A recent phishing campaign targeting customers of several major U.S. banks was powered by text messages directing recipients to call hacked phone lines at Holiday Inn locations in the south. Such attacks are not new, but this one is a timely reminder that phishers increasingly are using lures blasted out via SMS as more banks turn to text messaging to communicate with customers about account activity.
 The above-mentioned phishing attacks were actually a mix of scams known as “SMiShing” — phishing lures sent via SMS text message — and voice phishing or “vishing,” where consumers are directed to call a number that answers with a voice prompt spoofing the bank and instructing the caller to enter his credit card number and expiration date.
The above-mentioned phishing attacks were actually a mix of scams known as “SMiShing” — phishing lures sent via SMS text message — and voice phishing or “vishing,” where consumers are directed to call a number that answers with a voice prompt spoofing the bank and instructing the caller to enter his credit card number and expiration date.
Over the past two weeks, fraudsters have been blasting out SMS messages to hundreds of thousands of mobile users in the Houston, Texas area. The messages alerted recipients about supposed problems with their bank account, urging them to call a supplied number and follow the automated voice prompts to validate or verify their credit card account information.
On Saturday, Jan. 30, I called one of the numbers that was sent out in the smishing/vishing scam — 281-866-0500 – which is the main phone line for a Holiday Inn Express in Houston. At the time, calls to the number went straight to an automated voice prompt targeting Bank of America customers:
“Thank you for calling Bank of America. A text message has been sent to inform you that your debit card has been limited due to a security issue. To reactivate, please press one now.” After pressing one, the caller is prompted to enter the last four digits of their Social Security number, and then the full card number and expiration date.
My recording of the call was garbled, but here’s a copy of a very similar voice prompt targeting Key Bank customers earlier in January that also was run off the fax line tied to a different Holiday Inn a few miles away in Houston [number: 832-237-8999], according to Numbercop, a telephony threat intelligence firm.
Holiday Inn’s corporate office did not return calls seeking comment, but the company apparently got the message because the phone lines were answering normally on Monday. A front desk clerk who answered the line on Tuesday said the hotel received over 100 complaints from people who got text messages prompting them to call the hotel’s main number during the time it was hacked.
According to Jan Volzke, Numbercop’s chief executive, these scams typically start on a Saturday afternoon and run through the weekend when targeted banks are typically closed.
“Two separate Holiday Inns getting hijacked in such short time suggests there is a larger issue at work with their telephone system provider,” he said. “That phone line is probably sitting right next to the credit card machine of the Holiday Inn. In a way this is just another retail terminal, and if they can’t secure their phone lines, maybe you shouldn’t be giving them your credit card.”
Volzke said the recipients of the phony texts in Houston were geo-targeted by area code.
“The texts were sent in bursts with varying bank affiliations, including Bank of America, Fifth Third Bank, and Susquehanna Bank,” he said. “The campaign last week was an identical case to one a week or so earlier that referenced Key Bank, Bank of America and Wells Fargo.”
Numbercop says the text message lures were sent using email-to-SMS gateways, but that the company also has seen similar campaigns sent from regular in-network numbers (prepaid mobile phones e.g.), which can be harder to catch. In addition, Volzke said, phishers often will target AT&T and Verizon users for use in furthering these schemes.
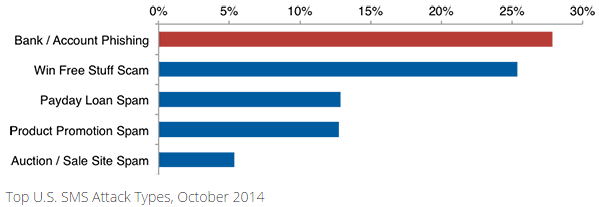
Many banks now offer their customers the ability to receive text message alerts about activity on their credit card accounts — such as recent transactions — so it’s not surprising that crooks are exploiting this medium. While vishing and SMiShing attacks are not new (see this story from 2010), they are on the rise: According to Cloudmark, the incidence of SMS bank account phishing in the U.S. more than tripled in September 2014. Cloudmark’s recently released Annual Threat Report found more than one in four unsolicited SMS messages reported in 2014 attempted to steal the victim’s personal or financial information.
Volzke says it’s unfortunate that more financial institutions aren’t communicating with their customers via mobile banking apps.
“Banking apps are among the most frequently downloaded and used apps,” Volzke said. “If the user has an app from the bank installed, then if the bank really has something to say they should use the in-app messaging method, not text messages which can be spoofed and are not secure. And yet we see almost no bank making use of this.”
Regardless of whether you communicate with your bank via text message, avoid calling phone numbers or clicking links that appear to have been sent via text message from your bank. Also, be extremely wary of any incoming calls from someone calling from your bank. If you think there may be an issue with your account, your best bet is to simply call the number on the back of your credit or debit card.




