An identity theft service that sells Social Security numbers, birth records, credit and background reports on millions of Americans has infiltrated computers at some of America’s largest consumer and business data aggregators, according to a seven-month investigation by KrebsOnSecurity.
 The Web site ssndob[dot]ms (hereafter referred to simply as SSNDOB) has for the past two years marketed itself on underground cybercrime forums as a reliable and affordable service that customers can use to look up SSNs, birthdays and other personal data on any U.S. resident. Prices range from 50 cents to $2.50 per record, and from $5 to $15 for credit and background checks. Customers pay for their subscriptions using largely unregulated and anonymous virtual currencies, such as Bitcoin and WebMoney.
The Web site ssndob[dot]ms (hereafter referred to simply as SSNDOB) has for the past two years marketed itself on underground cybercrime forums as a reliable and affordable service that customers can use to look up SSNs, birthdays and other personal data on any U.S. resident. Prices range from 50 cents to $2.50 per record, and from $5 to $15 for credit and background checks. Customers pay for their subscriptions using largely unregulated and anonymous virtual currencies, such as Bitcoin and WebMoney.
Until very recently, the source of the data sold by SSNDOB has remained a mystery. That mystery began to unravel in March 2013, when teenage hackers allegedly associated with the hacktivist group UGNazi showed just how deeply the service’s access went. The young hackers used SSNDOB to collect data for exposed.su, a Web site that listed the SSNs, birthdays, phone numbers, current and previous addresses for dozens of top celebrities — such as performers Beyonce, Kanye West and Jay Z — as well as prominent public figures, including First Lady Michelle Obama, CIA Director John Brennan, and then-FBI Director Robert Mueller.
Earlier this summer, SSNDOB was compromised by multiple attackers, its own database plundered. A copy of the SSNDOB database was exhaustively reviewed by KrebsOnSecurity.com. The database shows that the site’s 1,300 customers have spent hundreds of thousands of dollars looking up SSNs, birthdays, drivers license records, and obtaining unauthorized credit and background reports on more than four million Americans.
Frustratingly, the SSNDOB database did not list the sources of that stolen information; it merely indicated that the data was being drawn from a number of different places designated only as “DB1,” “DB2,” and so on.
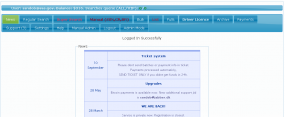
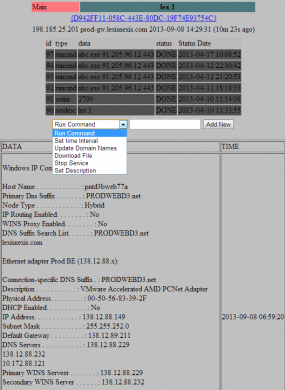
But late last month, an analysis of the networks, network activity and credentials used by SSNDOB administrators indicate that these individuals also were responsible for operating a small but very potent botnet — a collection of hacked computers that are controlled remotely by attackers. This botnet appears to have been in direct communications with internal systems at several large data brokers in the United States. The botnet’s Web-based interface (portions of which are shown below) indicated that the miscreants behind this ID theft service controlled at least five infected systems at different U.S.-based consumer and business data aggregators.
DATA-BROKER BOTNETTwo of the hacked servers were inside the networks of Atlanta, Ga.-based LexisNexis Inc., a company that according to Wikipedia maintains the world’s largest electronic database for legal and public-records related information. Contacted about the findings, LexisNexis confirmed that the two systems listed in the botnet interface were public-facing LexisNexis Web servers that had been compromised.
The botnet’s online dashboard for the LexisNexis systems shows that a tiny unauthorized program called “nbc.exe” was placed on the servers as far back as April 10, 2013, suggesting the intruders have had access to the company’s internal networks for at least the past five months. The program was designed to open an encrypted channel of communications from within LexisNexis’s internal systems to the botnet controller on the public Internet.
Two other compromised systems were located inside the networks of Dun & Bradstreet, a Short Hills, New Jersey data aggregator that licenses information on businesses and corporations for use in credit decisions, business-to-business marketing and supply chain management. According to the date on the files listed in the botnet administration panel, those machines were compromised at least as far back as March 27, 2013.
The fifth server compromised as part of this botnet was located at Internet addresses assigned to Kroll Background America, Inc., a company that provides employment background, drug and health screening. Kroll Background America is now part of HireRight, a background-checking firm managed by the Falls Church, Va.-based holding company Altegrity, which owns both the Kroll and HireRight properties. Files left behind by intruders into the company’s internal network suggest the HireRight breach extends back to at least June 2013.
