If you use Gmail and have ever wondered how much your account might be worth to cyber thieves, have a look at Cloudsweeper, a new service launching this week that tries to price the value of your Gmail address based on the number of retail accounts you have tied to it and the current resale value of those accounts in the underground.
The brainchild of researchers at the University of Illinois at Chicago, Cloudsweeper’s account theft audit tool scans your inbox and presents a breakdown of how many accounts connected to that address an attacker could seize if he gained access to your Gmail. Cloudsweeper then tries to put an aggregate price tag on your inbox, a figure that’s computed by totaling the resale value of other account credentials that crooks can steal if they hijack your email.
In a blog post earlier this month titled The Value of a Hacked Email Account, I noted that many people do not realize how much they have invested in their email account until that account is in the hands of cyber crooks. That post quoted prices from one seller in the cybercrime underground who buys compromised accounts, such as hacked iTunes accounts for $8, or credentials to Groupon.com for $5, for example.
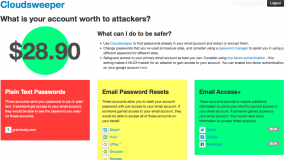
Chris Kanich, assistant professor at UIC’s computer science department and principal organizer of the project, said Cloudsweeper’s pricing model is built on prices collected from multiple sellers across multiple underground forums and services. I ran one of my Gmail accounts through Cloudsweeper, and it determined my account would be worth approximately $28.90 to bad guys. While this is not a Gmail account I use every day, I was surprised at how many third party services I had signed up for using it over the years. According to Cloudsweeper, bad guys with access to my account could also hijack my accounts at Amazon, Apple, Groupon, Hulu, Newegg, Paypal, Skype, UPlay and Yahoo, to name a few.
Cloudsweeper uses the Open Authentication (OAuth2) protocol to connect to your Gmail account and search through messages. OAuth is an open standard for online authorization, and using it with Cloudsweeper does not require you to type in your password as long as you are already logged into the Gmail account that you’d like scanned. Cloudsweeper doesn’t keep your credentials, and it forgets about your visit and inbox after you log out of the service, or within 60 minutes of inactivity.
PLAIN TEXT OFFENDERS
Prior to performing a scan, the service asks users if they wish to participate in a study, which Kanich said gathers and securely stores non-personally identifiable information about Cloudsweeper users who opt-in. That data includes how many types of accounts each user has tied to their Gmail. The study also draws on data from the second core feature of Cloudsweeper: The ability to discover and then redact or encrypt passwords that various services may send to users in plain text.
UIC’s Kanich said the project would like to maintain anonymized statistical information — such as how many accounts and what type — about visitors’ use of the tool.
“So with the user’s expressed permission only, we’ll store stuff like, ‘there was a password that was duplicated in seven different emails and the user chose to redact them all,'” Kanich said. “It’s a little bit funny because you don’t have to give us your password for Cloudsweeper to work, but a big reason you’re coming to us is so we can find your other account credentials.”
Click the blue “Cleartext Password Audit” button from the Cloudsweeper homepage and the service will scour your inbox for passwords that various third-party services may have sent to you in plain text. Cloudsweeper then lists the plaintext passwords alongside the names of the sites that sent them to you, and offers the options to encrypt or redact some or all of the passwords (or to do nothing, of course).
This process works by loading your messages via the Internet Message Access Protocol (IMAP), which lets users edit messages in their inboxes. Using IMAP, Cloudsweeper can redact or encrypt just the plaintext password in any email, leaving the rest of the message intact and untouched. Depending on how many messages you have in your inbox, this process may take quite some time.
Upon encrypting the password(s), the service presents a QR code that you can take a picture of with your mobile phone. You can also copy a longish decryption key and keep it somewhere safe. If you ever wish to un-encrypt the now obfuscated passwords, simply revisit Cloudsweeper and click the orange “Decrypt Messages” button from the homepage. Type or paste in your decryption key, or hold the QR code up to your computer’s Webcam and Cloudsweeper’s site will unscramble your encrypted passwords.
The password redaction/encryption feature is nifty, but it might be more trouble than it’s worth. After all, crooks who gain access to your Gmail account can simply request a new password from the site that sent it in the first place.
“That’s the biggest argument against this: That if you have access to the email account, you can just reset the password anyway,” Kanich said. “Right now, redacting the password is the closest thing to simply deleting the messages [containing plaintext passwords]. A lot of people do want to keep all of their email and don’t want to delete a lot of messages, even those that may have their passwords in them.”
