The same miscreants responsible for breaking into the networks of America’s top consumer and business data brokers appear to have also infiltrated and stolen huge amounts of data from the National White Collar Crime Center (NW3C), a congressionally-funded non-profit organization that provides training, investigative support and research to agencies and entities involved in the prevention, investigation and prosecution of cybercrime.
Last week, KrebsOnSecurity reported that entrepreneurs behind the underground criminal identity theft service ssndob[dot]ms also were responsible for operating a small but powerful collection of hacked computers exclusively at top data brokers, including LexisNexis, Dun & Bradstreet and HireRight/Kroll. A closer analysis of the Web server used to control that collection of hacked PCs shows that the attackers also had at least one infected system for several months this summer inside of the NW3c.
Core to the NW3C’s mission is its Investigative Support division, which according to the organization’s site “provides timely, relevant and effective services to member agencies involved in the prevention, investigation and prosecution of economic and high-tech crimes. The section has no investigative authority but can provide analytical assistance and perform public database searches.”
The NW3C said its analysts are frequently called upon to assist in establishing financial transaction patterns, developing possible links between criminal targets and associated criminal activity and providing link charts, timelines and graphs for court presentations. “Information obtained through public database searches can assist investigations by locating suspects, establishing property ownership and finding hidden assets, just to name a few of the benefits,” the organization’s Web site explains.
The NW3C also works with the Federal Bureau of Investigation (FBI) to run the Internet Crime Complaint Center (IC3), which accepts online Internet crime complaints from victims of cybercrime.
Neither the NW3C nor the IC3 responded to requests for comment on this story. FBI Spokeswoman Lindsay Godwin would say only that the FBI was “looking into it,” but declined to elaborate further, citing the ongoing nature of the investigation.
THE CRIME MACHINE
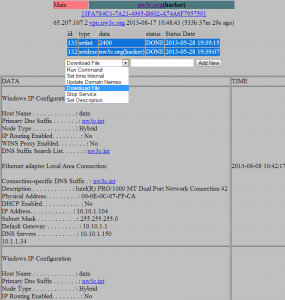
A number of indicators suggest that the attackers first gained access to the NW3C’s internal network on or around May 28, 2013. According to records in the online communications panel that the miscreants used to control their network of hacked systems, the affected NW3C server was taken offline on or around Aug. 17, 2013, indicating that the organization’s networks were compromised for approximately 11 weeks this summer. It’s not clear at this point why the miscreants marked this organization’s listing with a “(hacker)” designation, as shown in the snapshot of their botnet control panel below.
The attackers appear to have compromised a public-facing server at NW3C that was designed to handle incoming virtual private network (VPN) communications. Organizations frequently set up VPNs so that their remote employees can create an encrypted communications tunnel back to an otherwise closed network, and these setups are an integral component of most modern business applications.
Alarmingly, the machine name of the compromised NW3C system was “data.” On May 28, 2013, the attackers uploaded a file — nbc.exe — designed to open up an encrypted tunnel of communications from the hacked VPN server to their botnet controller on the public Internet. This appears to be the same nbc.exe file that was found on the two hacked servers at LexisNexis.
Abundant evidence left behind by the attackers suggests that they broke into the NW3C using a Web-based attack tool that focuses on exploiting recently-patched weaknesses in servers powered by ColdFusion, a Web application platform owned by Adobe Systems. I managed to get hold of the multiple exploits used in the attack server, and shared them with Adobe and with Rob Brooks-Bilson, a ColdFusion expert and author of the O’Reilly books Programming ColdFusion MX and Programming ColdFusion.
Although some of the exploits were listed as “0day” in the attack tool — suggesting they were zero-day, unpatched vulnerabilities in Adobe ColdFusion — Bilson said all of the exploits appear to attack vulnerabilities that are fixed in the most recent versions of ColdFusion. For example, three of the four exploits seems to have involved CVE-2013-0632, a vulnerability that Adobe first patched in January 2013, not long after the flaw was first spotted in actual zero-day online attacks. The remaining exploit in the attack kit targets a bug that Adobe fixed in 2010.
