The breach at Target Corp. that exposed credit card and personal data on more than 110 million consumers appears to have begun with a malware-laced email phishing attack sent to employees at an HVAC firm that did business with the nationwide retailer, according to sources close to the investigation.
 Last week, KrebsOnSecurity reported that investigators believe the source of the Target intrusion traces back to network credentials that Target had issued to Fazio Mechanical, a heating, air conditioning and refrigeration firm in Sharpsburg, Pa. Multiple sources close to the investigation now tell this reporter that those credentials were stolen in an email malware attack at Fazio that began at least two months before thieves started stealing card data from thousands of Target cash registers.
Last week, KrebsOnSecurity reported that investigators believe the source of the Target intrusion traces back to network credentials that Target had issued to Fazio Mechanical, a heating, air conditioning and refrigeration firm in Sharpsburg, Pa. Multiple sources close to the investigation now tell this reporter that those credentials were stolen in an email malware attack at Fazio that began at least two months before thieves started stealing card data from thousands of Target cash registers.
Two of those sources said the malware in question was Citadel — a password-stealing bot program that is a derivative of the ZeuS banking trojan — but that information could not be confirmed. Through a PR firm, Fazio declined to answer direct questions for this story, and Target has declined to comment, citing an active investigation.
In a statement (PDF) issued last week, Fazio said it was “the victim of a sophisticated cyber attack operation,” and further that “our IT system and security measures are in full compliance with industry practices.”
There is no question that, like Target, Fazio Mechanical was the victim of cybercrime. But investigators close to the case took issue with Fazio’s claim that it was in full compliance with industry practices, and offered another explanation of why it took the Fazio so long to detect the email malware infection: The company’s primary method of detecting malicious software on its internal systems was the free version of Malwarebytes Anti-Malware.
To be clear, Malwarebytes Anti-Malware (MBAM) free is quite good at what it’s designed to do – scan for and eliminate threats from host machines. However, there are two problems with an organization relying solely on the free version of MBAM for anti-malware protection: Firstly, the free version is an on-demand scanner that does not offer real-time protection against threats (the Pro version of MBAM does include a real-time protection component). Secondly, the free version is made explicitly for individual users and its license prohibits corporate use.
Fazio’s statement also clarified that its data connection to Target was exclusively for electronic billing, contract submission and project management. The company did not specify which component(s) of Target’s online operations that Fazio accessed externally, but a former employee at Target said nearly all Target contractors access an external billing system called Ariba, as well as a Target project management and contract submissions portal called Partners Online. The source said Fazio also would have had access to Target’s Property Development Zone portal.
According to a former member of Target’s security team who asked not to be identified, when a work order for an external vendor is created, the payment is collected through the Ariba system: Vendors log into Ariba, complete the necessary steps to close out the work order and they are later paid. But how would the attackers have moved from Target’s external billing system into an internal portion of the network occupied by point-of-sale devices? The former Target network expert has a theory:
“I know that the Ariba system has a back end that Target administrators use to maintain the system and provide vendors with login credentials, [and] I would have to speculate that once a vendor logs into the portal they have active access to the server that runs the application,” the source said. “Most, if not almost all, internal applications at Target used Active Directory (AD) credentials and I’m sure the Ariba system was no exception. I wouldn’t say the vendor had AD credentials but that the internal administrators would use their AD login to access the system from inside. This would mean the sever had access to the rest of the corporate network in some form or another.”
Last week’s story about Fazio’s role in the attack on Target mentioned that Target could be facing steep fines if it was discovered that the company was not in compliance with payment card industry (PCI) security standards. Among those is a requirement that merchants incorporate two-factor authentication for remote network access originating from outside the network by personnel and all third parties.
Another source who managed Target vendors for a number of years until quite recently said that only “in rare cases” would Target have required a vendor to use a one-time token or other two-factor authentication approach.
“Only the vendors in the highest security group — those required to directly access confidential information — would be given a token, and instructions on how to access that portion of the network,” the source said, speaking on condition of anonymity. “Target would have paid very little attention to vendors like Fazio, and I would be surprised if there was ever even a basic security assessment done of those types of vendors by Target.”
But according to Avivah Litan, a fraud analyst at Gartner, Target wouldn’t have needed to require vendors to use two-factor logins if the company believed it had taken steps to isolate the vendor portals from its payment network.
“In fairness to Target, if they thought their network was properly segmented, they wouldn’t have needed to have two-factor access for everyone,” Litan said. “But if someone got in there and somehow escalated their Active Directory privileges like you described, that might have [bridged] that segmentation.”
OPEN-SOURCE INTEL
Many readers have questioned why the attackers would have picked on an HVAC firm as a conduit for hacking Target. The answer is that they probably didn’t, at least at first. Many of these email malware attacks start with shotgun attacks that blast out email far and wide; only after the attackers have had time to comb through the victim list for interesting targets do they begin to separate the wheat from the chaff.
But Target may have inadvertently made it easier for the attackers in this case, in part by leaving massive amounts of internal documentation for vendors on its various public-facing Web properties that do not require a login. Indeed, many of these documents would be a potential gold mine of information for an attacker.
Here’s an example that just happens to be somewhat specific to HVAC vendors: A simple Google search turns up Target’s Supplier Portal, which includes a wealth of information for new and existing vendors and suppliers about how to interact with the company, submit invoices, etc. That page leads to a separate page of information on Target Facilities Management, which includes a slew of instructions on submitting work orders. That page also includes a link to another set of resources: A Supplier Downloads page that, oddly enough, is little more than a long list of resources for HVAC & refrigeration companies.
What could an attacker learn from this information? For starters, download any of the Microsoft Excel files listed at that page. Then scan the file with a free online service (like this one) that extracts metadata from submitted files. Scanning the file “FM_HVAC_Oct_2011_Summary.xlsx” from the Supplier Downloads Page, for example, tells us that the file was created in June 2011 with a copy of Microsoft Office 2007 licensed to Target Corp. That metadata also indicates the file was created or last edited by a person with the Windows username “Daleso.Yadetta,” and that it was most recently printed to a system on Target’s network in the following Windows domain: “\\TCMPSPRINT04P\”
Getting the layout of the various Windows domains within Target’s internal network would certainly help the attackers focus their attention. For example, consider what we know about a key piece of the malware known to have been used in the Target intrusion, first referenced in a story on Jan. 15, 2014. Investigators who examined the malware quickly noticed that it was designed to move data stolen from Target’s (then malware-infected) cash registers to a central collection point on Target’s network, a Windows domain called “\\TTCOPSCLI3ACS\”.
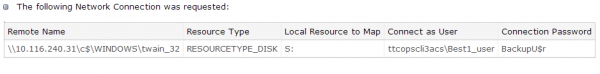
Investigators believe “ttcopscli3acs” wass the name of the Windows domain used by the POS malware planted at Target stores.
A little Googling shows that Target operates two data centers, both in Minnesota: Target Technology Center — or “TTC” for short — is located in Brooklyn Park, Minn. on one of the company’s corporate campuses. The company also operates a redundant data center — Target Technology Center Elk River (TTCE) in Elk River, Minn. as a backup. It’s a good bet that the server referenced inside the malware used in the Target breach resided within the company’s Brooklyn Park facility.




Guys,
Isn’t finger-pointing at Microsoft sort of like blaming it on sun spots? Microsoft is an embedded part of our landscape and unlikely to change. Do I like Microsoft? No, I think they are horribly misguided in customer focus at the IT level. They aren’t that great at the consumer level either. And their programming remains some of the sloppiest on the planet, short of java based coding.
But the complexity of the systems in play means a tight watchdog mentality. Target and their supplier failed miserably.
One of Target’s primary focuses are/were getting you through the cash register as fast as possible. It means hundreds of millions of dollars to them.
So is/was an encrypted POS system on their radar? Of course not. Slowing down the register clearance time would be a fundamental no/no from a marketing perspective and cost perspective. Loading more overhead for preventive systems would also not fly.
And here we are.
I have no doubt that the system expert that told them years ago to fix the POS software/hardware was written a nice check and told “thank you very much” and totally ignored. Target’s culture was as much to blame as anything. The customer experience is/was tantamount.
And yes, we flagged the small vendor relationship being far too open as a major flaw. I love efficiency (I have that tattooed on my left cheek) but in reality, non-essential (small) vendors still get paper checks for paper invoices, cost be damned. Letting everyone into your system for the sake of cost reduction (or worse, green initiatives) is the height of incompetence. And if downstream audits aren’t performed, shame on Target. I hate that consumers and banks got damaged because of this, but Target got what they deserved. And they will get what they deserve going forward.
This isn’t the government’s ACA website that has to be wide open to everyone on the planet. Of course, that leads to a different discussion for a different day.
> Isn’t finger-pointing at Microsoft sort of like blaming it on sun spots?
I like your comparison. We should all keep in mind that Target shareholders are a victim of this crime. Maybe the long arm of the law might apprehend at least some of the bad guys who did this.
Having acknowledged Target as a victim does remove Target’s responsibility to follow best practices. If you don’t lock your car and somebody steals your wallet out of the glove box, (1) you were careless, and (2) the wallet thief still committed a crime.
For people in smaller (and larger) organizations reading these comments, here are some easy and low cost precautions you can take to help level the playing field against the bad guys:
http://www.infrasupport.com/what-should-a-small-business-it-security-system-look-like/
– Greg
Greg,
Good reminder about best practices for small business systems. Target take note….
The wifi one is the hottest button. Too many ways in. So you compartmentalize it so if it gets compromised, you flush it. Oh the wailing…. Not having access to internal systems, website customer facing apps, etc.
Nice to be the owner, so I just glare at them…. Security has it’s limits…
Would this be a good place to plug the firewalls I build?
