Criminal commerce on the Internet would mostly grind to a halt were it not for the protection offered by so-called “bulletproof hosting” providers — the online equivalent of offshore havens where shady dealings go ignored. Last month I had an opportunity to interview a provider of bulletproof services for one of the Web’s most notorious cybercrime forums, and who appears to have been at least partly responsible for launching what’s been called the largest cyber attack the Internet has ever seen.
Earlier this year, the closely-guarded English-language crime forum darkode.com was compromised and came under a series of heavy distributed denial-of-service (DDoS) attacks aimed at keeping it offline. Around that same time, darkode.com welcomed a new member — a bulletproof hosting broker aptly named “Off-sho.re” — who promised to defend the site from future DDoS attacks.
Off-sho.re also said he could offer more robust and crime-friendly hosting services than darkode’s previous provider — Santrex, literally an offshore hosting facility located in the Seychelles, a 115-island country that spans an archipelago in the Indian Ocean. Off-sho.re’s timing was perfect: Darkode desperately needed both, and Off-sho.re seemed to know his stuff, so he was admitted to the forum and given stewardship of the site’s defense and hosting.
STOPHAUS V. SPAMHAUS
Of course, to successfully defend a network against DDoS attacks one must know a great deal about how to launch such assaults. Indeed, Off-sho.re was an integral member of Stophaus, an upstart group of bulletproof hosters that banded together in March to launch a massive Internet attack against anti-spam group Spamhaus.org.
Hundreds of ISPs route or deny traffic based in part on Spamhaus’s blacklists of known, cybercrime-friendly ISPs, and Stophaus formed in response to Spamhaus’s listing of bulletproof hosting provider in particular: A network known alternatively as CB3ROB, a.k.a. “Cyberbunker” because it operated from a heavily fortified NATO bunker in The Netherlands.
Off-sho.re is moderator of the Stophaus forum, and not long after joining darkode.com, he was recruiting fellow darkode members for the Stophaus cause. Stophaus’s records show that another core member was “0ptik,” a competing bulletproof hosting provider. Spamhaus had listed dozens of Optik’s domains, as well as virtually all of the IP address ranges Off-sho.re had rented at abuse-friendly Romanian hosting provider Voxility. It was payback time.
In late March, Spamhaus became the target of what experts called one of the largest computer attacks on the Internet. The method of attack — a DNS amplification attack — was similar to that first seen used in attacks more than a decade ago that targeted the heart of the Internet’s routing system, except that it was by most accounts much larger.
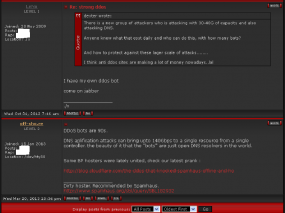
“DNS amplification attacks can bring up to 140 Gbps to a single resource from a single controller,” Off-sho.re wrote in a darkode.com posting less than 24 hours after the attack on Spamhaus began. “The beauty of it [is] that the ‘bots’ are just open DNS resolvers in the world.” Linking to a writeup from Cloudflare.com about the attack, Off-sho.re stated that “Some BP hosters were lately united, check out our latest prank.”
Last month, authorities in Spain arrested Sven Kamphuis, a 35-year-old Dutch man, thought to be responsible for coordinating the unprecedented attack on Spamhaus. According to Spamhaus, Kamphuis made claims about being his own independent country in the Republic of Cyberbunker. But according to Off-Sho.re, Kamphuis was just the public face of the movement. “Sven didn’t attack anyone,” Off-Sho.re wrote in an online chat with KrebsOnSecurity.
If Kamphuis was just a mouthpiece, who was responsible for the attack? What is interesting about the Stophaus movement is that Off-sho.re very well may have prompted Spamhaus to finally place CB3ROB/Cyberbunker at the top of its World’s Worst Spam-Support ISPs list, a move that helped to precipitate this conflict.
