Adobe Systems Inc. is expected to announce today that hackers broke into its network and stole source code for an as-yet undetermined number of software titles, including its ColdFusion Web application platform, and possibly its Acrobat family of products. The company said hackers also accessed nearly three million customer credit card records, and stole login data for an undetermined number of Adobe user accounts.
KrebsOnSecurity first became aware of the source code leak roughly one week ago, when this author — working in conjunction with fellow researcher Alex Holden, CISO of Hold Security LLC — discovered a massive 40 GB source code trove stashed on a server used by the same cyber criminals believed to have hacked into major data aggregators earlier this year, including LexisNexis, Dun & Bradstreet and Kroll. The hacking team’s server contained huge repositories of uncompiled and compiled code that appeared to be source code for ColdFusion and Adobe Acrobat.
Shortly after that discovery, KrebsOnSecurity shared several screen shots of the code repositories with Adobe. Today, Adobe responded with confirmation that it has been working on an investigation into a potentially broad-ranging breach into its networks since Sept. 17, 2013.
In an interview with this publication earlier today, Adobe confirmed that the company believes that hackers accessed a source code repository sometime in mid-August 2013, after breaking into a portion of Adobe’s network that handled credit card transactions for customers. Adobe believes the attackers stole credit card and other data on approximately 2.9 million customers, and that the bad guys also accessed an as-yet-undetermined number of user names and passwords that customers use to access various parts of the Adobe customer network.
Adobe said the credit card numbers were encrypted and that the company does not believe decrypted credit card numbers left its network. Nevertheless, the company said that later today it will begin the process of notifying affected customers — which include many Revel and Creative Cloud account users — via email that they need to reset their passwords.
In an interview prior to sending out a news alert on the company’s findings, Adobe’s Chief Security Officer Brad Arkin said the information shared by this publication “helped steer our investigation in a new direction.” Arkin said the company has undertaken a rigorous review of the ColdFusion code shipped since the code archive was compromised, and that it is confident that the source code for ColdFusion code that shipped following the incident “maintained its integrity.”
“We are in the early days of what we expect will be an extremely long and thorough response to this incident,” Arkin said. The company is expected to publish an official statement this afternoon outlining the broad points of its investigation so far.
Arkin said Adobe is still in the process of determining what source code for other products may have been accessed by the attackers, and conceded that Adobe Acrobat may have been among the products the bad guys touched. Indeed, one of the screen shots this publication shared with Adobe indicates that the attackers also had access to Acrobat code, including what appears to be code for as-yet unreleased Acrobat components (see screen grab above).
“We’re still at the brainstorming phase to come up with ways to provide higher level of assurance for the integrity of our products, and that’s going to be a key part of our response,” Arkin said. He noted that the company was in the process of looking for anomalous check-in activity on its code repositories and for other things that might seem out of place.
“We are looking at malware analysis and exploring the different digital assets we have. Right now the investigation is really into the trail of breadcrumbs of where the bad guys touched.”
The revelations come just two days after KrebsOnSecurity published a story indicating that the same attackers apparently responsible for this breach were also involved in the intrusions into the networks of the National White Collar Crime Center (NW3C), a congressionally-funded non-profit organization that provides training, investigative support and research to agencies and entities involved in the prevention, investigation and prosecution of cybercrime. As noted in that story, the attackers appear to have initiated the intrusion into the NW3C using a set of attack tools that leveraged security vulnerabilities in Adobe’s ColdFusion Web application server.
While Adobe many months ago issued security updates to plug all of the ColdFusion vulnerabilities used by the attackers, many networks apparently run outdated versions of the software, leaving them vulnerable to compromise. This indeed may have also been the vector that attackers used to infiltrate Adobe’s own networks; Arkin said the company has not yet determined whether the servers that were breached were running ColdFusion, but acknowledged that the attackers appear to have gotten their foot in the door through “some type of out-of-date” software.
Stay tuned for further updates on this rapidly-moving story.
Update 4:38 p.m. ET: Adobe has released a statement about these incidents here and here. A separate customer security alert for users affected by this breach is here. Also, in a hopefully unrelated announcement, Adobe says it will be releasing critical security updates next Tuesday for Adobe Acrobat and Adobe Reader.
Update, Oct. 5, 4:35 p.m. ET: Rakshith Naresh, a product manager at Adobe, said in a Tweet yesterday that the breach did not involve ColdFusion vulnerabilities.
Update, Oct. 9, 12:50 p.m. ET: Naresh’s Tweet stating that the breach didn’t involve ColdFusion servers was deleted at some point. I followed up with Adobe via email: An Adobe spokesperson said the company’s investigation is still ongoing, and that “at this time we have not identified the initial attack vector to include or exclude a ColdFusion server.”



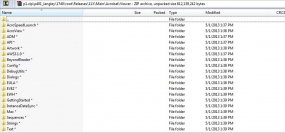
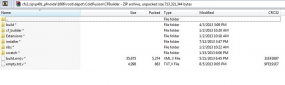

Don’t forget – this issue happened to Microsoft and a few other companies a few years ago. It was amazing to see the amount of chatter that created. BUT in record time, Law Enforcement knew the where abouts of each copy of the source code.
You know what is absolutely moronic about this breach? WHY do you have to have trade secrets on network facing equipment? In this day and age with all the breaches and other nasties happening out there, wouldn’t most companies think it would be wise to keep their trade secrets on a separate internal network that is not connected to the internet? How often does the source code have to be accessed?
