If your strategy for remaining safe and secure online is mainly to avoid visiting dodgy Web sites, it’s time to consider a new approach. Data released today by Google serves as a welcome reminder that drive-by malware attacks are far more likely to come from hacked, legitimate Web sites than from sites set up by attackers to intentionally host and distribute malicious software.
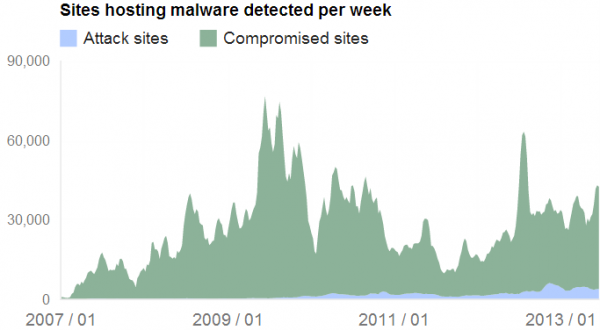
Today, Google released a truckload of data from its Safe Browsing program, which flags and warns users about more than 10,000 suspicious and malicious Web sites each day. The information clearly shows that gone are the days when folks could avoid giving their computers a nasty little rash simply by staying out of the Internet’s red-light districts (networks with large aggregations of porn and piracy sites, for example).
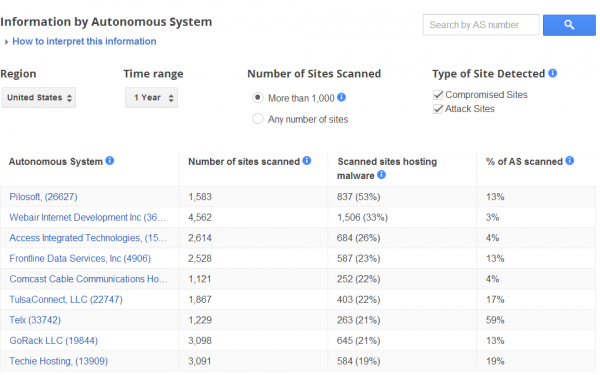
At the same time, some places on the Internet clearly are far more dangerous than others, Google’s data sets show. Have a look at the following graphic, which lists the most hostile Internet providers in the United States (the U.S. is currently responsible for just 2 percent of the world’s malicious sites, Google says).
The most malicious U.S. network listed by Google — a data center run by a company in New York called Pilosoft — is no stranger to lists charting the top sources of badness online. Pilosoft figured prominently in Operation Ghost Click, a U.S. Justice Department takedown targeting the DNS Changer botnet, which had a significant portion of its operations based at Pilosoft. Google says it has scanned 13 percent of Pilosoft’s network, and found that more than half of the sites it scanned were malicious.
Other top badness concentrations have a history of courting malware purveyors. Ask Google’s report to display the most densely malicious ISPs regardless of country and you’ll notice some interesting names float to the top of the list. Among them, Santrex Internet Services, is a well-known offshore bulletproof hosting provider based in the Seychelles.
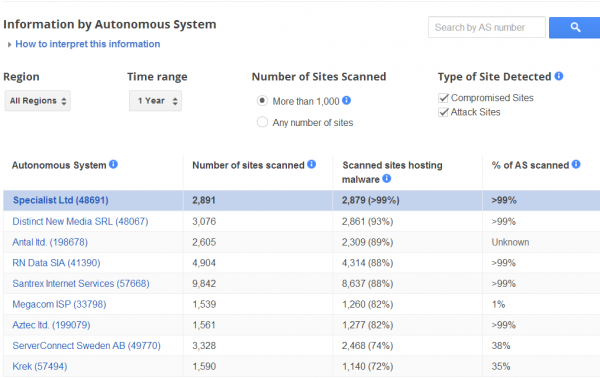
Some networks are completely overrun with malicious sites, and some actively seek out this condition.
