought from russians. But i mean they were both delusional liars. They type of people who can’t stop lying that might need medication.
And well take it from an online gamer thats been gaming for 20 years…..remaining anonymous online almost encourages that pseudo fantastica, compulsive lying, and pathological delusional behavior. I think its the nature of most hackers, imo. Imagine guys with multiple personalities hahah. They prolly have multiple identities.
Online gaming is so bad right now…. I wonder Brian, if you have ever come across the sites that sell all the hacks/bots. 3rd party software to cheat in online shooters? I always say its not just piraters that cause major companies to abandon the pc market. its also the HACKERS! who cheat and make people “ragequit” from games. You don’t have to be a computer nerd to know whos cheating. It might not even be because of 3rd party tools, just exploiting glitches in the game sometimes. Most normal people in society now have all abandoned pc. Including alot of major corporations like EA sports.
I wonder what kind of sales the people that sell these gaming hacks make?
I’m willing to bet its way more widespread then people realize. I mean these pc gaming communities are very tiny. The only popular games are rpg like games. Even though FPS shooters are more sportlike And now that mouse and kb is on the upcoming ps4. the pc gaming industry is totally gonna die. I don’t want to be forced to buy a seperate pc box just for gaming. I want to play on the pc i already own. But because of hackers like this guy. I feel i have no choice if i want more competitive matches or if i want to play certain games unavailable ( like sports games).
http://www.anonpaste.me/anonpaste2/index.php?fe7f18bba8782377#0MI4Vp2YdDYV5eX5atsYOM4iB3x6c5JmM65lDXlk9ko=
RAGEBOOTER.COM DB LEAK #5/17/2013
I find it funny how, today he shut down all his connection with the online world, such as his skype, his twitter, facebook(s), his booter.
Also. He told people that they should baypack all the payments sent to him even though that would mean he would be broke since his only way of making money was trough the stresser. Oh well.
Seems a bit suspicious to me. Nice article BTW.
Nice article, but it does bring up some interesting points. If this article wasn’t written people who use ragebooter might get a call from their friendly local FBI agent. But now that its ‘public’ no doubt some will stop using the ragebooter site.
Yes social networks are evil.
Now go update your facebook page. 🙂
I wonder if the FBI had a clause in its “deal” to where if this, Hobo would expose his ties with the Feds, that the “deal” is off and he would be new meat for Bubba.
I would continue to search for his activity and antics. Its only a matter of time before he shows back up doing the only thing he seem to know how to do – even if it is absolutely clumsy and pathetic effort or not.
It could simply all be bait – to draw others in. You can search phrases all day long and I am sure he will pop up and respond to one of them, like in here. LOL.
It never ceases to amaze me how many ‘wannabe’ hackers devise these convoluted plans to sell services online – and then go about it in the most moronic way possible.
I’m no crook, but it would seem this guy would take his anonymity a little more seriously, considering the plot.
I’ve been following the blog for quite some time now, and I have to say it – I love your investigative journalist style of blogging. You really take it above and beyond to capture the story and root out the facts.
Thanks for an entertaining read while I’m at work. Speaking of which, I better get back to it.
Sorry for the off-topic, but
anyone has an idea why I get an Error 404 when trying to access either the May 14 or the May 13 posts by Brian ?
Should have added :
only when I click on the title of the post. If I click on “continue reading”, the whole post comes up.
Ragebooter site is modified now, they removed the controversy content. I guess they running their service from underground 🙂
Justin gets even more press to promote his service
http://arstechnica.com/security/2013/05/ddos-for-hire-service-works-with-blessing-of-fbi-operator-says/
Reminds me of when i use to play the pc game counterstrike years ago. Haliburton and Army research and development would be probing my ports. I swear. Then i had this army recruiter stalking me for years outside my highschool and calling me up and i wondered if it was because of the video game haha.
I alos have reason to believe the gov’t is loggin all convos in another game i play. battlefield 3. EA is logging the chats….even though u can’t scroll through them in the game. And we all know the FBI is logging everything on facebook….lol Thats a given.
But when it comes to these hackers.. they all pathological hackers and you never know what to believe. gotta take what they say with a grain of salt.
Most security tools and services often start like this (e.g. Metasploit -> Rapid7) — at first, the community will be concerned because of how easy/accessible it is, then it makes its way mainstream and people become more accepting of the concept.
Most security tools and functions are heading this way; it’s only going to be easier and cheaper to do hacking/pentesting from the cloud. I think he also has a point in terms of the limits of his liability. If he’s running off Amazon, for example, why wouldn’t Amazon be liable — or even AT&T if the packets travel over their network?
Google, Amazon, and crew all do this – they’re providers and disclaim any adverse use of their services.