I think its failure of the mindset. Its ease of use over maintaining of security. And this is another BIG business that lacks due care and fails the prudent man rule. Its all about the almighty dollar, lax security and the established rules not being upheld.
One never knows if an account was compromised when an internal worker(s) use the same stinking password on every site. All the hacker has to do is find out where these people work, find a nickname, username, email address or other information. Then they can attempt to log onto a network and if successful, its immediate access with keys to the Kingdom.
I am a big believer in the computer rings of trust theory. In the center are the most valuable assets. Very limited access to the information is allowed. More access is granted the farther out the rings go, but network connectivity between rings is extremely difficult o surpass. Workstations are assigned to pass information between each internal ring – none of these internal machines have internet access. The outer most ring must have computers up to date, do not have access to the internal network and are wiped on a semi regular basis, or are deep freezed or other technology. Work is for work – not for individuals to surf and get their fix on social website poisoning.
Build it right and any breach is futile. BUT with big businesses, its about the bottom line. Create as much cashola as possible. When something like this happens, they have the cash in hand to make changes, but in the end who suffers?
“How often does the source code have to be accessed? ”
At the risk of being insulting, you must not work in software engineering. If a product has not yet been retired, source code will be accessed multiple times each day. For a large team, source code might be accessed multiple times each hour. In my last programming job, I was working from home, checked out a module, made some corrections, and tried to check it back in only to discover that two other people had also made changes and checked it back in, forcing me to do a double code merge (a real PITA if you are not sitting next to the other person), all in one day.
Adobe is still using CVS?!? o_O
If more than one person is accessing source code, one flavor or another of source code control will need to be employed. That’s been true since Bell Labs invented C, Unix, and a few other things.
Its another “matter of convenience”, depending on how they access their information.
Allowing people to access code from home is dangerous. It may be in modules, some may be a virttual connection to a server in the company or even alowed to download a segment, update and upload the code.
It also is a big issue when people BYOD to work… Thats a mess ready to stink to high heaven.
Accessing the code outside of the business walls opens up more risks such as insider threat, residual code left on workstations that could be vulnerable to attacks and malware.
Having the keys to the kingdom safe and secure is supposed to be the utmost importance. I am sure Brian will let us know how they got in on a future update, but again, controls were too lax.
They cant use VPN, SSL or whitelists? Allowing only known good IP addresses in instead of the whole world being able to knock on the door(s) ?
Its still unclear how the hackers got in, and though the source code is important, PPI is as equal or more important since it affects many, many people.
“Allowing people to access code from home is dangerous.”
I agree, but that horse left the barn years ago. And the second cousin, having separate software groups in different countries, is really no different. Dell and many other companies have test, product support, and even software development groups in India, all accessing the same servers.
“It also is a big issue when people BYOD to work… Thats a mess ready to stink to high heaven.”
BYOD is being driven from the top, because sales, marketing, and other groups have convinced corporate management that they need to be free of all IT encumbrances. Of course, when those people are responsible for data leaks, they will point the finger at IT.
But there is another shoe dropping with BYOD. Some beancounters have started to save money by requiring employees to supply their own devices, shifting hardware costs from the company to the employees. However, those employees are (rightfully in my opinion) refusing to allow the company to dictate IT policy on their property. This shortsighted dream will cost those companies much more than they save on hardware.
You mean 6 months ago. When eastern europeans hacked facebook and apple. And microsoft finally admitted a week or two later that they got breached at the same time.
whats scary about this, and none of them had the slightest clue what was done on their networks. (or at least they lied to the public) And whats scary about this, is if you want to virus everyone in the world….that would be how.
Also, why? because speed of information is essential! The same reason the NSA is now looking for commercial partner to make their own secure smartphones. Because they have to stay up to date and be able to use them to be more effective!
This is a huge irony in that Adobe is a an intrusive and constant pusher of updates (this is classic: http://xkcd.com/1197/), but they allegedly got hacked because they didn’t install their own patches.
Then again, it’s all good because it mostly affects the customers.
Ouch! But right on point in my opinion
You made that up! where did you read that! Don’t invent things just for a “clever post”. There is nothing to indicate that what you say is true!. No body has said it! You made that up!
Another piece of software I do not use…
This is what I call corpware, as large and medium business simply use the conventional software as it is so convenient…
Let’s call this for what it is – drive through ware…
To the pirates that took the source code for Adobe Acrobat,
If I give you a list of bugs to fix could you address them and send me a working copy back? I will be more than happy to pay you for your efforts. Despite Adobe’s claims to the contrary, I’m certain you have my billing info so please charge me a reasonable fee for your work.
There are issues that Adobe has not bothered to address that have persisted for the last 10 versions. Hopefully the code is now in the hands of a team that actually cares about the product.
“If I give you a list of bugs to fix could you address them and send me a working copy back? I will be more than happy to pay you for your efforts. Despite Adobe’s claims to the contrary, I’m certain you have my billing info so please charge me a reasonable fee for your work. ”
EPIC!!
~Zing~
Perfectly witty – and sadly true. Awesome post!
We were contacted yesterday by our identity theft protection company about an unauthorized attempt of a purchase at Best Buy using the Credit Card we use for the monthly payments for our Creative Cloud membership.
