Bloomberg reports that U.S. federal investigators probing the theft of 80 million Social Security records and other sensitive data from insurance giant Anthem Inc. are pointing the finger at state-sponsored hackers from China. Although unconfirmed, that suspicion would explain a confidential alert the FBI circulated last week warning that Chinese hackers were targeting personally identifiable information from U.S. commercial and government networks.
According to this story from Bloomberg’s Michael Riley and Jordan Robertson, “the attack appears to follow a pattern of thefts of medical data by foreigners seeking a pathway into the personal lives and computers of a select group — defense contractors, government workers and others, according to a U.S. government official familiar with a more than year-long investigation into the evidence of a broader campaign.”
While the story is light on details, it adds a bit more context to an FBI “flash alert” that KrebsOnSecurity obtained independently last week. The alert said the FBI has received information regarding a group of cyber actors who have compromised and stolen sensitive business information and Personally Identifiable Information (PII) from US commercial and government networks through cyber espionage.”
The alert notes that analysis of malware samples used in the attack indicate a significant amount of the computer network exploitation activities emanated from infrastructure located within China. The FBI said the tools used in the attack were referenced in open source reports on Deep Panda, a claim that also shows up in the Bloomberg piece. That story references data about Deep Panda from cybersecurity firm CrowdStrike, which specializes in attributing nation state-level attacks.
According to the FBI, Deep Panda has previously used Adobe Flash zero-day exploits in order to gain initial access to victim networks. While it may be unrelated, it’s worth noting that in the past two weeks alone, Adobe has shipped no fewer than three unscheduled, emergency updates to address Flash Player vulnerabilities that were being exploited in active attacks at the time Adobe released patches.
The FBI’s flash advisory continues:
“Information obtained from victims indicates that PII was a priority target. The FBI notes that stolen PII has been used in other instances to target or otherwise facilitate various malicious activities such as financial fraud though the FBI is not aware of such activity by this group. Any activity related to this group detected on a network should be considered an indication of a compromise requiring extensive mitigation and contact with law enforcement.”
In its own writeup on Deep Panda from mid-2014, CrowdStrike notes that “for almost three years now, CrowdStrike has monitored DEEP PANDA targeting critical and strategic business verticals including: government, defense, financial, legal, and the telecommunications industries. At the think tanks, [we have] detected targeting of senior individuals involved in geopolitical policy issues, in particular in the China/Asia Pacific region. DEEP PANDA presents a very serious threat not just to think tanks, but also multinational financial institutions, law firms, defense contractors, and government agencies.”
Leaving aside the question of whether state-sponsored Chinese hackers were in fact behind the Anthem breach, there are still many unanswered questions about this incident, such as when did Anthem find out about it? How long did the breach last? How did the attackers break in? What can other businesses learn from this incident to protect themselves?
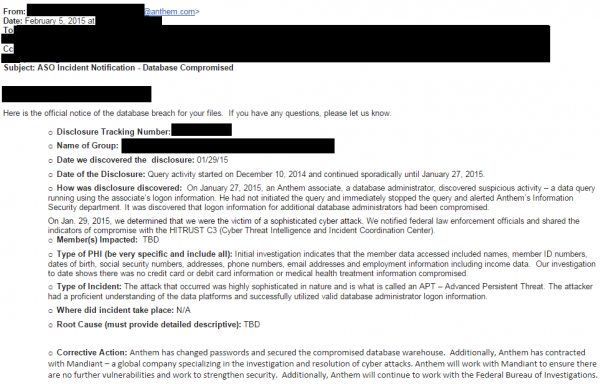
Steve Ragan, a journalist who writes the Salted Hash blog for CSO Online, references a document he received from a trusted source that was reportedly sent as a memo from Anthem to its clients. That memo notes that the unauthorized activity seems to date back to at least December 10, 2014. That activity apparently continued undetected until January 27, 2015, meaning the attackers had access to Anthem’s customer database for more than a month before they were discovered.
The memo explains:
“On January 27, 2015, an Anthem associate, a database administrator, discovered suspicious activity – a database query running using the associate’s logon information. He had not initiated the query and immediately stopped the query and alerted Anthem’s Information Security department. It was also discovered the logon information for additional database administrators had been compromised.”
