Multiple financial institutions say they are seeing a pattern of fraud that indicates an online credit card breach has hit Park-n-Fly, an Atlanta-based offsite airport parking service that allows customers to reserve spots in advance of travel via an Internet-based reservation system. The security incident, if confirmed, would be the latest in a string of card breaches involving compromised payment systems at parking services nationwide.
Update, Jan. 14, 2015: Park ‘N Fly has acknowledged a breach. See this story for more details.
Original story:
 In response to questions from KrebsOnSecurity, Park-n-Fly said it recently engaged multiple outside security firms to investigate breach claims made by financial institutions, but so far has been unable to find a breach of its systems.
In response to questions from KrebsOnSecurity, Park-n-Fly said it recently engaged multiple outside security firms to investigate breach claims made by financial institutions, but so far has been unable to find a breach of its systems.
“We have been unable to find any specific issues related to the cards or transactions reported to us and by the financial institutions,” wrote Michael Robinson, the company’s senior director of information technology, said in an emailed statement. “While this kind of incident is rare for us based on our thousands of daily transactions, we do take every instance very seriously. Like any reputable company involved in e-commerce today we recognize that we must be constantly vigilant and research every claim to root out any vulnerabilities or potential gaps.”
Park-n-Fly’s statement continues:
“While we believe that our systems are very secure, including SLL encryption, we have recently engaged multiple outside security firms to identify and resolve any possible gaps in our systems and as always will take any action indicated. We have made all necessary precautionary upgrades and we just upgraded on 12/9 to the latest EV SSL certificate from Entrust, one of the leading certificate issuers in the industry.”
Nevertheless, two different banks shared information with KrebsOnSecurity that suggests Park-n-Fly — or some component of its online card processing system — has indeed experienced a breach. Both banks saw fraud on a significant number of customer cards that previously — and quite recently — had been used online to make reservations at a number of more than 50 Park-n-Fly locations nationwide.
Unlike card data stolen from main street retailers, which can be encoded onto new plastic and used to buy stolen goods in physical retail stores — cards stolen from online transactions can only be used by thieves for fraudulent online purchases. However, most online carding shops that sell stolen card data in underground stores market both types of cards, known in thief-speak as “dumps” and “CVVs,” respectively.
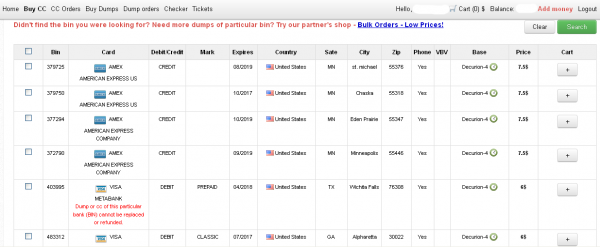
The CVVs stolen that bank sources traced back to Park-and-Fly are among thousands currently for sale in four large batches of card data (dubbed “Decurion”) being peddled at Rescator[dot]cm, the same crime shop that first moved cards stolen in the retail breaches at Home Depot and Target. The card data ranges in price from $6 to $9 per card, and include the card number, expiration date, 3-digit card verification code, as well as the cardholder’s name, address and phone number.
Last month, SP Plus — a Chicago-based parking facility provider — said payment systems at 17 parking garages in Chicago, Philadelphia and Seattle that were hacked to capture credit card data after thieves installed malware to access credit card data from a remote location. Card data stolen from those SP+ locations ended up for sale on a competing cybercrime store called Goodshop.
In Missouri, the St. Louis Parking Company recently disclosed that it learned of breach involving card data stolen from its Union Station Parking facility between Oct. 6, 2014 and Oct. 31, 2014.




I get the feeling you’re only covering this story to do with cvv’s because it has to do with rescator?
where do you see anything about cvv in this story?
i think he meant CC not CVV (CVV would be included in Dumps)
“SLL” encryption? Well, there’s the problem 🙂
SLL = Shift Left Logical No one can crack that.
No one could decrypt it either! The left most bits would be lost and the right most padded with zeros…
I am not sure why they even mention upgrading the SSL certs.
It just makes it look like they have no idea what they are doing.
It’s because they don’t know what they’re doing. It’s a pretty typical response to a company not used to be scrutinized for its security.
