Millions of Web sites were shuttered Monday morning after Microsoft executed a legal sneak attack against a malware network thought to be responsible for more than 7.4 million infections of Windows PCs worldwide.
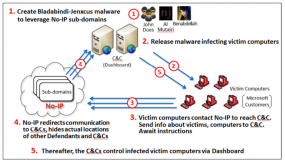
A diagram showing how crooks abused no-ip.com’s services to control malware networks. Source: Microsoft.
In its latest bid to harness the power of the U.S. legal system to combat malicious software and cybercrooks, Microsoft convinced a Nevada court to grant the software giant authority over nearly two dozen domains belonging to no-ip.com, a company that provides dynamic domain name services.
Dynamic DNS services are used to map domain names to numeric Internet address that may change frequently. Typically, the biggest users of dynamic DNS services are home Internet users who wish to have a domain name that will always point back to their home computer, no matter how many times their ISP changes the numeric Internet address assigned to that computer.
In this case, however, the attackers responsible for leveraging two malware families — remote-access Trojans known as “njrat” and “njw0rm” — were using no-ip.com’s services to guarantee that PCs they infected would always be able to reach the Internet servers.
Microsoft told the court that miscreants who were using these two malware strains were leveraging more than 18,400 hostnames that belonged to no-ip.com. On June 26, the court granted Microsoft the authority to temporarily seize control over 23 domains owned by no-ip.com — essentially all of the domains that power no-ip.com’s free dynamic DNS services.
Microsoft was supposed to filter out the traffic flowing to and from those 18,400+ hostnames, and allow the remaining, harmless traffic to flow through to its rightful destination. But according to no-ip.com marketing manager Natalie Goguen, that’s not at all what happened.
“They made comments that they’d only taken down bad hostnames and were supposedly redirecting all good traffic through to users, but it’s not happening, and they’re not able to handle our traffic volumes,” Goguen said. “Many legitimate users that use our services have been down all day.”
Goguen said while Microsoft claimed that there were more than 18,000 malicious hostnames involved, no-ip.com could only find a little more than 2,000 from that list that were still active as of Monday morning. Meanwhile, some four million hostnames remain offline, with customer support requests piling up.
“So, to go after 2,000 or so bad sites, [Microsoft] has taken down four million,” Goguen said.
Microsoft told the Nevada court that despite numerous reports released by Internet security firms over the past year about large volumes of malicious activity emanating from no-ip.com’s service, the company “consistently failed to take sufficient steps to correct, remedy, or prevent the abuse and to keep its domains free from malicious activity.”
But according to Goguen, the first time Microsoft brought its concerns to no-ip.com was at 7 a.m. on June 30, when the company’s CEO received a knock on the door of his family home and was served with a copy of the court order granting Microsoft authority over the 23 no-ip.com domains.
“We work with law enforcement all the time, and our abuse department responds to abuse requests within 24 hours,” Goguen said. “It’s pretty sad that Microsoft had to take such extreme measures to go about this.”
Goguen isn’t the only one who believes Microsoft swatted a fly with the equivalent of an atom bomb. Some of Microsoft’s previous legal sneak attacks targeted “bulletproof” hosting providers — those that promise to keep sketchy (and high-paying) customers online despite pressure from security firms and law enforcement. But according to Dmitri Alperovitch, co-founder of security firm CrowdStrike, treating no-ip.com like one of these shady providers is a mistake.
“They have always been very responsive to security researchers and law enforcement,” Alperovitch said of no-ip.com. “I do not consider them a bullet-proof or abuse-proof host.”
Meanwhile, Goguen said no-ip.com is considering its legal options for responding to the outage and to Microsoft’s allegations that the company somehow turns a blind eye to abuse complaints.
“We’re speaking with our lawyers about this, but right now we’re doing everything we can to fix this, and we need our users to understand that.”
In tandem with the action against no-ip.com, Microsoft also named and accused two men — software developers thought to reside in Kuwait and Algeria — of authoring and selling the njrat and njw0rm.
