A new report from the U.S. Treasury Department found that a majority of bank account takeovers by cyberthieves over the past decade might have been thwarted had affected institutions known to look for and block transactions coming through Tor, a global communications network that helps users maintain anonymity by obfuscating their true location online.
The findings come in a non-public report obtained by KrebsOnSecurity that was produced by the Financial Crimes Enforcement Network (FinCEN), a Treasury Department bureau responsible for collecting and analyzing data about financial transactions to combat domestic and international money laundering, terrorist financing and other financial crimes.
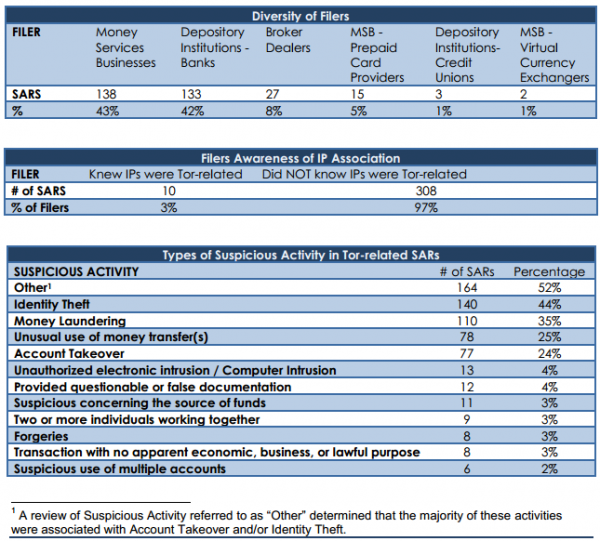
In the report, released on Dec. 2, 2014, FinCEN said it examined some 6,048 suspicious activity reports (SARs) filed by banks between August 2001 and July 2014, searching the reports for those involving one of more than 6,000 known Tor network nodes. Investigators found 975 hits corresponding to reports totaling nearly $24 million in likely fraudulent activity.
“Analysis of these documents found that few filers were aware of the connection to Tor, that the bulk of these filings were related to cybercrime, and that Tor related filings were rapidly rising,” the report concluded. “Our BSA [Bank Secrecy Act] analysis of 6,048 IP addresses associated with the Tor darknet [link added] found that in the majority of the SAR filings, the underlying suspicious activity — most frequently account takeovers — might have been prevented if the filing institution had been aware that their network was being accessed via Tor IP addresses.”
FinCEN said it was clear from the SAR filings that most financial institutions were unaware that the IP address where the suspected fraudulent activity occurred was in fact a Tor node.
“Our analysis of the type of suspicious activity indicates that a majority of the SARs were filed for account takeover or identity theft,” the report noted. “In addition, analysis of the SARs filed with the designation ‘Other revealed that most were filed for ‘Account Takeover,’ and at least five additional SARs were filed incorrectly and should have been ‘Account Takeover.'”
The government also notes that there has been a fairly recent and rapid rise in the number of SAR filings over the last year involving bank fraud tied to Tor nodes.
“From October 2007 to March 2013, filings increased by 50 percent,” the report observed. “During the most recent period — March 1, 2013 to July 11, 2014 — filings rose 100 percent.”
While banks may be able to detect and block more fraudulent transactions by paying closer attention to or outright barring traffic from Tor nodes, such an approach is unlikely to have a lasting impact on fraud, said Nicholas Weaver, a researcher at the International Computer Science Institute (ICSI) and at the University of California, Berkeley.
“I’m not surprised by this: Tor is easy for bad actors to use to isolate their identity,” Weaver said “Yet blocking all Tor will do little good, because there are many other easy ways for attackers to hide their source address.”
Earlier this summer, the folks who maintain the Tor Project identified this problem — that many sites and even ISPs are increasingly blocking Tor traffic because of its abuse by fraudsters — as an existential threat to the anonymity network. The organization used this trend as a rallying cry for Tor users to consider lending their brainpower to help the network thrive in spite of these threats.
“A growing number of websites treat users from anonymity services differently Slashdot doesn’t let you post comments over Tor, Wikipedia won’t let you edit over Tor, and Google sometimes gives you a captcha when you try to search (depending on what other activity they’ve seen from that exit relay lately),” wrote Tor Project Leader Roger Dingledine. “Some sites like Yelp go further and refuse to even serve pages to Tor users.”
