The Lizard Squad, a band of young hooligans that recently became Internet famous for launching crippling distributed denial-of-service (DDoS) attacks against the largest online gaming networks, is now advertising its own Lizard-branded DDoS-for-hire service. Read on for a decidedly different take on this offering than what’s being portrayed in the mainstream media.
The new service, lizardstresser[dot]su, seems a natural evolution for a group of misguided youngsters that has sought to profit from its attention-seeking activities. The Lizard kids only ceased their attack against Sony’s Playstation and Microsoft’s Xbox Live networks last week after MegaUpload founder Kim Dotcom offered the group $300,000 worth of vouchers for his service in exchange for ending the assault. And in a development probably that shocks no one, the gang’s members cynically told Dailydot that both attacks were just elaborate commercials for and a run-up to this DDoS-for-hire offering.
The group is advertising the new “booter service” via its Twitter account, which has some 132,000+ followers. Subscriptions range from $5.99 per month for the ability to knock a target offline for 100 seconds at a time, to $129.99 monthly for DDoS attacks lasting more than eight hours.
In any case, I’m not terribly interested in turning this post into a commercial for the Lizard kids; rather, it’s a brain dump of related information I’ve gathered from various sources in the past 24 hours about the individuals and infrastructure that support the site.
In a show of just how little this group knows about actual hacking and coding, the source code for the service appears to have been lifted in its entirety from titaniumstresser, another, more established DDoS-for-hire booter service. In fact, these Lizard geniuses are so inexperienced at coding that they inadvertently exposed information about all of their 1,700+ registered users (more on this in a moment).
These two services, like most booters, are hidden behind CloudFlare, a content distribution service that lets sites obscure their true Internet address. In case anyone cares, Lizardstresser’s real Internet address currently is 217.71.50.57, at a hosting facility in Bosnia.
In any database of leaked forum or service usernames, it is usually safe to say that the usernames which show up first in the list are the administrators and/or creators of the site. The usernames exposed by the coding and authentication weaknesses in LizardStresser show that the first few registered users are “anti” and “antichrist.” As far as I can tell, these two users are the same guy: A ne’er-do-well who has previously sold access to his personal DDoS-for-hire service on Darkode — a notorious English-language cybercrime forum that I have profiled extensively on this blog.
As detailed in a recent, highly entertaining post on the blog Malwaretech, LizardSquad and Darkode are practically synonymous and indistinguishable now. Anyone curious about why the Lizard kids have picked on Yours Truly can probably find the answer in that Malwaretech story. As that post notes, the main online chat room for the Lizard kids (at lizardpatrol[dot]com) also is hidden behind CloudFlare, but careful research shows that it is actually hosted at the same Internet address as Darkode (5,38,89,132).

A suggested new banner for this blog from the jokers at black hat forum Darkode, which shares a server with the main chat forum for the Lizard kids.
In a show of just how desperate these kids are for attention, consider that the login page for LizardStresser currently says “Hosted somewhere on Brian Krebs’ forehead: Donate to the forehead reduction foundation, simply send money to krebsonsecurity@gmail.com on PayPal.” Many of you have done that in the past couple of days, although I doubt as a result of visiting the Lizard kids’ silly site. Anyway, for those generous donors, a hearty “thank you.”
It’s worth noting that the individual who registered LizardStresser is an interesting and angry teenager who appears to hail from Australia and uses the nickname “abdilo.” You can find his possibly not-safe-for-work rants on Twitter at this page. A reverse WHOIS lookup (ordered from Domaintools.com) on the email address used to register LizardStresser (9ajjs[at]zmail[dot]ru) shows this email has been used to register a number of domains tied to cybercrime operations, including sites selling stolen credit card data and access to hacked PCs.
A more nuanced lookup at Domaintools.com using some of this information turns up additional domains tied to Abdilo, including bkcn[dot]ru and abdilo[dot]ru (please do not attempt to visit these sites unless you know what you’re doing). Another domain that abdilo registered (in my name, no less) — http://x6b-x72-x65-x62-x73-x6f-x6e-x73-x65-x63-x75-x72-x69-x74-x79-x0[dot]com — is hexadecimal encoding for “krebsonsecurity.”