Therefore, the statement “At this time, we do not believe the attackers removed decrypted credit or debit card numbers from our systems,” made by, Adobe’s Chief Security Officer, Brad Arkin is not true!!!!
I am trying to find out how and where to escalate this. We are having to audit the bank records to investigate if other purchases were made prior to the identity theft guard kicking in!
We will be posting this incident via social media later today, to warn people.
It’s unlikely that it’s related. Since Adobe only have Card number, Exp Data and CVV and not the Mag Stripe data they couldn’t have made a counterfeit card and used it at a Best Buy. Your card was likely compromised elsewhere.
Jay,
You don’t need a physical card with online purchases.
The only time our card has ever been compromised coincides (to the day) with the adobe breach?
What are the odds!?!?!?
I maintain my position that it is my belief that credit card information was compromised.
So are you saying that they used the card on bestbuy.com or in a Best Buy store?
And even if it was used on bestbuy.com (i.e. not cardholder present) that doesn’t necessarily mean that Adobe is where your card was compromised (unless that’s the only place you’ve ever used your card).
When there are millions of cards used daily, and tens of thousands of cards used for fraudulent purposes daily, the odds of what you’re describing happening are actually fairly good.
At the end of the day, we have identity theft and credit card protection on the cards.
All I know is they said the purchased was not allowed and blocked when trying to process a charge.
You are right in stating, there is no way to know that the card was compromised via the Adobe Breach. I hope that you’re right.
If anyone else is reading these comments, just make sure. Check your credit card that you use for your Creative Cloud membership for suspicious charges.
“I maintain my position that it is my belief that credit card information was compromised.”
I forgot, but yes, I agree. Your card was probably compromised. There’s just no way of telling if it was compromised at Adobe.
My credit card just got cancelled due to suspicious purchases my bank picked up. I’m seeing a lot of other Adobe account holders mentioning similar things on forums. Hmmmmm coincidence? On one hand we have Adobe ensuring us that the CC details are encrypted but also that we need to keep a look out for unusual account activity. I dont think we are being fully informed about whats going on but then I’m used to that from Adobe.
@anymouse
You have described a company with multiple branches/contacts but you have not explained why all or even any of them need to be attached by the Internet, 24/7. Most of us have spent our lifetimes with Instant On and appliances that are always on (think clocks on microwaves, TVs, etc) so it is no wonder that we’ve forgotten that there is another mode. It’s called “Off.” Your follow up comment cements this mentality. YOU want instant access to the source code from anywhere so of course, you should have it. Can’t do the work at home and bring it into the office. That would be inconvenient. And why in the world would anyone think that allowing developers to diddle with the source code without consulting any of the other developers is a good idea? That is a HORRIBLE idea. If there is a team working on the code, changes should be made AFTER the team reviews them for, oh, say conflicts? If a company allows its developers to change the code, on the fly, from anywhere in the world, it is obvious why there are so many bugs in newly released products and upgrades.
Taking just your first two items, sw developers in Mountain View, testers in Delhi. Give me an example of why those two locations need to be linked 24/7. MV needs to download sw for testing. That takes how long? And, the link is/should be attended. After download, you turn off the connection. AND, there is no reason why the download needs to be from an important server. The sw can be first downloaded to a flashdrive which can then be inserted into a clean PC or router that is dedicated to external communications, a connection opened, the data transmitted and then the connection closed. Nothing is left on the dedicated hardware. Coming back, same thing in reverse. There is absolutely no reason for Delhi to have 24/7 access and most certainly not access to a server or computer that does ANYTHING except accept and transmit the sw being tested. A similar case can be made for each of the other items in your list. A warehouse in China? Needs Internet access to the MV servers containing copies of the sw that is the company’s life blood? I don’t think so but perhaps since I’m just an old woman, you can give me an example of why this is so and why such a link needs to be up, unattended, 24/7. Lawyer in NYC? You need to be connected 24/7, through the Internet, to your lawyer? Why? What could you possibly need to communicate by Internet that requires a 24/7, unattended connection?
Even today, many remember XYZZY. Too bad they don’t remember OFF too.
“And why in the world would anyone think that allowing developers to diddle with the source code without consulting any of the other developers is a good idea?”
You have many misunderstandings about how software is created today. Software engineers do not “diddle” with source code.
First, it sounds like you think that someone writes a module and it is never modified again. That almost never happens.
Here’s what happens today in most corporations. Marketing and/or engineering create requirements. Developers write what they think will satisfy the requirements. Testers find bugs. Management changes requirements. Developers make changes. Repeat this process many times.
Then after the product is released, testers and users find bugs. Management adds requirements. Developers make changes. Repeat this process many times until the product is retired.
Sometimes management decides that something has to happen in a too-short period of time. Developers cut corners to meet the deadline. Often the product is hobbled for years, if not forever, because of this.
Developers change source code all the time without consulting their co-workers. They use some sort of source code control (e.g. CVS) to obtain it. They fix the bug or add new functionality. They check the code back into the repository. Rinse and repeat.
Developers rarely own a piece of code. That was true in the old days, but today everyone is allowed to make changes anywhere.
“Taking just your first two items, sw developers in Mountain View, testers in Delhi. Give me an example of why those two locations need to be linked 24/7.”