According to Spamhaus, while Cyberbunker and Spamhaus certainly have a bit of a history together, Cyberbunker wasn’t really a focus of Spamhaus’s blocking efforts until the fall of 2012. That’s when Spamhaus began noticing a large number of malware and botnet control servers being stood up inside of Cyberbunker’s Internet address ranges.
“We didn’t really notice these guys at CB3ROB much until last fall, when they started hosting botnet controllers, malware droppers and a lot of pharma spam stuff,” said a Spamhaus member who would only give his name as “Barry.” “Before that, it was mainly routing for some Chinese guys — Vincent Chan — fake Chinese products.”
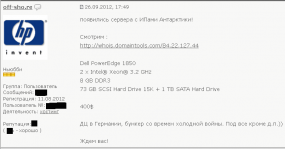
Oddly enough, this coincides with Off-sho.re’s entrance on the bulletproof hosting scene (at least as advertised on crime forums). In his introduction post to Darkode, Off-sho.re referenced his bulletproof hosting sales threads at two Russian-language forums — expoit.in and damagelab.org. In these threads, which began in Sept. 2012, Off-sho.re advertised the ability to host ZeuS and SpyEye botnet command and control networks for between $99 and $199 per month, and bulletproof domain registration from $30 per month. More importantly, Off-sho.re proudly announced that he was offering a premiere BP hosting service for $400 a month that was housed in an old NATO bunker in Holland and that used IP addresses assigned to CB3ROB (see screenshot to left).
CRUELTY-FREE CYBERATTACKS?
The attack that hit Spamhaus — known as a DNS reflection and amplification attack — leveraged unmanaged DNS servers on the Web to create huge traffic floods. DNS servers act as the white pages of the Internet, transforming or “resolving” human-friendly domain names into numerical network addresses used by computers. Typically, DNS servers only provide services to machines within a trusted domain. But DNS reflection attacks rely on consumer and business routers equipped with DNS servers that are (mis)configured to accept queries from anywhere on the Web. Attackers can send spoofed DNS queries to these so-called “open recursive” DNS servers, forging the request so that it appears to come from the target’s network. That way, when the DNS servers respond, they reply to the spoofed (target) address.
The amplification part of the attack takes advantage of the ability to craft DNS queries so that the responses are much bigger than the requests; they do this by leveraging an extension to the DNS protocol that enables large DNS messages. For example, an attacker could compose a DNS request of less than 100 bytes, prompting a response that is 60-70 times as large. This “amplification” effect is especially pronounced if the perpetrators query dozens of DNS servers with these spoofed requests simultaneously.
I reached out to Off-sho.re via instant message to ask why he thought it was okay to hijack servers that belonged to someone else for use in attacks on third-parties.
“No one launched or abused any attack, all DNS resolvers were machines that had this option open,” Off-sho.re explained. “No bots were used and no one was infected. The individuals who did the attack, didn’t harm any computer in order to launch it. So your question about the legal aspect of this thing is not relevant.”
Rodney Joffe, vice president and senior technologist at Neustar, a Sterling, Va. based security company that helps firms defend against large cyberattacks, said such attitudes are common criminal delusion.
“If you want real world analogues you can say, hey, that car was left open so I broke into it,” Joffe said. “That’s like saying, hey, all I did was open the car door, put a brick on the gas pedal and let the car run down the road and smash into someone’s house, but the guy who owned the car shouldn’t have left it unlocked. Put another way, just because I have a non-functioning lock on my door doesn’t give you permission to use my property.”
NOTHING PERSONAL
Off-sho.re insisted he did not directly participate in launching the attacks on Spamhaus. But as I discovered in my reporting, he had no qualms about ordering his minions to attack my site prior to our chat conversation. A few days before I reached out to him, Off-sho.re orchestrated an attack against KrebsOnSecurity.com as a means of vetting a new darkode.com member.
That assault was part of the initiation process for “Abscond,” a hacker who was seeking admittance to darkode.com and who’d claimed his specialty was providing DDoS services. To prove his firepower, Abscond was told to knock one of three sites offline: Darkode.com, krebsonsecurity.com, or xylibox.com (the blog for a French security researcher who goes by the pseudonym “Xylitol”). The conversation below took place between Off-sho.re and Abscond after the latter’s botnet failed to bring down Darkode.com.