Of course, more mainstream networks and ISPs also are constantly battling malicious sites within their borders. It’s worth noting that 22 percent of the sites hosted at one section of the network run by major ISP Comcast (AS20214) are malicious, according to Google, although the company says it has scanned only 4 percent of this portion Comcast’s network so far. Google’s data is broken down by “autonomous system” (AS) numbers — which are basically a numerical way of keeping track of networks — and a large ISP may control numerous ASes.
Several other Comcast ASes are listed in the first few pages of Google’s index of U.S.-based badness. To be fair, Comcast is the nation’s largest cable Internet provider, so it’s perhaps unsurprising that it hosts so many compromised sites. However, Comcast’s largest competitor in the United States — Verizon — doesn’t appear until page 19 of Google’s results (with 5 percent of scanned sites malicious and 5 percent of the network scanned).
More than ever, avoiding drive-by malware downloads means keeping your computer, browser and browser plugins up to date with the latest security patches. For tips on how to manage that and other ideas for safe browsing, check out my tutorial Tools for a Safer PC.
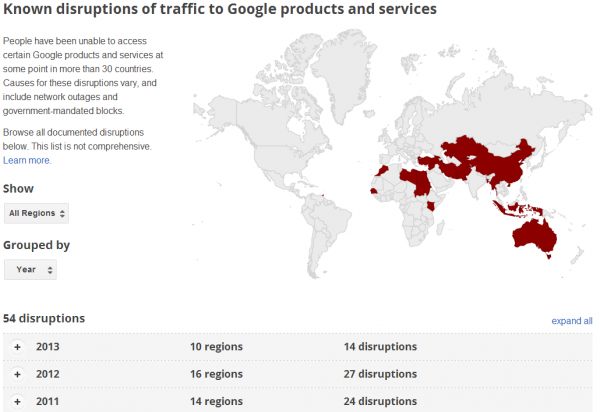
One final note: The malware data is only a subsection of a larger Transparency Report that Google has published. One very interesting section of the report (not malware-related) shows all of the places in the world where Google’s various services are currently being disrupted or censored in more than 30 different countries worldwide.




1. Use the latest version of Firefox (22.0) with two add-ons, AdBlock Plus and NoScript. The latter takes a few hours to get used to, but it’s well worth it in the long run.
2. Disable Java from running in the browser.
3. Keep Adobe Flash current, and remove any Adobe PDF software. Either use Firefox’s inline reader to view PDFs, or use a lesser-known viewer (Sumatra etc.)
Since doing these easy steps around 2 years ago, I haven’t been hit with a single confirmed malware instance… even when visiting notable porn sites. ☺
What is the effect of using noscript? What about disabling java? Novice here. Does your advice only hold true for the Firefox user?
Hi Gregry, I discuss some of the impacts of using Noscript here
http://krebsonsecurity.com/tools-for-a-safer-pc/
Also, you may consider as a more noob-friendly alternative using Click-to-Play
http://krebsonsecurity.com/2013/03/help-keep-threats-at-bay-with-click-to-play/
Gregory — the part about disabling Java holds for everyone, but AdBlock Plus/NoScript are add-ons exclusively for Firefox. NoScript prevents sites from using JavaScript without the user’s approval. As you visit frequently-used sites (Gmail, KrebsOnSec, whatever) you can whitelist these sites. After a few hours/days, you’ll have whitelisted everything you use regularly while keeping dubious domains (doubleclick.net, iesnare, google-analytics, etc) from serving their trackers/ads/malware/etc.
I tell everyone to use Firefox… IE, although it may have gotten “hardened” since version 8, seems to be a favored target of malware writers. I still keep IE around if some specific webpage has trouble loading on Firefox.
You can also get equivalent (and similarly named) addons for Google Chrome.
While of course it’s a good idea for everyone to use NoScript I still fear even this is too hard to use for some people. Often sites serve up content from many URLs so whitelisting just the URL you use to get to the site isn’t enough, people get frustrated leading to turning it off making it pointless etc. Also the notification that it uses is annoying (at least for me) 😉 It can be turned off but then some people are going to forget they’re using it and be mysitfied by sites not working.