“Our website guy told us we had the newest SSL certificates available!”
They really just don’t know any better.
I would use a house break-in analogy here. The thieves busted in through the front door and the owner says things are fine now because they installed a metal grate (from one of the top metal grate mfrs) in the upstairs bathroom window.
I can’t help but wonder if they outsourced all of their IT, and they have some low-bid contractor trying to figure out what’s going on.
They truly have no idea what they are doing and should be deeply fined for their negligence.
“While we believe that our systems are very secure, including SLL encryption,…”
What is SLL encryption?
In a magical land of executives who don’t know what they’re actually talking about, but get paid for it like royalty of old, it means “totally secure” after hearing something from the IT department about security and SSL 3.0…
I laughed really hard at this comment. What a Joke of a company, with or without their typo.
“While we believe that our systems are very secure, including SLL encryption,”
Also:
” we have recently engaged multiple outside security firms ”
What firms? Geek Squad? HAHAHA what a joke.
I would guess they engaged multiple firms but sufficient time hasn’t passed for them to actually document what they’ve found.
If the company just hired the firms yesterday, you can’t knock the firms for not having a report back to the company in time for its press release.
Secure Local Loop. It’s SSL for your loopback connection. That way you can be assured that connections made from your server back to your server are verified, secured, extremely robust, and use the latest technology from your SSL certificate vendor.
Or it’s just a typo.
At least Michael Robinson responds back with a decent answer to the question
The price of these is really amazing – a credit card number is almost worthless (way too much supply to demand) compared to the damage that can be done to the user holder.
If park-n-fly can’t figure out where they’re compromised, it means they’re probably still compromised (so use your credit cards there accordingly).
Brian,
The snapshot has an odd entry:
“Visa Metabank
Dump or cc of this particular bank (BIN) cannot
be replaced or refunded”
Translate please.
It’s a pre-paid Visa, and the note means that purchase of data is non refundable (probably because it’s hard to ensure there are any funds left).
The 6th comment, from dzy, is spam or worse. Someone should yank it.
My apologies for the spammy looking comment but I tend to be very protective of my email… which is why to my surprise when I got an google alert that my email was on the db30 site with from the looks of it – 15 different types of hashes.
I can’t find any information about that site and why they would post different hashes of my email.
Obviously it has something to do with logins…. but I’m perplexed as to what or why.
The forum posts on the site look strange as well.
Hey, I’m glad you randomly mentioned this. Tonight, I have spent hours trying to figure out what this site is. Like you, I found my Email information there.
At first, I thought the hashes were of the Email addess itself, but a quick check found they were not.
It’s driving me crazy because I’m hitting nothing but dead ends.
If anybody could be of help, I would appreciate it. After hours, I’m still not sure what exactly the site is used for.
I’d be concerned it’s a Russian-owned (supposedly) domain name . Second, it was created: 2013-09 (what a record–1.3 years in existance–that’s somewhat similar to trusting a 1.3 year-old child). Etc.
http://whois.domaintools.com/db30.com
Yep! It’s Russian for sure 😉 And it contains nothing except hashes of “plaintext”. And we DO NOT COLLECTING anything. Any appearance of any information on this site means that SOMEONE was searched for it or previously posted on pastebin etc. That’s it. No leaks or “hacking”. Cheers!
Where can I go to learn more about this particular breach?
You should check out the websites https://haveibeenpwned.com/
https://breachalarm.com/
and
https://pwnedlist.com/
Ah – this is what I was looking for. Any idea why the discrepency between the three sites are?
One says two sites with no password – one says 3 sites 1 password – one says two sites with 1 password.
I keep thinking about what Hector Monsegur said on Charlie Rose a couple days ago.
“there is no security”
I really don’t see how there is anything these companies can do, especially giant ones like Sony, They have to receive and make connections to do business.
He says the only way to secure your company, is not by hiring contractors, or some IT guys to install or configure software, whom you also have to trust. These guys are always turned like Edward Snowden. The only way is by educating all your employees to learn how to manage their passwords, and keep their own business machines secure, themselves. And I agree.
I always say, computer education should be considered primary education, between math and english, starting with kindergarten. Especially to make our country secure.