[00:01:51] <Off-sho.re> You can try on DK enemy sites as well, that will give you my vouch as well
[00:01:56] <abscond@jabber.org> ok
[00:01:58] <abscond@jabber.org> ill try that
[00:02:04] <abscond@jabber.org> let me try attack first
[00:02:09] <Off-sho.re> Ok.
[00:02:10] <abscond@jabber.org> and a few mins for bots to come back 😀
[00:02:14] <abscond@jabber.org> so im at full power
[00:04:26] <abscond@jabber.org> whats the enemy site?
[00:04:33] <Off-sho.re> there are 2, choose any
[00:04:40] <Off-sho.re> krebsonsecurity.com, xylibox.com
[00:04:47] <abscond@jabber.org> haha 😀
[00:04:49] <abscond@jabber.org> krebs
[00:04:50] <abscond@jabber.org> 😀
[00:04:52] <abscond@jabber.org> fkin fagt
[00:05:10] <Off-sho.re> Krebs is on Prolexic
[00:05:15] <abscond@jabber.org> ok.
[00:05:53] <abscond@jabber.org> darkode got some good ddos protection
[00:08:26] <abscond@jabber.org> krebs down?
[00:08:30] <Off-sho.re> Checking
[00:10:13] <Off-sho.re> Krebs is down, well done this time
“I confirm that Abscond can provide DDoS services,” Off-sho.re wrote to the darkode community.
Asked about the incident in a private chat via Jabber, Off-sho.re said the attack on my site was just a “stress test”.
“Regarding the site stress test – nothing personal,” Off-sho.re wrote.
By the way, “stress testing” is the new euphemism for launching DDoS attacks. If you aren’t yet familiar with this term as it relates to online attacks, see DDoS Services Advertise Openly, Take PayPal, and Ragebooter: ‘Legit’ DDoS Service, or Fed Backdoor?
Off-sho.re’s attitudes about ownership and what’s legal and acceptable online seems common in denizens of groups like Stophaus and other grey- and black-hat hacking collectives: that if something can be done then it is must be legal, allowable and otherwise okay. The governing mantra of these folks seems to be, “what’s-mine-is-mine and what’s-your-is-mine, too.”




DNS amplification attacks are becoming much more damaging because of DNSSEC, which bloats DNS answer packets to monstrous sizes. DNSSEC is actually more useful to attackers than to anyone else.
Lack of verification of sender in the transport layer is what makes this all possible – and that is the real problem.
Spoofing packets has been around for decades, the whole internet is based on a level of trust that is no longer applicable. That DNSSEC swallows a spoofed packet and sends a monstrosity to an unrelated host is a symptom, not the real cause.
You’re right, BCP-38 should be deployed everywhere. That is a real solution that covers a broad range of attacks, not just DNS reflection.
But it doesn’t change the fact that DNSSEC is more useful to attackers than anyone else.
What a retard, he didn’t know that xylibox.com is on blogspot. Good luck taking down google.
Your bias is inconspicuous Brian
Off-sho.re was not as amusing as Justin, but he shares the same psychopathic belief system.
“if something can be done then it is must be legal, allowable and otherwise okay”
Much of the world moved in this direction a long time ago. This attitude is not restricted to hackers.
Song-stealing, aka sharing, was one of the first canaries in the coal mine. Song-stealing was not an issue before CDs made digital copies of songs equivalent to the original. Anyone who copied songs from records using cassette tapes knows this, as the quality degraded with every copy. Now it is easy, so it is common.
But the USA’s shysters and capitalists were to first to demonstrate this school of thought, believing that loopholes were a license to run rampant through society’s roses.
I must stop writing now because I’m on double-secret probation.
Change “first canaries in the coal mine” to “first canaries in the digital coal mine.”