I told this story before but it’s a good one. A few years ago, a friend who likes cigars called me and asked me to clean a virus from the PC at a cigar store. So I drove over there and, sure enough, that PC was a mess. I talked to the owner and she was adamant, they never visited any compromised websites and were extra careful with that PC because it had all the software they used to operate the store. How did it get infected?
Then she told me customers come in and get on their wifi and out to the Internet. That was when I noticed there were no network wires connecting this store PC. The one they used for all their store operations.
You already know the rest of the story – that PC shared the same wifi with customers and an infected customer system probably nailed this one in the store. I offered to make her network right, with a customer wifi and secure internal wifi, all separated by VLANs and meeting at the firewall. She called her partner and they turned me down flat. Just another con-man selling gloom and doom.
I told her I wasn’t willing to invest hours of my time to clean her computer if she was unwilling to invest anything in her own security and then I left. I don’t like cigars anyway.
– Greg
Robert,
I agree with the sentiment that the cracker, not Target, is to blame but the reality is that Target signed a contract with VISA/MC guarenteeing them that they would use best practices for security, including yearly audits.
I have done one of these payment processing things before, about a year ago with a local organization that was applying to handle FHA loan approvals. The banks and government were on their necks to prove their network was secure, so I came in and did up a security report for them – and I covered everything including all of the stuff they would need their internal HR department to have their employees sign.
It took them about 3 months to get all the recommendations implemented and ultimately what ended up happening was the bank required them to get yet another auditing firm to audit them a second time. I was happy to get some atta-boys from that firm as later they told me that they were compliant with just about everything that firm recommended – and they were approved and so on and are handling the processing today, as far as I know.
The thing is that if you start digging you will find lots and lots of documentation out there about how the banks and payment processors and governments want you to setup your payment processing. Those guys create stacks of reports and paperwork but you do have to spend a lot of time digging it out. And you have to understand security and think like a cracker to apply the materials to whatever business is involved.
So really there was no excuse for this breach other than lack of incentive among exec staff at Target to emphasize security. I am sure Target will try using every excuse in the book when the VISA/MC lawyers and banks come calling for their money, but the VISA/MC and banks have been doing PCI compliance for a while now and they have all the holes covered, none of the attempts to blame the crackers are going to work. Target is going to get a real wakeup call, that is for sure.
+1
Ted,
I’m unclear exactly what I said that precipitated the thought that I don’t blame Target or their management. I fully hold them responsible. FCRA and PCI DSS, and a dozen other best practices guidelines squarely place the responsibility of providing a secure system in which to transmit data and process payments on the company. But policy, not procedures is ultimately what will be judged by a governing body or court. It’s the intent not the tactics. At least in assessing criminal intent and governmental rule violations.
Don’t forget about the core processors in the back office and their role as a 3rd party to “watchdog”. That’s why I love the financial reg side of the business: You guys actually created standards for everyone to live by and become certified. Unlike HIPAA/HITECH (at least the OCR enforced side, CMMS side has a bit more structure) which is where I am currently spending my days and nights.
I’m not sure we know enough yet to even start with blame assignment. Management gets reamed no matter what happens. That’s why they carry D&O insurance; they know they have a target on their back. (excuse the pun)
The lawyers and the government are now really driving this processes. Their responsibility to our society is to assess the damage and try to make it right (restitution) so all our/your hard work really gets trash canned, since it won’t matter what’s factual, it only matters what can be proven in a court of law, both judicial and public opinion, as the intent of Target and their 3rd parties (Policy) and then the attest (what they promised would be done.) Audit will take a back seat to the discovery phase of the lawsuits in trying to find more why than what. And of course assessing blame.
Remember BP?
Ultimately, it boils down to two basic concepts:
1. The truth lies somewhere in the middle.
2. Follow the money to the deepest pockets.
Number 2 supersedes Number 1 when the lawyers get involved.
I fully expect this never to see the inside of a courtroom, unless the US AG sinks his teeth into it for political reasons. I also fully expect Target to drag this out as long as possible, in the hopes of not having the Activist Eric Holder be that AG, since he will be working the angle of a disproportionate amount of pain on minorities. Cha-ching!
Facts and reality will get lost in the politics, sadly. No matter how much I may agree on your assertion of reality. I am process managment guy, so you know I love the process and controlling/improving/measuring the process.
But political surreality will take care over eventually.
If we treated air plane crashes like this, I would be petrified to fly in a plane. Somebody made a suggestion about an NTSB-type processes for IT breaches. I think in a system breakdown of this size, having a scientifically lead process rather than legal would serve us all better. Much better to have visibility, than sealed court documents after years of legal wrangling.
My two cents. Or 36 dollars and change. I drink Dos Equis. Stay thirsty, my friends…
Hi Robert,
Mainly I wanted to draw a distinction between the legal responsibility (which is Target) and the actual responsbility – which I regard as belonging to all of the vendors that put the Target POS system together for them. Those vendors will escape liability, as software vendors always do, while continuing to advertise and sell “secure” systems.
Today, if a dairy sells a gallon of lowfat ice cream that says “healthy” on it to the grocer and the grocer sells it to you, and you get sick because the dairy made a mistake, then the dairy is liable.
But, today if a software vendor sells a POS system to Target that says “secure” on it’s marketing literature, and Target gets cracked into because the POS vendor left a bug in the system, then the software vendor is NOT liable.
Yet, the software vendor gets a whole lot more money for their product than the dairy gets for the ice cream.
This is my complaint about the entire system. Until we start holding software vendors to the same standards of truthful marketing that we hold dairies, then we are going to continue to have breaches like this Target breach. Holding Target responsible does nothing, because the people who created the hole (the POS contractor) and the people who enabled the creation of that hole, are not going to pay as a result of this breach.
Hypothetically, if the POS software vendor was liable for holes, do you think they would continue to use Windows as a platform for their product?
I met with my local FBI contact a few days ago and, while they would not confirm or deny this, the 2 page NCIJTF memo is likely in regards to the Neiman Marcus breach rather than Target’s breach.
Pretty funny all this and it’s blamed on a free version of malwarebytes…however the pro version cannot be loaded on servers… it reeks havoc on windows server 2003 and greater, on pc’s it works great.
Ted,
Thanks for all the insights, we are taking the information and incorporating it into our guide sheets. We are also thinking about making a giant sign that reminds everyone about email security. I know someone said no one does email training, mark us down as the first then. Ted is so right about getting the staff to be your sniffers. Sure, you get some false positives, but you also get that big bad boy that would of knocked your system around for days.
Do you know if Cisco firewalls incorporate graphing or is this a data file to dump into excel on an hourly basis?
The other giant poster going up in IT is :
An ounce of prevention is worth a pound of cure….
Some things remain timeless…
Graphing, I use a free software called MRTG it does SNMP queries on switches and firewalls and such it pulls the MIB-II interface stats. Good early warning software and it runs on
windows, just load the free active perl. There is a better more complex software called RRD or even better and more complex is Nagios. Go to nagios.com for the commercial version and nagios.org for the free one.
You can also get netflow data from Cisco ASA firewalls but be warned since Cisco heavily modified the netflow data format for the ASA firewall. One tool that does understand the Cisco-modified format is ManageEngine’s Netflow Analyzer. That one is a free download and runs as the full product for 30 days then reverts to a stripped down free product. Or you can get the Cisco tools for manging the ASA but they are more expensive. I don’t know if Nagios has a plugin that understands the Cisco ASA version of netflow but I would guess the commercial salesguys would be more than happy to answer that question.
MRTG will get you 80% of the way to what Nagios will do and it takes maybe 4 hours for a newbie to understand it, set it up and get it running. To get the remaining 20% all the way there with Nagios is weeks of effort, but in a large enterprise that’s what you do.
But even a small 5 PC office with a single little Linksys router and an 8 port managed ethernet switch and a Windows 2003 server can take advantage of MRTG
Ted,
Thanks for the information. We are on Cisco ASA firewalls (as newbies) and it was a painful learning curve, but we are happy, given Cisco’s (so far) excellent but expensive support, and the real time monitoring by the mothership.
We started to use Sonicwall, but at the time, Dell was in the process of buying them and it seemed very chaotic to deal with, and support wasn’t transferred.
We are starting to build our black network and will have to decide one way or the other as we rip away the secure programs.
Of course, no system is truly black. Ask the Iranians… 🙂
Are you running the intrusion prevention system on the ASA? Cause otherwise all the ASA is, is a glorified router running NAT.
I’ve sold and managed ASAs for years, but I use other devices behind them for URL & virus scanning. The Sophos appliance is pretty good as are some others. The main thing the ASA has going for it is the name ‘Firewall” Given a choice I’d much prefer using something like a Cisco 1900 or 2900 as a NAT device or VPN/NAT router, and put an application scanner behind it. It just gives you a lot more flexibility to be able to initiate a SSH or Telnet session from the router prompt. These days the crackers get in through Phishing and bad URL’s and a nat device does practically nothing to secure a network anymore. And anyway, NAT is going to be going bye bye pretty soon with IPv6 coming in.
Hi Ted,
The IPS portion of the ASA is up. It was a bear to get “trained” though. It assumes the worst, so a lot of traffic had to be filtered at first. 1 1/2 years later, it’s better behaved.
LOL IPv6. I get the dirtiest stares from my IT guy when I tell him this is coming. Just from a layman’s standpoint, it seems like a nice step up and an absolute necessary step up if we are to support a growing internet and interworld, but it means all legacy systems have to go bye bye that don’t support it, though everything I can find so far in the shop, with the exception of two older servers, does support it. I haven’t had time to see if a NIC retro is all that is necessary, but I suspect not, since the packet sizes at 9K need a total rethink for efficiency. I am glad we recently reworked with Cat6, though.
I’ve got Dale working on the data bridges for the graphs, thanks so much for the software freebie ideas. We have to deal with old and tricky data sets from incoming data files for processing all the time, but I was not looking forward to yet another head scratching session to figure out Cisco’s data language. It seems so unnecessary to do that You have to pay a lot of money to make your system less open? I’m sure its a revenue making machine for them, since small shops will just hire a Cisco certified guy to do the work. We tend to rail against non-open platforms.