Not sure how one could make it easier to use but if users can use it it’s well worth it.
unfortunately, although there are chrome extensions with similar names to noscript, they do not provide similar levels of security.
check this post by the creator of noscript (and pay attention to the post updates) http://hackademix.net/2009/12/10/why-chrome-has-no-noscript/
Ah, didn’t know this, thanks.
The Firefox addon “IE Tab” may solve most of your IE compatibility issues (Chrome has it, too.)
I agree with your list 4/8 or 8/16
A weakness of NoScript et al is that if you approve a site and then it becomes compromised, its scripts are free to run. And that’s Brian’s fundamental point with this article: statistically, the majority of bad sites are normally safe. So they could easily be on your whitelist.
As a point in case, when I was a sysadmin, I was using our own non-profit agency’s homepage as the default Start Page for our fleet. And one day our web-hosting provider got pwned, resulting in our own website attacking our own computers for most of the workday. Unsuccessfully, I’m happy to say.
For the record, if you wanted the approximate equivalent of NoScript with IE, you would block active scripting in the Internet Zone. Now set the Trusted Sites Zone to at least a Medium-High security setting and add your trusted sites to Trusted Sites. In addition to allowing scripting only on approved sites, now you have Protected Mode and a Low-Integrity process to mitigate the damage if/when one of your trusted sites does go rogue. I believe IE has had this capability since IE 5.01, circa 2001.
you know – that’s exactly what I have in the back of my mind while using noScript. It falls down on the job if a website you have previously whitelisted gets pwnd.
Also, the sites that have 10 -15 different addresses loading content, it’s hard to figure out which one to allow, so I end up using “temporarily allow all” quite regularly. It takes just one hacked site to mess it all up.
Even on regular sites I rarely need to enable anything, often the scripting is just for ads or some feature of the site I don’t really care about anyway – I like it better not allowing anything unless I tell it to.
Hi nov,
1. Firefox checkbox seems to be checked by default (secure by default). It has another one below to block phishing.
2. AFaIK OpenDNS block malware sites by categorization. So it relies on customers feedback and probably some internal work.
What I see more often blocked by OpenDNS are the phishing websites blocking. It is feeded by some other sources like their own PhishTank web site were users submit phishing URLs.
Or to put it another way, Forrest Gump-style, “Badness is as badness does…” probably everywhere, but in actually targeting Google seems mostly concentrated in a swath of Asia from East to SE to SW plus Oz.
Brian:
Any correlation between the Google data and the recent WordPress attacks? Do you know of anyone that could drill down through the AS to determine the hosting platforms that are being compromise most often?
thx
You may find the APWG Survey from 2012 relevant still. I summarized the survey at http://securityskeptic.typepad.com/the-security-skeptic/2012/09/apwg-web-vulnerabilities-report-act-ii.html – the report can be viewed there as well.
WordPress sites are enormously popular among illegal pharma affiliates. Type “no prescription” site: edu for your daily sample.
I used NoScript for a long time (years) and eventually got rid of it. Yes, it was great security but you were constantly getting popups and virtually every site that you went to needed to either be completely or partially whitelisted or the next visit would result in the same annoying messages.
Unless you only go to a handful of web sites again and again, NoScript will be an ongoing pain.
Even using NoScript and allowing all scripts (even globally I believe, though I never personally selected it) still does provide a benefit in the form of preventing & alerting on XSS attacks.
What this list article doesn’t state is that a large number of online phishing sites hosted on some of those very I.S.P.’s (AS#) also contain backdoor malware like Zeus or Citadel
Where do I find that google report in PDF format?
Uh, wait, let me Google that for you!
Brian
I’m a huge fan. Thanks for all the great stuff you have published.
For once I have to take issue with you. Your final graphic is prefaced by the words “Google’s services are currently being disrupted or censored by regimes…”
I was pretty surprised to see Australia lumped in with China, Afghanistan, Tajikistan and other countries not noted for free access to the Internet.
But the graphic does _not_ show current disruptions… it shows disruptions over all time. Your link to http://www.google.com/transparencyreport/traffic/#expand=TJ does correctly show current disruptions, which are very different and do not include Australia.