It’s like using a public water fountain. It’s there for a purpose, whether your getting a sip, or filling up a bottle. If it’s there people are going to use it however they want, if the owners of it want to stop they can easily put a sign up stating the rules, or in other words hosts can just disable recursive dns.
I could offer you a number of reasons that I think you’re comparison is not very apt however I think I’ll just go with this: most p2p users don’t think they’re causing any harm since no one has lost any property.
Yes you can argue – correctly I think as it happens – that sales are reduced however the p2p user isn’t usually in the mindset of “I’ll download this so I don’t have to buy it” rather they are in the mindset of “I’ll download this because it’s convenient and providing gratification much sooner”. The IP owner has lost a potential sale however they have not lost any property: they are not worse off after the copy has been made.
It’s rather different to illicitly transferring money from a bank account or knocking sites offline.
A common attitude these days toward security and privacy can be illustrated this way: A padlock is interpreted as a challenge to overcome, rather than a privacy mechanism to respect.
Padlocks only keep out honest people.
The morality discussion is interesting, but it is as old as humanity itself. Bad behavior is still bad behavior, it’s really just the degree of caring about it that makes some of it more egregious.
No harm no foul?
When we as a group decide that this behavior is no longer tolerable, we as a group take action to mitigate it.
As always once identified and brought out into the light of day these cockroaches scurry back to the dark corners of the internet and hide until they need more attention.
SgSanford: A padlock, a login screen, are ‘stop signs’. They are designed to give you some time to think, and then make the moral choice. If you are determined to breach either one, you have a problem with your ‘heart’ or ‘soul’.
You wrote: “When we as a group decide that this behavior is no longer tolerable, we as a group take action to mitigate it.”
The ‘group’ already agrees that this behavior is wrong. It is a commonly-held value. However, the ‘group’ cannot cure a person’s ‘heart’ or ‘soul’ for them. If they are determined to violate another person’s tool shed or computer, they will do it.
Bottom line – we always do what we want to do. The problem is with our ‘want-er’.
The criminal attitude reflected in “what’s mine is mine and what’s yours is mine” is as old as mankind. What’s new is the risk reward ratio on internet is still far out of balance compared to physical crimes. Not sure governments have the will to deal with such threats since they are global and respect no boundaries.
“The criminal attitude reflected in ‘what’s mine is mine and what’s yours is mine’ is as old as mankind.”
That is only partially true.
In 1959, the country was shocked to its core by the killing of most of the Clutter family in Holcomb, Kansas. Truman Capote’s book “In Cold Blood” was written about this incident. Today, multiple killings are painfully common.
Many people grew up in towns safe enough for families to not worry so much about locking house and vehicle doors. Today, this behavior would not be wise anywhere.
Something is different today.
I have kids. They only know what you teach them (by instruction or by imitation). It’s hard work raising kids. Even if you put tons of time into it you can still fail.
Society doesn’t have a lot of role models out there. I can hardly name anyone that I would want my kids to emulate, including myself some days.
Still, I’m a much better parent than the internet will ever be. The world probably needs a distributed parenting network to turn this thing around.
One good role model is David Beckham.
He works hard, takes care of his family, doesn’t do drugs and never, ever badmouths anyone. He has had a lot of crap thrown at him over the years and not once has he ever responded to it.
He is a decent, honest, genuinely nice man.
According to the Bureau of Justice Statistics and the FBI, crime in the U.S. is at its lowest levels since the 1960s. In fact, the murder rate of 4.7 per 100,000 residents in 2011 (latest official data) is lower than then 5.1 rate of 1960 (a year after the murder of the Clutter family).
Total Crimes lowest since 1967
Violent Crimes lowest since 1970
Property Crimes lowest since 1967
Forcible Rape lowest since 1976
Robbery lowest since 1967
Aggravated assault lowest since 1976
Auto Theft lowest since 1963
Burglary lowest since 1965
United States Crime Rates 1960-2011
http://disastercenter.com/crime/uscrime.htm
Yes, and despite the shrill screaming of the news media, crime involving firearms has been dropping steadily for 10 years or more. Their is one type of crime against persons that is increasing slightly, but I don’t remember what it was – but it wasn’t enough over all, to slow this trend down – so far.