“The big issue with ColdFusion is that so many people install and set it up without following any of Adobe’s hardening guidelines,” Brooks-Bilson said in an email to KrebsOnSecurity. “Most of the exploits that have come out in the recent past have all worked via a similar mechanism that is easily mitigated by following Adobe’s guide. Of course, so many people disregard that advice and end up with servers that are easily compromised.”
STEALING DATA ON VICTIMS AND FELLOW CROOKS ALIKE
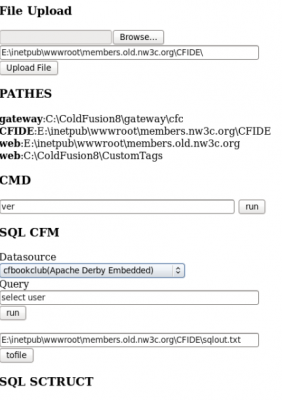
The ColdFusion exploit server contains plenty of records indicating that the attackers in this case plundered many of the databases that they were able to access while inside of NW3C. Part of the reason for the persistence of this evidence has to do with the way that the attackers queried local databases and offloaded stolen data. It appears that once inside the NW3C’s network, the bad guys quickly scanned all of the organization’s systems for security vulnerabilities and database servers. They also uploaded a Web-based “shell” which let them gain remote access to the hacked server via a Web browser.
The attack server and shell also let the attackers execute system commands on the compromised hosts, which appear to be Microsoft IIS servers. Their method also left a detailed (if not complete) log of many of their activities inside the network. One of the first things the attackers did upon compromising the “Data” server on the network was run a query that forced the local database to dump a copy of itself to a file — including a list of the authorized users and passwords — that the attackers could download.
The bad guys in this case also appear to have used their access to the NW3C to steal 10 years’ worth of consumer complaint information from the Internet Crime Complaint Center (IC3), the aforementioned partnership between the NW3C and the FBI that tracks complaints about cybercrime.
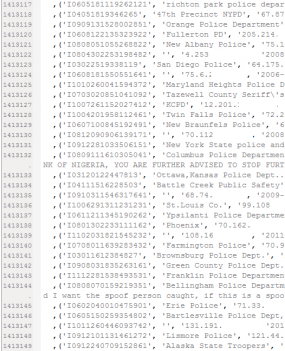
Present on the attacker’s server are some 2.659 million records apparently lifted from the IC3. The records range in date from about the time of the IC3’s inception — May 8, 2000 — to Jan. 22, 2013.
It’s not clear if the stolen IC3 data set includes all of the consumer complaints ever filed, but it seems likely that the archive is lacking just the past few months of records. In a report released earlier this year, the IC3 said it was receiving about 24,000 complaints per month, and that consumers had filed 289,874 complaints last year. The IC3’s site doesn’t maintain annual complaint numbers prior to 2003, but according to the site some 2.35 million have been filed with the system since then. To put the year-over-year growth in complaints in perspective, the IC3 said it wasn’t until 2007 — nearly seven years after its birth — that the organization received its millionth complaint.
Many of the more recent complaints involve ransomware, a threat that holds computers hostage in a bid to frighten users into paying a ransom to regain control over their PCs. Ironically, ransomware attacks most often spoof the FBI, and state that the user was caught downloading child pornography or pirated content.