An initial analysis of the malicious bot program installed on the hacked servers reveals that it was carefully engineered to avoid detection by antivirus tools. A review of the bot malware in early September using Virustotal.com — which scrutinizes submitted files for signs of malicious behavior by scanning them with antivirus software from nearly four dozen security firms simultaneously — gave it a clean bill of health: none of the 46 top anti-malware tools on the market today detected it as malicious (as of publication, the malware is currently detected by 6 out of 46 anti-malware tools at Virustotal).
ASSESSING THE DAMAGE
All three victim companies said they are working with federal authorities and third-party forensics firms in the early stages of determining how far the breaches extend, and whether indeed any sensitive information was accessed and exfiltrated from their networks.
For its part, LexisNexis confirmed that the compromises appear to have begun in April of this year, but said it found “no evidence that customer or consumer data were reached or retrieved,” via the hacked systems. The company indicated that it was still in the process of investigating whether other systems on its network may have been compromised by the intrusion.
“Immediately upon becoming aware of this matter, we contacted the FBI and initiated a comprehensive investigation working with a leading third party forensic investigation firm,” said Aurobindo Sundaram, vice president of information assurance and data protection at Reed Elsevier, the parent company of LexisNexis. “In that investigation, we have identified an intrusion targeting our data but to date have found no evidence that customer or consumer data were reached or retrieved. Because this matter is actively being investigated by law enforcement, I can’t provide further information at this time.”
Dun & Bradstreet and Altegrity were less forthcoming about what they’d found so far. Elliot Glazer, chief technology officer at Dun & Bradstreet, said the information provided about the botnet’s interaction with the company’s internal systems had been “very helpful.”
“We are aggressively investigating the matter, take it very seriously and are in touch with the appropriate authorities,” Glazer said. “Data security is a company priority, and I can assure you that we are devoting all resources necessary to ensure that security.”
Altegrity declined to confirm or deny the apparent compromises, but through spokesman Ray Howell offered the following statement: “We consider the protection and safeguarding of our various systems of the utmost importance. We have dedicated significant information security resources to managing security and protecting the data and privacy of our customers. We have a range of incident response specialists and teams from both inside and outside the company investigating your allegations vigorously.”
Referring to the SSNDOB compromises, FBI Spokesperson Lindsay Godwin confirmed that the FBI is “aware of and investigating this case,” but declined to comment further except to say that the investigation is ongoing.
KNOWLEDGE IS POWER
The intrusions raise major questions about how these compromises may have aided identity thieves. The prevailing wisdom suggests that the attackers were going after these firms for the massive amounts of consumer and business data that they hold. While those data stores are certainly substantial, fraud experts say the really valuable stuff is in the data that these firms hold about consumer and business habits and practices.
Avivah Litan, a fraud analyst with Gartner Inc., said most credit-granting organizations assess the likelihood that a given application for credit is valid or fraudulent largely based on how accurately an applicant answers a set of questions about their financial and consumer history.
These questions, known in industry parlance as “knowledge-based authentication” or KBA for short, have become the gold standard of authentication among nearly all credit-granting institutions, from loan providers to credit card companies, Litan said. She estimates that the KBA market is worth at least $2 billion a year.
“Let’s say you’re trying to move money via online bank transfer, or apply for a new line of credit,” Litan proposed. “There are about 100 questions and answers that companies like LexisNexis store on all of us, such as, ‘What was your previous address?’ or ‘Which company services your mortgage?’ They also have a bunch of bogus questions that they can serve up to see if you really are who you say you are.”
According to Litan, Dun and Bradstreet does roughly the same thing, except for businesses.
“Dun & Bradstreet doesn’t do KBA per se, but if you’re filling out a business loan and you want to pose as that business, having access to a company like that can help,” Litan said. “Dun & Bradstreet is like the credit bureau for businesses.”
Overall, Litan says, credit applicants fail to answer one or more of the KBA questions correctly about 10-15 percent of the time. Ironically, however, those that get the questions wrong are more often legitimate credit applicants — not the identity thieves.
“These days, the people who fail these questions are mainly those who don’t remember the answers,” Litan said. “But the criminals seem to be having no problems.”