And many sociologists believe that this general trend is mainly due to Roe v. Wade (1973), because the number of people who tend to commit violent crime, i.e. young males from broken homes, has been reduced via abortion. Children, especially boys, who are not wanted tend to get into trouble. This was also the reason why the crime rate in gold rush towns was so high; American Heritage did a story on this in 1996 (go to http://www.americanheritage.com and search for “Violence In America”).
There are other social factors at work here. JCitizen correctly noted that firearms are clearly not the only factor.
Another way to compare violence over time is to look at murders of law enforcement officers: 1990: 132, 1995: 133, 2000: 134, 2004: 139, 2005: 122, 2006: 114, 2007: 141, 2008: 109, 2009: 96 (from http://www.census.gov/compendia/statab/2012/tables/12s0330.pdf). Note that the high was recent, in 2007. This data does not fit so nicely into your assertion.
But my point still stands. The Clutter family killings were shocking because home invasions in the middle of nowhere were uncommon then, but are common now. Before that, violent crime tended to happen in cities, but now it is everywhere.
Wow, I just looked at the data you linked to. I assumed you were not misrepresenting that data.
Yes, the murder rate was 5.1 in 1960. It dropped slightly after that until 1965. Then it climbed until 1980, when the rate was 10.2, exactly double that of 1960. It slowly dropped over the following years, albeit fluctuating.
But not until 2009 did it finally drop below 5.1 Your big point that 2011’s rate of 4.7 is lower than 1960’s rate pales in comparison to the fact that only during 1961-4 and in the past three years for which data is available was the murder rate lower than that of 1960 and almost all of the intervening years.
Probably because the word “rate”, may mean per 100,000 populations. If the murder rate rises between 1950 and 1960, but the population explodes ( hence baby boomers), then the actual rate could be the same per 100,000 during the period in question – in which case the rate of murder was flat.
Just like the FBI Uniform Crime Reports warns on its start page – you have to be careful with the statistics – the thing that irritates me is the US news media says be-damned with the facts just lie through your teeth – just like folks in Germany believed that little paper hanger Paul Joseph Goebbels – tell a big enough lie, enough times and the public will believe you!
@ SaucyMugWump,
Have you actualy checked the US demographics between 1959 and now.
Just one aspect is the US population has effectivly doubled.
Other aspects sugest that crime rates are also closely linked to “anti-pinking” agents (tetraethylelead) used in petrol/gas for cars.
Crime figures are affected by many things but all crimes at one point were unknown including the original sin of murder, so at some point there will be a “first of its type crime”. Many first crimes are not realy first crimes, that is some other human advance opens up a new domain, and somebody takes a common crime type in another domain and uses it first in the new dommain. Most types of new “fraud” fall into this pattern.
Sounds like ‘stress testing’ is the new “For educational use only”!
I compiled a group of publicly available analyses of darkode.com.
1. Source: https://safeweb.norton.com/report/show?url=darkode.com
Opinion: Norton Safe Web has analyzed darkode.com for safety and security problems. (partial list) Suspicious Applications Threats found: 0, Total threats found: 0
2. Source: http://www.mywot.com/en/scorecard/darkode.com
Opinion: Unsatisfactory in Trustworthiness, Vendor reliability, Privacy and Child Safety
3. Source: http://www.siteadvisor.com/sites/darkode.com
Opinion: darkode.com
This link might be dangerous. We tested it and found security risks. Beware. ( the page contained a large red circle surrounding a white “X”)
4. Source: http://www.google.com/safebrowsing/diagnostic?site=darkode.com
Opinion: What is the current listing status for darkode.com? This site is not currently listed as suspicious. Has this site acted as an intermediary resulting in further distribution of malware? Over the past 90 days, darkode.com did not appear to function as an intermediary for the infection of any sites. Has this site hosted malware? No, this site has not hosted malicious software over the past 90 days.
Conclusion: Keep the children away from dardode.com.
A little harsh to post abscond’s jabber in public.
