In a statement released this morning, women’s clothier chain bebe stores inc. confirmed news first reported on this blog Thursday: That hackers had stolen customer card data from stores across the country in a breach that persisted for several weeks last month.
Bebe stores said its investigation indicates that the breach impacted payment cards swiped in its U.S., Puerto Rico and U.S. Virgin Islands stores between Nov. 8, 2014 and Nov. 26, 2014. The data may have included cardholder name, account number, expiration date, and verification code.
The company emphasized that purchases made though its web site, mobile site/application, or in Canada or other international stores were not affected, and that customers should feel confident in continuing to use their payment cards in bebe stores.
“Our relationship with our customers is of the highest importance,” said bebe CEO Jim Wiggett, in a statement. “We moved quickly to block this attack and have taken steps to further enhance our security measures.”
Predictably, bebe stores is offering free credit monitoring services for one year to customers impacted by this incident, even though credit monitoring services do nothing to help consumers block fraud on existing accounts — such as credit and debit card accounts that may have been stolen in this breach.
Consumers still need to keep a close eye on monthly statements, and report any unauthorized charges as quickly as possible.
On Thursday, KrebsOnSecurity reported that several banks had complained about a pattern of fraudulent charges on customer credit cards that all had one thing in common: They’d all been used at bebe locations across the country. One bank contacted by this reporter also found several of its cards for sale in a brand new batch of stolen cards pushed onto the market in an underground “carding” shop, cards that all turned out to have been used at bebe stores during a two week period in the latter half of November.
Interestingly, when I first accessed the breach notification page at bebe stores this morning, Kaspersky Antivirus flagged the page as a possible phishing attack (see screenshot below). This is most likely a false positive, but I thought it was worth mentioning anyway.




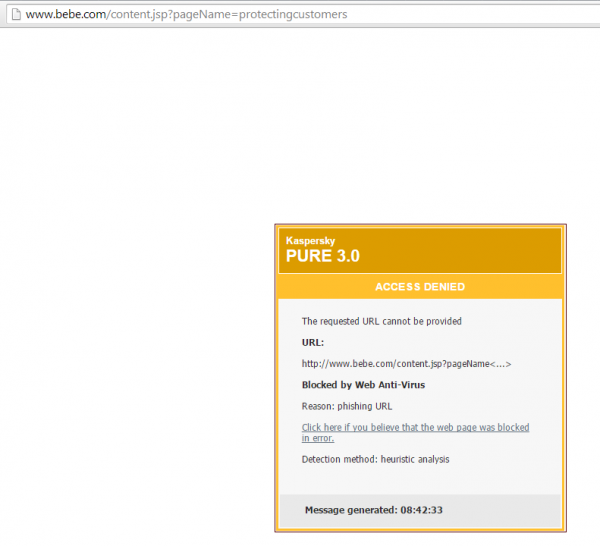

Not to go off topic here , but what is your opinion on Kaspersky Antivirus verses say Bit Defender which scores very high on the A/V Comparison website ?
Considering Kaspersky’s close ties with Putin and former KGB, I don’t go near it.
Since credit monitoring services really are worthless, surely there must be a market opportunity for some other type of service that assures customers affected by breaches like this one other than LifeLock.
Zander Insurance Group and other insurance groups sell Identity Theft policies that help you handle the process of recovering your identity and protect you from financial loss. It looks like LifeLock offers similar services now, but limits your recovery costs to $1 million, while Zander’s provides you with $1 million in reimbursement protection and unlimited identity recovery services.
Most likely a false positive, since the site will be at the top of a few “bad” web site lists for a while.
Kaspersky doesn’t do too bad on both the AVC and AV Test web sites.
Hey Brian I am surprised how you get this first hand information as on when they banks see a pattern of fraudulent CC or DC transactions they will reach you…I assume your passion towards security makes them to reach you to further see n confirm the links/sales of the breached info in background forums…again when is the end for this kind of retail breaches so for 25+ came to light there could be hundreds that went stealth
Often company public relations related to information security is STUPIDLY humorous related to the ONGOING breaches at company-after-company, “customers should feel confident in continuing to use their payment cards in bebe stores”…trust us till the next breach so we can tell you this statement, again.
Is it ironic yet that it is safer to shop online than it is to use your credit or debit card in the physical store?
I am so sick of hearing these breached companies saying “Our relationship with our customers is of the highest importance,” …If that were TRUE then they would have encrypted ALL customer data on their servers in the first place…any thing less tells me they are not being TRUTHFUL..
.One of the first questions to a CIO for the company is ‘whether ALL data was encrypted on the server(s)?…if not..Then ..ALL.. other comments from that person representing the company should be considered BS. Anything about being concerned about the Customer is just ..FEEL GOOD.. words for the customer and re-marketing purposes for the company…”
For those working in IT in vulnerable companies…monitor “out of band IP addresses” there can be dragons lurking there.
Does anyone know the purported reason why companies even keep credit card numbers?
If I were running a business, I would send the data through the payment system as is required for it to work, but would never dream of actually storing it.
I can’t think of any reason why any of this should be stored by a retail outlet. It should be made illegal, with a very short conformance period.
Pat, they’re not stealing the cards from storage. They’re planting malware on the cash registers that snags the card data as it’s being run through the transaction on the way to being processed.
How many of the 200 +/- stores were represented in the compromised data set? Absent information (or even an estimate) on how many people were affected, which stores were infected, how large was this breach?
We know there was at least one store in each of the US, PR, and USVI. Were there only three? That could be done by one person on a vacation. If many more, think of the organization size to physically compromise each within such a short span of time. OR was it a POS virus that was pushed out to many terminals auto-magically? Perhaps as part of a compromised or faux-maintenance effort?
Rather than dishing public relations pablum it would be refreshing to hear from Bebe the facts, or even a promise that facts will be made available as they are known. Or, are we (you know, the consumers) all just mushrooms?
Jonathan @nc3mobi
Nate, I have to agree with you. It’s the same line every time.
And that security is of the utmost importance blah blah…
If that were true, the breach would not have occurred.
“We moved quickly to block this attack and have taken steps to further enhance our security measures.”
Obviously not. How many weeks went by with the attackers being there unnoticed?
Each store takes weeks and months to detect IOCs.
I believe most of these stores were PCI compliant too?
That too is a big fat fail, compliance does not equal security.
These payment networks need to be air gapped or something, the malware it seems has to get in somewhere externally (like contractor maintenance accounts) and the biggest problem here ironically is that we network everything these days.
We’re dumb, everything does not have to be connected…
Another similar name and location. Wonder who is doing this or releasing the data.