Litan related a story she heard from one fellow fraud analyst who had an opportunity to listen in on the KBA questions that a mortgage lender was asking of a credit applicant who was later determined to have been a fraudster.
“The woman on the phone was asking the applicant, ‘Hey, what is the amount of your last mortgage payment?’, and you could hear the guy on the other line saying hold on a minute….and you could hear him clicking through page after page for the right questions,” Litan said.
The Gartner fraud analyst said she has long suspected that the major KBA providers have been compromised, and has been saying so for years.
“We could well be witnessing the death of knowledge-based authentication, and it’s as it should be,” Litan said. “The problem is that right now there are no good alternatives that are as easy to implement. There isn’t a good software-based alternative. Everybody in the industry knows that KBA is nearing its end of usefulness, but it’s not like you can instantly roll out biometric identifiers to the entire US population. We’re just not there yet. It’s years away. If ever.”
CUSTOMER SERVICE
A closer examination of the database for the identity theft service shows it has served more than 1.02 million unique SSNs to customers and nearly 3.1 million date of birth records since its inception in early 2012.Thousands of background reports also have been ordered through SSNDOB. Records at the ID theft service indicate that the service was still able to order background reports via LexisNexis more than 10 days after the data aggregator disabled the infected Web servers listed in the botnet’s control panel, suggesting that the intruders still had a store of accounts that could be used to pull information from the company’s databanks.
In a written statement provided to KrebsOnSecurity, LexisNexis officials said that report was generated from a law student ID that was being misused.
“Unrelated to the intrusion you have asked about, you provided to us a LexisNexis report. We determined that that report was generated from a law student ID that was being misused. That ID accesses only unregulated public records information and was identified by our fraud detection tools and shut down by us before you brought it to our attention.”
The registration records for SSNDOB show that most users registered with the ID theft service using Internet addresses in the United States, the Russian Federation, and the United Kingdom, although it is likely that a large portion of these users were using hacked PCs or other proxy systems to mask their true location.
SSNDOB also appears to have licensed its system for use by at least a dozen high-volume users. There is some evidence which indicates that these users are operating third-party identity theft services. A review of the leaked site records show that several bulk buyers were given application programming interfaces (APIs) — customized communications channels that allow disparate systems to exchange data — that could permit third-party or competing online ID theft sites to conduct lookups directly and transparently through the SSNDOB Web site.
Indeed, the records from SSNDOB show that the re-sellers of its service reliably brought in more money than manual look-ups conducted by all of the site’s 1,300 individual customers combined.
I would like to thank Alex Holden of Hold Security LLC for his assistance in making sense of much of this data.
Stay tuned for Part II and Part III of this rapidly unfolding story. Update: See Part II of this series: Data Broker Hackers Also Compromised NW3C.
Update, 2:05 p.m. ET: SSNDOB appears to be down. Also, one likely reseller of the ID theft service’s data — a fraud site called bstab[dot]su, has been having trouble all morning looking up SSN data. Lookups at that service are sending paying customers into an endless loop today. See image below.



![The botnet interface used by the miscreants who own and operate ssndob[dot]ms](https://krebsonsecurity.com/wp-content/uploads/2013/09/SSNdobBotC2-600x118.png)
![Breakdown of ssn[dot]dob users by IP address](https://krebsonsecurity.com/wp-content/uploads/2013/09/ssndobusers-285x171.png)

Umm…..wow!
Frightening, interesting. However–“pubic internet”? Lol. I know–spelling is so mundane! Could you use a good proofreader? You don’t have to publish this. I certainly don’t want to pubically–uh–publically humiliate you. Sorry–I just could not resist. It gave me a good laugh during an otherwise frightening read. Have a blessed day, Brian, & keep up the good work.
You are a tool. You do realize that something as mundane as that is quite easy to overlook, right? Spell-check won’t get it because ‘pubic’ is a word, and grammar checks won’t catch it because from a grammatical analytic standpoint it is correct. For example: In the pubic area. In the public area. Both are grammatically correct, albeit the context is wrong for this article. I am sure you are also aware that when proofreading, your eyes can play tricks on you and you really think you are seeing things that are not there. I am sure you have see the ‘tests’ where you read through something, then at the end it says, “I bet you read ‘blah’. Go back and look at the line.” When you go back and look, what you thought was blah was really something else. So, you’re an idiot.
and are you a proof reader by profession ?
its a skilled job and a good reader does not only check once, i know readers whobwould re-do pages 5-6 times.
thats why i used to be a well paid, respected job, but no longer.