The notice from Anthem to its clients concludes that “the attacker had proficient understanding of the data platforms and successfully utilized valid databaes administrator logon information.”
As for how the attackers broke in, perhaps the FBI’s Flash warning on Deep Panda (PDF) holds some clues.
Incidentally, infosec professionals take note: Anthem is hiring. On Feb. 4, the same day that Anthem disclosed a breach at its “database warehouse” may have affected as many as 80 million consumers, it also posted a help wanted ad for a “Cloud Encryption Security Professional.”






Well this could get very interesting. But of course there’s probably going to be tons of proof linking state sponsored Chinese and we’re going to see no reaction, meanwhile sanctions were thrown again DPRK that didn’t do anything.
““the attacker […] successfully utilized valid databaes administrator logon information.”
admin and password123 strikes again…
More likely sending passwords clear text strikes again.
..or even more likely, phishing email caught a few fishes, then went after the school internally. Fish in a barrel.
So how about getting the FBI to declare Flash as a Chinese-malware-vector and therefore illegal.
Ban it and require its immediate removal.
Cheer all around !!
Like anything else, as long as the majority program with and use the program, it will live on. Apparently with 3 updates in a very short period of time, if there is/was any type of fuzzing that they could have done to look at the glaring holes, it apparently was totally ignored – on the security side of the house.
And of course China will say they did no wrong. Either they are blind to the corruption that surrounds them, or they are shoring up for some sort of digital warfare with all this potential PII.
Let’s face it, they could simply steal this information and not do a thing with it. Its more of flexing its “skills” showing the world that its stupid easy to break into any corporation – or other entity.
After all of this – corporations STILL let people with highly elevated rights surf the network. No such thing as two accounts, one for internal admin work, and another with minimal rights to surf with and open emails. HTML email should not be allowed inbound to cut down on spoofed emails.
It boils down to simplicity or security. Companies need to pick their poison and then, be at the ready to confront what may come their way. Many are simply blinded by dollar signs. It’s about profit and gains – until something like this comes along. AGAIN.
This is NOT the first time this has happened to this company – and I am sure it will not be the last. The CSO should be branded and catapulted out the front door.
One of the commenters above blames the security side of the house and the CSO.
That commenter is wrong. The security people are waving their arms and telling anyone who will listen that the assets are not being protected, but the people who decide the priorities are not listening very closely. They’re playing on the risky side and they will only learn when breaches like this burn them. Some of them won’t learn the lesson until they’ve been burned two or three times.
We know how to protect against most of these incidents, but it’ll take someone with a security background sitting in the CEO, CFO, COO positions to make it happen. It will cost them lots of money and it will be a continuous effort. That’s the cost of doing business today.
Some commenter above seems to think that the one who is in control of security operations isn’t at fault. The person taking that job, sitting in that seat IS responsible for security that surrounds them. CSO failure is when they are willing to take a paycheck and sit quietly when events like this happen.
Getting “burned” 3-4 times? One might call that a stance of “acceptance”, but that many blunders in a row will have heads rolling and profits taken by the government in way of fines, and potential class action suits.
Obviously, we all don’t know how to protect against these incidents, because if we did, they wouldn’t be happening. Ignorance, does not replace due diligence, due care nor the prudent man rule. I can see this company sitting in front of congress and answering some serious questions about how security is being handled within.
Security does not have to cost an arm and a leg. There are a TON of third party tools out there that can be used, some even are free. Its the CSO that should instill some energy in finding ways to correct issues BEFORE they become incidents.
Security incidents happen and some are human nature. Minor infractions can be dealt with on a case by case basis. Breaches are another matter – they can affect millions of customers and who’s job is it to protect that data?
It’s blatant incompetence, laziness and accepting defeat instead of ingenuity and brain storming. Accept a paycheck and avoid conflict….yeah yeah, sure, sure that’s a winning way to run a business.
Free tools? Really? Authorized by a CSO of an enterprise such as Anthem? Or any enterprise for that matter? Unless you have some kind of first hand info, you may want to ease up on the finger pointing.
Data breaches are going to be a reality for any entity connected to the internet. For most it is only a matter of time. Yes there are a myriad of ways to protect yourself, but in the end, the cost is going to be the mitigating factor and no CSO in the world has the weight to overcome that.