And that brings us back around to our Windows subject. The basic question is: If not Windows then what? The world isn’t going to go Mac crazy just for an operating system, or that would have happened over 20 years ago. Unix based systems are great for servers, but lousy for user facing work. I started on Unix based systems (remember Xenix?) so long ago I can’t remember when I did and loved the stability, speed, and programming cleanliness. We had servers in the 90’s that would stay up for months if we wanted them to without a reset.
I think economics is the key driver here. A competing system could be developed, but at what price point? Linux is almost free for the software, but then you are compelled to design your own system/architecture/database and support it. There goes the economics.
Windows Server, up until 2012 has really laid some eggs. I think 2012 finally is a good product, but only because they went back to “old school” for much of the management, simplifying the operating system and lowering the overhead. Sort of NT on steroids. So maybe Windows is finally getting their cranium out of their anus…. there have been lesser miracles.
On Target, we still have much to learn, I think, before we really know what went on. I do agree that legal and actual responsibility can be worlds apart. The software suppliers have shielded themselves for decades behind pages of legal hoops (independent or contract software developers don’t get that privilege most of the time. Sort of strange.) and while yes, margins between the two are quite different, the software company knows that one software catastrophe puts them out of business, and it can impact millions of other users who have nothing to do with the issue. And there is no insurance for it. Public legal liability doesn’t normally put you out of business, because it can be mitigated by risk management (insurance, partial self insurance, pools, etc.) They aren’t quite the same.
Don’t feel too bad for the dairy producers. They are for the most part large agribusiness, just as ruthless as any industry. The FDA also plays a huge role in trying to assure food product safety (and you can’t sue the FDA, at least not yet) and when it fails, people can die.
No one dies normally from a system breach, except for some executives that might commit suicide over it, should their professional lives come to an end of this.
I may be reading too much between the lines, but all business executives are not evil or calcified in their decision making/listening. American business, as a whole, would not be what it is today if that were true. We would have long ago had another labor revolution if that were the case, and as far as the eye can see, labor organization is in a free-fall.
For all it’s problems and non-capitalist restrictions, the American business engine is still the best in the world. And America is still a place thousands of people every week risk their lives to come to. It is in definite need of an overall, as does our political system, but even considering the constraints, America Works….
(stepping off of soapbox and taking fork full of apple pie from mouth)
> Linux is almost free for the software, but then you are compelled
> to design your own system/architecture/database and support
> it. There goes the economics.
Who do people keep claiming that Linux means you’re on your own for support? Red Hat generates more than $1 billion annually from support subscriptions. I’ve used Red Hat support at all hours of the day and night for critical projects.
Cisco wants you to believe it’s the only game in town and many organizations buy that cool-aid. This is a shame and a testimony to the power of marketing. There are plenty of other ways to do your IDS and traffic monitoring independent of Cisco.
“…The basic question is: If not Windows then what? The world isn’t going to go Mac crazy just for an operating system, or that would have happened over 20 years ago. Unix based systems are great for servers, but lousy for user facing work…”
For starters you can’t separate MacOS X from Apple hardware. Years ago when Steve Jobs was out of the picture at Apple, Apple was headed the direction of allowing clone hardware and just selling software, much like Microsoft. But, Jobs made a famous tradeoff when Apple hired him back – which sacrificed Apples ability to ever pwn the desktop software market, by killing all the Mac cloners.
Today there’s probably 10 times the number of Ubuntu Linux desktops in service than there are MacOS X. Apple’s never going to let go of the Mac since it would be a huge blow to company pride, but clearly their future is NOT in desktop systems and everyone knows it.
Now as for Unix systems being lousy for user work – just ask all the people who have tossed Windows laptops in favor of Android tablets about that one. If the assertion that Unix was lousy for desktop work was true Microsoft wouldn’t have come out with Windows 8 to try to knock Android back.
Besides that, it’s a spurious argument anyway as Linux can be apped and themed to look like Windows 7 or Windows 8 + MS Office installed. With a little work you can get 80% of the way there, enough to drop a user in front of without training. The fact of it is that there’s a larger jump from Windows 7 interface to Windows 8 interface than there is from Windows 7 to Ubuntu’s default interface.
The other (inconvenient to the MS advocates) fact is that outside of the United States, Windows isn’t nearly as popular, and Mac’s are practically nonexistent. In some parts of the world the world HAS in fact embraced something else. Don’t fall into the trap of being US-centric.
If your running an organization that is actually at the point where you can restrict your users from having local administration rights over their PCs then you are at the point that you could deploy Ubuntu. Yes the screen would look a little different but user training could overcome that. And actually, there are X window managers that look identical to Windows desktops. I am frankly amazed that call centers and other businesses that pay employees to do data processing aren’t already doing that. After all your employees are being paid to take phone calls and pound data into input forms screens, they aren’t being paid to download screensavers and change desktop themes.
The way I see it is that Linux can easily move into the low-end. A couple weeks ago I was at a McDonalds with one of those 4-monitor game consoles. Something had gone wrong with it, and it was stuck at a Linux boot prompt. That’s where I see Linux really useful. Move it into there, into running kiosks and stuff like that, first. Then into places like POS systems were the people are running cash registers all day. You can still use Windows in the back office if you want, but for purpose-built terminals, that people are not going to run Word and Excel on, why on Earth would you use Windows? If Target had Linux POS systems would it have been cracked?
As for server 2012, my experience with it is it works OK on brand new server hardware, but don’t try upgrading something like a rack of HP Proliant DL 380 G4s from Server 2008 R2 or you’ll be sorry.
And as for America being the place thousands of people come to, if you subtraact political & economic immigration, that isn’t actually true. There’s not tons of Japanese and Canadians and Austrailians and Britons all fighting to get in here. To a Mexican the choice of living in a country with no jobs vs living illegally in a country with jobs is a no-brainer, same went for Vietnamese boat people, but there are actually lots of quite nice places in the world to live that look pretty much like the United States, except maybe a bit cleaner. Japan, for example, if you can get beyond the language and the toilets that have more controls on them than a jet airplane, it’s a pretty nice country. The US could learn a lot from many other countries, actually.
This blog post, “How to spot a phishy email” might also be helpful. Should be required reading for everyone who uses email.
http://www.infrasupport.com/how-to-spot-a-phishy-email/
As for graphing – I’m with Ted in the MRTG camp. You can also run it on a spare PC loaded up with your favorite flavor of Linux. Put 2 NICs in the box and set it up as a bridge. Then you can use it for all kinds of diagnostic work.
Me, again. Sorry to keep butting-into what is obviously a very professional discussion, but I’m learning more here than I have in 15 years on the interwebs.
I run a one-man show as a sports photographer, so no Big Company to worry about. But with gazillions of photos in various storage mediums, some online, I am concerned about security.
Which brings me to a novice question. I currently store all my passwords in the Notes app on my phone. Bad idea? I have a feeling the answer will be yes.
Re: Chuck –
>I currently store all my passwords in the Notes app on my
> phone. Bad idea? I have a feeling the answer will be yes.
That Notes app with all your passwords – it’s all local inside your phone right? What happens if your phone is stolen? Even if those passwords are inside some cloud service somewhere, your phone probably has the password.
One quick story – years ago, I parked my car and climbed out to run into a customer site and do some work. My cell phone fell out of its holder on the pavement in front of the car. I discovered the phone was missing off my belt maybe 60-120 seconds after I walked in the building. I ran out but the phone was already long gone and somebody was already making calls on it and burning up my minutes. This was before the days of smartphones.
I cancelled the phone and replaced it, so this didn’t cost a fortune. But the whole thing was scary.
– Greg
Chuck, do yourself a favor and download the free app “password safe” There’s a smartphone app and a windows app and linux app and so on and on for it. Put all your passwords in that app, then the app has you put a password on it. Then if you lose your phone no big deal. And the file format that the passwords are stored in is the same as the desktop app uses.
Bad idea, but passwords will always have problems. First: Make sure you use your phone’s encryption and lock-out mechanisms properly; this is always a good first step. Next, get something like KeePass or another secure password container program. This is far from perfect and is still able to be ‘broken’ but you will be better off than just using your phone’s note taking application. When you do this make sure you pick a strong password to be the one password you MUST remember. You can always hide this on a piece of paper and put it inside of some place secure in your home where nobody would look, just in case you made it “too” secure, until you have it well memorized. Generally it is bad idea to keep passwords on pieces of paper but a separation and lack of reference and sufficient hiding should be OK for a short period of time. Better than a bad password.
Thanks Ted,Greg and Voks for tbe tips.
Almost all of my passwords are made from a dozen or so chunks that I combine in various ways. On paper I keep clues to each chunk and the way the chunks are combined. The clues are cryptic. A thief would see something like . Probably excessive, but it’s actually pretty easy to implement and maintain.
would see something like fc-ob (prior post used greater and less symbols, duh)
Brian, I am now awaiting moderation for my FIRST comment and my ONLY article load today. 🙁
Greg,
I always try to take responsibility for my words. Ted was compelling me to come up with a way to contend with a Microsoft-less world (I enjoy the mental exercise of contemplating that…) and one way is to use Linux.
But you would be required to build your own world, so to speak. Yes, Linix supports it’s operating system and at a very reasonable cost. But what resides on the operating system and the programs to interact would have to be built to replace the millions of applications already on Microsoft. I don’t think anyone would content just plopping my database on Linux is going to work. (Ted certainly wasn’t) So I would have to build my own support for that. Not to mention retraining everyone.
Rest assured we love Linux. It gets to play more in cloud based applications and the hardware to support it, than middle-ware applications. We tend to think that we are slaves to Microsoft, but in reality we are slaves to whatever the programmers use. If someone would like to lead a software revolution away from Microsoft, I’m all for it. But no one can or will spend huge dollars for that.