You used to be a job? o.0
Ordinarily I wouldn’t bring this up but your comment was about how you used to be a proofreader :p
I believe ted leaf meant to type “thats why it used to be a well paid…”
Goodness. Such name-calling in response to a lighthearted observation. Tsk tsk.
@Whatat Oolsack
Whoa, calm down!
Jackie:
You misspelled “publicly”. No worries, though. It happens to everyone.
Definitely frightening. “These days, the people who fail these questions are mainly those who don’t remember the answers,” Litan said. “But the criminals seem to be having no problems.” man…. and then she goes on to say that nothing better will be rolling out anytime soon even though the whole industry knows its pretty much useless now? Jeez….
You never cease to amaze me about knowledge of miscreant activity. I am thankful for your site because it is a valuable tool in education for fraud prevention!
“For its part, LexisNexis confirmed that the compromises appear to have begun in April of this year, but said it found “no evidence that customer or consumer data were reached or retrieved,” via the hacked systems.”
The standard disclaimer these companies always issue – and it’s almost always not true. If these guys have been sitting in your system for months, they GOT SOMETHING! They don’t sit on one PC for months without pivoting…
BTW, Lexis/Nexis was compromised earlier IIRC. Ah, here…
Arrests Made in ’05 LexisNexis Data Breach
http://www.washingtonpost.com/wp-dyn/content/article/2006/06/30/AR2006063001222.html
Quote
Federal authorities last week arrested five men in connection with a 2005 database breach at LexisNexis Group that the database giant said led to the theft of personal records on more than 310,000 individuals.
End Quote
Guess Lexis/Nexis needs a “security assessment review”…preferably by someone who knows that “there is no security”… 🙂
Oh, and then there was this in 2009…
LexisNexis admits to another major data breach
http://www.scmagazine.com/lexisnexis-admits-to-another-major-data-breach/article/136140/
Quote
About 32,000 people are being notified that their personal information may have been compromised after a breach at consumer data provider LexisNexis resulted in identity theft and credit fraud, the company has disclosed.
According to the breach notification letter LexisNexis began sending on Friday, the thieves operated businesses that were former customers of data aggregator and credentialing service ChoicePoint, which was acquired last year by LexisNexis parent Reed Elsevier.
Using personal information of U.S. residents obtained from LexisNexis and fraudulent mail boxes in the United States, criminals applied for and obtained bogus credit cards. The scheme is linked to a Nigerian scam artist, according to CBS News, which first reported the breach.
The U.S. Postal Inspection Service (USPIS), in a statement issued Monday, said it was investigating the data breach. It would not reveal details, but said a total of 40,000 notification letters were being sent, and 300 actual identity theft victims already have been notified.
Criminals may have had access to individuals’ personal information, including names, birth dates, and Social Security numbers between June 14, 2004 and Oct. 10, 2007, according to LexisNexis. So not to compromise the integrity of the investigation, LexisNexis was instructed by USPIS to delay notifying individuals whose information was compromised.
End Quote
Indeed! Naturally, these companies are such a huge target, of course the fraudsters are going to go after them many different ways.
“Data security is a company priority, and I can assure you that we are devoting all resources necessary to ensure that security”
This is so funny, they devoting all necessary resources after get cracked…
crocodile tears
Thank God Brian Krebs wears a WHITE hat!!!
Shall I add “freeze credit” to “to do” list today? Thank you Brian.
Might be best — if you’ve been the victim of identity fraud recently — to apply to the credit bureaus for a 7-year fraud alert. You’ll need to present a police report, but it’s better than freezing your credit, and it’s free.
Sorry, exactly how is a fraud alert better than a credit freeze? A fraud alert tells you something is amiss after the fact. A credit freeze prevents the problem in the first place.
Sorry, poor choice of words on my part. It’s not “better” than a freeze, it’s just a lot less hassle for ID theft victims. Freezing your credit for any considerable length of time can create problems for consumers down the road, whether it be in trying to land a new job or get credit.
The point is, consumers should examine all of their options and the potential ramifications — including a freeze and an extended fraud alert — before making any decisions.
For my part, I have chosen to pay for a company that manages my identity and alerts me if they see any hard pulls on my credit file. I prefer this to outright freezing my credit file, but your mileage may vary.