Computer education should be as important as math and science but the problem is even if everyone was taught how to identify a compromised website, email address, etc., the bad guys are always one step ahead of the good guys. The average person could never be as smart as they are or keep up with the new ways they figure out how to be bad.
The thing is, there never has to be total security – there has to be enough that the business can fulfill its long term objectives without losing data or money enough to threaten its survival.
Usually that flies in direct conflict of the CEO gets unlocked unrestricted access and most employees treat their work computers the same as their home computers. If the workers can do whatever they want the same as at home, your network is not secure.
Ahhh, the things breached companies say. You can tell when the business folks are not talking to their IT folks and vice-versa. The Sony CEO characterized the GOP hack as an IT matter. Bet the business folks disagree. Park n Fly thinks they can identify their vulnerability by researching every claim of fraudulent card use. Bet the IT folks disagree.
Any possibility this is related to Charge Anywhere breach?
“Unlike card data stolen from main street retailers, which can be encoded onto new plastic and used to buy stolen goods in physical retail stores — cards stolen from online transactions can only be used by thieves for fraudulent online purchases. ”
I dont think that this statement is correct, I am pretty sure you can create a valid card with the 16 digit PAN which I assume is in the dump information
Actually the dump of the 16 digit PAN is not sufficient. The magstripe includes another “CVV1” number which is not the PAN and is not the CVV2 printed on the back. This rudimentary bit of security separates the swipe uses of the cards from the I’m-looking-at-it uses. The target style dumps generally included the PAN and the CVV1, which of course the bad guys want to make fake magstripe cards. I don’t know about this dump in particular. Anyway, EMV is 100x more secure than this silly magstripe system.
Mr. Krebbs should research and write an article about fraud known as false CEO or fake president scam (in French, fraude au faux president). It’s a nasty one and targeted companies often end up losing millions of EUR (for instance, the tire maker Michelin is one of the latest victims of this fraud). and coppers across EU countries are struggling to discover who’s behind this scam. Understandably, there is a lack of publicly available information since victims aren’t that keen to get into the spotlight.
I appreciate how well researched articles by Krebs are and frequently make reference to this site.
However far too many of the comments are time-wasting speculation. It’s ironic how those who know the least voice their opinions most loudly.
What can we do to eliminate the spam on this site?
And your post is highly technical and contains awesome informative information ? Some of these posts can be considered brainstorming for some, educational and enlightening for others.
It seems that your “above all of this”, minus your spam post.
Rather than attempting a flame war, how about a well done Krebs and move on?
I recently made a reservation with Park n Fly. A few days later, several fraudulent charges were attempted on my credit card. Et voila!
What can possible go wrong they have SLL security.
Possible ongoing Wells Fargo hack for whole month december including actual lost of cash from customer accounts. May be related to Sony hack excepts money transits Mexico then Venz, then who knows after. Some signes point maybe Iran.
Tend Thousands accounts maybe. Possible hac of teller machines suspected but the how is not yet known. Advise additional detail sare they become available please.
My plan is far more secure. Each credit card is issued with its own laser-equipped satellite. Whenever fraud is detected the satellite blasts the perpetrator with a razor-thin beam that etches the word “thief” on his forehead in 27 different languages. Using advanced optics, if the system sees that the person has already been branded then the next laser session fries him into bio-friendly ash that can be sprinkled on crops or high end lattes, imparting an extra zing. In addition, the reflected light from all the satellites will create so much ambient light that we’ll save trillions on street lamps and eliminate conspiracy theories about why the lamps go off when you walk past. This is fool proof.
Had two cards compromised in the last few weeks.
Not sure why it didn’t occur to me until I read this, but PNF is the ONLY place I used both cards.
Suspect that not a breach of Park n Fly, but rather carders validating compromised cards with low value transactions.. Easy to confirm were any of the transactions initiated by card owners?
My son’s Visa card was hacked right after he made reservations two weeks ago at Park n’ Fly in Nashville TN. It was the only transaction he made all month on his card. So someone really needs to investigate Park n’ Fly and warn there customers.
I worked for a CC gateway company called 6 card solutions, park n fly was one of there customers….at least 3 years ago.
The breach could be higher on up the ladder, somewhere between the reservation website and 6card….