The complaint against no-ip, the accused malware authors, and the rest of Microsoft’s various legal filings in this case are available at this link.




It seems that Microsoft operated here as the law enforcement arm of the US government. That is pretty creepy.
The merging of government and corporate power, the first step to a totalitarian state.
“Fascism should more appropriately be called corporatism because it is a merger of state and corporate power.”
–Benito Mussolini. (from Encyclopedia Italiana, Giovanni Gentile, editor)
Oy… I apologize to everyone for the derail, and no offense to the poster I’m replying to, but this just screams for correction.
What the Fascists are referring to are not corporations like we understand them today i.e. large incorporated businesses. What Mussolini was referring to was the concept of the “corporazione” i.e. the “guild”. “Corporates” in that political system were not incorporated businesses, but rather groups representing interests i.e. trades, professions, etc.
The closest analogy (and don’t take the comparison too far) are either modern labor unions like the United Auto Workers , or professional organizations like the American Medical Society. It’s not a good comparison because the Fascist “corporates” were entities given power by the government – as opposed to deriving legitimacy from the makeup of its members – but it’s the best that can be done nowadays.
So to make things topical to this thread: No, Italian Fascist “corporativismo” is not analogous to modern corporation/government synergic abuses. That doesn’t make modern problems any less wrong, but it does mean that the comparison is not accurate. Business/Government abuse of power is problematic on its own merits, not because it harkens to an interpretation of Mussolini’s statements that’s ultimately inaccurate.
Again, apologies for swerving off topic, and no offense to the posters above.
No offense taken for the ‘correction’, but Mussolini was very well acquainted with more modern non-guild corporate entities as were well-established in many parts of Europe and North America before and after WWI. So far as I’m concerned, the broader definition fits and is quite accurate.
Wow – I used no-ip for years and I’m damn sure I wasn’t using it for no good.
I feel for all those innocent users of that service. I dodged a bullet only because I moved to an ISP that offers a fixed IP address and hosted most of my sites with hosting companies.
I don’t know how to feel about this… They’ve take out an entire business which is extreme especially when no-ip is not at fault; However, no-ip was the largest network of scriptkiddie botnets ever seen (due to the fact people could register multiple subdomains for free and if one was taken down due to an abuse report, the bots would just connect to a backup one).
While I do feel bad about what has happened to no-ip.com, for which Microsoft must make amends to, I do want to drop atomic bombs on these miscreants who create software that make our computers dysfunctional.
If we did not have to suffer these cretins, we would not need such drastic measures. My hope is that this may serve as a warning to such sociopathic morons to cease and desist in their actions.
But in the end, humans being humans, we will have to nuke them to eradicate the vermin.
“nuking” them may create mutations that are worse than what we have now. Remember the origin of “Godzilla”?
In this case Microsoft has met the enemy and they are them. (Sorry, WaltK). Aiming for 2k, or even 20k, and hitting 4M is similar to a “controlled laboratory virus” that escaped. I think the legal system may call it “exceeding the scope” of the court’s order. I’m sure many an expensive lawyer will take each side and in the battle of deep pockets there are many Davids and few Goliaths. (On the other hand David might have read Sun Tzu and used better tactics to win).
Some solution that avoids, or limits, impacts from the Law of Unintended Consequences might be better than nukes. On the other hand they can very very tempting.
While I appreciate the metaphor, I am not real.
Whine Natalie. Why did no-ip not better police their clients/users?
Even the name reads bogus.
With 4 million+ clients, they responded to abuse requests within 24 hours–how would you suggest they police their clients? Nothing is hosted on their service–it’s all just pass through (e.g. if you get traffic for URL ‘X’, send it to IP address ‘Y’).
The name isn’t bogus either–if you know what dynamic DNS is, then it makes complete sense. It’s rather fitting actually.
If Microsoft is not able to do this, but does more damage than good, then they should pay for it financially, and lose the right to cease domain names this way in the future. It should be an FBI task anyway.