Interesting. I have resisted the identity-management route because I have always thought I could keep myself safe by being super careful or just plain “not stupid”. But your using one is making me reconsider, especially after a rash of replaced credit cards in the last 6 months. I know it’s different, but just the level of sophistication these thieves seem to be rising to has made me wonder if I shouldn’t just cave in and do it.
Thanks many times over for your excellent information, Brian. Blessings on you, your family, and the business.
Remember that Brian, because of the work he does, is a superconducting magnet for the online lowlifes.
Your mileage will vary, but should generally be much better.
I’ve been wondering if this is a good idea for some family members. Do you recommend any companies?
Fair point. I froze my credit reports a number of years ago, and have never regretted it. I’ve had to unfreeze them a couple times when I was doing something significant, but the inconvenience was far outweighed by the peace of mind. And no annual fees to boot! But I’m also the kind of person who never signs up for department store credit cards and the like, so I can imagine that for some people it might be a less attractive option.
If you don’t want to share the specific company you deal with for identity management, can you share what characteristics you looked for before selecting a company?
I’m sure Brian’s company is probably better; but, I use Abine.com
Abine.com checkout page (name,address,credit card number) is http:// not https://. I would not trust that website with my info.
Oddly Abine.com the https:// works in Firefox private mode ,but in Google Chrome i only get http://.
fyi SafeShepherd.com provides some better security and service
I have no insight, but suspect unless consumer and business data aggregators have the data reports separated by the different access levels–from data reports with fraud alerts, frozen credit reports, or managed/notifier services–that data may still be in the same system and vulnerable to stealing. Even if the reports are not in one system withing the aggregator, that’s not to say the ‘network’ where the data resides isn’t accessible to be stolen. I suspect all the ‘protected’ data could be stolen (most data is stored in systems that are interconnected with other systems and network accessible).
“Everybody in the industry knows that KBA is nearing its end of usefulness, but it’s not like you can instantly roll out biometric identifiers to the entire US population. ”
The simple answer to this is to use Notaries (http://en.wikipedia.org/wiki/Notary) for any credit granting over $300. Sure face to face transactions can be scammed, but it is much much harder.
Good investigative work. I look forward to reading the rest. Keep up the outstanding work! Hmmm, I wonder if this means you’re going to get another drug shipment.
I dealt with a state agency “knowledge-based authentication” a week ago, and it was kind of scary on how much they knew about me with regards to the correct answers verses the bogus stuff.
By the way this is a real good article
This LexisNexis is so big that they do not have to play by the rules. I have reported them to BBB etc. to no avail. They mis-reported that I was in an accident (which is not true) which caused my rates to increase for my automobile. When i objected to their inaccurate reporting all they did was send me a copy of my credit report and have taken no action to correct their deficiency AND NO ONE SEEMS TO CARE, not the BBB and most importantly the Washington state insurance commisioners office who BTW have done nothing but side with insurance company’s regardless of the complaint.
Ken, I think your frustration is mis-directed regarding the inaccuracy of your auto insurance claims.
LexisNexis is the transient factor, not the source of the root inaccuracy. THAT’s where you should really focus….but you probably already know that.
This also shows how the “Knowledge Based Authentication” so popular by credit card issuers etc is just fundamentally broken: it assumes that the person knows the information (not true: how am I supposed to know, at work, what my credit card spending was last month!) and that the bad guy doesn’t (not true: the bad guy just pays, if not SSNDOB, the next one to come along).
At this point, credit issuance should REQUIRED that the applicant’s photo ID be examined, either by somebody affiliated with the company issued or in a notarized statement. Anything less is insufficient.
LexisNexis should be out of business. This wasn’t the first time and probably won’t be last!
As usual Krebs is doing the dirty work for InfoSec that we should be doing ourselves!! Thanks Brian!
I am not at all surprised about LexisNexis being breached. They’ve been breached before and the nature of their business is such that’s always open to lots of abuse.
Knowledge-Based Authentication isn’t really dead though. As usual the failure here is laziness and poor security training. Employees at call-centers aren’t told “Hey if the person takes a long time to answer a question and sounds like they are clicking through documents, deny them access!”. And financial institutes *could* require two-factor authentication for phone calls, but don’t want to spend the money to roll those things out.
Simple things like sending confirmation letters to an address on record for a person saying “Oh hey we’re just confirming your recent credit report request on this date, from this phone number” could help as well.
But that costs money. 🙁
what about adding cellphones to the authentication process like google, ebay and other companies do now?
like how bout one step is you replying to a text message sent to your phone?