Other than maybe Target…. 🙂 Hey, there may be their legal defense…. Build a new POS on Linux… It would certainly support their speedy customer experience mandate from marketing.
A company the size of Target can go to any POS vendor and tell them “jump” and they will say “how high” If Target wanted a POS system on Linux a vendor would build it for them.
One of the biggest PC based POS systems used to be Counterpoint. 100% Linux. Then they came out with a very crummy Windows version that was a kind of port of the Linux version. It was not well received. Counterpoint ended up collapsing and NCR bought them and is busily working on killing the product. When you ask NCR about POS they sell you hardware cash registers.
You say you have to build your world but we have to do that with Windows also. And you say there’s millions of apps on Microsoft well no customer is going to buy all of them – all a small customer cares about is what is the platform the apps they need run on, and all a large customer cares about is how do I want to arrainge my IT infrastructure so that my users can’t stick their fingers in it and wreck it, and so that it helps them to do their job – not to listen to downloaded mp3s or whatever else they do on their home PC – just so that they use it to do what I am paying them to do.
As for being slaves – only small customers are slaves to programmers. Large customers who DEFINE THEIR NEEDS SPECIFICALLY are in control of the programmers. They have the money, the programmers want that money to eat, the programmers do it THEIR way, not the programmers way, to get that money.
This is as much about a generational shift in the computer business I think. Right now the CEO’s of companies mostly grew up before computers, so when the IT people came along and told them “your going to do it this way” the CEO’s let the IT people dictate terms because they had no idea how exactly the new technology would help them.
Now however more and more CEO’s are younger and they are saying “hey, I want to run my business a particular way, I’m going to tell IT either they create the system I want or I’ll fire them and find someone else”
You want someone to lead a revolution but it just isn’t going to work that way. 30 years ago when the CEO’s thought a computer was a misspelling of the word calculator, that was the time for people to lead revolutions. We had Gates and Jobs and McNealy and Gerstner, Jr all those other giants. That is because the public knew nothing about computers and they wanted to be led.
But today, no one person leads. Quick, name the CEO’s of Microsoft and Apple – I’ll bet you can’t without looking them up. No more than you can name the CEO’s of Target and Walmart or the CEO of ABC, NBC or CBS. The computer industry has matured. And the only way a mature industry survives is by following the customer.
We have exchanged a handful of leaders for millions of little tiny leaders – the consumers. Just like the automotive industry did when Henry Ford died, just like the electrical industry did when Westinghouse and Edison left the field. Just like the oil industry did. And so on and so on.
And the customers are out there buying tablets, last I looked. Android tablets, not Windows tablets.
It will be the industry workers, the system admins, computer consultants, and so on – who are going to have the hardest time of it, I think. Just like has happened in most other businesses. A lot of us got in when we were regarded as Gods. Today, not so much anymore I think.
When you buy a car today, do you ask a mechanic what car you should buy? No. You might ask him if the car you have decided to buy is a good one – but your mechanic isn’t in the drivers seat. And why should your computer consultant be dictating what you should buy? Your mechanic doesen’t.
Ted and others,
Wow, such hatred for Microsoft. Why? We’ve been using their stuff for 30 years, as an industry. And yeah, we hate parts of it/most of it/all of it.
But IT is no different than any other part of business. If there is a pervasive reason to do so, companies switch to the most advantageous. This gives them, at least for a while, technological advantage.
So why haven’t these systems been moved to UNIX? Why are there still AS-400 boxes running? And probably a few System 38’s.
I started in UNIX, have had UNIX servers. But in the 1990’s we were forced to switch. The software companies wrote for the platform. And they couldn’t write for two platforms in most cases. (Yes, Unix can simulate Windows, but don’t you create overhead and services that must be maintained? Basically you create your own Windows. Why do that? Just to escape Microsoft?)
Other countries have had the luxury of starting their systems after the Windows revolution. They can make the analysis of what is best for their business model. And if they don’t choose Windows so be it. That’s good business.
I repeat. If someone wants to lead the post-Windows revolution, give me a system that makes sense for business reasons. Change for the sake of change is never a good reason. Make it a pervasive reason, and the world will flock to you. Just as someone pointed out about non-American platforms (I apologize for being so American providential. It is all I know.)
But Ted you are wrong about immigration. There are hundred’s of thousands of worker permits issued or renewed every year. And they are Canadians, Indian, European, Malaysian, Etc. Oracle couldn’t run if you stopped all the programmer integration to this country. Microsoft either.
But it is also people escaping political, economic, and social destitution around the world that makes it a flood to this better place. Of all descents.
This is who we are and have been over 200 years. Is it in need of improvement? By all means. I don’t know how HLS does their job with the porous boarder we have and the lax attitude toward proof of citizenship and boarder enforcement. And no one should feel good about citizenship annexation, as proposed. It still should be a controlled process of immigration and a privilege to be a citizen of ANY country, not a right. Everything else is still a privilege that can be lost, by your own actions or the actions of others. Should be the Bill of Privileges as a Citizen. Rights tend to become entitlements. Whether we are talking about guns or voting.
(Now waving flag and eating apple pie on a Chevy Truck singing God Bless America. In Mandarin…)
Wow, such hatred for non-Microsoft. Why?
Come on Robert, that’s a straw man argument right out of the Microsoft palybook. You don’ t like our stuff – must be because you hate us for non-technical reasons. Never because our stuff isn’t as good as the stuff from the other guy.
“..If there is a pervasive reason to do so, companies switch to the most advantageous…”
Wrong. Companies switch for many reasons other than that. What technological advantage does Windows 8 + Office 2013 have over Windows 7 + Office 2010? None that I have seen with any of my customers. In fact it decreases productivity for a while until they get used to the change. Than later productivity is the same as it was before.
“…So why haven’t these systems been moved to UNIX? Why are there still AS-400 boxes running? And probably a few System 38′s….”
I would say, why haven’t the AS400’s been switched to Windows? It’s the same question with the same answer. The answer is that it’s working and MANY people do indeed ignore the marketing BS and use what works. Just like many people will still be running Windows XP for the rest of this year and maybe longer.
“…I started in UNIX, have had UNIX servers. But in the 1990′s we were forced to switch. The software companies wrote for the platform….”
No, what happened was that this was an era where the UNIX software companies had very high margins, expensive support contracts, etc. And some other newer software companies who had nothing, no customers, saw an opportunity to edge in by selling crummy software for cheap. Since there’s always some customers willing to risk saving money for possibly poorer products that might work OK enough to do the job, those software companies got a foothold.
Fast forward and now the Windows software companies are the ones with very high margins, expensive support contracts, etc. And the Linux people are the New Kids on the Block doing to Microsoft the same thing that Microsoft did to Solaris and Netware years ago. Except that unlike the old UNIX software companies of your youth, Microsoft isn’t stupid enough to not learn from it’s own roots – and is doing what it can to try to close the openings for people to fly under their radar. But, the only thing that Microsoft could REALLY do is drastically drop it’s prices – if they sold Windows Desktop at $10 a copy, and Window Server for 50 a copy, Linux would be dead. And they ARE doing that in China, by the way, because what keeps them awake at nights is the fear of Linux in China.
“…And they couldn’t write for two platforms in most cases….”
That is marketing BS out of Apple, Micosoft & Sun’s playbook – even today, some of the Linux proponents are stupid enough to say that stuff that runs on Linux (like this blog we are using) can’t be ported as well to Windows.
“…Basically you create your own Windows. Why do that? Just to escape Microsoft?…”
No, to create viable competition. Competition makes products better. We have none in the US desktop software market, this is a statement of fact from the DoJ Microsoft monopoly lawsuit. That’s the main reason Microsoft software products like Windows are totally crappy. Products of theirs like the Xbox that have viable competition are far, far better.
“…Change for the sake of change is never a good reason….”
Nobody who switched to Windows 8 from Windows 7 can say that without being a hypocrite. Don’t know if you are one of those people but the statement is ofen used by people fighting Linux and Unix who don’t apply it to Microsoft’s so-called “upgrades”
I am just saying, if you can justify switching to Windows 8 from Windows 7 you can justfiy switching from XP to Linux for the same reasons.
@Ted Mittelstaedt February 25, 2014 at 1:32 pm: “if [Microsoft] sold Windows Desktop at $10 a copy, and Window Server for 50 a copy, Linux would be dead.”
Really? I’m not a sysadmin (except for my own boxes–just a 24/7 desktop+cluster linux user), but my impression is that admins who deploy linux do so mostly because it’s both simultaneously more secure *and* more efficient *and* more convenient to work with, not for price.
Regarding the desktop, my question is, can’t pretty much anyone who *really* wants a “free windows” get one? And isn’t the question mostly moot anyway, because most consumer hardware comes pre-bundled with Micro$oft? And aren’t people who choose to run windows over linux virtually all people who
* place no value on security
* are smiles-n-thumbs-up for NSA backdoors
* think “package management” is done by UPS and FedEx
? ICBW–haven’t been a fulltime windows user for a decade–but my impression is that the linux-vs-windows decision isn’t made mostly by price, but by knowledge and inertia.
Big businesses save millions if not billions on large scale Linux deployments. Microsoft talks a good game about the cost of Linux being equivalent to Windows once you spend the extra time learning how to deploy Linux but that’s mainly window dressing because it is only applicable to small businesses that don’t have a dedicated IT person. Sure, if you own a 3 person business and you are your own system admin, to you the tasks of system administration are probably as welcome as getting a tooth pulled, or getting your car tuned up since they detract from your main business that makes money, whatever that is. So the “we save u time” argument will reasonate with you.
But it’s different with larger businesses that have dedicated system admins.
If you have 1000 Kiosk computers that will be running a web browser to pound data into a database (or get it out of a database) your admin may take a week to learn how to build a Linux kiosk system to work vs a day to learn how to build a Windows kiosk.