Redirecting traffic to Microsoft is like spying, and probably breaks lots of US laws, and Microsoft propbably gains intel they can use commercially. Especially since they are in the hosting business.
I agree with you here. It should be a partnership with law enforcement, at the least. I could see the FBI or another entity being a go-between between the private company and the courts.
If the company would like to take an action that would involve acting against another private entity, they should have to convince law enforcement that it must be done, and then allow the law enforcement body to obtain the court order.
At the very least, it would add another barrier to pulling a stunt that is the equivalent of using a hammer to cut out a tumor.
While I’m generally against making sweeping attacks like this, unfortunately too many of these malicious baddies are running around wreaking havoc on our systems. It’s the little guy who can’t fight it and loses his/her machine and data. I gotta be honest I say good on ya Microsoft – besides they probably afford any fallout suits if they got the wrong ip’s.
I agree, while its sad when innocent people get caught in the cross fire, I believe ISP’s can do more to be proactive, the stats show that half of all attacks against the USA are from the USA? Why because foreign cyber criminals are signing up for Amazon, GoDaddy, etc web services in our country. It helps hide the source of the attacks. This is a global problem and I’m happy to see our country taking some proactive steps to make a dent in the $500 Billion a year
Global cyber problem. What should we do, just sit back and continue to let the transfer of wealth continue? Many nation states are supporting this activity. Follow the $…….
Happy 4th!
Thing is, Microsoft could have cooperated with no-ip instead of shutting them down. It would have been just as effective (well, probably) and there wouldn’t have been 4 million innocent victims.
I think this is disconcerting because apparently No-ip[dot]com wasn’t offered a chance to appear in their own defense before their property was seized and handed to another private party. Is that due process?
+1 to this.
To play devil’s advocate, however, allowing the company to defend itself would also allow the company and the miscreants to plan a mitigation strategy, such as opening a similar company under another charter, at another domain address, and moving all of the bad activity there.
To be effective, shutting down bulletproof hosting operations and botnets needs to be done as a surprise. If you tell the criminal where you will go to catch them, they won’t be there when you get there.
This is clear overreach IMO.
I amd far from the only security researcher who can say the no-ip were responsive to take down requests and abuse reports. Typically it took a day or so, but for a small company I consider that quite satisfactory – even huge comanies such as Google and Microsoft take a good few hours because you have to validate that the abuse request is valid before acting. In fact I believe that no-ip worked with the Mariposa Working Group to take that botnet down – a takedown that led to actual jailtime for the people behind it.
This takedown has impacted some 4 million domains run by legitimate people (including me) to try and get at about 20,000 domains (a hit rate of at bets 0.5% (and given that many were already taken down probably more like 0.1%).
One could use the same argument to take over hotmail – after all pretty much every email I’ve ever received from a hotmail IP address has been spam and in many cases it is the classic Nigerian scam email.
Microsoft should become aware they are dancing a very fine legal line between the legal government demands in the US, that they answer to legal orders for data they store on their global systems as “property”, and using the US legal system to control the electronic “property” of other firms that impact legitimate global businesses. Many businesses and governments in Europe, exam these legal actions as a negative risk to their operations. International American companies that depend on the European business for their revenue are experiencing a significant reduction of European business.
Wow scary creepy & yet…
It’s like the whole NSA phone collection thing (as I understand it)
They want to catch potential ‘bad guys’ but they collect everyone’s phone calls to do it. Worth it? Maybe, maybe not. Hindsight is always 20/20 but if bad things are prevented from happening the urgency is much more difficult to justify.
BTW @BrianKrebs: in the 2nd to last paragraph njrat is misspelled as njrar. 😉
Looks like I’ll be driving to my mom’s house to fix her computer errors for a while instead of using RDP through her no-up address. If you’ve ever tried to get your mother to find her ip address, you’ll understand my pain. Hint- it’s not 192.168.0 or 1. anything.