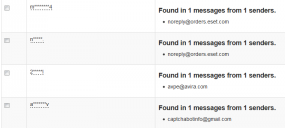
Interestingly, as evidenced by the screenshot above, many of the passwords this tool detected as having been sent to my Gmail inbox in plain text came from antivirus vendors. Storing passwords in plaintext is a security no-no, and these firms should know better. I’ve encouraged readers to name-and-shame companies that perpetuate this practice by forwarding such emails to plaintextoffenders.com, which redacts and publishes these missives each day. Passwordfail.com maintains another list of plaintext offenders, and even has a browser extension to warn users before they register at a site that stores passwords in the clear.
As I noted in several recent posts, Gmail and other Webmail providers — Yahoo! and Hotmail/Live.com — all offer multi-step authentication; if you haven’t already protected your accounts with these features, please take a moment to click the relevant links in this sentence to learn more about how to do that (UIC’s Kanich said his group is looking at adding Yahoo to Cloudsweeper, but that Live.com doesn’t work with IMAP). See this post for a primer on picking and managing strong passwords.
Did you use Cloudsweeper to price your Gmail account? If so, leave a comment below and tell us about your experience.




Hey Brian, I have $20 CASH in my pocket – will you settle for that for your account?
:oP
Isn’t the other side of the problem that most web accounts can be compromised by knowing the answers to simple challenge questions for password resets?
Would love to see this tool try to attack that part of the problem too.
I’m curious what anyone thinks about how Google text’s activation codes to cell phones to open an account.
Is that not a good security measure?
Wouldn’t it be good to do the same thing for any changes to an account?
$28.00 = $8/Apple + $15/Amazon + $5/Facebook
(But I don’t have a Facebook account.)
I did use this as a prompt to clean up this rarely used email from all the companies it was scraping — I’m pretty good about this stuff and I did have a lot of old and potentially exploitable email — lots of discovered passwords (all now redacted or changed)
The new value after this exercise: $0.00, and no passwords.
$0.30
In other words, it costs more to go through the effort of hacking my email account than it is worth!
Mine is worth a bit of time in jail and about _
– $5k fine .
apparently worth $15 for amazon, although with some of the other accounts, you also need my mobile phone to enter the 2nd step verficiation
facebook is $5, but then it also needs the phone and twatter is all of $0.30
got an account with godaddy that is used to only report the scammers who email me special offers and that is worth not a lot
My personal gmail account is worth $0. I use a non-gmail account for my business mail, though, and it might be worth more. I don’t store any messages that include plain-text passwords, however.
$8.40 – but it’s the potential for access and pword reset for Paypal and others which I find unsettling. I don’t have much, but what little I have is important to me. Not sure how much it helps but I use two-factor for gmail and Lastpass for most of my passwords.
And your just going to give a 3rd party access to your gmail account to calculate a price, dude honestly??
I was seriously wondering when someone was giong to mention that…
Agree…I just cant affort to lost control to my mail account…priceless to me!
Well, Google is sending data to NSA anyway, so it doesn’t matter too much. 😉
Congratulation guys!
You’ve just given your private data to unknown and untrust people.
However, after PRISM has perlustrated your accounts this is not a big deal at all.
It did not work. I tried the app five times and each time I got this error after accepting it: There was an error authenticating with Gmail. If you’re interested in connecting, please try again.
@X
First of all, thank you for “perlustrate” – what a delightful word.
As to unknown and untrust[ed] – yup, you’re right. I’ve never met the two guys doing this project. I’ve never been to the University of Chicago.
The links provided lead to the appropriate pages; the FAQ gives some good info, and there’s also a link to the various studies ongoing at U of C.
So there are two kickers, no, three:
I must trust that they tell the truth that they’re only using non-personally-identifying info.
I must trust that the pages are indeed from these guys and the U of C.
Finally, I must trust that the SSL certs are valid and the connection is not intercepted and decrypted. Lately that’s becoming a real concern.
Now I think of it, I must also trust that Chris and Peter aren’t secretly taking copies of info from my emails to later use for nefarious purposes.
That’s a lot of trust to give out, and in that you are perfectly correct, and all just to participate in some study that might lead to some useful data and maybe help a couple of guys on their masters or Ph.D.
In real life most of us online do that all the time – with our banks, with e-tailers, with the people who provide our operating systems, applications, drivers, security utilities, etc.
It comes down to a judgement call. I added one more, used the tool, then went into gmail tools and revoked access.
Others may of course do as they will, making their own judgements and extending their own trust as they go.
the value of my account for hackers might be of interest to me. the value for me is slightly different.
yet, giving an app access to “read and manage” my e-mail is priceless, to say so 🙂