Because:
– there is a 12-hour time difference between India and the USA
– some groups in India work Indian hours while others work North American hours
– people do not work exactly 9-5
– a boss might demand that someone fix something today, requiring longer hours
– some companies allow testers to change source code, but even if they do not change it, they need to be able to view it
– multiple people might check out the same module, resulting in code merges afterward
– a software development group might be split between India and North America
– and so on
“The sw can be first downloaded to a flashdrive”
Are you aware that complicated products like Windows have tens of millions of lines of code?
“A warehouse in China? … Lawyer in NYC?”
If I could draw Venn diagrams here, I could explain the overlapping domains of the various groups I mentioned.
If you really want to understand the problems inherent in software engineering, I recommend the book “The Mythical Man-Month: Essays on Software Engineering” by Fred Brooks.
@anymouse
You said, “Software engineers do not “diddle” with source code” and “Developers change source code all the time without consulting their co-workers.” QED
“it sounds like you think that someone writes a module and it is never modified again.” No, I don’t think that. Because of the aforementioned, non-cooperative changes to code, new bugs are constantly being added to software, bugs that need to be fixed by adding, unintentionally of course, maybe (job security?), new fixes/bugs.
Your timeline for creation, review, re-write makes sense in today’s environment. My point is that the environment is faulty. None of those steps require 24/7 open access. You discuss an issue, you hang up the phone. You transmit code to be worked on, you close the connection.
India: Our hypothetical has India just testing not developing. They test, they report. 12-hr time diff doesn’t matter, nor their work hours, nor an impatient “boss.” And WHOOPS!! “some companies allow testers to change source code.” QED2. Need to view source? Fine, open connection, send, close connection.
Flashdrives: 128gb commonly available for less than $150.00,. 256gb = $410 retail, 512gb.= $965, (Kingston), 1T = $unknown (Kingston). Or you can just use a portable hard drive. If 1T isn’t enough to store the source code, break the program into segments.
Mouse. It sounds like you are just hanging on to bad habits because you are comfortable with them. They are still bad habits. Proof? Look at the breaches, expense, trouble, people’s credit being compromised. I know how it is to get sloppy too. You do things a certain way. Your way works. Then technology changes so the bad guys can co-opt your work because of your sloppiness. Solution? Change. Don’t defend poor or outdated practices just because “that horse left the barn years ago.” It is never to late to close the barn door… or move to a better barn.
Feel free to submit an article describing your proposal for an industry magazine, e.g. Computerworld. You will be laughed out of the Internet. Your proposal will reduce efficiency because what you are proposing is reverting back to the days of dial-up. And your comment about using flash drives is just plain stupid, given that source code is constantly changing in a large company. What part of “tens of millions of lines of code” didn’t you understand?
“It sounds like you are just hanging on to bad habits because you are comfortable with them.”
They are not “my” habits, bad or otherwise. You have never worked in engineering and it really shows. Do you always tell people how to do their job when you have absolutely no clue what that job entails?
@anymouse
You are right about my being ignorant of the day to day procedures by which software is developed. So instead of arrogantly slamming me, why not explain where I went wrong? For instance, when you said “software developers in Mountain View, software testers in Delhi,” I assumed you meant the people in Delhi were to run the software, abuse it, try to make it fail, so as to find bugs and/or design flaws. If that is true, then why would they need to download any, much less “tens of millions of lines of code?” Is it more efficient to send them the source code and have them compile it in Delhi than to send them the working program?
““And your comment about using flash drives is just plain stupid, given that source code is constantly changing in a large company.” How does the fact the source code is constantly changing affect the method by which the program is transmitted to testers? I’m pretty good at extrapolating but that leap of logic is too big. I can see how constantly changing code might require more frequent transmissions but not why that’s a good reason to hook up the servers that hold the source code for a direct Internet interface. Or again, am I missing something in my naiveté? If you don’t use an isolated, dedicated server and you don’t send directly from a network server, how do you send the program to India?
“So instead of arrogantly slamming me”
I was very respectful right up until you wrote “It sounds like you are just hanging on to bad habits because you are comfortable with them. They are still bad habits.” You only think they are bad habits because you do not understand software engineering.
“How does the fact the source code is constantly changing affect the method by which the program is transmitted to testers?”
The fact that you do not see the flaw in your statement means you do not understand the process by which developers create code. I’m really tired of explaining it to you. My previous post was quite long, yet you did not understand. Read a few books on software engineering.
P.S. Do not assume testers work on static code. And do not assume all developers in one company work in one building, time zone, or country
With all due respect for your expertise, anymouse, your reply to Ms. Trefethen is quite condescending. Today’s routine would not have been tolerated when many of us began coding. The fact that a company can make more money by exposing MY system to malware through unsecure practices doesn’t make me agree that it’s OK.
I just cancelled my cards. It’s my anniversary and I have to postpone everything I had planned until next week. I have to find and correct any place where that data may be. I’ve dealt with a rush of phishing and spam for the last 3 weeks – now I know why.
Adobe is offering me a year’s credit monitoring. Whoopee. You say “what part of 10’s of millions of line’s of code don’t you understand”? My response is what part of 2.9 million customer credit cards don’t YOU understand. What they need to do is spend $290 million helping every single one of the 2.9 million to redo their bank accounts and cards used to buy the software in the only way it is offered – by subscription. Maybe then everyone at Adobe will figure out that the cost savings to development that we as customers bear isn’t worth it anymore.
“With all due respect for your expertise, anymouse, your reply to Ms. Trefethen is quite condescending.”