“4MM”? That’s a blast from the past. Especially in the computer world, M stands for mega and is not 1,000 (from the Roman numeral). “4M” would do the job just fine.
Thanks Microsoft you for killing my network storage down putting the DDNS down. I know, you hate network storage because you want people putting everything to your cloud.
Now , looking for an european DDNS provider. Oh, sure, some malware was using it. Like the amount of malware and spam I get from hotmail, right?
Just an excuse to kill home Own.clouds.
Uriel
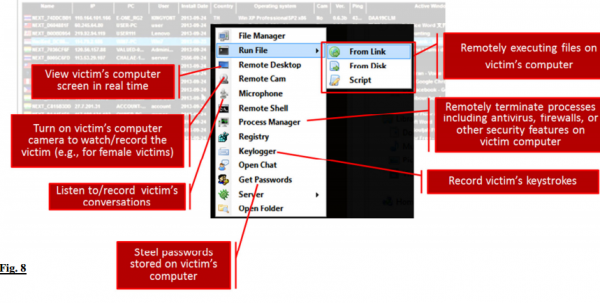
Is ‘Fig. 8’ Microsoft’s graphic? They spelled ‘steal’ wrong.
Yeah, I noticed that too. I guess the court doesn’t care if the plaintiff isn’t literate.
I noticed this, too. I laughed my radioactive laugh.
Microsoft is the new Department of Homeland Security
seizing websites
WTF? Why was Microsoft even involved in this? Something doesn’t add up
no-ip com is another one of those gray-area service providers who know their services were being blatantly abused, but decided to simply close their eyes and claim they had no knowledge of the script kiddie and criminal botnets that were abundant as lice in their hair. This “blind eye approach to no-accountability” didn’t work for MegaUpload … don’t see how no-ip would think it woiuld work this time for them. If you want a static ip, then get a real one. Can’t afford a static IP and need RDP to fix mom’s computer, use a service like MeetMe. n Of everyone I know who used no-ip, not one of them were using it for legitimate purposes anyway. With all the botnets spiderwebbing the Internet, expect to see more free dynamic DNS services like no-ip to get hit with similar heavy handed tactics.
Totally agree. I am glad that M$ is doing this. You want access…buy a real IP address.
As for the company involved, tough. I feel the same way about banks like UBS that launder billions for cartels. If your business model caters to criminals, then tough. Put me on the jury that sues M$ for this and I’ll try my best to make sure this company never receives a dime.
Agreed!
Notice, at least in this article, it says they received numerous reports from Internet security “firms” over the past year followed by “the first time Microsoft brought its concerns.” This assumes they were warned about this many times, but once action was taken, they cry “Microsoft didn’t give us a chance.”
This should serve as a lesson to other Dynamic Domain Service providers to keep a better eye on how their services are being used.
BTW, funny how Microsoft says “e.g., for female victims.” Reminds me of Mortimer Duke “…pork bellies, which is used to make bacon, which you might find in a ‘bacon and lettuce and tomato’ sandwich.”
No-ip responded appropriately to abuse alerts etc. from many security vendors. I have personal knowledge of some of this and Mr Krebs could easily ask any number of his contacts in the space to confirm this.
Microsoft NEVER asked them.
Worse Microsoft’s takedown strategy has led to about 4 million legitimate non-criminal users of no-ip to suffer a Denial of Service because Microsoft did not in fact get the infrastructure in place to handle the huge volume of DNS requests that no-ip handled each day. That means that families who used no-ip webcams to keep their eye on loved ones, people who vpn into their home network via a no-ip address and so on have been unable to do so.
At this point anyone who runs any small business offering a service on the internet that could be used for criminal activity as well as legitimate uses can potentially see their business be taken away from them with no warning and no way to provide a defense just because Microsoft’s DCU got a judge to sign off on a TRO. That is extremely disturbing.
Betan, from your omniscient perspective of “everyone you know who used No-IP wasn’t using it for legitimate purposes anyway”, you are now uniquely qualified to generalize your sample size to the entire Internet? Not only that, but qualified to pass judgement on the legitimacy of their activities as well. Congratulations must be in order. I’m pleased to meet a supreme being.