Hello,
My name is Justin Poland and I am the true owner of Rage Booter.
Now I know many don’t even like the idea of a booter and I fully understand this, however I Justin Poland was not the person Krebs interviewed. I have been in West Virginia since the 6th because my little brother and sister are graduating from high school.
This being said the person you interviewed was ‘MindCrack’, he has been known to social engineer company’s and Skype into getting my personal info as well as passwords and such. Once he had this information he took over my Facebook and all which I was unaware of because I was not using the internet nor Facebook since I have been helping my siblings prepare for there future.
I can personally guarantee that the FBI has no involvement in my project nor will it ever. The mug shot photo posted earlier was in fact me when I got a DUI, however shortly after that I left for West Virginia.
I mean no harm to anyone and just wanted to set the record straight. MindCrack goes around trying to diminish my sales anyway he can and often pretends to be me so he can get into other stressers. He has currently social engineered Skype into giving him two of my Skype accounts already. I have a personal Skype which he doesn’t know and never will, though I have considered to stop using Skype due to there poor security and even poorer customer support.
I have re-secured my servers as well as everything else however I am still in West Virginia. If Mr. Krebs would like a real interview I am willing to give it to him but this story is completely false and really somewhat unbelievable.
Kind Regards,
Justin Poland
i smell FBI damage control. 😉
What do you mean by that? I assure you I have nothing to do with FBI and have never met nor will ever met a FBI. I am still in West Virginia and Krebs should be able to confirm that the person he interviewed was not me. If I have to I will drive down to Alexandria and prove it to him.
But w.e though I have way more important things to worry about.
Kind Regards,
Justin Poland
“Siskovic also declined to verify whether the FBI had an Agent Lies.” Smells like utter BS. You can call ANY field office and ask whether or not an agent exists and they will answer you truthfully. After all, if someone knocked on your door and you needed/wanted to verify this individual, this is the route to go, speaking to any SA or SAC.
Yeah, I thought so too. I didn’t have any problem getting the Los Angeles FBI field office to check on whether there was an Agent Richard Miller on their payroll, when I was investigating the spoofed letter from the FBI that tried to get Prolexic to drop me as a client:
http://krebsonsecurity.com/2013/03/the-world-has-no-room-for-cowards/
As a side note, while the FBI LA office was truthful in their statement that there was no one named Richard Miller currently employed as an agent of the FBI, there was at one time a very famous Richard Miller FBI Agent: According to research that Prolexic’s techs dug up, in the 1980s an FBI agent by that name earned the distinction of being the first FBI agent to be indicted for esiponage; he apparently was convicted in 1984 with conspiring to sell classified information to KGB agents:
http://en.wikipedia.org/wiki/Richard_Miller_(agent)
I was tasked to perform an incident response, and forensics job for a VoIP based compromise where the company decided to call in the FBI. We (myself and colleagues), ended up spending a lot of time explaining the methodologies we used to pinpoint data (PBX was running on embedded Linux), how the log files were structured, how information was coming across via SIP packets, and so forth. About 3 months after the fact, I got a call from someone with something out of MAD Magazine, don’t remember the exact name, was something like “Johnny Hollywood” or something extreme. I told him I would get back to him. Called MY local field office, explained to them why I am asking about this agent, and they only verified whether or not he worked at said field office. (They obviously won’t tell you which group he works at/for).
Something to keep in mind, calling a “Press *anything*” of the FBI will get you the same repeat answer. “We can neither confirm nor deny that we can even confirm or deny this…” These “press” people aren’t typical agents. You can ALWAYS verify the identity of any agent by calling their field office, or yours.
Another thing to bear in mind… Right now I can take the caller ID of any field office, change my caller ID, call you (Brian) and yap you to death: “This is Agent Orange, and I will confirm that Hacker Bunny Foo Foo is indeed working with us!” If you use Caller ID as an identifier ever… Shame on you.
J. Oquendo
@BrianKrebs
Do you acknowledge that you where not even speaking to me this whole time? I hope you understand that. None of your interview has been to me. I have been in WV. This is clearly a kid trying to scare customers away from my product so that they can make more sales, however it failed.. but I hate for you to think your story is any what legit when it wasn’t even me who you interviewed.
I have got my facebook back and if you wish to talk we can talk on my phone or facebook..
“One final note: Services like ragebooter.net would not be nearly as usable or profitable if they were unable to accept payment via PayPal.”
And what about bitcoins?
Asylum booter is just one of them. There is many more. This is becoming quite alarming. DNS servers has to be patched and zombies PC should be quickly banned from internet in some ways.
Al, bitcoins, yeah the official black market money!