The following is an example of one such complaint, slightly redacted, taken directly from the stolen IC3 database. I liked this complaint because the person who filed it acknowledges up front that he was browsing porn when he got hit with the ransomware attack, and that his wife was the one who saved him from his own ignorance:
(‘I1211100143194982’, ‘Kernersville Police Dept.’, ‘174.98.xxx.xxx’, ‘2012-11-10 01:43:19’, ‘2012-11-10 01:47:01’, ‘I was on an adult website (I don\’t know which one) when suddenly a screen popped up that had the FBI logo at the top and all this information about my having violated copyright laws or child pornography laws and my computer had been locked by the FBI and if I didn’t pay a $300 fine within 72 hours by MoneyPak a criminal charge would automatically be filed and I would go to prison for 2 to 12 years. It said once I paid the money my computer would be released within 1 to 4 hours and it listed where I could go to purchase a MoneyPak card and then how to put the MoneyPak into the computer for payment. It said if there were any problems to email fine@fbi.gov. I left to go buy this MoneyPak card and while gone my wife started looking carefully at this warning. When I returned she said she believed this was a scam and she wanted to turn my computer off, not give them any money and contact the FBI for confirmation, which we proceeded to do. First she tried the email address and it came back undeliverable. She then went on her computer and went on the FBI website and looked up scams and found the Citidel scam which fit the profile almost exactly. We have left my computer turned off, will contact my bank ASAP and will get our IT man in to try and remove this malware as soon as possible. We don\’t have any paperwork as we couldn’t print the site but we will see if our IT guy can get anything of value to help you identify these perpetrators. We should be able to get our money back for the MoneyPak so we probably won’t be out any money but it sure was scary. I knew I hadn’t done anything wrong but the site itself is very scary. Most people would pay up and if not for my wife, so would I.’, ‘5’, ”,”
DEEPER ACCESS
The stolen IC3 data indicate that the attackers sought to grab and offload all of the data they could access, but the IC3 database itself isn’t particularly useful, except perhaps for spamming and phishing. Other database queries show the attackers had access to systems at NW3C that could look up records which appear to be related to ongoing criminal and possibly civil cases. Some of the more interesting data headers in the information returned by those requests include;
-ACCURINT – A LexisNexis tool designed to “assist law enforcement officials in identifying people and their assets, address, relatives, and business associates by providing instant access to a comprehensive database of public records that would ordinarily take days to collect.”
-AMCRIN – Information from Amcrin Corp., a company best known for its CrimeDex networked database of criminals.
-ASSIGNED TO / HANDLED BY – Ostensibly the law enforcement officer and/or agency tracking the case.
-CHOICEPOINT – A legacy entry from the now-defunct data aggregator that was purchased by LexisNexis in 2008.
-DOB (Date of Birth)
-NICB – Most likely short for the National Insurance Crime Bureau, a non-profit member organization created by the insurance industry to address insurance-related crime, and one that works closely with law enforcement agencies.
-RISS – Regional Information Sharing Systems is an information-sharing program funded by the U.S. Federal government whose purpose is to connect databases from local and regional law enforcement so that they can use each other’s data for criminal investigations. (Update: A representative from RISS responded to this article in a comment below).
-“TLO” – TLO Online Investigative Systems is a data broker that caters to lawyers, private investigators, law enforcement and insurance firms. The company also sells, among other things services, locational information on license plates that have been filmed and identified.
-SSN (Social Security Number)
Alex Holden and his security consulting firm Hold Security LLC were instrumental in identifying and analyzing the attack server. Holden said that if the attackers had at least 11 weeks to access systems within the NW3C, they probably already have all of the data of consequence that could be gained from internal systems there.
“Based on sophistication of these guys, the custom tools they were using and the length of time they had to look around, it is unlikely that they walked away without whatever they were after,” Holden said. “Did they get 100 percent of it? Probably not. But from what I’ve seen of how these guys operate, they didn’t just plant their flag and leave. They were methodically exploiting systems and access to gain access to all of the data they could get their hands on.”
Holden added that while some of the information stolen from the NW3C may not be particularly useful for traditional cybercriminal purposes, that data may be of more interest to foreign governments. He noted that one of the more interesting lookups the attackers ran instructed the NW3C’s database to produce a list of foreign law enforcement agents who were working active criminal cases with the organization. Other queries forced the database to dump information from the law enforcement agents acting in a supervisory role at the NW3C.
“Other entities that might be interested in this data include foreign governments,” Holden said. “These guys may also be passing or selling this data off to other nations as well.”
Stay tuned for Part III and IV of this investigative series.





It is far worse than that, we set up the “Enterprise Organization” and stuck pigs in the system, only to find the pigs got stuck and blew everything up, so now our data services are designed to be disposed of, and we had to put Jill Kelley in to finish them off! Clarence said to. [Clearance]
“Most people would pay up and if not for my wife, so would I.”
He married well.
She didn’t. 🙂
Just goes to show that a little awareness (and a lot of skepticism) goes a long way.
Wouldn’t make a blanket statement on the condition of their marriage though.
Anyone unaware could’ve fallen prey.