Is that too easy to spoof, I’m always trying to get these game companies to adopt these measures also, if not at least to recover compromised accounts.
I don’t like anything done over the cell phone. The legitimate messages from banks and the such look like phishing attempts and the phising attempts look like official messages. I never reply to anything sent to me in a text from anyone I don’t know personally. Of course, to investigate the message with a separate phone call takes up quite a bit of time as the bank or credit issuer grills you with questions you don’t have the answers to at the moment. You can’t win.
LexisNexis ‘…said it found “no evidence that customer or consumer data were reached or retrieved,” via the hacked systems.’
How quaint. That’s like a bank saying, “We just learned that a sophisticated operation created a massive underground tunnel into our vault that went undetected for months, allowing a criminal enterprise unfettered access, but there’s no indication that they stole anything.”
Crime Units are freakin Nutso sometimes.
Just because they dont see any data exfiltration doesn’t mean it didn’t happen.
It depends on how it was exfiltrated. It could have been done via an encrypted channel, or even more masterful, and somewhat boring, but it works – a person simply accesses a file and either records the data as they scroll slowly through the list, or they save the data via print screens.
Crooks have PLENTY of time on their hands, creating records from scratch gives them something to look forward to, and eventually they can say its brand new information and may get a few more pennies a record.
There are a thousand ways to avoid the detection of data being whisked away. They have to be smarter than the crook, or, learn from other organizations that have been through the same thing.
It boils down to the experience of the Fornesic teams brought in. IF none are brought in , and its either an in house cluster, or better yet – a perverse writeup to say they haven’t found anything at all to keep the integrity of the business the same while dumbing down the breach. How do you know they are telling the truth ?
If security by obscurity is present, so are the smoke and mirrors when it comes to the truth of the matter.
This is why data breaches can take forever to dissect, and get resolved. By then, whatever data was taken is spread all over the crooks network.
Company spokespeople = spokespeople of feel-good rhetoric. It’s rather pointless to receive communication from many spokespeople:
Aurobindo Sundaram, vice president of information assurance and data protection at Reed Elsevier, the parent company of LexisNexis. “…no evidence that customer or consumer data were reached or retrieved…” My answer: It’s not likely the breachers are going to recreate what they’ve done to exfiltrate any data. If LexisNexis has no log, there’s no record of what did and didn’t leave LexisNexis.
Elliot Glazer, chief technology officer at Dun & Bradstreet, “Data security is a company priority, and I can assure you that we are devoting all resources necessary to ensure that security.”
Spokesman Ray Howell, Altegrity holding company of Kroll Background America Inc, “We consider the protection and safeguarding of our various systems of the utmost importance…”
In the end I’m leaning towards it’s “Breached security”.
I can’t help but notice that in the scenario you painted the phrase “no evidence that customer or consumer data were reached or retrieved” is correct.
I think I get your point. It depends on whether proper network logging is enabled to be able to tell what’s going on with the network. Without proper logging there’s a better chance the breacher can enter without being seen or knowing what the breacher has done.
There’s also the intruder that enters and covers tracks by changing or deleting logs, files, etc–in the network and hiding. As the entry point for the breacher, “none of the 46 top anti-malware tools on the market … detected” the backdoor malware when it was first detected by non-anti-virus means.
What’s important to realize is that Lexis Nexis, (ChoicePoint was purchased by them-remember the big data breach and ID theft in 2005?) Hireright and others have alkl of our data and we have no control over that data. Once you do become a victim of ID theft from one of these companies, it is like puling teeth to regain your good name. I have a client right now who is the victim of criminal ID theft. Just think about all the background checks that these companies sell- and what would happen to you if your good name is destroyed. This story is about my client Stepen Echols who I have been helping pro bono for 2 years. http://www.military.com/veteran-jobs/security-clearance-jobs/2013/09/03/vete Also see this http://www.nytimes.com/2012/07/25/opinion/faulty-criminal-background-checks.html
The full first link:
http://www.military.com/veteran-jobs/security-clearance-jobs/2013/09/03/veteran-homeless-after-battle-with-identity-theft.html
Great research, Brian! This is scary, scary news.
8.18.2.254 / Kroll’s IP is listed in the CBL (Composite Blocking List) ; last detected at 2013-09-25; “infected with…botnet”
Hopefully they don’t plan on sending email from that netblock anytime soon :/
The breachers could stay more inconspicuous–don’t use it for spam–and keep stealing ID info instead.