I would be interested in hearing about the actual phone system, at the holiday inn. A system that was so easily compromised would lead me to believe that the vendor whose system they used is insecure. Could you find out more information?
This is it! Finally another incident of phone system hacking exposed.
I have had multiple customers in my shop telling me they were directed to hackers when they’ve called what they thought were phone numbers for HP, MS, Dell and Norton. Each one said they got the phone numbers from proper sources (web site, application, etc). One even brought me the paper document they received from Dell informing them their Norton subscription had expired. When they called the number, hackers wanted to remote into their PC.
I’ve seen this type of “hack” for about 2 years now and, with this story, am now convinced that phone systems have been hacked to redirect calls.
Anyone major phone geeks here? This needs some research into VOIP hacks.
Doubtful. More likely what you’ve seen is a few cases of a rogue (or incompetent) agent in an otherwise legitimate call-in service center. It ‘s more frequent of late, because many of the big-name PC and AV vendors are farming out their service centers to third-party contractors as a cost-saving measure.
My state agency sees constant hack attempts on our 800 lines and video conferencing systems from around the world. Current hotspot for scans specifically at our video conferencing phone systems are coming from ISPs in France.
We’ve had at least two incidents of successful hacks of our 800 lines, raising flags at our national phone provider when they saw calls originating from Cuba outbound to the Middle East and Cyprus from our lines. These incidents weren’t just ‘forgot to change default password’ hacks but were slightly more sophisticated. It caused our teams to really up the configuration of the security mechanisms that come with the systems. The national provider was quite helpful in offering assistance in both cases.
I agree and disagree with EstherD
I’ve had reports of calls placed to legit HP customer service being answered by HP customer service… and followed 5-10 min after terminating the call by tech support scammers looking to follow up on the printer issue with an “OMG your computer is infected!!!” tech support scam.
My take on this event was that the outsourced tech support was either hacked, or worse was in on the game. I could easily see this being a side-line of seemingly legit overseas IT services companies… very hard to prove, and a steady supply of potential targets calling the legit side of the business.
I’ve also heard of calls to various tech support lines (even ISPs) that resulted in the customer being transferred to tech support scammers… hard telling if the “scammers” in this case were actually scammers or just ineffective and overpriced tech support, but the effect is roughly the same. At least one or two of these stories seem to have actually been scammers, which would support the rogue employee theory. I could easily imagine a recruiting campaign aimed at call center employees to pad their income with commissions from the scammers for forwarding callers.
It may not be that they were hacked, it could just be they were using the default passwords. I can imagine a user saying “who cares about that password, it’s just the phones” not realizing it could be used in this way. Most people just don’t have security on their minds like readers of this website do.
Hey, where is that Mitnick guy when you need a comment on phone system stuff?
I agree, with Michael. How easy was to hack their phone systems?
I considered calling the Holiday Inn number and saying: “This is the Bank of America calling. Do you have any messages for me?” Nah, too lame.
How did the SMSers know which bank the cell phone holder used, or did they just send a bunch figuring they’d get somebody who used these large chains?
Did they ever send more than one bank request to the same cell # (which would be a tip off I would think to the cell user)?
And that comment by Volzke saying Banks should use the in-app messaging abilities of their Bank Apps is an EXCELLENT suggestion and analysis of how to thwart this!
Unfortunately, not all financial institutions have banking apps for all platforms.
I have accounts at two large, assets in the billions, credit unions. One has an app for Apple and Android, but not Amazon or Windows. The other has an app for Apple, Android, and Amazon, but not Windows.
No idea what that Jan guy is on about saying the fax machine is next to the credit card machine. The credit card machine will have a secure link to the processor, you can’t just hijack a PSTN line and expect it to work. The fax service will almost certainly be a fax to e-mail gateway commissioned centrally by Holiday Inn.
His comment implies some sort of physical hack at the hotel when it’s more likely someone had access to HI’s account with their telephony provider (Level 3?) and could redirect the number to a rogue IVR (not actually hard to set up these days!).
It sounds like he phone line is almost certainly VOIP (not PSTN). If you have the password, it could be easy to change the programming / configuration remotely from anywhere on the internet.
Thanks for the heads up about this issue, very interesting topic
If you ever watch the IPViking real time attack map, that KOS has featured before, you will see at times large swaths of attacks aimed at SIP. I am curious if the compromised lines were somehow related to the large SIP attacks?
This has got to be one of the best web sites on the internet. I have been coming here several times a day and I am never disappointed. Thanks you Mr. Krebs.
To Itsmeitsmeitsddp:
Your comment is hard for me to understand. What does IPViking mean? What is KOS and what is SIP?