Why stop there? Just take down the DNS root servers, that’ll stop the bad guys for good.
So a private company successfully gets a warrant to seize the property of it’s competition because a small percentage of it’s users are THOUGHT to be involved in malware… Makes total sense..
As far as ISP’s and private companies that “should really do more” it would require prying more into what we do online and more tracking of every user. Not good.
OR, people that have been hit with a virus can educate themselves so it doesn’t happen again. There are free anti viruses, and some easy steps you can take to greatly minimize the chance of your computer getting infected.
Commmmon Man, a Home business account with a major ISP costs $100.00 a month. If you already have internet you can host your own servers from your home. So maybe your bill will increase some. Write it off in taxes each year. Stop being such a tight wad when it comes to a business. Thats why many potential websites are not going to go anywhere.
PLUS there are a TON of low cost web site hosting sites out there that are a better alternative than any sort of DNS redirects.
Some people that write here haven’t a clue on what these miscreants will do to make money off others.
Who’s to immediately say that the person or persons involved are clean, and not taking any sort of kickbacks? I personally don’t care if it is one or one million people who use this service and are victims….. they issue is its a SECURITY ISSUE. As if 2000 bad websites isn’t enough of a concern. What the heck……
The company better be shoring up its accounts – not against Microsoft but the end user who may have suffered since their data has passed through this service. Obviously the company in question isn’t paying much attention to the security side of the house until NOW.
Microsoft doesn’t act on a whim, they probably have enough data – probably as much or more than NSA on individuals. So whatever this company is complaining about is a finger pointing event – trying to buy time to save their subscribers. In the end I am sure we will hear about the inner workings of this company and what they actually were doing.
Bottom Line – there are BETTER solutions than using this type of cheap service. Now, you get what you paid for.
Right on! Now Microsoft need to clamp down on other free services, such as free email. It’s only used by miscreants and cheapskates!
In case you didn’t notice, many of those complaining *aren’t* running a business, and don’t get to “write it off in taxes”. And while I’m sure it’s nice for you to be rich enough to not worry about how much you’re spending on internet service, some of us have to live on a budget.
At the end of the day, it all boils down to whether or not you believe Microsoft’s assertion that no-ip.com were either unwilling or unable to assist in taking down the botnet, and that therefore Microsoft had to take over the entire service. It is conceivable that Microsoft can justify this – but since Microsoft never even asked them about it, it does seem rather unlikely.
Can someone explain how (technically) Microsoft got access to these domains from no-ip.com?
When Natalie Gogun says “but it’s not happening, and they’re not able to handle our traffic volumes”
Does that mean Microsoft re-directed all the traffic of no-ip.com though their own servers?
Microsoft is doing what no-ip.com never did. It is protecting the people! no-ip.com took profit over people’s security and now it is paying the price. Go Microsoft!!!
This is like driving a pushpin with a pile driver. I cannot understand how some can support this. Using Microsoft’s estimate of 18,400 malware serving hosts out of 4 million hosts in the 23 domains you have less than 1/2 percent. Using No-IP’s estimate of 2,000 that is about 1/20th of a percent. The inverse of both calculations is more than 99% of the hosts are not serving malware.
No-IP is very responsive to abuse notices. Their service is a natural draw to miscreants. The fact that they are able to keep abuse below 1% is amazing.
Using some off the cuff guestimation there must be almost a percent of all internet hosts serving up malware if you round up to the nearest percent. I guess we should hand the entirety of the internet hosts to some benevolent organization to cleanup that mess.
If you have a hammer, everything and everyone looks like a nail!
OK, check my math…
Assuming conservative figures, that MS is correct about 18k bad guys, and ONLY 4M sites went down, that gives an effective hit rate of 0.0045.
Out of every thousand people kicked off the Internet, AT MOST 4 or 5 were guilty. In terms of percentages, that rounds to… 0.00%.