But, once he learns how to do it in both instances, you save $50,000 on the Windows volume licenses for those kiosks. Plenty of money to pay your admin how to “do Linux” or better yet hire another admin who isn’t such a stick in the mud and already knows Linux.
Seriously! How can someone working in the computer industry today justify NOT learning something about an operating system that is completely free and will run on any old PC they have laying around? What’s a brand new PC at Fry’s cost on sale, anyway? Couple hundred bucks. I would expect any system admin I hire to be buying a new machine every couple years FOR THEIR PERSONAL USE. They should have their older systems lying around.
Anyway, Puppet Labs makes millions building software that will do large scale Linux deployments. I don’t use their stuff because I don’t own a large scale Linux deployment but someone is, and whoever is, is paying them big bucks. That wouldn’t be happening if businesses wern’t saving millions and millions on Windows licensing by replacing it with Linux.
Re: Robert –
> If someone would like to lead a software revolution away from
> Microsoft, I’m all for it. But no one can or will spend huge
> dollars for that.
There are ways to do it without spending a fortune. But it’s an evolution, not a revolution, so it doesn’t create any tension in the board room.
Take a page from Microsoft’s own “embrace and extend” playbook. Protect a LAN segment filled with flaky Windows POS systems with a Linux firewall, for example. Or maybe virtualize Windows Servers and put in a bunch of firewall rules in the hypervisors to protect the server(s). Red Hat offers an enterprise class environment called RHEV that does everything you expect from a virtualization environment at a fraction of the cost. Maybe use the virtualization environment for all the clustering and failover and then save a fortune by going to SQL Server Standard instead of Enterprise.
So you keep the same databases and legacy environment everyone is used to and surround it with newer stuff to protect it. And then gradually over time, change out the legacy stuff as newer and better apps come along.
– Greg
+1
Thanks for the +1. In a shameless plug that will help buy some groceries, if you want me to build something like this for you, get in touch with me here:
http://www.infrasupport.com/contact-us/
– Greg
Ok, so I am missing something. From the article…
“Most, if not almost all, internal applications at Target used Active Directory (AD) credentials and I’m sure the Ariba system was no exception. I wouldn’t say the vendor had AD credentials but that the internal administrators would use their AD login to access the system from inside. This would mean the sever had access to the rest of the corporate network in some form or another.”
and then…
“In fairness to Target, if they thought their network was properly segmented, they wouldn’t have needed to have two-factor access for everyone,” Litan said. “But if someone got in there and somehow escalated their Active Directory privileges like you described, that might have [bridged] that segmentation.”
How does someone’s AD privileges get escalated like this? Since the malware bot in question only resides on the users at Fazio’s PC to access Target the only privilege that the bot could have would be the Fazio’s user privilege.
While I can see that the Fazio user’s account @ Target would be known, I don’t see how the AD permissions could be elevated. There has to be more to it than this.
I also would like to know about technique by which AD privilege could be elevated. I suspect the exploit was enabled by AD misconfiguration or too much privilege, not an issue with how AD works.
Casey,
Our first gut question when this all broke: How did they do this without inside help?
Maybe your point begs re-asking the question?
We are asked to believe that some anonymous group breaches the number two retailer’s IT site, goes undetected for weeks/months, and slithers out the back door without a trace.
Or that it was carefully executed with inside help.
Which one fits scientific methodology?
Its easy to tell when a user privilege is elevated in AD, and who did it. If there was an inside person that did it, s/he should be getting out of the country already.
There are plenty of cases where breaches happen without inside help. That’s neither proven nor dis-proven (at least publicly) in this case.
I think it was probably a user that had too high a priority (very high as a matter of fact).
I was also thinking that if the networks were properly segmented the PCI/POS portion should not have been reachable by the non-PCI/non-POS portion but I have to revise that based on if the malware could have been installed on the billing server by the Fazio user account and captured login information.
#1 is a much more sound conclusion.
Look at it this way. This is a standard risk/reward scenario that is adequately explained by games theory.
If the Target system admin works like crazy to be the best security expert on the planet – spends all his free time reading about security, doesen’t have time for a wife and kid, basically works 16 hours a day on probes and attack scenarios on his network to discover holes – what does he get out of it? Does he get a bonus for preventing an attack? No. Let’s say he makes $100K and works at Target 5 years, thats about $250K by the time the govenment has taken out taxes. Also, if there is an attack what does he suffer? Well, basically nothing. The worst will be he will be fired and when he goes to the next job his new employer will likely not care. In short, he has minimal buy-in.
Now look at it from the crackers point of view. If the cracker is unable to penetrate, he has spent weeks or may be months of effort attacking Target and not gotten paid a cent, he has spent years learning how to attack these installations and not gotten paid a cent. Maybe in the Target scenario he has spent 16 hours a day for 5 years learning abut Target and trying to penetrate Target.
But, if he succeeds what then? Maybe several million dollars of stolen money goes straight into his pocket. (by the time he is paid from laundering the card #s) He has maximal buy-in.
In short the reward for the crminal activity is far, far greater than the reward for just doing your job at Target or even being a total star at Target.
Target (and other) CEO’s could only change this if they gave buy-in to the system admin. Not the CIO (who doesen’t touch the technology) or the upper mangers, but buyin to the actual grunt who touches the hardware. And that is a complete anathema to the corporate big business culture in America – which is to give buy-in to the people in the organization who are furthest away from the actual work being done.
This is why you don’t read about these kind of breaks for small enterprises, in those setups the owner is likely doing the configuration of the POS terminal so they have buy-in to make sure something like this does not happen.
The reason a lot of people would like very much to believe there was inside help is because it would justify not giving the grunts buy-in. They would say “the grunts are going to screw you anyway so why give them stock options” They would say the grunts don’t deserve it becuase they don’t bear responsibility. In other words it preserves the big business notion that the people at the top who are farthest away from the customers, deserve the most money for “leading” and other unspecified things.
Is the current CEO of Microsoft a “vision guy” who was pulled in from CocaCola after Ballmer was tossed out of the company? Or was he a guy who actually had his hands in the guts of the technology?
Think about it.
There is a feasible scenario where this happens without inside help. Poor practices yes, but deliberate inside theft? Not necessarily.
We read in a Krebs on Security post the bad guys made their actual entry via a Target website. And now we know they owned a Fazio PC that used Target A/D credentials to login to a payment system of some kind. I believe we also read here that Target used either factory default or easy to guess passwords for its POS terminals
And anyone in any IT department knows the mantra today is do more with less. Imagine the temptation while putting together a new project, say a credit card loyalty program, to cut a few security corners. After all, the stuff is all behind a firewall, right? The project will be operational in, say, September in plenty of time for Christmas by cutting a corners, otherwise it won’t be ready until, say, January. And it will cost more. You’re the Target CFO. You have shareholders who want to see ROI all the time – do you vote for January with security “bells and whistles” or functional in Septembe in time for Christmas?
You can see the conversations unfold in board rooms and conference rooms everywhere. Those IT guys speak a different language, they’re not tuned in to our business needs, they only want to play with technology, blah blah blah.
So the Target internal systems go into production with glaring holes nobody cares about. It’s not inside theft, its inside recklessness due to a culture that dictates do more with less.
So given what we know and some educated guesses, what if . . .
What if that web server were in the same segment as the POS terminals? That’s too wild and reckless – but what if the web server was able to access some other server in common with the POS terminals? That feels more feasible.
So then, using the web server as a jumping off point, how about logging into it using the Fazio credentials? Say with RDP? From here, start your probes and map out the Target internal network.
Find a database server that looks promising. Log into it with those same Fazio credentials. And from here find paydirt – 300,000 POS terminals around the world, all with the same easy to guess login credentials. Now you can insert your POS stealing program. And you can find some other internal servers to use as ftp jumping-off points. All you need is an ftp client, installed by default on all Windows systems.
And viola – steal 40 million credit card numbers. This is all pure speculation.
– Greg
Greg,
I like your methodology here. From many angles this does make sense. It’s still the vastness of it all, I believe this is the current record holder, that bends my incredulity meter. Your scenerio, which I can warm up to, still has a window of weeks or months. Nordstrom is talking 7 months. This is bigger. You have to fall asleep at the wheel for a long time.
Ted and I are going round and round, but he challenged me to think like a cracker. If I’m a cracker, I will work years, risk possible detection, and still might come away with zero? Except for the thrill of it all, it can’t be. If I am a smart cracker, I have an insurance policy. That’s collusion or blackmail. In a group that size, especially if what you are saying is true, I can find someone to compromise.
Other random thoughts related to this. The crackers are savvy enough on the marketing side not to flood the market. Taking a page out of the narcotics trade, they keep supply and demand as stable as possible. Not sure Arthur Laffer would like us using the Laffer curve on narcotics, but it certainly works well in an almost pure form of capitalism. There is a sweet spot for all the players involved.
But huge variables. The deterioration rate of market share and margins is highly volatile. You might get 10% or 20% of your haul out and have it collapse. The credit card system is pretty slow to get these numbers out of the system (If I were them, I’d buy them on the open market and destroy their value out of the gate, as a defensive measure. You kill the value in the first 3 million. Of course, it’s a fragmented business with little cooperation currently. And you have to make some “special friends.” But in the face of billions in losses, maybe money well spent.) but I suspect they will get much better.
So you hedge your bet with an insider. I would of course say that is also risky, since it means a potential whistle blower.
I guess I started this mess, but I did so trying to figure out which made more sense. Greg, I think you changed my mind. I like your analysis.
But Ted, having a management hating IT guy in every IT center in the country should make them prime targets for cracker friendship, shouldn’t it? 🙂
Just kidding, Ted. I feel your pain….