Seems the IP is offline now.
Hehehehehe it doesnt take much for the crooks to get out. If the ISP doesn’t knock them out, then they can reach out to a Free DNS service and change the IP of where the server is housed. heck, if the bandwidth is sufficient, one may be able to sit at a local coffee shop that offers free wireless access and get an IP from them, go to the DNS site, change the DNS entry to the one he is sitting at, fireup the smtp service and send spam all over again. It depends on the ruleset of the free wireless service, but many don’t pay attention to what is being passed, as. As long as there are customers in the shop and spending cash is all that matters = Þ
Article:
o “a tiny unauthorized program called “nbc.exe” was placed on the servers”
o “An initial analysis of the malicious bot program installed on the hacked servers reveals that it was carefully engineered to avoid detection by antivirus tools”
Presumably, this hack targeted Windows servers. My questions:
o Why was neither Software Restriction Policy nor AppLocker configured for these servers as they are included at no cost with Windows? In other words, raise the bar for the malware miscreants.
o Why was no file integrity software (e.g., tripwire, OSSEC) installed on these servers and reports reviewed? In other words, assume that there will be an intrusion and monitor your systems?
I’m sure that their are more questions along this line of inquiry …
What a great piece of investigative journalism!
Good job Brian, and thanks for the effort, it makes the work we do much more interesting when we can see how the other side has been leveraging their work for money.
The statements from each victim also lets us see how the companies handle what has been an obvious breach.
Can’t wait for parts 2 and 3.
I did a WHOIS on the SSNDOB domain out of curiosity. It shows as being registered out of a town I am familiar with:
Domain Name: ssndob.ms
Domain ID: 277706-MNINET
WHOIS Server: whois.nic.ms
Referral URL:
Updated Date: 2013-09-25T16:26:34.579Z
Creation Date: 2013-03-27T17:32:36.453Z
Registry Expiry Date: 2014-03-27T17:32:36.557Z
Sponsoring Registrar: Key-Systems
Sponsoring Registrar IANA ID:
Domain Status: serverHold
Domain Status: ok
Domain Status: serverUpdateProhibited
Domain Status: serverTransferProhibited
Domain Status: serverRenewProhibited
Domain Status: serverDeleteProhibited
Registrant ID: 277705-MNINET
Registrant Name: Danny J. Smith
Registrant Organization: SSNdob
Registrant Street: 1696 Heron Way
Registrant City: Hillsboro
Registrant State/Province: OR
Registrant Postal Code: 97123
Registrant Country: US
Registrant Phone: +1.5038462154
Registrant Phone Ext:
Registrant Fax: +1.5038462154
Registrant Fax Ext:
Registrant Email: ssndob@dnsname.info
Admin ID: 277705-MNINET
Admin Name: Danny J. Smith
Admin Organization: SSNdob
Admin Street: 1696 Heron Way
Admin City: Hillsboro
Admin State/Province: OR
Admin Postal Code: 97123
Admin Country: US
Admin Phone: +1.5038462154
Admin Phone Ext:
Admin Fax: +1.5038462154
Admin Fax Ext:
Admin Email: ssndob@dnsname.info
Billing ID: 277705-MNINET
Tech ID: 277705-MNINET
Name Server: ian.ns.cloudflare.com
Name Server: uma.ns.cloudflare.com
DNSSEC: unsigned
Additional Section
Sponsoring Registrar URL: http://www.key-systems.net
Sponsoring Registrar Address: Key-Systems GmbH Im Oberen Werk 1 66386 St. Ingbert
Sponsoring Registrar Country: DE
Sponsoring Registrar Phone: +49 (0)68949396850
Sponsoring Registrar Fax: +49 (0)68949396851
Sponsoring Registrar Customer Service Contact: tld-cocca@registry-auto.rrpproxy.net
Sponsoring Registrar Customer Service Email: tld-cocca@registry-auto.rrpproxy.net
Sponsoring Registrar Admin Contact: Hostmaster of the day
Sponsoring Registrar Admin Email: registry@key-systems.net
TERMS OF USE:
You are not authorized to access or query our Whois database through the use of electronic processes that are high-volume and automated.
The data is for information purposes only. MNINET does not guarantee its accuracy. By submitting a Whois query, you agree to abide by the following terms of use:
You agree that you may use this Data only for lawful purposes and that under no circumstances will you use this Data to:
(1) allow, enable, or otherwise support the transmission of mass unsolicited, commercial advertising or solicitations via e-mail, telephone, or facsimile;
or
(2) enable high volume, automated, electronic processes. The compilation, repackaging, dissemination or other use of this Data is expressly prohibited.