In what Bizarro universe is this a good idea? It is relatively simple to code up your own personal dynamic DNS utility. The only reason for the miscreants to use no-ip was to hide in the crowd of innocent users.
All they have to do is pick a burner site to point to and they are back in business.
The only people who will be offlined for any time are the folks using the service for legitimate purposes. And yes, it is legitimate to use a dynamic DNS to avoid paying money for a fixed IP, whether anyone likes it or not. On the Internet, you can often substitute cleverness for cash; that’s part of its value.
I think MS should get slapped down for this, and an example should be made to curb this kind of high-handed action.
Even corporations should know you don’t knock another business off the net with impunity. They had lawyers, but not law on their side.
(Disclaimer: I’m not a lawyer, but I’ve been an Internet engineer since corporations weren’t allowed on the net. Sometimes I miss those days.)
I doubt very much that a court would allow Microsoft to take control of No-IP’s domain names without them being informed. That sounds like a lie to me. The whole story has yet to come out. I am betting No-IP got what they deserved. A good portion of what is wrong in the world wouldn’t exist if so called “good people” like those working at No-IP didn’t turn a blinds eye towards what is obviously criminal activity. Activity that they help facilitate by providing services. They continued to line their pockets long after they were told what was going on because they didn’t want the income to stop.
You can read it yourself:
http://www.noticeoflawsuit.com/docs/14cr987-Microsoft.pdf
Microsoft’s request for this emergency ex parte relief is not the result of any lack of diligence on Microsoft’s part, but instead based upon the nature of Defendants’ unlawful conduct. Therefore, in accordance with Federal Rule of Civil Procedure 65(b) and Civil Local Rule 7-5, good cause and the interest of justice require that this Order be Granted without prior notice to Defendants, and accordingly, Microsoft is relieved of the duty to provide Defendants with prior notice of Microsoft’s motion.
Good intentions by MS are meaningless. If you claim you can do X and you fail there has to be consequences.
1. MS should have to compensate no-ip and its customers.
2. No court should ever trust MS again in a similar situation without a 3rd party audit of the plan.
I thought the statement, “no-ip.com could only find a little more than 2,000 from that list that were still active as of Monday morning” was particularily interesting. That’s like someone who facilitates a huge criminal network saying, but only 2,000 were found to be committing crimes this morning.
It’s rare that police action against a business doesn’t have an adverse impact on the whole business, including the innocent. That’s why you need a court order. That’s why businesses that commingle legitimate and illegitimate transactions do so at their peril. We have seen it recently with large banks and money laundering. I’m not saying it right, but there is nothing new going on here. This is the predominant way legal authorities encourage businesses to be proactive about weeding out illegal activities that find their way into the business.
There is no magic threshold for action or absolutes in these cases. The courts try to decide if the proportion of legitimate and illegitimate transactions in a business rises to a level that management “knew or should have known” the illegitimate transactions were occurring and whether they chose to not make a meaningful effort to minimize those transactions. So ask yourself, did no-ip know or should have known, and do you think they were making a significant effort to minimize these transaction.
I read it a bit different.
Out of more than 4,000,000 legitimate domain names, Microsoft provided a list of 18,400 names that they suspect to have been used for malware connections.
Only 2000 of them still existed, the other 16,400 were already gone!
So 2000 out of 4M, that’s liking bombing a town of 2000 people because of one criminal living there (that you know of).
Let me add… Keep in mind that the US Legal system is adversarial by nature where one party takes its best shot and the other party fires back. No-Ip doesn’t have to just take it from Microsoft. They can quickly get before the same judge, show that they didn’t know or if the did know, they were taking significant actions to minimize the illegal activity. The court order then can often be quickly lifted.
The courts are typically loathe to issue an order that can shut a business down without a trial and typically only do so by an order when the evidence is very compelling. Of course the judge has only heard Microsofts side thus far.