“Find a database server that looks promising. Log into it with those same Fazio credentials”
Certainly that sounds plausible. And most certainly that is how other hacks have been done. However, that’s not the same as having an AD userid privilege escalated. Just seems strange to me that 2 sources in the post mentioned that as a possibility. I have never heard that being done (other than by a “rogue” admin)
Well, we’re all speculating. You don’t need any special privileges to probe. What does AD privilege escalation even mean anyway? How many of us automatically make “Domain Users” a member of the local administrators group when we join workstations to a domain?
Here it is 2 months after the initial reports and we’re all still speculating on what happened. I hope Target publishes a step by step sequence of events on this soon.
http://www.infrasupport.com/target-get-on-the-ball-with-this-data-breach/
– Greg
Greg: is there anything, besides ethics, that would compel Target to fully disclose exactly what happened? Could they hide behind some sort of “we don’t want to say which exact doors we left open and give others ideas” defense?
Hi Chuck – I read about every fact I know about this whole thing right here in this blog. I don’t even know anyone who works at Target. So my opinion is probably not worth the disk space to store the words.
But I’ll share it anyway.
Yes, there is something besides ethics that could compel Target to fully disclose what happened. If a good portion of those 40 million customers were to tell Target they want Target to come clean, Target would listen. Otherwise, Target could probably hide behind that excuse.
Readers and commenters in this blog may have some influence too. I wonder what would happen if, say, the Minneapolis Star Tribune and St. Paul Pioneer Press were to be bombarded with letters to the editor demanding Target come clean? Or if some major shareholders were to be persuaded that coming clean would enhance shareholder value by disarming more lawsuits?
So it could happen.
– Greg
Greg: Thanks for the feedback. I may be able to push the issue a bit at Examiner.com, where I do some writing and photo assignments.
While the Target story will be a bit of a stretch from my usual gig, doing action sports photography and reporting on the America’s Cup, they may allow me to publish something on the sibject of how much Target is going to share about the details of the breach.
If I use any material from this blog and comments, I’ll get permission from everyone first of course, and either use names or amonymous quotes, whichever you’re comfortable with. The article will link back here, with the blogger’s permission.
At the very least, it may offer a slight prod aimed towards Target, especialy if Google News picks up the article, which they often do, as long as we have fewer than one typo per sentence. Examiner.com has a roller-coaster-ish reputation as a media outlet, but it often produces some decent stuff.
Anyway, just a thought. If anyone wants to contact me about the plan, either for or against, my email is: chuck@2007ac.com.
Speaking of typos, I noticed a few in my previou comments. Large thumbs is my excuse.
Well, this morning’s analysis brings a little more insight into Target’s risk management.
They reported a $44 million insurance company payment as partial offset to their initial 60$ million drip in the bucket for breach costs. I am sure this will start ramping up quarter by quarter and into the weaker quarters for the rest of the year.
Traffic was hit by the breach. Sales were down over 5%, which in retail is huge during the Christmas quarter. Target likely makes .30 on the dollar past initial break even, so roughly speaking a $1 billion dollar drop in sales costs them about $300 million.
Everyone is be very prolific on this site, so I won’t attempt to add to each. Enough to say that visibility cannot occur until the criminal investigation is complete. And if I am their legal counsel, less is more right now. I think visibility does help to heal, but Target should be afforded enough time to “know it’s future” with regard to litigation, restitution and government action.
The best news they may have right now is that there is a ground swell trying to have Eric Holder removed as US Attorney General. I think that would be in everyone’s best interest to occur and as quickly as possible.
I don’t get it – how does Eric Holder fit into this?
Greg,
Eric Holder is charged with prosecution of all government rules/laws surrounding PCI (Personal Credit Information), HITECH rules violations, and any other attached standards that are government based.
Mr Holder is one of the most activist AG’s in American history. There is no doubt, if still in office, he will also pursue this from a civil rights angle, that is his calling card, as well as the current administration’s. His angle will be that minorities were disproportionately impacted and that this must be remedied.
If Mr. Holder is impeached or resigns, then a new AG will have to be brought in under a more conservative congressional approval cycle and in an election year. With the current fervor over gay marriage (like we don’t have enough to deal with in this country, still trying to figure out why this has gotten so out of hand) and Mr. Holders apparent overstep, that is starting to look more likely. Not placing odds or anything, just saying in the last couple weeks, the heat is getting warmer.
It’s an interesting inner-connected world, isn’t it?
The situation is adequately covered by civil contract law. Target signed a merchant agreement and the banks will hang he/she/it out to dry on that. (since corporations are people use your term of choice to refer to the entity) This is why we have contract law in this country, to allow the civil court system to take care of these things. There’s no need for Holder to involve himself unless that process breaks down (and there’s no indication that it is)
And why your bringing gay marriage into this – oh wait, I know – that’s the real source of irritation with Holder.
Ted, there is no way this softball of a situation is going to be passed up by hundreds, maybe thousands, of individuals with legitimate and questionable lawsuits. Including Mr. Holder.
My gripe with Mr. Holder is that he is working diligently to extend Federal Powers in State’s rights areas. I don’t like his politics in everything from wiretapping to the IRS. I personally think he is a lousy AG in protecting the people. All the people.
If you are insinuating anything else, I would ask the moderator to address this. In nothing I wrote could anyone think I either approve or disapprove of gay marriage. I think all government is too deeply embedded in our lives. Not a bible thumper. Not a libertarian. Just think we focus too much in this country on the wrong things. Eric Holder I think tops that list.
And Eric Holder petitioning/demanding that State AG’s to ignore State law is or is bordering on an impeachable offense (You are asking a state elected official to practice dereliction of duty). It’s being reported that others feel the same way and are circulating a petition to have him impeached. (and it’s not the Tea Party or even the Republicans.)
And if he were gone, Target would have one less ax-grinder to worry about. That’s my point.
Fast & Furious was a bad plan gone totally wrong; and The AG lied about knowing or doing anything constructive about it. It doesn’t matter who dreamed up the stupid thing; it is how it was handled. There’s a reason he and David Axelrod almost went fist city in a Washington DC hallway, and it was over bad practices like this.
I just got no use for someone with no respect for the Bill of Rights, let alone state’s powers.
F&F was just another one of those “Set a thief to catch a thief” plans, and those plans are risky and sometimes do blow up. But sometimes they work. When F&F started under the prior AG, it did appear to be working and that guy didn’t stay around long enough for what he started in motion to blow up in his face (since his boss was at the end of hsi second term)
The same thing happens when people hire “ex-crackers” to vet their computer security systems. Personally, I have absolutely no use for these “reformed computer crackers” who hire out as “computer security experts” ; in my world, once a cracker, always a cracker.
Good post Ted! I guess I’m just too distrustful of those that want to point to a false allegation, that US gun dealers sell to cartel straw-men. If that is in fact going on, none of the guys I personally know down there is aware of it, although they’ve been approached by people they suspected of this. The problem there is, once again, were these government investigators or actual cartel straw men? There is just too much motivation by the left to show that we are the whole cause of the troubles in Mexico – when in fact all black market arms are known to come from Israel, Iran, and other GWOT countries, and Venezuela. I have the PDF of this report from the FBI and other agencies involved with global arms trafficking.
I just don’t trust this administration, or the Bureau, which has been staffed by Democratic party administrations for years now, and Bush was unwilling to fire them, as it would be seen as meddling with our Federal law enforcement.
I saw on the news today the Eric was sent home after having a heart attack at a meeting in DC. I wished I could hope him well, but I think the pressure is deserving.
“…there is no way this softball of a situation is going to be passed up by hundreds, maybe thousands, of individuals with legitimate and questionable lawsuits…”
When you get a credit card you sign away your right to sue someone like Target, in exchange for the card issuer compensting you if money is stolen out of your account. So there are not hundreds to thousands of individuals out there with the standing to sue Target. There are just a bunch of banks who had to pay out money to their card holders.
Even if there were thousands of people with standing to sue they would be put into a class action lawsuit.
The court system over the years has developed the class action lawsuit to prevent being swamped by ten thousand little Grandmas who got $150 stolen out of their card account and who all want their money back. There is really no other way to work things.
As for Holder, his “telling state AG’s to ignore the law”, if you have any examples NOT involving gay marriage, lets hear them. Otherwise, I’m just going to cut it short and say that from my POV, if the only thing you can come up with where Holder is telling people to ignore the law is related to gay marriage, then your a bigot and I’m not going to waste time trying to convince you otherwise.
As for the overall States Rights issues, it is ironic you bring that up when discussing the Target breech, as the Target breech is absolutely not a states rights issue. But, I will say this about states rights;
Every President since the Civil War has extended federal powers over states rights. I really don’t think there is much left of any States Rights, and in 2014, in the United States, it is very difficult to argue that there should be.
I personally have no use for States Rights. I’m a modern person who is a product of a modern US Society, I watch TV that’s produced in other states, wear clothes produced in other states, eat food produced in other states, shop at stores owned by companies based in other states. ALL other states – I probably have at least 1 item in my home that has been manufactured in one of every state in the Union.
The USA today is over 300 million AMERICANS. It’s not 38 million Californicans, 5 million Coloradoians, 26 million Texans, 20 million New Yorkians, etc. etc. etc. Today we do things TOGETHER as a NATION.
MY state didnt get a choice to go into Iraq, if it had, it would have NOT gone into Iraq and no Guard would have been sent there. It didn’t get a choice to set gasoline prices, set corn prices, and it wasn’t consulted about vehicle airbags. Nor was any other state in the Union. We just don’t do that anymore, and we haven’t since before YOU were ever born.
The States Rights ship sailed in 1861, and when I read or hear people saying States Rights to me what that sounds like is “go away I want to do something secret that most people would find disgraceful”
He doesen’t.
The tea baggers are convinced that Holder’s decision to not defend the Defense of Marriage act was what resulted in SCOTUS overturning it, and and to add insult to injury he has the audacity to encourage state AG’s to not defend their variants of DOMAs. They cannot forgive him for that so they are calling for his resignation over trumped up nonsense like Fast & Furious (ignoring of course that F&F got started under the Bush administration and Holder likely knew nothing about it until the program blew up)
Apparently they figure that the Target breach must have been aided by homosexuals working inside Target – after all Target is controlled by homosexuals, didn’t you know that, that’s why they have those big giant red balls in front of their stores.