He did only do as he was instructed.
I think you were a little harsh on him.
He is a hacker, he ddos’d krebs site so why not publish it?
Leave the wannabe contract killer alone! He is just on his trial run killing some random homeless.
if you compare a murdered to a guy who ddos’ed a site for a few minutes you need to think again.
Lack of ethics is scalable. Once you excuse your unethical behavior because you were “just following orders,” you no longer deserve respect or trust from society in any matter.
“He did only do as he was instructed.”
Same defense the Nazis used at the Nuremberg Trials. That is an incredibly lame justification.
I find it a real troubling to find that the domain name Off-sho.re (AS34971) has it’s name servers with cloudflare
http://dns.robtex.com/off-sho.re.html#graph
It is also an interesting coincidence perhaps, that according to my stats, attacks against domains using the Cloudflare umbella have flatlined to virtually nil, in the last couple of weeks.
Speaking of CloudFlare, I still cannot figure out why, for two weeks last July, Spamhaus blocked nearly all of CloudFlare’s IP addresses. When you looked up any CloudFlare address that was blocked, Spamhaus showed this blurb on the top of reporting page: “Hosting service refuses to shut off abusers. Spam & cybercrime ‘reverse proxies’ stay up after being reported. Cybercrime world now knows of this ‘bulletproof hosting’ and is rushing here.”
Truer words have never been written. See this page for details:
http://www.cloudflare-watch.org/cfblock.html
CloudFlare somehow got those blocks lifted after two weeks. Ever since then, Spamhaus has blocked only a handful of single IP addresses at CloudFlare, instead of entire netblocks totaling 37,000 addresses.
Then in March Spamhaus hired CloudFlare for DDoS protection. Why hire CloudFlare? Why not sign up with a more reputable anti-DDoS service?
Meanwhile Matthew Prince, co-founder and CEO of CloudFlare, was hyping the story about how he mitigated the largest DDoS in history and rescued Spamhaus. He was even got his picture in the New York Times:
http://www.nytimes.com/2013/03/28/technology/attacks-on-spamhaus-used-internet-against-itself.html
Thankfully, NYT’s reporting was offset by others who reported that the whole episode was overhyped by CloudFlare.
CloudFlare is dirty. Thanks for running the CF watch site — this info needs to be publicized!
unbelievable. Its also amazing to me how these guys really believe their own lies.
They really do think they are untouchable. You know is a shame senator rockefeller is retiring. He really is against hacking…. I wish the gov’t and more importantly american corporations wake up soon and realize this is no longer just a sci fi movie. Cause these kids really feel they are untouchable.
Any chance to get their off-sho.re domain named killed? .re is Reunion, a territory which is part of France: not really a no man’s land without laws.
I don’t believe that a criminal hosting service is truly bullet proof. When all else fails , you can send complaints to the downstream peers for the AS number.
In the case of ‘Off-sho.re’ (ASN34971)
route: 37.247.48.0/21
descr: Prometeus Fist PA Block
inetnum: 37.247.48.0 – 37.247.55.255
netname: IT-PROMETEUSIPERWEB-20120418
descr: Prometeus di Daniela Agro
country: IT
————-
Peer/Transit
————–
ASN 20836
Name CDLAN-AS
Description CDLAN Autonomous System
————–
Which then leads to:
——————————————
Down Stream peer/transit ASN 20836
——————————————
ASN 3356
Name LEVEL3
Description Level 3 Communications
ASN 6762
Name SEABONE-NET
Description TELECOM ITALIA SPARKLE S.p.A.
ASN 6939
Name HURRICANE
Description Hurricane Electric, Inc.
ASN 174
Name COGENT
Description Cogent/PSI
——————————————
MAP of network ASN34971
http://as.robtex.com/as34971.html
——————————————
It appears that ‘Off-sho.re’ is no longer resolving to the A Name
off-sho.re changed the nameservers on their registration hours ago (2013-05-20) from this:
andy.ns.cloudflare.com
zara.ns.cloudflare.com
to this:
ns-canada.topdns.com
ns-uk.topdns.com
ns-usa.topdns.com
It resolves to 175.45.176.68 in North Korea on these new nameservers. There’s a 302 redirect to the InterKo/ which has a bunch of North Korean content. There’s also http://off-sho.re/InterEn/ for the same thing in English.