Digging deeper shows that Australian access to some Google services was indeed interrupted … only once for 57 minutes on 6 June 2012 as a result of a data centre outage. Hardly in keeping with the implications of the final part of your article!
As you are invariably fair and committed to accuracy, I am sure you will want to correct any misapprehension that Australians are currently blocked from accessing Google by our current “regime”. However flawed our politics may be, we do live in a free country with a representative democracy, as do you.
Brian
Your final graphic is wrong, wrong, wrong!
Why won’t you fix it?
What exactly is wrong about the graphic? It’s not *my* graphic btw.
Brian
If you follow the link you provide in your article, it does not show the graphic you have included.
I describe it as your graphic because you chose to include it. And it does not represent what you say it does.
Thanks for coming back on my second post.
Do You know & trust Steve Gibson’s “Shields Up” to be reliable?
It’s A free “check” on any open ports ON YOUR COMPUTER available at GRC.ORG
The days of worrying about ports is long in the past. Routers took care of that. Plus all this stuff comes in on port 80 with normal web traffic.
Steve Gibson has pointed out recently, alot of new routers have UPNP on the public interface!
He also has a test for that on his site as well.
But I agree the biggest problem is HTTP, its very scary nowadays.
Oh and just to add, Also at Gibson Research at GRC.com you can test the security certificates of websites to see if there is a man in the middle attack against you.
I’d actually be interested in hearing some opinions on Steve Gibson as a security researcher.
To me as a relative lay person in security and working in marketing he seems like a very successful marketer but completely idiotic about computers and security.
For example I’ve recently read a piece by him where he makes the claim that his software SpinRite works on Flash drives. The majority of stuff he writes about firewalls appears to be horse**** – oddly enough someone told me he has an affiliate relationship with Zonealarm Firewall (had? havent heard of AZ for years) – and who can forget his “THE INTERNET WILL END IN 6 MONTHS” stupidity from years ago.
I don’t know if I’m offbase here but the guy appears to be clueless but able to spin a load of garbage that sounds that sounds convincing to lay people from where I’m sitting.
@ Neej : “I’d actually be interested in hearing some opinions on Steve Gibson as a security researcher.”
That is the wrong question. Although Steve Gibson has had some “research” insights, for us he is mainly a technical commentator. For over a decade he was a columnist for InfoWorld, the old ink-on-paper subscription magazine. Since 2005 he has presented WEEKLY video / audio podcasts about current network security issues. He creates and maintains very unusual podcast transcripts on his site (grc DOT com SLASH securitynow) which thus represent a tool for finding and reading networking explanations.
Is he always right? Of course not. Nobody who opines for decades on end will be right every time. Expecting perfection is as ridiculous as someone never misspeaking or making an error on their job. He has, however, been professionally attuned to the computer and networking news of the day literally for decades.
Looking at a massive body of work to selectively find errors and blaming those on incompetence speaks to the partiality of the reviewer. Unless someone has personally worked with the nitty-gritty details and consequences of networking protocols, I doubt they will know more about it than Steve Gibson.
“To me as a relative lay person in security and working in marketing he seems like a very successful marketer but completely idiotic about computers and security.”
I would call that as wrong in both counts. If there is something you want to know about networking security, there is a good chance Steve discussed that in some show (there are 409 shows). Search it out, then read the transcript, or watch the video from Twit (twit DOT tv SLASH show SLASH security-now). A weekly show on networking security can be boring. But boring is not incompetence.
People should consider Steve Gibson’s work as a networking security resource, in addition to, and in comparison to, other such resources. They can form their own opinions about the worth of what he does.
Yes, completely was likely the wrong description by me and it’s interesting to read this. Thanks
He speaks on a wide range of topics, and is usually reporting on what alot of other sources are reporting on and explains it in laymen terms for us who aren’t as tech saavy. I think thats great and don’t know of any show like it. He doesn’t brag about being an expert at anything and is not your usual arrogant rude computer nerd. I don’t know why you have a problem with his show. His show is how I heard about BK’s blog for example.