Even if you do all the right things, defense systems can still be circumvented by something as simple as a user not paying attention. This issue spans more than just technology and budget, IMHO. This is a constant cat and mouse game and I think the root of it all is bottom up security awareness starting with vendors approaching their code with security consciousness.
I guess this means Anthem and Adobe will share financial liability for all costs incurred by everyone who has their identity compromised, right?
Liability? That’s what cyber insurance and free credit monitoring is for!
Ok, we have black hats in China….this is news.
The issue isn’t that we have hackers, the issue is that we have our information being put in places that are not secure. But we aren’t supposed to blame Anthem for any wrong doing. Just like we aren’t supposed to blame Sony for anything.
How does one get upset with a thief being a thief (it’s in the nature of a thief to be a thief)? We all know there are thieves in this world. That’s why locks were invented. You can’t put this stuff out there to be had and then complain because someone set out to have it.
Who exactly have you been hearing say we aren’t supposed to blame Sony for anything? Sony’s been getting slammed left and right (and rightfully so) for their cybersecurity practices.
80 million names, addresses, birthdates and social security numbers hacked; 80 million fake tax returns submitted.
You’d be better off if your credit card was stolen. Your birthdate and social security numbers last a lifetime and some agencies and companies just retire those two pieces of information to authenticate you.
Well, that is not comforting to the 80 million victims. Collateral damage can ruin people’s lives.
This is why the IRS needs to initiate the IP PIN number for all tax filers!
As a victim of tax fraud in 2013 and now again in 2014, I can attest that this is a time consuming process. It seems that the IP PIN would eliminate much of the tax fraud.
That’s why I put a freeze on my credit with all three bureaus as soon as I heard about this breach. Better safe than sorry at this point–there’s just no use pretending that our private data is private any longer.
I’m also upset that because I’m not (yet) a victim, I’m not allowed to receive an Identity Protection PIN (IP PIN) from the IRS to prevent crooks from filing fraudulent tax returns in my name. Enhanced security like this should be made available to every citizen who is concerned about their financial security and stopping tax fraud against the American people. I’d love to see Mr. Krebs do an article about this.
http://www.irs.gov/Individuals/The-Identity-Protection-PIN-IP-PIN
You gotta love being required to buy Obomacare insurance or paying a penalty, giving all your personal information on their applications and then finding out that the actual database storing the personal information is not even encrypted. I can’t believe they don’t even take encryption precautions. Once your personal information is stolen you can never get it back. The only plus side here is that at least the information stolen includes each and every employee all the way to the top so at least they will feel the penalty as much as their customers!
Encryption of data stored in secured data centers is worthless. In order to get thru the encryption, one only needs to compromise an account with access thru the encryption… and think about it, who needs to see the data, the nurse, the doctor, the claims analysts. Then, who administers/maintains those systems?… They have access to the keys.
Dave, its not useless to encrypt data when done properly.
http://en.wikipedia.org/wiki/Hardware_security_module
When using an HSM having access to the database is not enough to decrypt the data and no one has access to the keys.
You also need access to the highly secured HSM to decrypt the data. The HSM should also be setup to stop working should unusual activity be detected such as bulk decryption requests thus limiting how much data a hacker could obtain.
Let’s keep useless (and divisive) political opinions out of this. Please!
+1
Yesterday somehow I saw Fox say Obamacare was hacked and 80 million records stolen, sheesh, give us break, all insurance companies would have the same risk.
Anthem is not a governmental agency. You can bet that Anthem has been advised by a long string of consultants over the years to safeguard/isolate its databases.
This is very interesting. I’m like a broken record on the data selling epidemic in the US and have been for a couple years now having been a victim of flawed data. It was about 3 weeks ago I received a call about wanting to know if I was interested in a clinical trial. It was an offshore call as the accent was Asian and the caller had my name and said they had on record that I take blood thinners. Being a data person and delving into this topic all the time about licensing data sellers, my ears lit up.
Where did this call come from as there was no number listed and when I asked for the company name they immediately hung up the phone, but they had my name and said information that I take blood thinners. This could have very well been a pharma company using an off shore calling center too but now with the Anthem breach it just made me think a little bit about data if you will.