No more or less than her words I was replying to. If you do not consider “It sounds like you are just hanging on to bad habits because you are comfortable with them. They are still bad habits” insulting, then you and I speak different languages. She has no idea what goes on in software engineering, yet she believes she has the answer to all software problems. I call that highly presumptuous. I was respectful until she wasn’t.
” Today’s routine would not have been tolerated when many of us began coding … My response is what part of 2.9 million customer credit cards don’t YOU understand.”
I was replying to very specific comments of hers. I never addressed the basic issue, though I did touch on it in other posts.
Here’s the problem: it is impossible to secure these systems when they are spread over multiple campuses tied together through the Internet. The minute we allowed outsourcing, we needed servers that would be vulnerable. VPN, secure servers, whatever, they all have flaws. If you want security, then mandate — by law — that these companies cannot outsource and must be tied together by T1 (or faster) lines. Internal communications will be impossible to intercept.
But everyone wants immediate access and cheap prices. You get what you pay for.
Are you one of those who believe that open source software is more secure. In other words the more eyes on it, the more polished it will be? I know some believe that open source software is the safest, and that everything should be open sourced.
Besides the fact this may cut profits, what is your take on this?
I always struggle on the fence. Common Sense tells me if its open sourced attackers, black hats, will find the vulnerability before the white hats. I also always believe black hats severely outnumber white hats nowadays lol. I also think 9 times out of 10, its a spy within the company.
what are your thoughts? more eyes or less eyes on the source code is better? and should everything just be open sourced for the betterment of society?
@Diane, you are either a troll or totally blissfully ignorant of software development process. Are you a CompSci teacher by any chance? Anyway, thanks a lot for many giggles I had reading your ideas. Please, don’t stop, we all need more laughs.
@Grin
Glad to give you giggles but I doubt Adobe thinks this breach is funny. When tested and trusted procedures result in failure, it is usually a good idea to think outside the box, to question that which has been taken for granted. So since you find my idea of reducing efficiency in exchange for increasing security a laugh, perhaps you might share with us what approach you would take to augment or replace current practices and prevent or at least mitigate the effects of future attacks.
With respect, Ms. Trefethen, many of the people here don’t care. They don’t have the desire, and some the ability, to relate these problems to real people who have to pay real money to fix problems they cause.
I’ve maintained for decades that every developer should be required to do desktop support (REAL support, not call center support) for a year before they write a line of code. It would increase the quality and usability of software tremendously.
Maybe they should take every developer at whoever’s company’s trade show, put them in bright shirts that say “I write the software you use” and make them deal with customers for a week. A little direct feedback may make an impact with those who care, at least.
I have worked in most phases of software engineering: requirements (systems engineering), development, sales engineering, product management, and marketing, and some IT.
I do not believe your ideas will work in practice for a few reasons.
Look at the requirements for a support job versus a developer one. The former requires only a high school education, while the latter generally requires a B.S. or higher. No company would pay developer wages for a year to someone working in support. I suspect most developers would refuse to work in support because their skills will become stale.
Developers could be required to work one week every six months or so in support to gain the experience you mentioned, but I’ll bet their managers would not eliminate their deadlines, so the developer would just play hookey. I was; I did.
Marketing and engineering management only allow certain developers to speak with customers. Many developers are not good with people. Many developers do not want to deal with customers. Some developers will share future product ideas (trade secrets). Some customers may even be corporate spies trying to obtain as much data as possible (the Chinese do this all the time).
ah yes there it is….but thats my question. If corporate spies are such a problem, and indeed I think they are, then why is Diane asking a crazy question?
Isn’t it common sense to not have the source code accessed remotely? I mean so it would be as easy as selling your password? We are supposed to feel secure over this?
What is the real issue here, are they outsourcing to other countries? lol
Please send your complete ID so that I can make sure that HR NEVER hires you to work at my place of work.
@Manuel
Your comment was merely a gratuitous insult and it contributed nothing to the conversation on Adobe’s breach nor to the edification of those whose education in software development is lacking.
Frustration with those who do not comprehend what you are saying is understandable. However, to dismiss them without making the effort is unhelpful and lazy. Anymouse was frustrated but s/he tried to provide information for those not familiar with the sw development environment to at least give a glimpse into the difficulties faced by developers.
As to my “complete ID,” that’s pretty fatuous from one who is afraid to put HIS last name on his posts. You want to know who I am? If you weren’t so lazy, you could look me up on the net and thereby glean sufficient information to fully inform your HR department.
Diane,
You have no experience or any understanding of how modern software development cycle works. Your comments and advices look stupid to software engineers who actively take part in the process of creating real world products. Your theory is very far from the reality and anymouse gave you a pretty good overview of how things work nowadays. Sorry, but your flash drive proposal is the silliest one, try to sell it to any collaborative team of developers who dynamically work on shared code, I would really want to see their reaction.
@N
“Your comments and advices look stupid to software engineers who actively take part in the process of creating real world products. Your theory is very far from the reality and anymouse gave you a pretty good overview of how things work nowadays.”
1) If you are referring to anymouse’s criticism of my mentioning Flash Drives, my advices [sic] related to sending data to sw testers in India, not to a team collaboratively developing a program.
2) If a procedure followed “in reality” is flawed, why defend it? Why not fix it?