Thank you
@Mark Allyn
KOS – Krebs on security, this website you are viewing
IPViking is another website that among other things has a map showing internet based attacks around the globe
SIP – Communications protocol used for voice over ip (VOIP) phones
Some companies allow phone lines to be manually forwarded to another office when they are closed or running reduced staff (as on a weekend). Holiday Inn’s problem could have been as simple as someone changing the forwarding to a number that the hacker controls.
Where do the recordings end up?
Did Holiday Inn really fix the problem, or did the hackers back away on their own? If Holiday Inn was able to fix the issue, it should be easier to track down the cause. If the hackers backed out on their own, they might have covered their tracks.
Crap. I am one of many Houston local IT guys for the IHG here in Houston (Holiday Inn is one of the flags). While we do not service the phone systems, I’m sure us IT boys will be involved in some way.
A co-worker of mine received an automated call (Not SMS) that was targeted toward Santander banking customers. It requested him to enter his social security number. He hung-up and told me about it. We called a branch manager who looked up the source number. He confirmed the source number was an official Santander bank number. Spoofing is nothing new. So its important to remember that even if a number is trusted, you should never give personal information to an unexpected caller.
Seems as if I have to reccomend the old podcast of the 2600 again, and the history of phone spoofing. And like your SSN, the first couple of numbers off any phone card, any debit card, any credit card, tell you who its assigned too, like in MasterCard, or visa, the second sequence says what bank its affiliates with, such as boa, or vanguard or system used with such as tell guard, shucks, all so offers knew which ones to look for, and the clerks handling them were taught to honor the company card unquestionably.
Here is an interesting thought. Telecommunication, and computers. All good communications companies ( at, Verizon, sprint, etc….) Use computers to tie into and control the internet and voice communications. It is one and the same. Could there be another weak exploitable link no one is looking at.
I still don’t understand why spoofing is technically permitted on phone systems. Isn’t there some way to secure our telecomm infrastructure from such easy hacks?
Classic example is Dr. Jones is on call on Saturday night and wants to contact you back to discuss the incision from your Wednesday surgery that looks red and inflamed. You don’t need his personal phone number, but the main office number with the answering service will work just fine.
There are plenty of other situations like this. In my 911 center all outbound calls show the main non-emergency line. I wouldn’t want someone to call back a specific spot in the room when that person is up on break later.
Yes there is, but for some reason the FCC does not require it.,
The Caller ID system we have now allows business customers to supply the Caller ID info. As we see, it can be anything. I get some calls with numbers that aren’t in service, I get some from directory service (xxx-555-1212) and even some from 000-000-0000. As good start would be for the FCC to require phone companies (i.e. Verizon, AT&T etc) to verify that the number being provided was assigned to the trunk being used. If it didn’t match then put the trunk number in there instead. This would point out the boilerrooms fairly quickly and they could be shut down. It would also locate the point-of-entry for the foreign VOIP calls we keep getting, as those have to entry the phone system somewhere, through some business trunk. Just make it so that if the number supplied doesn’t match the range of the trunk, then we get the trunk number.
There is also a completely separate number-identification system used for 800-calling. That HAS to correct because the recipient pays for the calls and is legally entitled to know the exact numbers that called. It would be good to be able to get this number as well as/instead of the rubbish we get now.
Chase sends communications to its customers within its mobile IOS app. It annoyed me that they would not use text messaging that is more convenient for me than opening an app and signing in. Seems I need to reconsider.
At this point I assume when I dial the official published number for any establishment where I provide sensitive financial or personal information, that I am talking with employees or official contractors of that business. If that certainty is blown away even for a day, then what ?
Binfer messaging app is secure and encrypted. There is no charge to it. Check it out: http://www.binfer.com
It’s like my Grand-daddy used to say, “If it ain’t one thing, it’s another. Yep. Yep. Yep.”
WOW this hit close to home. I live in Houston, TX and just to image that that this type of scam went on in my city on top of all the current data breaches in the news. Really hit close to home! Krebs I wonder where Texas as a state and Houston, TX as a city rank in regards to cyber attacks, data breaches, identity theft and malware and phishing scams?
In reference to IPViking being mentioned, I went to that web site and was wondering why St. Louis is getting hit so much? Any ideas why they are a major target?
Several major financial services firms have their headquarters in St. Louis including Wells Fargo Advisors, Edward Jones, and Scottrade so they may be the targets.
In addition to what Dave said there are also a couple of large data centers there too which coincidentally is where IPViking hosts some of their honeypot servers I believe.
Recommending that people use banking apps is like telling surfers to tie meat on a long rope to their leg to avoid sharks.
Is this a peripheral event in the midst of the largest cyberheist in history? See Daily Telegraph, London, 2/15/2015 article: Hackers steal £650 million in world’s biggest bank raid http://www.telegraph.co.uk/news/uknews/crime/11414191/Hackers-steal-650-million-in-worlds-biggest-bank-raid.html