As I have read the hackers were specific on what they took, in other words the information that could produce money by selling it. We do have a data selling epidemic in the US and without some kind of licensing, data stolen like this can be repackaged and sold to companies who don’t know they are buying hacked data too. All of this gets out there about us consumers too.
So there’s another danger here as data just like counterfeit drugs get in the mainstream system except this could even be easier if you will. It’s definitely something to think about though, as I have been crusading for licensing/indexing data sellers for consumers to use to find who sold their data when repackaging takes place and you’ve been sold a few times and the data is flawed. This shines yet one more reason to index data sellers as who knows what the hackers will do here and what attempts will be made to sell this data and where.
We have a high level of sophisticated hackers out there and this is really a big deal here with Anthem. In view of the above, and again it’s just me speculating but I am wondering how much of this has already gone on.
The data selling business is worth $180 billion a year in the US and so it seems hackers want some of this money too. I would imagine with getting social security numbers the IRS might be put on alert to look for fraudulent tax returns as 40% of them go through. The IRS has a hole to where the name and social security number on a return filed are not matched to verify! That is enough to make your hair stand on end as it’s something even a person not in technology would assume should occur too. Who knows, they could sit on the data until they decide they want to strike at any given time to make money. Here’s where 60 minutes did a story on a hospital selling data and it was all inside jobs, 3 times in 2 years and what they did was not rocket science either. Anyway, the IRS is one place the affected Anthem policy holders will maybe need to watch.
http://ducknetweb.blogspot.com/2014/09/one-more-reason-to-license-data.html
I wrote up my blood thinner story and there’s other links that tell about what insurers buy, i.e. all your credit card transactions. It was in fact Blue Cross that said they buy our credit card transactions to see what size clothes their insured are buying and you can’t make that up. We know of course if insurers are buying our credit card transaction they are looking for more than that, as common sense would say. I’m stuck and can’t find where the blood thinner data originated about me either.
As I started talking about 2 years ago, I said there was a data selling epidemic and it’s obviously not just here in the US anymore as hackers want to cash in too and that’s scary. Here’s my campaign and I badger the FTC and a few members of Congress almost weekly as we need a law to index and license the sellers so transactions can carry that license with it and those buying data won’t end up buying hacked stolen data as well. Sounds like this hack was all about wanting to make some money like banks and US corporations do with selling and scoring us.
http://www.youcaring.com/other/help-preserve-our-privacy-/258776
It’s no longer about putting data up on the Pirate’s bay anymore, it’s about money.
Duck, duck, goose!
As I started reading your post about two years ago, I realized this post was going to be, about something that would include hackers too. Then I read the article, and saw a tiny flashing light. I realized it was my spaceship calling me home.
It was then I saw the meaning of life in bright neon letters. Could it be? NO! It wasn’t, but it was a ninja. He told me if I could eat 9,000,000 bowls of colon blow and survive I would be the strongest root in the garden in that once we had grown. I have no surprise but to tell you, the world is dark and gloomy, but rather the strawberry craft that is making your dreams a reality.
Lets join hands and sing the songs of joy, written and performed by Randy Newman. Oh, and hackers and junk.
Unlike many large attacks I am not seeing anyone trying to sell the data exposed by Anthem. That leads me to believe they are sifting through the data looking for specific individuals.
Someone needs to tell these CEO’s they need to be careful what personal information they make available online BIOs. Anthem CEO Joseph R Swedish boasts being an advisor to “China Health Care Corp.” specializing in finding maternity care for VIP’s in China.
BillP
BillP Studios
Funny how they will quickly turn over all this info in this case, but in the SONY hack they can’t tell us anything.
>Recipients may share this information with peers and partner organizations within their sector or community, but not via publicly accessible channels.
Someone leaked again…does the PDF contain an individually-identifiable Easter Egg to identify the leaker?
> That memo notes that the unauthorized activity seems to date back to at least December 10, 2014. That activity apparently continued undetected until January 27, 2015, meaning the attackers had access to Anthem’s customer database for more than a month before they were discovered.
anthemfacts.com – Creation Date: 2014-12-13T16:04:36Z
The fact-finding domain seems to imply that Anthem knew about it 3 days after the breach.
Wow, great find on the domain registration date.