I really fail to understand why people think that this breech fallout is going to involve anyone other than Target and VISA/Mastercard and the eventual class action that will be filed that will consolidate all of the banks currently suing Target. This matter is covered by contract law and nothing a court is going to do anywhere is going to successfully invalidate any of the contract provisions that Target was operating under to take credit cards. The banks are going to hang Target out to dry based on their merchant agreement and if you think the federal AG is going to have any power to change anythign in that, I have some beachfront property for sale in Florida real cheap!
Uhm… All this political stuff is great and I really really want to join in, but I have a hunch sooner or later Brian will want to nudge this discussion back on topic.
– Greg
Greg –
“You don’t need any special privileges to probe”
Actually, if you have secured your systems correctly, you do (or should).
“What does AD privilege escalation even mean anyway?”
That’s what I think I was trying to ask originally. I thought that there was some trick/hack/exploit that was out in the wild to allow this. The quotes in the original blog entry doesn’t go into any scenarios on how this could happen.
” How many of us automatically make “Domain Users” a member of the local administrators group when we join workstations to a domain?”
That would be a big No-No.
“I hope Target publishes a step by step sequence of events on this soon.”
So do I, but ‘soon’ is relative term. Bits of it will leak out, but we probably won’t know what really happened until criminal charges are filed and indictments are handed down (unless they are sealed of course)
All true. And had Target followed all these good security practices, none of us would be here talking about it.
Ya know – as long as we’re speculating – here’s a bizarre thought. I never realized, apparently nmap can compile under Windows. It just never dawned on me to even care about trying it under Windows.
What if…? Imagine gaining a beachhead on a Target Windows server and then downloading something like nmap and using that server to port-scan and characterize the entire network.
– Greg
Doesen’t everyone already do that to their own networks?
Where I used to work, they would have caught that (and stopped it) pretty quickly
If you prohibit your system admins from becoming familiar with the same software that the crackers use, why would you believe they would have the competence to be able to catch and stop those tools from being run on their network?
Kind of like telling a locksmith that he is prohibited from learning how lockpicks work!
Very, very misguided and backwards attitude!
“If you prohibit your system admins from becoming familiar with the same software that the crackers use, why would you believe they would have the competence to be able to catch and stop those tools from being run on their network?”
Sorry Ted, I must come from larger organizations. Sys Admins are not (and should not be) all-powerful. In fact. I DONT want the sys admins to be familiar with cracker software. It’s simply not their job. Where I work (and previous places I have worked) the company has a separate security group that is their job to police the network and servers for identification and nullification of threats
Really it comes down to a separation of duties. Different access levels for each group. Also, not every admin has an all-access pass to all servers (or for those that do, everything is logged and monitored). Some have admin access on servers A-K, others admin access on servers L-Z.
Similarly Security doesn’t have all-access to swtiches, routers, servers. Not their job to maintain those or get in there and poke around.
“Kind of like telling a locksmith that he is prohibited from learning how lockpicks work!”
Not really. I liken it more to a cashier at a store (let’s say Target), and the Loss Prevention team at the same store. The cashier CAN spot issues with theft in the store and report it to management/LP. But they aren’t charged with going around and watching people in the store to see what they are up to. That’s LP’s job. Similarly, while LP can have the cashier open up the cash drawer, they do it while the cashier (and a manager/supervisor is watching).
“Very, very misguided and backwards attitude!”
Your opinion has been noted.
Actually I HAVE worked for (and with) that large of an organizations and in all cases so far they have been organized into different business units that each had their own IT groups. And yeah I know that some people would wax eloquently about how much money you would save by combining all of those groups into 1 group, my experience is that when you create these super-duper large IT groups that you get exactly the sort of bureaucracy that your referring to which carries so much inefficiency that your not really saving any money.
Getting back to Target, can we agree that Target has a responsibility to secure it’s network? If so, and your assertion is that Target’s IT group is large enough that it would have a separate security group within IT, then can we agree then that this group has miserably failed in it’s duty?
I don’t know if Target has such a group. If it did, then obviously that group would not want “the sysadmins” to run those tools. But if it did not, then who exactly would be responsible for doing this if the sysadmins are prohibited from doing it?
Whether or not it enhances security to have a homogenous giant network where everything is joined together, and the IT group is so large that it has a separate security group – or whether it enhances security to break the businesses into separate independent units where the network is hetrogeneous and comprised of a conglomerate of networks where getting a password merely gives you access to a small part of the conglomerate, is an interesting discussion and I thing we could both argue the point and consume another blog the size of this one.
But I will merely close by saying that not all large organizations go for the homogeneous network with a separate security group, and I won’t resist adding the cheap shot that if Target was organized that way, it certainly is an indiction of how glaringly large the downside of creating a network like that is.
Absolutely Target has a responsibility to secure its data and network. In that regard, it has failed. It will pay the price (however many hundreds of millions it will cost them). Maybe it will be a wake up call to all industries that deal with PCI data. Although I don’t know what direction that will take those companies (larger insurance policies? more expenditure for security/network/IT? More focused on getting EMV [chip & pin] cards/readers in place quicker?)
“…is an interesting discussion and I thing we could both argue the point and consume another blog the size of this one.” Absolutely agree with that 🙂
I wonder if Beth (Target -CIO), is going to restructure? Because certainly there is room for improvement “in the trenches”
Casey
> In fact. I DONT want the sys admins to be familiar with cracker
> software. It’s simply not their job.
I get the separation of duties concept. It’s a great accountability mechanism. Least privilege is another one. All of that CISSP stuff we learned has its place. It’s important. Accountability is a good thing.
But like all good concepts, they can be taken too far. I’ve been inside my share of big companies and I’ve seen it time and again. Everyone knows their own little corner of the world and nobody thinks holistically. And trying to get even the simplest things done involves hours and hours and hours of cross functional meetings, change control procedures, and you name it. I shouldn’t complain too loudly when billing by the hour. 🙂
Suggesting that sys admins should be denied learning opportunities such as learning cracker software because that isn’t their job is short sighted. I am not suggesting corporate anarchy, just that we need an educated workforce. For system admins, knowing cracker software makes perfect sense. Bad guys are using cracker software to penetrate those systems. Doesn’t it only make sense that we teach admins and the good guys how to recognize it?
Companies should encourage all kinds of education because we in the US will only win the competitive race by out-smarting the other guys.
Actually the group that is being reported by the Washington Times to be in impeachment mode for Mr. Holder is the Coalition of African American Pastors (CAAP). Not too many Tea Party members there, but they obviously have some concerns that are fairly conservative. And they are speaking out. There’s that first amendment stuff that seems to be so vexing to some people. Of course the first amendment as originally written is a shadow of it’s former self in practice, having been fairly gutted over the years in some areas, and extended in others.
The lawsuits are mounting by the day now. As of yesterday there were 70. Each case, if a class action suit, must be certified by a court or dismissed. Very costly, very time consuming. Don’t think this is contractual tort action, so we will see how big the ball and chain gets for the Big Red Ball guys. And this plays out over years and years. Still think the weight of it all will push them into irrelevance or death.
They are reported in a January 2014 article in The Royal Gazette to have some $100 million in cyber crime insurance and another $65 million in D&O coverage. Don’t think that will get the job done, but it helps. They ate $44 million in the latest quarter.
Someone questioned about how to pressure Target to give early visibility. We the people hold that card: Stop going to Target. Let them know you will stop until they disclose.
Maybe 5 to 6 million people would be enough economic impact to bring them to their knees in about 6 months or so. Target exists on a very thin margin line and break-even point. On $73 billion they made net income of $3 billion TTM or about 4%. If you disrupt their revenue by say 7 or 8%, they fall into the red. They were off 5.4% during the Christmas quarter, so they aren’t far off just with paranoid people who don’t want to shop there out of further data breach concerns.
Of course lightning can’t strike twice can it?
Here’s a funny. Did anyone know that Target actually runs two criminal forensics labs (non-violent crime)? They apparently interface with many government law enforcement agencies. I have this picture in my head of them powder bombing the servers for fingerprints and going “what do you mean, it’s bad for the servers? It’s just fine, airborne particulates! It’ll settle in a couple hours…. “
That is amazing. MBAM, even the Pro version is anti-malware and isn’t anti-virus, It’;s supposed to work as a supplement to a good antivirus/firewall software. No wonder Target got invaded.
Wow, been gone for a while and look at this stuff to choose from! Hmmm, where to start….
1. Ted is right and Ted is wrong. One big IT system doesn’t guarantee success. At any size. Anyone here think the ACA (Obamacare) IT system is a great centralized system?
But neither does IT decentralization. It may mitigate centralized risk if deployed in that manner. It may provide redundancy. It may provide a certain level of compartmentalization, if deployed in that manner.
But ultimately it is the people who run whatever size system that provide success or failure. To date, the machines and systems don’t protect themselves or us from ourselves or the crackers. They do what we program them to do. We are the system, not them.
We call it an IT System without remembering that it’s just a DT (data technology) System without people to turn it into information. Or for that matter, protect it.
Anyone ever used Mechanical Turk? I love Amazon’s description: Artificial Artificial Intelligence.
As far as cost savings one way or the other, define cost. This is one of my favorite subjects. It’s one of the most difficult concepts for business people to grasp. Obviously government officials as well.
Many think the price tag of an item, or a line item on a PO is it’s cost. It’s a good starting point…
Scale of economy is a definite beginning point when we talk about IT strategy or anything else. However dividing into business units is done primarily for non-IT purposes. IT really has only a small bearing on it. It’s done primary for other strategic reasons:
It’s done for corporate political reasons.
It’s done to foster competition between units.