He married well not only because she was smart enough to figure out it was a scam but also because apparently, she condones his consumption of porn. 🙂
Now that means, if IC3 reports were made, the person making the reports can be exposed to whomever the reports were made about? Isn’t that dangerous depending on what the reports were?
Ya, and not only that its exposed agents working in other countries, which is extremely dangerous for them I’d imagine.
Lets hope the trend of recognition continues to spread. It makes people aware, and opens those eyes to what is important on the war between miscreants and the IT industry. Brian’s blog was listed on csoonline;
September 27, 2013— CSO— The reported hack of major consumer and business data aggregators has intensified doubts of the reliability of knowledge-based authentication widely used in the financial services industry, analysts say.
The computer systems of LexisNexis, Dun & Bradstreet and Kroll Background America were hacked by an underground identity theft service that sells social security numbers, birth records, credit and background reports on millions of Americans, Brian Krebs, a former Washington Post reporter and author of the KrebsonSecurity blog reported on Wednesday. Krebs uncovered the hack following a seven-month investigation of the criminal site ssndob[dot]ms.
Being in Information Assurance, let me tell you, its not easy trying to keep up with daily tasks, let alone trying to indentify and thwart attacks an potential pre and post attacks.
There are devices out there that will assist an organization and show data to people who will monitor them. They can even be displayed on a big screen TV so within the masses maybe some one will point to it and go OMG! we’re under attack ! Simply put the POC info on the screen and its a done deal.
Not so fast. many cannot interpret the complicated ways of attacks. We are fortunate – so far – that many attacks aren’t being hidden. The attacks are typically logged, but once they are in, they don’t want you to see that. So, they may use some sort of encryption or other methods to keep the IT people guessing. You have to dig into logs and look for activity to locations that your systems have no business talking to.
The networks on many businesses are a convenience for many. They surf as they wish, and it only takes one of them to get infected before that bot starts scanning the network for other vulnerable machines. From there the network slows down, and things go amuck. By then, its usually too late – if the crooks wanted something off your server, it is usually carried off your server withing hours to days of the infection/ intrusion.
The only effective way to thwart whats happening in the world of evil activity is to build yourself a timeline to touch something important each day. It doesn’t have to take hours – looking at a IPS or IIS log can be daunting, but getting a low cost log aggregation system like what GFI offers will condense the mayhem into something that makes sense and can be monitored by alot of people.
You have to start somewhere, and when it comes to information assurance, its best to start at the ground level and work yourself up to an effective security posture.
Barbara Plunkett is always saying we just have to assume we are hacked now, and its more about detection rather then prevention I guess.
She says there is 1 million viruses made every month! Every month? And on top of that they stay in the wild only a short time, so chances are we never catch it. That makes me feel like virus scanners are just completely useless nowadays.
I think the NSA is looking for a commerical partner to make special smartphones for their employees. She says they need to be using them, but smartphones cannot be trusted. I guess they will make something similar to how they hardened Obama’s Ipad.
Another real interesting article.
You mention RISS.NET and ACCURINT? Where they compromised also?
I have no indications that they were. What I believe happened is the guys at NW3C had access to information that was drawn from those different databases, and therefore the hackers who broke in had the same access to those records.
As you may know RISS.NET contains a lot of Criminal Records including arrest..WOW.
The Regional Information Sharing Systems® (RISS) became aware of your blog post on October 1, 2013 and would like to clarify some important and relevant points:
The only connectivity between NW3C and RISS’ secure Law Enforcement Cloud called RISSNET™ is through a secure VPN which can only be initiated by the RISS security appliance that protects RISSNET. When a RISS user accesses the NW3C website, the email address of the user is the only information that is sent about the user to the NW3C servers. The word “RISS” is also part of the header.
Because transactions on RISSNET cannot be initiated from NW3C, the only way any resources located on RISSNET could be accessed inappropriately would be through imitating a valid RISSNET user and attempting to logon directly to RISSNET.
Since only a RISSNET user’s email address could have been obtained from the compromised NW3C servers, it is unlikely that an unauthorized access to RISSNET could be gained using the information available from the reportedly compromised servers. Though unlikely, out of an abundance of caution, RISS technical staff has identified a relatively small number of RISSNET user accounts that have accessed NW3C during the period of exposure (May 28, 2013 to August 17, 2013, according to the article).