3) Similarly, if “how things work nowadays” causes huge, damaging consequences to thousands of customers, unless as RRobinson stated, “they don’t care,” it is the responsibility of both the company and also those with hands on, every day, to to address the problems that cause the damage and for the latter to offer possible solutions from the vantage point of what they think is practicable, what will work.
It is incredibly arrogant for anyone even partially responsible for a disaster and who has at least some of the tools to rectify its causes to dismiss it with, “That’s how things are – that’s the way we do business.”
“That’s how things are – that’s the way we do business”
That’s your problem in a nutshell. No one is saying that. The other developers and I understand perfectly well what you are saying and we immediately see the flaw in your logic.
@anymouse
When you seemed to argue that sw testers need 24/7 access to source code and/or the developers, I asked why and though clearly you think you have answered me, I fail to see any relationship between my queries and your answers. Unless someone else wishes to step in and act as a middleman, there’s no point in our continuing to post at each other. Your responses don’t answer my questions or if they do, I don’t understand your logic. We are at an impasse.
Have a nice weekend.
Diane don’t let all these malcious hackers bother you. You ask a completely legitimate question.
Common sense tells us why in the world would we want the source code accessed remotely, with all these breaches, and especially with all the corporate spies out there like anonymouse claims.
I wonder if ironically, thats why anonymous is no longer employed as a software engineer.
I”m asking the question if you guys believe open source is the way to go? Common sense tells me hell no, especially if there is more black hats then white hats, in large numbers. But maybe i’m wrong. I’m always on the fence on this issue. Maybe its the fact that open source usually means non profit, and they are just simply not a target for the anti corps, anti gov’t delusional nutjobs.
If adobe was open sourced could they still make money. Do they need to be non profit so the anarchists dont’ attack them? lol….
then again ubuntu’s website was hacked recenlty….
Software engineering is a complicated career. Engineers are expected to know all sorts of things: Java, Swing, C, C++, Ruby on Rails, scripts, SQL, blah-blah. That’s why I left, because I got tired of learning completely new stuff every few months. A dirty little secret of the software business is that there are few older engineers for all sorts of reasons.
I am not a current developer, as my last Java job was a few years ago, so I forgot something I would have been reminded of the minute I logged onto my workstation.
I would bet that every single software product sold today used a software development environment of some kind. Wikipedia has a page on it: integrated development environment at https://en.wikipedia.org/wiki/Software_development_environment. Read it.
Everything is tied together for developers. Developers can compile, check into / out of a repository, and first-draft test. Some companies allow testers to use it and some don’t (there are different levels of test, something I think you do not comprehend). A flash drive would not work with it.
The problem is that you think software engineering is a simple process, when in truth it is very complicated. That’s why good developers command really big bucks because it is a rare skill. Your flash drive idea would put developers back 30 years. No manager would accept your idea for this reason.
Read the Wikipedia page on software development at https://en.wikipedia.org/wiki/Software_development. Try a few of the links on the right under software development process. Unless you spend some time reading these pages, you will never understand it. This is not arrogance on my part. I have tried to explain software engineering to non-developers, but it is just like being a cop, attorney, or dentist in terms of being unfathomable to outsiders.
Maybe I work around people with better morals …. but have any of you ever worked with a developer that purposefully puts in bugs for job security? Really? The natural occurance of them seems to keep most of us employed without having to make an effort to purposefully do something wrong.
I forget the term in engineering, that they actually teach in schools, where the focus is on how to make something stop working after a certain time period?
Do you know the correct term for this? I think its immoral, and i could never be an engineer for the fact i would let my professor have it.
“I forget the term in engineering, that they actually teach in schools, where the focus is on how to make something stop working after a certain time period?”
Most of what you write is nonsense, but this is demonstrably so. No professor or TA would teach such a thing. That sort of thing may be taught at hacker conventions, but those people, by and large, are not software engineers. Except for the NSA and CIA.
planned obsolescence
Adobe’s CF product manager has confirmed the breach did not exploit any CF vulns. http://ow.ly/puaFU
That Adobe manager deleted his Tweet or was made to do so. Adobe pointed this out to me, and I asked whether they had ruled out ColdFusion as an attack vector, and they said they had not. See the last two updates in the post above.
Maybe the hackers can create proper PKG installers that follow Apple guidelines? Puleaaasseeee…..
Seems fitting to point out 2 years back to:
Adobe, McAfee to Combine DRM and Data-loss Prevention
http://www.pcworld.com/article/172701/article.html
I’m a longtime Canadian Adobe customer who was affected by this. I received my privacy violation notification from Adobe last night, about the same time I discovered this website on an unrelated security issue.
I am appalled by this, and especially Adobe’s dismissive FAQ answers about this serious matter (http://helpx.adobe.com/x-productkb/policy-pricing/customer-alert.html)
What is most interesting to me is the timing of this and long-delayed disclosure to customers by Adobe. Adobe’s financial quarter ended August 30. Prior to that time they were aggressively trying to get their sales up for Creative Cloud – which has had a significant negative reaction from customers, me included. I was one of those targeted customers, as a longtime, and CS6, customer who had not yet bought into their perpetual payment plan.
Creative Cloud normally retains a customer’s credit card on file to make the monthly license/subscription payment.
Had the credit card / personal privacy breach been disclosed in a timely manner, prior to the end of the quarter, and during the final sales pitch, customers would have had even more reason to avoid Creative Cloud – hurting sales and the Adobe’s quarterly results.