>>> Last update of WHOIS database: 2013-09-25T16:26:34.374Z <<<
One thing I noted in digging a little deeper is that the ZIP is incorrect for that street address. Correct ZIP is 97006.
Also, that address would include an apartment number if it were complete – Google Street View shows apartments under construction at that street address.
The phone number for "Danny J. Smith" is a Verizon VoIP line out of Portland that is assigned to a customer in McMinnville, OR.
I'm guessing this is probably a false identity used when registering the domain. Big surprise there.
I wonder who is actually paying for the registration…
That WHOIS information is fraudulent. The proprietors of this ID theft service reside in Russia, to the best of my knowledge. I may have more information on this aspect of the business in an upcoming story.
Do you Mr Brian ? Give as a hint then 🙂
Would the registrar, key-systems.net update the fraudulent record, so that may get the true credentials, rhetorical?
That registrar isn’t one of the more reputable ones, last I know.
As a person with the first-hand knowledge of this brilliant piece of investigation by Brian, I am not very encouraged by Mr. Sundaram’s comment “… but to date have found no evidence that customer or consumer data were reached or retrieved…” especially since the last sale of LexisNexis’ “customer or consumer data” on ssndob.ms happened about 24 hours before this article’s publication to a scammer from Nigeria.
CloudFlare.com, a reverse proxy, has 101 nameservers on Anycast. They do a poor job of purging old data. This means you can select any of them (below we use “abby”) to get both old and current information on whether a particular domain used CloudFlare:
dig NS +short EXPOSED.SU @abby.ns.cloudflare.com
dave.ns.cloudflare.com.
fay.ns.cloudflare.com.
dig NS +short SSNDOB.MS @abby.ns.cloudflare.com
ian.ns.cloudflare.com.
uma.ns.cloudflare.com.
dig NS +short SSNDOB.RU @abby.ns.cloudflare.com
ian.ns.cloudflare.com.
uma.ns.cloudflare.com.
dig NS +short SSNDOB.CC @abby.ns.cloudflare.com
duke.ns.cloudflare.com.
olga.ns.cloudflare.com.
dig NS +short SSNDOB.INFO @abby.ns.cloudflare.com
fay.ns.cloudflare.com.
tom.ns.cloudflare.com.
I mentioned the CloudFlare connection and the honeypot possibility to Brian in an email last April, after he wrote about exposed.su. Brian responded, but offered no opinions or information regarding this. Hopefully he will give CloudFlare a nod in future installments of this story.
For what it’s worth: The same SHA256 hash of the listed file has some assocation with another host not mentioned in the article, kartmanscript [dot]com 103.8.24.167 Malaysia.
https://malwr.com/analysis/Yjg4ZDJmOTM1MjM2NDI0Y2E1MDkwMDQ3MjA4MjhmNjA/#signature_network_http
One of Avivah’s comments rings a bell. I spoke to a very accomplished identity thief in prison over the weekend. He said that when he would go into a Home Depot and apply for credit, he’d be put through to an 800 number to verify his identity.
When they asked him his verification questions, he would look for the answers in the stolen credit report he had in his hands. Sometimes it would take extra long to find the right answer.
The person at the other end of the line would never get suspicious. Even more frightening, the Home Depot employee across the desk would never say anything either.
Here is the thing – what technology is the best in this situation to curb fraud ?? What do you want the Home Depot go to the person’s house on the application and knock on thier door??
There is no fraud-proof method so the Home Depot and other organizations utilize the best technology available to them.
If they’re asking questions such as “how many credit transactions did you make last month” and the like would you expect anything else?
Wow this is very interesting. I wonder if you publishing this article contributed to the site being down? I also wonder if this helps or hinders the people in law enforcement? Good analysis though
I refused to participate in a health screening for my former job, a participation that was “voluntary” but from which I would be penalized for not participating. My reasoning for not participating was that “data would be shared with trusted partners” of which there was no notice of who these partners were. For all I know, it was the company listed above that was one of the “trusted” partners. If I don’t trust someone with my data, guess what, they aren’t going to get it from me, that way it can’t be misused or lost in the first place. This is the age of information, people, be careful of how you use it and who you give it to. I was willing to be penalized rather than give my information to some unknowns.