Dingledine continued:
“The result is that the Internet as we know it is siloing. Each website operator works by itself to figure out how to handle anonymous users, and generally neither side is happy with the solution. The problem isn’t limited to just Tor users, since these websites face basically the same issue with users from open proxies, users from AOL, users from Africa, etc.
Weaver said the problem of high volumes of fraudulent activity coming through the Tor Network presents something of a no-win situation for any website dealing with Tor users.
“If you treat Tor as hostile, you cause collateral damage to real users, while the scum use many easy workarounds. If you treat Tor as benign, the scum come flowing through,” Weaver said. “For some sites, such as Wikipedia, there is perhaps a middle ground. But for banks? That’s another story.”




I think this article just points out how unprepared the banking industry was and rushed too soon into the Internet and electronic banking without first knowing what they were doing. They know all about common fraud as its been with the industry since the start of banking. It may have been good business for them, but costumers have been drawn into this mess. We as costumers are paying the price in spite of their ‘guarantees’ to hold us harmless.
As a consumer, you have Regulation E protection. Which equates to consumer over protection and all but removes you from being responsible for your own account. What people don’t realize is that they have this protection and the increased scrutiny and regulation compliance banks are under. The banking industry is highly competitive. If the banks don’t offer the online ability they lose a huge source of income. The everyday account holder also doesn’t realize that banks can’t control the transactions they receive and they have very few ways of identifying incoming transactions as fraud. If they started blocking transactions then they would most likely upset their customers and possibly violate federal regulations. Don’t blame the banks because of the actions of criminals. Blame the criminals!
Exactly! Focus needs to be on identifying and jailing the criminals, not on protection.
The crims will run you ragged if you try to win by only playing defense.
This is true in every conflict from fighting wars, to fighting viral infections.
Take out the enemy or it may recover & come back stronger, having learned from your best attack.
Brian, remember few years ago when two rootkit sellers were competing, one had a way of disabling and uninstalling the competitor’s exploit and installing their own.
Looks like law inforcement could move towards something similar.
It’s a battle of technology, so either you are smarter & more effective than the bad guys, or you’re losing.
Right now, the good guys are losing. ;^(
I disagree. Try walking into a bank with your face covered and no ID and asking to access your account. That is essentially what anonymous access is. I think the banks have every right to demand that you access it conventionally.
In more than 20 years, I’ve never had any security problems related to my online banking. I thought my uncle was a mad scientist way back in the early 1980’s because he managed his banking and credit card statements through the online networks CompuServe and Prodigy. Nobody in the family knew what the **** he was rambling about.
You as a consumer are paying nothing. Banks and credit card companies are liable for all fraud liability.
That’s not true. We all pay for these fraud charges indirectly in form of fees backs impose on us.
Indeed. Banks don’t make the profits they do being altruistic coverers of bank fraud – they of course pass those costs on to their customers and later less dividends for their shareholders.
It’s a big world and the internet is open to almost anyone. One way to guarantee being wrong is to talk in absolutes.
Indeed, in the case of your specific statement, I’m not aware of anywhere that it is correct. Credit cards are generally the most consistent as they all hail from a small number of companies that all belong to the PCI but even then, depending on the way transactions are processed, the consumer can lose out.
Sure you can get around the TOR node by using a online proxy service in the location bar and then accessing the bank account that way.
Its trivial to download all tor exit nodes and put it in a firewall but very few people understand this is useful.
Tor exit nodes come and go all of the time – simply downloading one list and dropping it in without regularly updating the list won’t be helpful.
And for that matter, there is always a chance that a new exit node has appeared which is not in the list, so blocking all known Tor exit nodes is not a guarantee..
Still better than doing nothing!
There are only 4,294,967,296 possible IPv4 addresses, which easily fits on a single 4 GigaByte flash chip, so currently manufactured routers should have this chip to be able to program in Go / NoGo flags for all possible IPv4 addresses.
However, this could never work with IPv6 …
And there are trillions of possible domain names …
And proxie services …
And botnetted computers and servers compromised at a hosting service or a business could be programmed to serve as Tor exit nodes for the duration of a data grab.
..And lions and tigers and bears, oh my!!
They sent this to banks with no instructions or recommendations whatsoever. It’s like “there’s some really bad stuff out there. Good luck and godspeed”. Completely useless to us.
Phil, if you don’t have tech staff competent to interpret and act on that you should not put your bank on the ‘net. It is irresponsible and a disservice to your depositors and shareholders. If the OCC had any gumption they’d make sure banks were competent to assess and mitigate risks of being online.