According to some analysts, Adobe was having to spin positive sales results quite hard already in last month’s report.
Should the SEC be investigating this? There appears not to have been full and timely disclosure of the breach to investors, and had there been, it could have materially affected last month’s financial results.
Were customers like me put at greater risk because Adobe did not disclose in a timely manner to protect their quarterly results at a critical time? It sure seems possible to me.
I will be filing a formal complaint with the Privacy Commissioner of Canada about this matter and asking for an investigation. (The Canadian Privacy Commissioner has previously investigated Facebook and required changes.)
Interesting link to the FAQ. The FAQ errors out when I try to view any of the vital questions 🙂
Unfortunately, not the source of Flash or the Flash-protocol: So, the one stealing the code could have improved the quality/performance of the flash protocol or the flash plugins 🙂
ADM does not exists and is not supported in Acrobat anymore, it can not be XI source code
There’s no list of all the products that got leaked?
As far as adobe morones demonstrated their skills in past and present:
Expect everything got leaked. Including all customer and credit card data, decryption keys, every line of every piece of adobe sourcecode. And assume that all their software is backdoored. Until proven otherwise. Regrettably.
So how much will the compromise of all those credit card numbers put a dent in their shiny new subscription version of Adobe Creative Suite, d’ya think? And how long before customers start clamoring to be able to buy CS DVDs at their favorite big-box retailers again?
Hi Stratocaster,
I am one of the few that likes the concept of subscriptions. It make my personal life a lot easier. I understand the differences and risks. Would I do that in a large corporation? Not a chance.
I had to work directly with Adobe’s enterprise licensing group for almost 2 years. I was actually shocked several times by the arrogance and insensitivity to us as a large customer.
In the end, I have to use Adobe software to do my job. Some of it is the best available. If I had a viable alternative, I wouldn’t go near Adobe for love nor money.
that arrogance and insensitivity, is typical of all nerds in the computer industry. hackers, crackers, white hats, black hats, software engineers, programmers, developers etc….. They are all the same, they all extremely rude and arrogant. we are just stupid cows and monkeys to them. Its hurting their industry severely in recent years.
IMO, thats why the computer industry is going downhill, thats why noone uses linux, thats why pc gaming has been spiralling into the abyss for the past 10 years, most of the great forums and blogs of the past 20 years have died and become ghost towns and the internet is just full of anti american protesters, trolls and foreign spies.
Smartphones are just another bubble and illusion that will burst eventually when people realize they are more compromised then their pcs. But the diff right now is they are faster and still function when their pc doesn’t lol.
Most of these computer people ( i won’t characterize them further with fear of being called a biggot) resent society. Thats why noone blinks an eye when they get 35 years or death for doing absolutely nothing but being labeled or associated with malicious hackers…..
as sad as that is….
I think it’s great that we are talking about this but no need to exacerbate the dialogue with abuse. I switched from CF to Railo last year and am moving to Python this year, but I respect Adobe/Macromedia/Allaire. Flash is dying and may soon be dead, but when Adobe corrects their pricing model for CS the company could well flourish again. (And note the footer for this site cites WordPress, which is also dying fast since Google deprecates rankings for anyone still using primitive tools like WP 😉
Hi Brett Delmage:
It is all too common as I am sure, people here know more than I do, that companies never disclose how often they are hacked. Only when the company has to ‘get ahead’ of the story, will they ever release that information and when they do, they will always minimize it and deny, deny, deny. This is done, for what I believe to be legal matters. Make it hard for anyone to prove the thieves got your information from them.
What we need, and I hate to say this, is a Fed law that makes it mandatory that companies release this information within days of finding a breach. This will make the companies more security minded, customers will ‘feel’ secure, and I believe it would harden code.
But then I am not a coder, nor hacker, just a tech junkie.
Ms. Trefethen seems to have fair and valid points, as most do on this topic. There has to be a compromise on the “convenience” side and not the security side of making code.
I just received my email from Adobe an hour ago, but knew about this leak days ago, from this website. I am just glad that Adobe did not have any credit card info on file. And now, I will not bother going to the Cloud, I will simply use my current version of Adobe products.
ADOBE loses user info and the tech media has a field day.
ESET loses user info several times in several countries and not a word is said.
ADOBE should hire ESET’s spin doctors to cover up their mistakes.
People wake up , his was the NSA hacking Adobe, the code they stole was to inject false code on the internet to spy on people, the credit cards and information was to add to their database and so they could track all adobe users, content creation, financial transactions. When a large company is hacked they say this because they are not allowed to say it was the government.
That’s precisely why the millions of compromised credit cards haven’t been fraudulently used.
http://investigativerep.blogspot.com/
>Also, in a hopefully unrelated announcement, Adobe says it will be releasing critical security updates next Tuesday for Adobe Acrobat and Adobe Reader.
As soon as the code is leaked Adobe fixes their own purposedly planted backdoors.
As any neuroscientist will tell you, the “corporate” behaviour merely patterns the “four F’s” (feed, fight, flight, f…) of the cold-blooded reptilian behaviour. It lacks empathy and compassion to equate to even a primate grade, let alone a human person. If you understand this than you understand why in this day and age corporations still store customer data like credit card info and passwords in clear code (unencrypted). It is because they don’t care, …it is not in their nature. Their nature is only to respond to a threat.