I don’t think hes full of horse**** when he says 100s of thousands of routers and devices in the world have upnp on the public interface nowadays. Or that hackers are more commonly are intercepting your webpages with fake ones. He has generously lets use his servers for tests for these things on his website.
Of course if your a target, not a security expert, and the hacker is persistent enough, most measures are probably useless. Tthis particular blog post, and the exploits out there confirm that more and more. Which is making it harder for people to blame users. But why make it easy? Why not run some tests for fun?
Amen brother! He’s one of the good guys!
Is he still really hyping spinrite? It’s abandonware that hardly ever even functions anymore. It’s going a decade since he has done anything with spinrite.
Hes updating spinrite 6 and working on spinrite 7 now.
So it will work with Mac computers and won’t depend on bios anymore.
Google suffer this “Why do you look at the speck that is in your brother’s eye, but do not notice the log that is in your own eye?” Luke 6:41 says.
They allows malware hosting in Google Drive which are used by criminal in malware spam attacks containing links to malware hosted at Google Drive.
They ignored reports specifically on this abuse. What a pitty!
Anyone have an opinion on Malwarebytes Anti-Exploit
as a useful tool ?
Mr Long, I use it and consider it an excellent scanner…
I think users should be wary of using both Anti-Exploit and EMET, given that they appear to do the same thing.
The Malwarebytes Anti-Exploit forum is at http://forums.malwarebytes.org/index.php?showforum=126.
They also have great free support full of experts to help you if you think you are infected.
I have used Firefox in the past but prefer Chrome now because it is faster. You can download NoScripts, Ghostery, Ad Block and Do Not Track Me. They are all extensions for Chrome and secure your browsing quite well. Uninstall Java and replace adobe PDF reader with Foxit Reader and you are good to go.
Strange that I never see mention of Sandboxie. It’s not the easiest thing to set up, but get hit with malware, you just delete the sandbox and it’s gone. I’ve found it very useful.
Sandboxie is mentioned in the Tools for a Safer PC Primer that I linked to at the bottom of the story.
I use AdMuncher andFlash Cookies Cleaner,and Ad Muncher even keeps ads out of my Outlook e-mail account.
A must read to accompany this article
Download me—Saying “yes” to the Web’s most dangerous search terms
http://arstechnica.com/information-technology/2013/06/download-me-saying-yes-to-the-webs-most-dangerous-search-terms/
“free e-cards,” listed in the McAfee Top 50, US
“free game cheats,” “game cheats” qualifies as a McAfee Top 50
“free games,” noted as popular generic search query
“free lyrics,” “lyrics,” and “song lyrics” were among the McAfee Top 50
“free music downloads,” the No. 1 term for Average Risk, McAfee Top 50
“free screensaver,” noted as a popular generic search query
“free wallpaper,” “wallpaper” is a McAfee Top 50
“free word unscrambler,” the No. 1 term for Maximum Risk, McAfee Top 50
I think studies like these are great for showing that it’s not always “stupid users” clicking on links that they shouldn’t be. In my experience the security teams are very quick to blame the users when really, what can we expect?
Related to the “it’s not always the stupid users” I’ve been browsing on my ipad while I’ve been home sick and, especially for those of us whose eyesight is beginning to suffer from the ravages of time, it’s very easy to accidently click on a link for (say) an advertisement due to the size of the screen and the way in which ads are being placed around about where you expect a navigation control. This must be even worse on iPhones and as far as I can see there is no way on these devices to block active content. As an aside here, I was looking for firefox for this environment only to discover that there is no such beast due to Apple’s policies, but that there are a number of apps that try to look superficially like firefox
On my proper machines I use Opera with Plugins and Javascript off by default, but Opera allows site by site setting of these options and I whitelist a number of sites (a calculated risk). I have no idea if this also allows third party active content on those pages. And even if it doesn’t it wouldn’t stop infected host site scripts running. I’m not sure what the answer here is but I think I’ll start using Sandboxie or something similar, although I’m sure someone is working out how to attack the sandboxes as well.