I tweeted about the domain registration date early yesterday afternoon.
http://twitter.com/briankrebs/status/563421238610370560
Then I realized that the date coincided with the name change from Wellpoint to Anthem. Also, it previously hosted information about that.
http://twitter.com/briankrebs/status/563422693991927809
Looks like they didn’t learn their lesson the first time around.
http://www.hhs.gov/ocr/privacy/hipaa/enforcement/examples/wellpoint-agreement.html
>Recipients may share this information with peers and partner organizations within their sector or community, BUT NOT VIA PUBLICLY ACCESSIBLE CHANNELS.
That’s standard. Very standard. I see notes like that all the time for information that’s far, *FAR* less sensitive. It’s normally just a boilerplate for people to not go off speculating or drawing conclusions from whatever their point of view is without factoring in what the entire organization knows and has decided as a whole.
Yes, the mindset behind the warning can lead to abuse or silencing important voices. Yes, it’s abusable. But it’s mere presence isn’t indicative of anything beyond the mundane.
Obviously this hack was perpetrated by a formal Sony employee. I wish they’d catch her already.
“Atlanta-based cybersecurity firm CrowdStrike”
Atlanta? Their website and Google Maps say Irvine, California. Atlanta’s our turf!
But still the United States goverment continues to allow mainland China to wreck are ecomony and then steal are trade secrets month after month without any penality
Although this hack really worries me since the hackers were able to snatch quite a bit of information, but I cannot stop laughing at Anthem’s CEO statement on “anthemfacts dot com”…… It is just dumb to start relaying the situation in such manner:
“Safeguarding your personal, financial and medical information is one of our top priorities, and because of that, we have state-of-the-art information security systems to protect your data.”
BUT…..We were hacked!!!!
This is shaping up similar to the infiltration of the 1950’s by the USSR; although, they obviously didn’t have the Internet. The Internet has allowed for the mass collection of information whereas in the past individual companies were targeted to compromise people who had access to information. Now, we have computer files and can do the targeting back home outside the country.
Why all the hate to China, Sony, and N.RK. come now. Hate blinds the eye and freezes the brain to a pattern. It focuses you on feeling rather then rational response. The rational response is for the board of directors to fire those responsible for the disaster. Including themselves. The mighty bit their poisoned apple of profits over all, and too hell with their fiduciary duty to run the company in a responsible manner. Remember a company needs managers that can hire the right people to sell, and protect the company, since our government only wants to spy on its citizens. Those working should have been the best and brightest available, not the friends of the boss, or friends of some government agency, or Buffy down the street with the big …..
At this point we don’t know enough details to say exactly what was going wrong there, but I haven’t seen any indication that nepotism had anything to do with it.
It is always tempting to just say we should fire those who are responsible, but that ends up making people so risk-adverse that it can make it impossible for any work to get done at all.
Or perhaps you are trying to hire someone who you might think to be the “best and brightest”, and you tell them that you have this set of applications with crummy security that they need to help develop, but if anything goes wrong they all get the axe. Who is going to take a job with that hanging over their head? Certainly anyone bright enough to do the job will realize that they are in an untenable position and won’t accept the job if offered.
@OtherEric
“It is always tempting to just say we should fire those who are responsible, but that ends up making people so risk-adverse that it can make it impossible for any work to get done at all.”
I’m not saying we should fire anyone, especially since the same type of person would be hired in their place. But maybe being risk-adverse shouldn’t have anything to do with “getting the job done.”
If your job is to be risk-adverse, then how do you get that job done if you’re always told that “making the most money” is more important?
It’s a double-edged sword, and businesses routinely stab themselves with only one end. Please someone show me a case where a company wasn’t successful because they were too secure! Ha!
The only way that security is going to get better is if it somehow ties directly to profits. If Anthem made more revenue by being more secure, then only the most sophisticated attacks would work – instead of whatever DBA probably clicked on the wrong email.
What really annoys me is the refusal of most companies to use 2FA for their logins to their internal applications. They seem to have the idea that the internal network is always safe from bad guys.