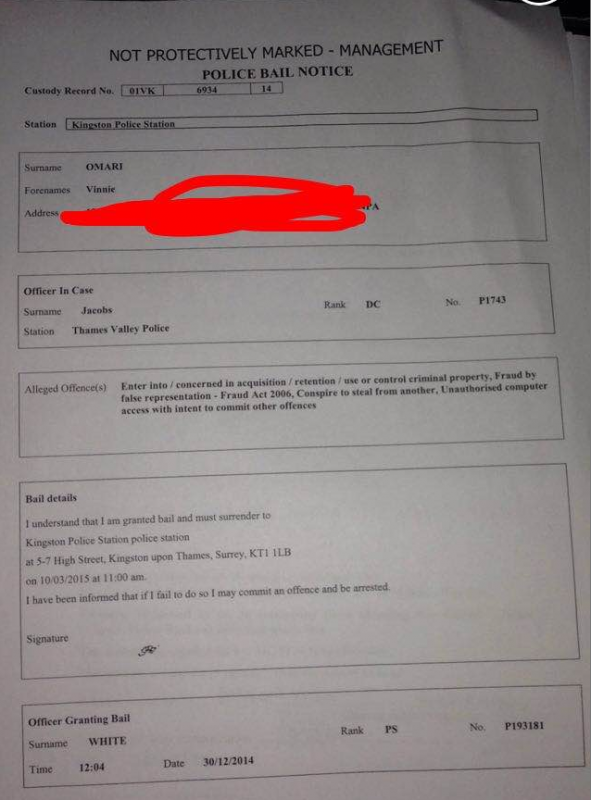
Last, but certainly not least, it appears that Vinnie Omari — the young man I identified earlier this week as being a self-proclaimed member of of the Lizard kids — has apparently just been arrested by the police in the United Kingdom (see screen shot below). Sources tell KrebsOnSecurity that Vinnie is one of many individuals associated with this sad little club who are being rounded up and questioned. My guess is most, if not all, of these kids will turn on one another. Time to go get some popcorn.
Happy New Year, everyone!




Congrats on a great 2014, Brian, and I look forward to reading more great work on Krebs On Security in 2015.
Regards,
Hi Brian,
Thanks for all the hard work,and congratulations! Popcorn indeed. I needed a good laugh and this story was just what the doctor ordered. Have a great new years.
Related:
https://www.youtube.com/watch?v=qRNlUjQ3Dvk
By out on bail they mean after breaking down in tears at potential prison he agreed to go home and rat out his friends by being an informant.
So VERY, VERY true.
You hit the nail on the head.
So many decisions, so little time …
Rat my friends out, or buy a gallon jug of KY jelly …
Which should I choose?
Priceless! Happy New Year to all the White Hats.
Abdilo Namangan
Hey Abdildo – spell your name correctly!
David Crees
Name: Abdilo, Notavirus, Surivaton, Grey Hat Mafias Bitch
Age: 15
Gender: Guy
Religion: Agnostic
State/Country:QLD, Australia
Time Zone:GMT +11
You forgot one important item.
Sexual orientation: Soon to be queer as a three dollar bill.
Is that supposed to be an insult or are you just 12 and retarded?
#LizardFail.
Now I would imagine that Vinnie is wetting his pants by now and is busy ratting out the rest of his crew like Sabu from LulzSec.
So his parents actually named him Vinnie and not Vincent? Wow. That’s one hell of a gene pool.
I wonder if there’s a parallel universe where it doesn’t turn out to be a bunch of stupid kids.
So … basically … these kids are calling themselves hackers but on a cursory inspection it appears that I, definitely not any kind of hacker or IT security er, expert, have a similar level of ability.
So is it that I’m a hacker or the “hackers” in question are just total failcakes 😀 I’ll leave the reader to pick the obvious answer to that one LEL.