It’s done to foster business growth by appealing to local communities and, oh wait, states, to garner tax incentive, worker incentives, construction cost grants, a list of things.
It’s done to make it manageable in some cases, as bigger is rarely more manageable, except maybe to the most egotistical and micro-managing business leaders which in turn makes business continuity almost impossible. (yet another reason for the business unit strategy).
Tax strategy (avoidance in some cases).
Incubation strategy.
Realizing break-apart value.
A number of reasons, other than IT.
Ted is dead on though about large organizations. In today’s business climate, few are feeling that a homogeneous IT strategy is safe, security/loss prevention group or not. No one feels very safe right now about the vast majority of IT strategies. I hope that changes soon.
Ted and others, please lead…if you can’t even agree about sysadmin roles, what does that say? Are the industries best practices really a farce/obsolete?
I think one reason Brian built this website and fosters this blog so that you guys and gals, all of you, can begin to bring order out of this chaos. Virtually no business person right now understands the root cause analysis of all this.
In reality, no one has enough hard data yet to do so . But when we finally do, management tends to look only at the results. You don’t want business people making decisions in this area on just results. They’ll make bad decisions. Show them the body. Show them this shouldn’t have happened if just a few things are done. And that these items must transcend our desire to eliminate inconvenience, which I still feel is a root cause for this in Target’s case, at least at the POS side.
Side note; Edward Snowden should have never occurred if decentralized systems protect us, yes? He was sitting in Hawaii, collecting pass codes from what? Humans… hehe! Here we are again, people creating havoc and mayhem…. His knowledge as a sysadmin certainly helped him in this case and obviously hurt his employer, we the people.
2. Target has their own criminal investigation labs/units (2) and a very large loss prevention unit. Loss prevention failed if they were the key holders. IT failed if sysadmins held the keys. Perhaps it should have been that neither held the key, it was shared. Checks and balances.
Target is a centralized IT structure, at least day to day, with one back-up, since it was built in 2001. Their DP/BC plan may move it to a tertiary location or locations. But to be sure, it is certainly a case of a centralized system that massively failed.
3. We are closing all courts related to civil contract tort from here on out, since Ted says written contracts solve all business problems and they stand alone between the two entities to cover all business related issues. Wow! we are in a way better world. Oh, wait…. Ted, last I checked, anyone can be sued for anything. That’s why there’s so much insurance written for liability. And so many lawyers.
4. Yesterday, the St. Louis Police Pension fund has fired the first lawsuit at Target for shareholder damages. I think we covered that in earlier discussions as a likelihood. Check that box…..
5. Ted, do a quick Google on Mr. Holder and you’ll find he has tried to stop Arizona from having it’s own immigration policy by again asking the AG’s to ignore any passage of such bill, and tried to stop the Arkansas AG from honoring some legislation to allow teachers to arm themselves. Do you really want to try and defend Eric Holder? He’s in contempt of Congress right now for withholding documents, for goodness sakes. And the poor guy knows, if everything crumbles, he’s got his neck on the chopping block first. No wonder he’s having chest pains and shortness of breath.
State’s gay marriage ban and his attempt to undermine it by illegally asking State AG’s to disregard their sworn duties should shock the living daylights out of any intelligent person. I would be equally mortified if this were state bans on guns and he were asking AG’s to ignore the law (not that he ever would.)
The AG has not one shred of jurisdiction on this and has likely committed a crime in doing what he has done. Are there political reasons for this? Yes. And now you know the problem…. You can’t be AG and uphold the law and be an anchorman on the activist team for special interests for your boss. One of those conflict of interest things that seem to be so out of favor these days.
The bizarreness of all this is Obama himself, in a November 2008 interview with MTV said he was against same sex marriage. He then spoke out of the other side of his mouth by saying he thought Prop 8 in CA was unnecessary (Prop 8 banned gay marriage). Then, as probably the most ironic statement any potential president has ever made, given his 6 year assault on the US Constitution, he closed by saying: “Usually, our constitutions expand liberties, they don’t contract them,” (as reported by ABC News, should anyone feel this is some right-wing conspiracy or something.)
If you don’t like State’s rights then you obviously must abhor the US constitution and the entire reason for the US being formed: freedom from the power of central tyranny caused by too much power in too few hands. Are you Canadian? European? If you are, then that would explain some of your comments.
How does nexus or state’s borders work if there are no state’s right? Now about state criminal law that is permitted (at least for a few more years) above and beyond federal law? If there are no state rights, then stop paying your state’s income tax and see what happens. State’s rights dead? Hardly. Under attack? Yes.
All of this said, what I fear most is the misconception and manipulation of the balance of power that was provided for in the US Constitution. It was meant to be a dance. A check and balance. Delicate balance, slow to change. Thoughtful and pondered. Debated. Measured. Like the executive, legislative and judicial systems. You know, the ones that exist in some shape or fashion in virtually every corner of the planet that is even remotely a republic?
I enjoy sparring with you, Ted. I hope you understand I do respect you and your right to think as you do, and hope you feel the same. If we can’t, we are in trouble in this country…. (Oh, wait, we are in trouble aren’t we?)
I actually do share your disdain for the size of the ego of management in many large companies. But I also share equal disdain for IT “experts” (self-proclaimed or otherwise) who are long on nuts and bolts but short on understanding real process control. Or worse, denial that anything could be wrong.
“It can’t happen to us, we’re Target!” (Famous last words) “It won’t happen to my system!” (Famous last IT sysadmin or IT expert words).
Isn’t IT supposed to presume something is wrong until proven right? This isn’t a court of law. And it’s not like we are trying to prove mathematical theorems.
And aren’t we supposed to hang our egos at the door every morning? And stop looking for lightning bolt answers and start finding thousands of little things to change and fix to make great systems?
You get the last volley on this, since I’m under the gun for the next 3 weeks. Planes to catch and bills to pay, as the man said….
Robert,
I think you did a good summary of the pros and cons on the centralized vs decentralized approach. And yes, even the best system will be wrecked if you hire bozos to run it. But there’s an old approach to solving problems: divide and conquor. I think that breaking up large IT groups in the last analysis creates fewer opportunities for major problems that are large enough to potentially take a company down.
I hesitate to jump into the political states rights issue but I will – as I said before I have little use for States Rights. And your correct, I am “against” the US Constitution in this regard. But, I will also point out that there is 200 years of caselaw and SCOTUS decisions which have ALSO come down “against” the US Constitution in this regard. The fact is that if you were a pure Consitutionalist you would be against the Federal Income Tax since that wasn’t written into the Constitution and for the first 100 years of the country’s existence there was no federal income tax.
The Founding Fathers created the separation of powers from federal to state government for 2 major reasons:
1) They did not want to address Slavery
2) They felt that individual states would be the champions of citizens individual freedoms, far more than the federal government would be.
But what the last 200 years have taught us is that in actuality, when applied, the very sad truth is that the individual states have, in fact, NOT been the champions of citizens individual freedoms. Far, far from it in fact. Most states when given a chance have repeatedly ruled against citizens individual freedoms. They do it by trying to define people in the country as non-citizens, like the South did with the Slaves and Arizona is doing today with Mexicans. They do it by constant and never-ending creation of minor traffic infractions and city ordinances designed to make minor and piddly things illegal from barking dogs to peeing in the grass to driving 15 feet in an empty bicycle lane before a turn. And when private citizens try to get a little relief – like begging their city governments to pass HELPFUL ordinances, like requiring builders who are building multistory apartment buildings to put in some parking spaces for God’s sake so the tenants don’t dump their cars all on the street for the next 20 blocks and make it impossible to park your car – it’s like pulling teeth to get it done.
The majority of states are against gay marriage, that’s why the feds had to spell out for them that SCOTUS would no longer uphold their anti-gay legislation
The majority of states are against smoking weed when 50 years of government studies have been unable to find anyting wrong with it.
The majority of states were against abortion, which was our fathers arguement.
And I do not see most states rushing to sue the Federal government over infringing rights during their wiretapping of everyone’s phone calls. By contrast most states are rushing to have their own police departments interface with the Feds to be able to get access to that data.
The fact is that on the scale of supporting citizens individual freedoms, it has been the FEDERAL government that has most often come down in favor of individual citizens freedoms. Quite the opposite from what the Founding Fathers thought would happen.
Who knew, eh?
To say that the IT group that is large enough dent work because of the Target incident isn’t valid…its a sample size of one. As to compliance programs in general, they are not a substitute for holistic security. I talked to a CIO at ROSA this week that said his biggest struggle is that his superiors will spend money to be compliant because of the financial impacts if not done. Security has no fines if not properly implemented, just pure risk/reward, and leaders are often willing to take gamble that it won’t happen to them.
Gunky,
Please reference the Department of Health Human Services site regarding both civil and criminal fines for failure to provide ePHI (Personal Health Information) security.
HITECH provides very large teeth now. If you aren’t in the medical field or other field governed by HITECH, it might not apply to you. But to say there is no penalty is no longer true. Other areas like Sarbanes-Oxley also provide specific penalties and fines.
I will agree that management sticks their head in the sand far too long on this many times. And rolls the dice hoping that that they don’t get caught.
Risky business…
I’m really enjoying the theme/design of your blog.
Do you ever run into any internet browser compatibility
problems? A small number of my blog audience have complained about my
website not operating correctly in Explorer but looks great
in Chrome. Do you have any solutions to help fix this problem?
Hey Brian, I see the “cartoon photos” comment that just came in and I know this stuff is a hassle but I have to laugh. Almost a year ago, I did a blog entry about how to recognize a spam message – see the URL below. The search engines found it and I was buried in Chinese spam comments, plus zillions of others in English vaguely complimentary with links to drug websites. I think every Chinese drug seller tried to sell their junk through that blog post and I finally just turned off comments.
Here’s the blog post – anyone reading this comment, feel free to use it with your end users.
http://www.infrasupport.com/how-to-spot-a-phishy-email/
– Greg