Analysis of the RISSNET logon activity of each of these users indicates that no illegitimate successful logons were accomplished on RISSNET during the period of exposure. RISS has also disabled the VPN between RISS and NW3C until further notice.
Thanks for the comment, Julie. It’s nice to know RISS is taking this seriously.
Thanks Brian.
So if a authorized users pc compromised and login is captured, you don’t think it can be compromised? And people wonder why so many hacks happen, idiots in the government and the contractors supporting them!
Looks like the links to the last two queries are mixed up (notunited.txt and supervisors.txt).
Thanks, Guus. Fixed that.
Brian some how (? ) you can always get your nose in thing not many people know about .And there you are again . As far as . know there is only one place on earth you could get this sort of information and its not in NSA headquarters 🙂 .
Im starting to become confused Brian
About whats going on inside
Im not sure what to believe
Is it truth or is it lies
I feel like you don’t trust me
You never tell me a thing
It hurts so much inside
I don’t think i can win
What makes me upset
Is you don’t see the pain in my heart
Just because you don’t trust me
I’m starting to fall apart
P.s The worst part about being lied to is knowing that you weren’t worth the truth.
hahaha
This is pretty crazy though if they now know what hackers are being investigated. What a blow to the FBI.
Why are they always getting hacked so dam much? They have all this data on us and it seems that its easy for hackers to take it. Almost seems like a common thing.
I always joke with people about other websites, that if the FBI can’t even protect their data how we can expect anyone else to?
You have an error in the following excerpt.
“-NICB – Most likely short for the National Crime Insurance Bureau, a non-profit member organization created by the insurance industry to address insurance-related crime, and one that works closely with law enforcement agencies.”
It should be “National Insurance Crime Bureau” not “National Crime Insurance Bureau”.
thanks
Any chance you have a malware report on this ?
No, but it’s very likely to have been the same malware used in the attacks against LexisNexis, Dun & Bradstreet and Kroll. And in that writeup, I did include VT and ThreatExpert analysis links
http://krebsonsecurity.com/2013/09/data-broker-giants-hacked-by-id-theft-service/
OK thanks Brian. I am sure that if VT and Threat expert did not pick this up to begin with it must employ some level of encryption or obfuscation.
I worked in their it group years back. I wasn’t involved in their public facing website. But, their “management” was a collection of “good ole boys” who had little tolerance for those that did not have a military or law enforcement background. They drove away their top performing developers and analysts.
Such a shame when you think of what this organization could have been, with the talent it once had.
That can be said about any workplace and “cronyism”… I’m a black guy, from DC in Minnesota (but I’m making it work)… so yeah, I hear you.
Tim,
Having been there with you, you said it all. If you weren’t part of the good-ole-boy law enforcement network, you were crap. They would never listen to any of us IT folks and they certainly did not have a clue.
“The big issue with ColdFusion is that so many people install and set it up without following any of Adobe’s hardening guidelines,” Brooks-Bilson said in an email to KrebsOnSecurity. “… Of course, so many people disregard that advice and end up with servers that are easily compromised.”
In my opinion, the companies that sell the software which needs to be patched or hardened have an obligation to pro-actively contact every single customer and ensure/verify that the guidelines are implemented. It is obviously not enough to only make the information available and expect the customers to comply. I can hear the objections, but if I were running Adobe, it would be The Right Thing to do.
Well said, if Adobe would buy Java from Oracle it could easily take every position in a top 5 of most vulnerable applications. And will keep this dubious honor month after month after month. The only danger to their position would come from Microsoft.
Really strange why all this data has been left publicly accessible ? Cannot Police just have their own VPN network.
What’s up to all, since I am truly keen of reading this web site’s post
to be updated regularly. It includes nice stuff.
Related? Source of ‘fullz’?
http://www.justice.gov/opa/pr/2013/October/13-crm-1116.html
Excerpt: “The indictment alleges that Ngo operated one or more online marketplaces for various carding activities, known as carder forums, where he stored and offered for sale “fullz” and other PII, including “fullz” of individuals located in the District of New Hampshire.”