Hint: it took Mr Krebs 24 hours to unmask these tits 😀
They’re not hackers really, they’re script-kiddies. The day DDosing makes you a hacker is the day breaking down a door with an axe makes you a locksmith
The Lizard Squad : is this what you all mean by a “dox”? Found it from a Google search.
http://www.phoon[dot]co[dot]uk
So much for my attempt at obfuscation. Try again.
http://www.phoon[dot]co[dot]uk
because im feeling generous heres some more fun intel for you to play with krebs
julius “ryan” kivimaki was also a member of the group HTP (http://www.exploit-db.com/papers/25306/)
he also had involvement with numerous high profile attacks/defacements against governments
that server you found the adobe source code on was under control of kivimaki
http://www.zdnet.com/article/mit-website-hacked-over-aaron-swartz-a-second-time/ << also kivimaki's work
kivimaki also was the perp behind the attack on nist, alongside one of the sources whom has given you information, an individual that goes by the name of ryan king, known handles are aurora, starfall, reiko, and numerous others (this individual had direct contact with kivimaki when he was arrested with the stolen cards during defcon in 2013, most likely the source that you spoke with)
i have tons of intel on these kiddies
Most people do, its not like they hide who did it, they publicly brag about what they do and if you happen to be in contact with the people then you find stuff out. I’ve known zeekill for like 2 years now, since a call with him, sirenfal and shoedad.
someone,
I thought starfall rang a bell. Take a look at: http://krebsonsecurity.com/2013/03/the-world-has-no-room-for-cowards/
Specifically (linked in the post): http://krebsonsecurity.com/wp-content/uploads/2013/03/arsattackbootertw.rtf
These people were also involved with and/or framed for the Deus Ex hack in 2011: http://krebsonsecurity.com/2011/05/anonymous-splinter-group-implicated-in-game-company-hack/
All these individuals originated from an IRC channel on a network called skidsr.us, which to my understanding partly evolved into HTP years later.
As far as I’m aware Ryan King is a little bit more on the ethical side, at least compared to Kivimaki and the Lizard skids.
Is he the same Starfall as the guy pretending to be a girl on Hackforums?
I wonder if the Lizard Squad was responsible for taking this site down for about 15 minutes about 945 AM EST time…did anyone else have a problem loading the website?
Yes, I had some temporary issues this morning as well.
I had issues as well, interesting take on the suggested reason…hmmm
http://money.cnn.com/2015/01/02/technology/security/krebs-lizard-squad/index.html
Looks like 2 are in in a cell already.
http://www.csoonline.com/article/2863968/cyber-attacks-espionage/two-alleged-members-of-lizard-squad-arrested-following-xbox-livepsn-christmas-attacks.html#tk.rss_news
in a nutshell;
To top it off, Finland’s National Bureau of Investigation (NBI) picked up another alleged member of Lizard Squad later in the week. The 17-year-old, known as “Ryan,” acted as spokesperson for the group in the aftermath of the Christmas attacks. Unlike Omari, Lizard Squad told The Washington Post that Ryan remains in jail.
Brian:
I have to make a confession. I might have started this whole journey for these kids when I did my naughty stuff neary 50 years go. (I am a 61 year old kid now).
In the 1960’s, when I was in the fifth grade in school, I learned how to fix TV sets on my own in my own shop that I put together myself (my father was an accountant and knew nothing of electronics).
I went to the town dump, picked up old TV sets, used my self tought electronc skills to fix them up, then sold them to my fellow classmates whose parents did not want them to have their own TV sets.
I wonder if I created the first round of spoiled electronicially fed kids who never wanted to go outside. 🙁
Mark
Looks like they might have been playing a bit this morning- the site was unavailable, presumably another of the continuing stream of DDOS attacks..
Nice to see you standing up to the kids, not enough do!
Lizard Squad are funny tbh.
These silly little kids, thing they are men. Utterly clueless about life.
I hope they enjoy picking up soap in the showers answering to a 6 ft 25 stone ladies man known as butch.
Ayy this nigga lmao!!!!!!!!!!1
You know you got under these kids skin when they attacked your site.
Lets see how tough they are when facing a 5 or 10 year prison term.
lizzard losers is their new nickname.
Oh gee look the net is still up and i was gaming online through their entire attack , laughing at them.
Please don’t advocate or make jokes about prison rape. Even the worst criminals don’t deserve such treatment, let alone “hackers”. If you support prison rape, you support all rape.
Hah, script kiddies getting their asses kicked.
I’m sure I’m going to sound like a moron so flame on with ease, but can’t we block IP’s from outside the US? Block IP’s of proxy servers? Shut them down at the source? Can’t ICANN and registrars reclaim domains being used for illegal purposes? Block IP’s of international ISP’s from countries we know to be a problem? If Netflix can keep me from using their service when I’m out of the country can’t we do the reverse?
Hi Brian,
Thanks for all the hard work,and congratulations!