A most excellent thread and comments…Thank you all…
Great post but Mr Krebs can you show the first picture with the graph correctly as it distorts the graph and creates a slightly inaccurate image in reader’s minds.
Oops my bad.
How is it that an ISP that is 50% malicious is still allowed to operate in the US? Are we going to pretend that some law based on “ignorance of customer activity” should protect them?
I don’t know about legal limitations in US. But others US based services like SkyDrive, Google Drive, and Dropbox allow criminals to store malware files.
Then the criminals send Malicious Spam including links to that legitimate onlinestorage services containing the malware file.
I don not understand this Google behavior, why Google mail does not allow to attach en EXE file, but Google Drive allows storing malware EXE files and allow link to them which are subject of abuse?
Who is going to shut them down? You have ‘Justice’ Scalia up there yesterday making an argument about why discrimination should be legal for Pete’s sake….
Corporations own our country and if they pay the right folks they get away with a lot more than we think they could.
“malware attacks … from hacked, legitimate Web sites”.
Upon-realization-that-a-legit-site-is-serving-malware solutions, which I haven’t seen a comment on:
1. Firefox has a checkbox for “Block reported attack site” (I’m not sure if it is default ON or not). I see it blocks one recent malware site (upon testing).
2. At least one router model I know of blocks website malware attacks (sort of like OpenDNS, but the router has the feature to perform safety checks). From what I’ve seen it blocks upon realization when even a legit page contains malware. Cisco calls the feature “‘Safe Surfing”. From my testing it seemed to catch all new malware sites very quick. (Personally, I didn’t find OpenDNS to block malware sites well enough in my testing more than a year ago).
“malware attacks … from hacked, legitimate Web sites”.
Upon-realization-that-a-legit-site-is-serving-malware solutions, which I haven’t seen a comment on:
1. Firefox has a checkbox for “Block reported attack site” (I’m not sure if it is default ON or not). I see it blocks one recent malware site (upon testing).
2. At least one router model I know of blocks website malware attacks (sort of like OpenDNS, but the router has the feature to perform safety checks). From what I’ve seen it blocks upon realization when even a legit page contains malware. Cisco calls the feature “‘Safe Surfing”. From my testing it seemed to catch all new malware sites very quick. (Personally, I didn’t find OpenDNS to block malware sites well enough in my testing more than a year ago).
Also, it’s not necessarily about blocking hacked, legitimate Web sites. From all my checking, the hacked, legitimate Web sites are not the malware servers but re-directing to non-legitate sites for the malware serving. Those upon-realization-that-a-non-legitimate-site-is-serving-malware sites are blocked in my testing by ‘Web-of-Trust’ (WOT).
Hi nov,
Firefox setting for blocking reported attacks and phishing are ON by default ASaIK.
OpenDNS in my experience block few malware sites, it is based on website categorization. So I think that legit abused websites are not categorized as malware sites, usssually.
OpenDNS block very often phishing websites, I think because they have the Phistank website to colect lot of users reports on phishing URLS.
It’s not necessarily entirely about blocking hacked, legitimate Web sites. From all my checking, the hacked, legitimate Web sites are not the malware servers but re-directing to non-legitate sites for the malware serving. Those upon-realization-that-a-non-legitimate-site-is-serving-malware sites are blocked in my testing by ‘Web-of-Trust’ (WOT).
Yes, it’s true that most hacked sites are merely attempting to redirect visitors to other compromised sites, but that is a distinction without a difference to most people.
My experience on checking Malicious Spam attack shows me that legitimate websites are abused to redirect to another legitimate websites, hosting the malware files. I have been doing this checks since more than two years down here in south america in a private company. The abused legitimate websites are from all around the world but are mainly european. The attackers seem to play with the time zone, so when the attack starts, the abused legitimate website are in a time zone where people already finished their workday. That way the warning arrives too late to website administrator, on their next workday. Websites hosting the redirection or the malware usually are small shops, professionals or organizations, and abandoned websites also.