Lots of security companies have figured out how to detect Tor Networks. Similarly to browser fingerprinting and behavorial analysis used in context aware authentication, you can do a contextual analysis on the browser without actually needing the nodes.
Browser traffic from Tor has it’s own unique properties that alone don’t necessarily mean a lot, but when put together you can detect Tor with a remarkably high level of accuracy. These tech companies are trying to get banks on board with varying levels of succes.
Good grief, we weren’t even a banking service and we blocked many things like this on our gateway; mostly just for HIPAA conformity.
I just can’t believe how stupid the IT people are at such institution. if they even have any, which most I know, don’t. At least they setup Barracuda appliance or similar gateway, and hopefully do it right.
interesting. i use a VPN to enhance anonymity, was wondering why all the google sites were suddenly pushing CAPTCHAs in my face lately
If a FI gets hacked by someone using Tor, blocking Tor would not have done any good. It would have only slowed the process down. If someone manages to leap over the 100 other hurdles that should be in place, then Tor is merely the method to avoid prosecution. This type of security is very broad (often impacts the availability of services to legit users), and very much “front line”. This is probably why FIs have not put much focus on it. The article event states this fact (that it’s an ID theft issue which usually stems from other phishing and social engineering attacks directed at the customers not the FIs)…see the quote from Nicholas Weaver in the article.
But many armchair quarterbacks want to point to $25M in losses over 13 years and accuse IT of being stupid. Nicely done.
Comparing what FIs do to what someone in healthcare does is not even the same game. It’s like pointing to an offensive play in the NFL and then trying to apply it to baseball. Our business models and the regulation we are under is completely different. There may be some overlap in practices (meaning the methods we use), but it stops there….just my 2 cents.
All I can see here is a cavalier attitude towards a consumers money. The financial industry does not care, the retailers don’t care, and of course, government could give a damn.
What it all boils down to is that folks, we are on our own.
@stevieod, while I empathize with your sentiment, I think your summary is a bit harsh. By nature of large industry, corporate, and government bureaucracy, they have always been slow to adapt to technological advancements. These issues affect all of us and even the most pessimistic can agree that when money starts to be lost, people will pay attention.
The fact of the matter is that 2014 has seen an unprecedented level of sophisticated breaches, many far more damaging than a lot of folks had anticipated. In all seriousness, the last 12 months will be studied for years to come. There are countless programs being developed in the public and private sector at this time, many initiated in just the last six months, that will help better protect us in the near future.
While most of these programs are widely under-reported in the news media due to their lackluster level of click-bait, rest assured that you will continue to hear more about them throughout 2015-2016.
If you are a online newsphile might I suggest following the ‘Computer Security’ section of Google News.
blocking Tor would not be a solution.
firstly, the crooks will simply switch to public hotspots, open proxies, VPN or zombie computers.
secondly, it is impossible to maintain an up to date list of working Tor exit nodes in order to block them.
the banks should focus on suspicious user activity; when I traveled to Thailand first time in my life and started to pay with card there, I was expecting a call from my bank because they should have seen it as a strange activity, shouldn’t they? but nothing happened … and I was very displeased
I was wondering if some of the websites which only operate locally will block all ip address from China, Russia and USA. Will this help them to decrease atleast 90% of threats.
The old saw is that cars get used in bank robberies too, so why not ban them? There are many legitimate uses for anonymity; FinCEN’s ability to function as a police-spy agency is greatly facilitated by the abolition of anonymity (i.e. blanket Tor block). On the other hand the state of many https interfaces exposed by banks , etc. to the Internet — as judged by say SSL Lab’s testing service, or reports of criminal activity on this web site — is horrifying bad in many cases. And as many others here have noted, achieving anonymity through other means is likely well within the means of actors capable of initiating an illegal transaction, or successfully attacking those weak websites for more general criminal purposes.
The FinCEN report that Krebs relates here is simply bad. Correlation is not causation, and there is no mechanistic understanding or model of the known attacks in FinCEN’s report. Hence, they are totally unable to provide any meaningful long-, medium-, or short-term guidance on how to secure a bank’s infrastructure against cybercrime.