Please find a quote from a neuroscientist regarding this – shouldn’t be too hard given that “any” will confirm it. Because it seems like an invalid equation to me.
I doubt your going to find different behaviour from an individual in the same situation and that there’s a huge link to compassion and empathy. You seem to be barking up the wrong tree.
I fail to understand as to why Adobe has to store customers’ credit card numbers. A policy has to be evolved to ensure that companies do not stores customers’ credit/debit card details in their systems
I would think if Adobe does any part of their own credit card processing (which to me would be the only reason they would store CC numbers) they should be subject to PCI compliance which does require not storing numbers in the clear among other security measures.
Hello Brian . Do we have to uninstall Adobe products now? I use photoshop and adoble flash player
source code, too? wonder if [they] can find potential backdoors.
Quick question for the people in the industry, Im no security expert but I thought Adobes response to the break in a little strange.
It sent an email to affected users with a link to reset their passwords.
From my limited knowledge of Phishing emails (limited to dont click on any links) this seems a strange way for Adobe to communicate with their clients.
Am I being unfair when I say that this illustrates that Adobe don’t understand security? Do other large companies also do this?
Any insider knowledge appreciated.
Stephen Johnson
Yes. I got one of those reset emails. So I went to Adobe’s website directly, not through the link in the email (heh heh heh, ize jeeenyus), and reset my password. I immediately got another email from Adobe telling me to reset my password.
Hmmm, I thought, this one would seem to be truly legit since it was triggered by my visit to the site. Maybe to reset my PW effectively, I need to use the link in the email. So I did and reset my password a second time. I immediately got another email from Adobe telling me to reset my password.
This death loop has continued until this very day, when I went mad.
After thrashing about Adobe.com for quite some while and finding no FAQ or other tech support on PW resets, I located a “Contact Us” option I could use for this issue. As I frittered away more time waiting for the Chat rep to respond, I decided to just cancel my account.
Canceling my account took quite awhile. And… less than 5 minutes after the Chat rep told me my account had been canceled and signed off, I got an email from Adobe saying my account had NOT been canceled.
My account had not been canceled, Adobe said, because if I canceled my account I would not be able to use my account.
I sit here in awe.
I got multiple account password resets too.
The tweet mentioned in the 10/5 4:35 update is now deleted.
Sounds like a planted backdoor. Auchhhh
From Adobe forum:
What information exactly did the attacker gain access to?
http://helpx.adobe.com/x-productkb/policy-pricing/customer-alert.html
Our investigation currently indicates that the attackers accessed Adobe customer IDs and encrypted passwords on our systems. We also believe the attackers removed from our systems certain information relating to 2.9 million Adobe customers, including customer names, encrypted credit or debit card numbers, expiration dates, and other information relating to customer orders. At this time, we do not believe the attackers removed decrypted credit or debit card numbers from our systems.
We are also investigating the illegal access to source code of numerous Adobe products. Based on our findings to date, we are not aware of any specific increased risk to customers as a result of this incident.
What is Adobe doing in response?
As a precaution, we are resetting relevant customer passwords to help prevent unauthorized access to Adobe ID accounts. Customers whose user ID and password were involved will receive an email notification from Adobe with information on how to change their password. We also recommend that customers change their passwords on any website where they may have used the same user ID and password.
We are in the process of notifying customers whose credit or debit card information we believe to be involved in the incident. Customers whose credit or debit card information was involved will receive a notification letter from us with additional information on steps they can take to help protect themselves against potential misuse of personal information about them. We have also notified the banks processing customer payments for Adobe, so that they can work with the payment card companies and card-issuing banks to help protect customers’ accounts.
U.S. only: Adobe is also offering customers, whose credit or debit card information was involved, the option of enrolling in a one-year complimentary credit monitoring membership.
We continue to work diligently internally, as well as with external partners, to address the incident. We have contacted federal law enforcement and are assisting in their investigation.
————————————————————–
I just finally got my notifier to today.
http://www.pcworld.com/article/2054160/adobes-source-code-was-parked-on-hackers-unprotected-server.html
Adobe’s source code was parked on hackers’ unprotected server
Excerpt:
Case in point: A massive breach of Adobe Systems’ network was discovered after the source code of numerous products, including the Web application development platform ColdFusion, sat parked on a hacker’s unprotected Web server open to the Internet.
The breach, which also encompassed 2.9 million encrypted customer credit card records, was announced by Adobe on Oct. 3. Adobe had already been investigating a breach when Alex Holden, chief information security officer of Hold Security, independently found what turned out to be the company’s source code on a hacking gang’s server.
Adobe’s source code “was hidden, but it was not cleverly hidden,” Holden said.
Source code could make it easier for hackers to find vulnerabilities in Adobe’s products, Holden said. But so far, no new zero-day vulnerabilities—the term for a vulnerability that is already being exploited but doesn’t have a patch—have surfaced in the last couple of months since the source code was taken, Holden said. So far, the source code has not been publicly released.
(snip)
“Have surfaced”. I have one that I would like explored by others more knowledgeable. Adobe allows for editing files remotely. If you have the source code, I would assume you can edit a file others created.
Like I said in my first post on this thread, court docketing systems used Adobe PDF. Therefore, if someone logs into PACER, can someone edit the files on the docket? Like Judge’s orders or opposition’s motions?
Thanks.
Oh goody. I got a coupon from Adobe for a discount on the licensed software; but no offers of ID protection. I find that presumptuous.