If Microsoft was found to have not acted in good faith with the information given to the judge that prompted the order, they are subject to the judges wrath, which can be substantial and very painful even to a behemoth like Microsoft (judges hate to be used as pawn in business disputes).
Microsoft attorneys are not invincible… they can’t even spell (look at the exhibit they prepared for the judge – Fig 8 above – they spelled “Steal” as “Steel” in the callout for “Steel Password” [sic]).
As others have said: a large portion of no-ip was a malware and botnet cesspool, but Microsoft is really overstepping their boundaries.
The ratio of bad to good domains is not really relevant. It’s the amount of harm that the bad domains are doing which is linked in part to the volume of traffic going to those domains.
In my opinion, the harm caused by these bad DDNS domains is significant, and they pose a clear threat to internet users in general.
Frankly my recommendation for corporates is that they should block access to all DDNS domains from their own networks, because of the high risk of malicious sites and the low strategic value of those legitimate DDNS sites that exist.
Although this mess is unfairly hitting legitimate users (e.g. people with webcams, home security systems etc) I do not believe the world is going to end.
I think your right on.
People like to complain, because it seems to be the right thing to do.
The stuff the crooks are pushing is bad stuff. Thats the bad stufff they know about thats going through this “service”….. What about all the other unknow really bad undetected crap that is going through, or was/is planned to go through this service?
People don’t care about security issues until its too late. When they are personally affected, thats when they see $$$$$. I haven’t looked to hard, but has anyone that uses this service even thought that they somehow could have caught this creeping crud, and it could be on their machines right now?
Sure its an inconvenience, but I don’t see legitimate ISP paying people going at the throats of the ISP when the network goes down for periods of time.
Absolutely agree, a few days down to clear out the crooks will make the company – who obviously has failed to do so – more secure and trustworthy – as long as they aren’t part of the issue.
So Microsoft breaks the communications chain between these devices and hardly anyone asks what is next. I assume MS is probably trying to get as much infected traffic info as possible and may try to take over the C&C side, or at least ID exactly where all this stuff is, and have a government step in and seize it.
I would like to beleive that its already happened, since they don’t want the crooks to simply switch over to an alternate service once / if this “service” comes back on line.
So from what I understand from Microsoft action, this means every one using no-ip is guilty until THEY decided the user is innocent.
Do we have the right to have a lawyer?
I just had an idea about how bad it could be : for people who use it fairly and makes money of it how will they be refunded from the shutdown of their website?
Sure, lawyer up.
With all that cash you wasted on a lawyer, you could have written a Business Plan and a Disaster Recovery style plan, and had an alternate service already running.
All I am saying is NEVER rely on something for the long haul. The crooks PAY for this service as well, paying customers doesn’t mean they are completely clean.
Greedy comes to mind. This is not a way to get rich quick scheme. if you’re thinking it is, your no better than the miscreants that caused this issue in the first place.
If you have the time to analyze and show records of hourly potential losses, and can prove to a jury – which may take years, the lawyer costs would surely outweigh anything you can claim to be acceptible.
If you were a big business, your conversation here would probably be different, as the big business would have its own legitimate DNS server or, definately be ran without this Malware attractant service.
I think your point applies to any legitimate activity, not just big business.
the complaint i hear seems to be the equivalent of conducting business in a seedy bar and then complaining business disruption when the place was raided because of illegal activity.
The other consideration i don’t see in these comments is the bad actors have an incentive to attract legit activity as it forms a human shield and provides cover. whether that is no-ip or not is a good question, the evidence seems to at least raise that possibility.
As it’s presented so far, I can’t fault MS, particularly since no-ip admits it knew of 2000 it apparently did not take action on. this suggests the legit users have a beef with noip rather than ms, or the court.
anyway, for what it’s worth, i agree with your assessment.