My own company “scanned” all of our computers looking for MalwareBytes – and had people remove it if they had it installed. Entirely because of licensing – the free version is only allowed for home/personal use, and that much is a valid concern. My argument would have been that they should have simply purchased a corporate license, and they were sort of headed in that direction until some doofus in IT nixed it because he said that “we can block the malware at the firewall”. Which of course ignores flash drives or someone using their laptop in a hotel/airport. So the money got redirected to some new toys for this guy (to try and block malware at the firewall), and the rest of us feel like we are flying blind.
Here’s an additional thought, 80 million social security numbers, the Athem hackers have a gold mine as I said above due to the issues at the IRS with 40% of fake returns paying off, this could go on for years, so those affected by the Anthem data hack, check your IRS return this, next year, the following year an so on. They could sit on this and make money for years. This is just one obvious exploit.
Folks the data selling and mining business in the US alone is now worth around $180 billion dollars a year, so you think hackers want some of that money if the getting is good, of course they do. I read a comment above that someone said they were not aware of any Anthem data being used, well again wake up as they have to have time to reformat, repackage it and so on and selling the data could go on for years. I don’t know where people’s common sense is at today.
Good video, clip #2 is Dr. Halamka at Harvard Medical talking about the value of stolen data. The other clips are great too as well as the entire interview at the post, but #2 toward the middle gets right down to what the data is worth and how medical data is shared. It’s one of the best explanations I have seen by all means.
http://ducknetweb.blogspot.com/2014/10/cxotalk-dr-halamka-cio-of-beth-israel.html
By the way, as related reading, data selling and scoring in the US is directly related to keeping our rate of inequality growing as well as well all get scored into a corner with data and we can’t get out and add flawed data in there and you are judged on stuff that doesn’t even apply to you, so guilty by the data before you can even speak and I have real life experience with that.
http://ducknetweb.blogspot.com/2014/06/data-selling-and-direct-correlation-to.html
One more link that kind of shows how bad the data selling is and how it destroys our dignity is a story about a hospital buying up data broker and credit card transactions to review and of course both of which have nothing to do with getting medical care you need. So again it’s back to the data selling epidemic in the US and furthermore look at all the big banks with labs in the Silicon Valley, why are they there? They want code and apps to be able to mine even more of our data…it’s insane, so again crooks want in on this money too sadly.
http://ducknetweb.blogspot.com/2014/06/oh-crap-now-hospitals-are-now-buying.html
To Peter: You are a candidate to work in the Intel arena . Of course you’ll have to bite your lip more than 100 times day, but ? or you could start you’re own side show ,down low and be ready for the next manly administration in dc to rock and seal these thug/rogue nations off…
US Corporates are losing PII to the hackers by the tens of millions. Target 60 million, Home Depot 50 million, Anthem 80 million. The Million count has not much significance any more.
And with the Russian and Chinese (and yes for sure the North Koreans if you want to believe they have the capacity) plundering PII for months from databases of these companies before they are found, you’d think that in their daily corporate meetings these and other companies are toiling over how to protect themselves. No Such thing !!
Major focus of daily corporate conference calls still is: Are we on target for meeting the cost reduction quota for this month ?
And how is this cost reduction being pursued? By out sourcing more and more work to their ‘partners’. And what is outsourcing in real terms?
Laying off their employees and giving more work to their IT subcontractor, with HO in India or the Philippines, who can bring in bodies to do the same work for half or lesser the cost. No background checks no benefits. No nothing to worry about. And a position can be filled overnight. These ‘partners’, with their revolving doors will hire anyone who walks in their door.
This ‘outsourcing’ on the cheap is also a can’t-get-any-easier way for the hacking mafia to position their cells inside these major companies via their $10/hour IT ‘partners’. And systems and database password are being given to these $10/hour ‘partners’ left and right.
I can only guess how many of these ‘partners’ are inside Target, Home Depot, Sony and Anthem, and other companies, walking in everyday with a fresh update of rootkits on USB drives in their pockets.
Will these corporations get off their cost reduction frenzy and pay attention to safeguarding the PII of their customers?
Not a chance. Definitely not until the Feds get out of bed with these companies and crucify the entire management team of one of them in court to set up an example. Sarbox, HIPAA, GLBA. The laws are all there but meaningless trash on paper until they are implemented and an example is demonstrated.
What are the chances that this will happen ?
Be careful all, spam already being sent out with fake credit monitoring links.