An actual part of the problem, unlike the Tor network, is the US Congress’ ESIGN law from 2000 (heavily supported by the banks at the time), where Section 101(c)(1)(C) uses the phrase “reasonably demonstrates” without any reference to the technical basis for “reasonable”, to make electronic “signatures” have force of law. This is a far more significant source of the disaster that is modern electronic financial “security” than the Tor network. The law legalizes all sorts of things in the way of authentication and non-repudiation that should be illegal. The technical objections voiced at the time are now drowned out of most search engines by the lawyer’s guidance on the law.
Okay, here’s another two cents worth. About the social engineering. Have any of you checked you own name out there? Not even once? Especially the report writers. You could probably find everything down to your shoe size out there. Without even the least security it’s all listed somewhere. Sure, you may have to go to a pay site, but its there, down to your last e-mail this morning. All in less then .012 sec.
Don’t blame the mom and pop, but the collectors, who try to make money off what you may do next. But then how would google profit off selling data to a hardware store that would like to know if I want to buy nails? Self awnsered, right?
Who would use for this? Its not 2008 anymore and Tor’s on some shaky ground. Would be better to just use a socks5 or two, would be faster and just as secure.
“Some sites like Yelp go further and refuse to even serve pages to Tor users.”
Yes and why not? When you see one thousand malicious attempts for every one real user via Tor – it becomes simple economics. Same rule applies to traffic from China, Russia etc.
Why not allow Tor but require two-factor authentication via Yubi, SMS, or google authenticator. Anyone tech savy enought to use Tor should be able to set up two-factor authentication.
Yep. Blocking Tor is useless in protecting access to online banking. People who come in use the front door and have a key. In other words, if someone manages to steal money from accounts using online banking they have gained credentials somehow…..and that is either by hacking the bank (highly unlikely and AFAIK never been done), or hacking the customer. In almost every case customers get malware, get keylogged, and then the attacker has their credentials. Two-factor is a great tool, but not everyone uses it. In some cases call centers get social engineered in to resetting an account for someone who merely has access to the customers email and can then reset the password, etc.
That said, all this whinning about Tor and FIs not blocking Tor is a load of ignorance that stinks to high heaven. It’s proof that people who are being critical don’t fully understand the eco-system.
As a side note, most banks are already blocking malicious IPs and there’s a few public lists in the industry of these that get shared. Some are already known Tor nodes, and some are not. Most online banking also does transaction based security, GeoIP filtering as well as layered MFA + two-factor.
Who cares if an ip address belongs to Tor? If you block it, the criminal uses another service to get an ip address for his communications with the target.
The real problem with account takeover is that financial institutions are not in control about the financial transactions.It’s just risk management: “What is the financial risk when we execute this transaction?”
The answer to this question solved all account takeovers in a large dutch bank. And their customers do use Tor, no problem at all.
$24 million? Isn’t this really a drop in the ocean to the overall figure?
Also many banks here in the UK (and I assume elsewhere) require you to tell them if you are leaving the country for a while so that they will allow transactions from that region during your visit. Would it not be beneficial for the same to be done with the online banking features. This would not necessarily mean an outright block but maybe read only rather than allowing you to make transfers when coming from an IP in a country they wold not expect.
Yes and no. Banks are supposed to file these reports all the time when they see or suspect fraudulent activity, but I’m told that’s far from the reality. So these SARs are pretty dramatically under-filed. Also, everything is relative. Yes, check fraud costs way more than cyberfraud. Does that mean we shouldn’t care about stopping cyber fraud? I’ve written over 100 stories about small businesses here in the US that have been robbed of their ability to make payroll or have gone bankrupt because crooks broke in via a banking Trojan and emptied out their operating accounts. Now we can say the theft of $500k from a single company is not such a big deal in overall scheme of things, but I assure you it’s a huge deal to the bank and more importantly to the victim organization.
http://krebsonsecurity.com/category/smallbizvictims/
Brian, I’m sorry….but to claim that SARS are not filed is just wrong. First of all they are a legal requirement for us. Secondly staff are trained on a continual basis and made aware of this (among other) requirements frequently. And finally (most importantly) we are audited by both our private auditors and the FFIEC or corresponding examination committee yearly or more on the reporting of suspicious activity. It’s incredibly easy to determine if a FI is avoiding or failing to file SARs. If caught not filing this could seriously impede an institution through an increase in insurance costs, fines, or lowered CAMEL etc.
Unless you can document what you said, I would suggest you kindly not say such a blanket statement.
John,
Glad to hear your institution is on top of things. Certainly doesn’t mean that’s the case across 20,000 + US financial institutions and money service businesses. Do you really expect me to name names in this comment? I’m relaying what sources have told me, not providing an audit report.