Where did you get the idea that no-ip knew about the 2000 prior to the court order being served? I think that’s based on a list Microsoft gave them afterwards.
from the article they had ‘numeros reports from security firms’ indicates it was not a one off oversight. secondly, whatever process rhey did the day after should have been done the day before.
the process that no-ip employed seems to be similar to a bar where the owner knows about drug dealing on the premises, but only takes action when someone else complains, then goes back to allowing the drug deals.
it’s unlikely 2000 is correct, and unlikely 18000 is correct. it’s also true that the realty could be higher, or lower, or somewhere in betwwen. my estimate is people can argue over that number for longer than humans inhabit the earth, so i wish you luck in that task. there isn’t a requirement to precisely guess the number of drug deals at any exact point in time either, otherwise you complain about 2 and they simply move the count to 1 or 3. did no ip know about 1985 , or was it 2006? whatever number is chosen, it’s likely wrong, and constantly changing. so what is your guess on the number of jelly beans? and if it’s greater than one, why didn’t they take action on it prior to the ‘raid’?
the ms complaint was against no-ip, so the action affected no ip, just as a complaint against a bar allowing drug activity. patrons of that bar may be disappointed when it’s raided.
i imagine one could build a free service for everyone, with the sole bad actor fronting the cost. you then argue that the ratio is even more extreme, so no action should be taken. as you can see it’s not the ratio, it’s whether the service knowingly allows the bad actor, as the become complicit, just like a bar owner that sees drug deals on premises and does nothing unless a complaint is filed.
if the complaint and order was against the drug dealers/miscreants, then i agree, the bar owner is ‘damaged’.
no-ip seems to have said ‘we are shocked to hear that gambling is going on in this establishment'(casablanca).
so lets be clear, the order is against no-ip, not the many miscreants using it’s services, or the human shields using the service. the health department shutsdown a restaurant, not just the meat dishes. sure the vegetarians would not have gotten sick, so they complain about the heavy handed action.
i would agree with those ‘real users’ argument had the ms complaint not have no-ip as the defendant.
bottom line is even if no ip was complicit in one miscreant malware usage the action is appropriate, otherwise every criminal enterprise could start up a free service, only allow their own illegal activity and they would be insulated.
did noip know of, and take no action on at least one domain? if so, then the ms action to put no-ip as defendent is correct, and the collateral damage is no-ip’s fault. from the evifence known so far, that seems to be the case.
whatever process noip used for their 2000 shpuld have done beforehand, not afterwards, given they were alerted to the problem for quite some time.
i hear the arguments that it’s heavy handed, etc, and to everyone that enjoys a nice almost free meal at that restaurant they are upset it got raided. those folks, through ignorance, or turning the blind eye, etc., enable the restaurant by providing cover to the illegal activity. heck, some bad actors donate to charities to create another layer of ‘protection’.
anyway, i agree with you, it’s likely not 2000, though at some point in time it likely was. i used noip’s number as a token for ‘greater than zero that we didn’t take action on’. whatever the number, they calculated, they knew about the problem for an extended period of time. and they ARE the defendant, so of course the action pertains to them.
i suggest that if noip cared about it’s legit users they should have taken care of the issue, just as a bar or restaurant that knows of on premise drug dealing.
legit users should voice their anger at noip, not ms, or the judge. it would also be wise to be aware of volunteering to become a human shield.
there may be more to the story, but that is how it appears to me at this time.
There is no evidence that no-ip knowingly allowed anybody to misuse the service. So far as I can see, even Microsoft aren’t claiming that.
Microsoft had identified a number of specific addresses that were being misused. No-ip had *not* identified these addresses, either because they didn’t have access to the same information (e.g., it may have been based on information collected from Microsoft’s anti-malware product lines) or because they didn’t have the resources to process the information effectively.
I see no reason to think that no-ip wouldn’t have been willing to cooperate with Microsoft’s attack on the malware network. If Microsoft had simply asked them to assist, and told them which addresses needed to be shut down and when, there wouldn’t have been a problem.
This isn’t a bar that allows drug deals unless someone complains. This is a city whose police force haven’t been able to catch every single criminal.
It really doesn’t seem likely that burning down the entire city was justified.