This is going to be a huge factor in all of this data being stolen. Even if the attackers don’t exploit the information they have obtained you should be on the lookout for copycat style attacks. Phishing emails from “Anthem” are going to run rampant for a long time until this eventually becomes history. Keep an eye out for the spam highlighting Anthem credit monitoring, life monitoring, and other services that do not explicitly come from verified Anthem emails. Snail mail is going to be a good defense on Anthem’s part to keep some of these incidents down. It is too easy to create similar email addresses related to their company and subsidiaries along with crafty landing pages. Plus there are plenty of users still affected by the Flash exploit that was recently discovered. Taking control of an astronomical amount of machines that belong to scared and paranoid Anthem customers is possible.
My take on what the work day today is like at Anthem: https://www.youtube.com/watch?v=z5rRZdiu1UE
And On Feb. 4, the same day that Anthem disclosed a breach it also posted a help wanted ad for a “Cloud Encryption Security Professional.” I’m going to send my resume in under the name Lloyd Christmas – I’ll be hired by Monday.
Seriously everyone lock your credit at the three credit agencies and get a pin number from the IRS so nobody can file taxes on your behalf.
“… the attack appears to follow a pattern of thefts of medical data by foreigners seeking a pathway into the personal lives and computers of a select group — defense contractors, government workers and others, according to a U.S. government official familiar with a more than year-long investigation into the evidence of a broader campaign.”
Wow. The implications of that are ominous. Not “ominous” in some imminent, urgent manner, but rather in a sense of having a new feeling for the long term goals of the ones in government supporting and directing these hacking groups. They are **really** gathering a large database to mine for their spying activities.
Could this be partly an inside job via one of their countless (Chinese national) programmers or statisitcal analysts, a fari number of which will listen to the word of “The Party” ?
“… the attack appears to follow a pattern of thefts of medical data by foreigners seeking a pathway into the personal lives and computers of a select group — defense contractors, government workers and others, according to a U.S. government official familiar with a more than year-long investigation into the evidence of a broader campaign.”
Smells like team propoganda.
Follow the money…
Brian, another great (and timely) story — this is the first I’ve heard of the ‘Deep Panda’ group, and while this is the only story on your site involving them which appears from clicking on that tag at the end of the current article, a quick DDG search identifies that they’ve been around for awhile.
So, two questions – 1) are they possibly connected to the previously exposed and now-infamous Unit 61398 insofar as anyone has been able to discern, and 2) are they completely unrelated to the supposedly legitimate Panda Security antimalware vendor?
Completely unrelated to Panda Security. The “Panda” name was chosen because China is known for pandas.
CrowdStrike’s chosen name for Unit 61398 is similar: Putter Panda.
Thanks – I know all about the pandas from having worked extensively in China over the past 2+ decades, and thought there was a pretty good chance they were unrelated to Panda Security. I figured Brian would have pointed it out if it was the case, but since he didn’t it was worth the query to confirm. Whether there’s a formal or informal association (even one which is just competitive) with Unit 61398 still remains an open matter, though.
I forgot I had this agreement with LifeLock and thought it was a good post for those who want to do something right now and not wait until Anthem makes an announcement. So far all I have seen is the standard information on calling credit agencies and so on and yes there’s a cost here but it’s not too bad and from what I read here it might save some of the chasing around.
http://ducknetweb.blogspot.com/2015/02/anthem-security-breachtake-look-at.html
Anyway it’s there if anyone is interested in taking a look and I’m not here to hard push it by any means but it does work good enough.
If this came through twice, delete the second one. This is information about LifeLock and maybe some folks might want to read about it. It does work and this is not a big push at all here.
http://ducknetweb.blogspot.com/2015/02/anthem-security-breachtake-look-at.html
It does work and so far we don’t know what Anthem will be offering yet in detail other than what we have seen in press releases that tell you to call the credit agencies, etc. so this might save some chasing. I know it’s not fair that we have to pay for such either, but for good or bad here it is.
We need to finally stop using the Social Security Number as a (virtually) unchangeable system of both identification and authentication.
As bad as the credit card breaches are – at least I can have that number changed. I can’t get the SSN changed and the SSN on its own has no authentication component.
The whole system needs to be reworked to include some form of two-factor authentication, at least on an voluntary (for the individual, not the government/company/etc.) basis.