See:
http://www.justice.gov/usao/nys/pressreleases/December14/ThomasHaiderComplaintPR.php
I’ll respectfully call your bluff on that one. SARs are no laughing matter. The IRS has a stake in them so to think that the government would look the other way or not drop the hammer when they’re within their legal right to is a bit of a stretch…I agree they’re not always filed. Human error being the cause, not a lack of care or failure of oversight or banks disregard for the law. Also, a SAR doesn’t equal fraud every time. In fact most the time it’s not. Many legit transactions require the filing of a SAR. We have guidelines when they are required (hence it’s easy to audit transactions to see if a bank is in compliance). The SAR requirements are known by criminals and they are smart enough to avoid them too.
I doubt you’d have a government source giving you this data and if so shame on them. To lead the public to believe banks are wanton about their risk management is to lead them to believe the system cannot be trusted. The entire purpose if the FFIEC is to privide trust, and a layer of accountability so that consumers don’t fear their deposits being wiped away.
Again, maybe this is so with regular banks, but there are thousands of organizations that are money service businesses that move tons of money around for cyberthieves and yet traditionally have done a pretty poor job of documenting fraud traversing their networks.
That I can agree with. But to that point we are no longer making a correlation with online banking, Tor and fraud etc. Your first statement was somewhat accusatory toward FIs that we have a disregard or care less about fraud and the fact that we don’t submit SARs is evidence, and further evidence we don’t secure our public facing services like online banking. That’s not fair. Nor true.
I agree check cashing services might skirt the SAR (they are criminally responsible most likely if they do so intentionally). But even then….the IRS takes this pretty serious. SARs primary use is to identify money laundering or tax evasion. I doubt you would get away with it for long before the tax arm shuts you down.
John,
Per my point, MoneyGram is a money transfer business, and their compliance officer just got sued by the USDOJ for failing to file SARs
http://www.justice.gov/usao/nys/pressreleases/December14/ThomasHaiderComplaintPR.php
Thanks Brian. I still think it’s incredibly rare and probably not “largely un-filed”.
Thank you for the 60 minutes piece, and this article too! I still remember the first time I used Tor to do online banking over an open wifi network. Here I was, trying to be more safe in that activity than before – and my banking site really gave me some grief about it. And yea, I’m glad they did, kinda. But at the same time, it really made me think – gee, my bank’s site would actually be easier to use & access in this moment if I was *less* safe on this wifi. That was a pretty strange moment.
I work in a science lab. In the 80’s we *dreamed* of the day the network would reach all parts of the building/site/country/planet. None of us considered basic evolution – opportunists fill all parts of a new niche. These are the cybercriminals, I guess. We had no idea this would happen.
Oh, ya, never leave your car keys, wallet, purse, etc. with a random stranger you meet, and never online bank in a coffee shoppe.
So, I guess you should have Snort looking for any Tor-related IP transactions on your LAN?
Is this a real study? It seems kind of flaky.
I bet more than 52% of fraudsters use https. Maybe we should just block all encryption ….
Only 133 banks are filing SARS ???
The sample sizes (6,048 SARS) seem way to small for legitimate conclusions.
Did you know that most bank robbers use cars ??? And that the rest use the internet?
Before the internet – it was telephones and before that it was mail. (They still call it Mail Fraud).
And yet another jab at TOR to say “see they bad” to get something to shut it down. Thanks federal government.
They are still on the child porn chant and drug dealing chant … so let’s add the Bank Fraud chant.
Anything created can be used for good or evil… Until the outlaw everything due to able to be used for evil… then I’ll start to actually listen and pay attention. Maybe if the fed’s start the outlawing with actual paper money… you know cause it is used in basically everything evil…
Excellent point! But the Feds fund Tor last I heard. I think it depends on the agency, but you have a point.
“…FinCEN said it examined some 6,048 suspicious activity reports (SARs) filed by banks…”
“Our BSA [Bank Secrecy Act] analysis of 6,048 IP addresses associated with the Tor darknet…”
Is it just a coincidence that these two numbers that should be unrelated are equal?
If in those 6048 SARs, “Investigators found 975 hits”, how does that constitute “a majority of bank account takeovers”? It looks closer to 1/6 than to 51%. The graphic “Tables from the FinCEN report” shows 52% of the Tor-related SARs were “Other” (which according to the footnote therein were mostly Account Takeovers), not that 52% of the “Other” SARs were Tor-related.