The CloudFlare nameserver records will probably stay up for a few days (or even weeks):
dig off-sho.re @andy.ns.cloudflare.com any
(When you check for CloudFlare nameserver information you can use any of their 100 nameservers because they are on Anycast, which means that each of the 100 returns the records for any and all of them.)
They show an A record to 37.247.55.89 in Italy, which we first recorded about ten days ago. Last October the CloudFlare records pointed to 94.102.60.14 in Netherlands.
I suspect the North Korean stuff is just for laughs.
You never know, maybe Kim Jong Un has decided to get his feet wet in the bulletproof hosting business. They have countless banks of 56K modems available to scale up your host’s connection bandwidth on demand.
Every Cloudflare DNS server address/name may respond with answers for any of the domains that they host, but *that* is not what anycast is.
Stress testing? That’s like saying a gun is a bullet proof vest tester.
If one is operating in a controlled environment, then a stress test is reasonable. However, if one is operating in the open on resources owned by the rest of the world, it’s called attempted web-icide.
This sort of sophistry should be the only justification required to isolate them from the rest of humanity. Let him stress test in his own little sandbox and leave the rest of us alone.
These issues are so complicated that it is hardly surprising that members of traditional legislatures are largely incapable of addressing cyber crime matters.
Earlier this year, I watched televised proceeding of a British parliamentary committee, members of which were gamely trying to engage in interlocution with three experts. The experts produced beautifully clear and informative responses to näively simplistic questions but the committee members were quite unable to comprehend those responses.
I despair of democracy.
And thus is the paradox – I’ll keep my Democracy though – thank you very much!
Incapable of addressing cyber crime matters? I understand what you are saying, Chris, but… members of traditional legislatures have aides, committees and sub-committees to do everything for them but vote. These aides gather the information, provide it to the member and hope the member’s vote reflects what he learned. It happens this way for most of their votes.
As SgSanford said, “Bad behavior is still bad behavior.” We know cyber crime is wrong; it says crime right in the title. How long do we have to wait for someone to do something about it?
That’s true, but the dysfunction on the Science and Technology committees in the US House and Senate is extreme. It seems like every time a legislator makes some absurdly hare-brained comment about the internet, climate, or human reproduction, they guy is a member of one of those committees. I think the creationists in congress try to stack the committees full of people who are too ignorant of science to doubt whether Genesis is literally true. And that ignorance extends to everything else.
Whoa there AlphaCentauri! I agree most of the people working in politics are idiots, and there are a lot of creationist idiots but not all the creation scientists are not true scientists, some of them just happen to be on the Creation side of theory but also open minded enough to change their mind about how nature works.
Just like every theorist, you have to fall into one or more camps during your studies, depending on what you think is the truth. Some scientist just want to fall into whatever camp gets them research money – I don’t ascribe to those. I’ve been in research, and seen perfectly good studies ruined by scientists just because they have a personality disorder. So it is all too complicated to put a thumb on.
One thing is sure – a lot of us better get interested in politics (*puke*) and get our hands dirty, or we should just shut up about the dysfunction in Washington. I don’t know if I have the stamina to be a politician, but I am sure not political enough to get along – I’m sure grid lock would be a permanent thing if I were voted in!
@ d
And all those aids etc form a very long food chain that not only needs to be fed but entertained as well.
Well funded lobby groups know this and copiously meet these needs whilst giving their view point.
It has got so bad that lawyers working for lobby groups are actually drafting the legislation and ammendments and putting them into the food chain so those in the food chain can just sit and enjoy the entertainment…
We don’t have democracy but “representational democracy” and if various statistics are to be belived those representatives are way way more criminal than the average person…
How did Krebs get DDoS’d if he’s on Prolexic?