For the third time in a week, researchers have discovered a zero-day vulnerability in Adobe’s Flash Player browser plugin. Like the previous two discoveries, this one came to light only after hackers dumped online huge troves of documents stolen from Hacking Team — an Italian security firm that sells software exploits to governments around the world.
News of the latest Flash flaw comes from Trend Micro, which said it reported the bug (CVE-2015-5123) to Adobe’s Security Team. Adobe confirmed that it is working on a patch for the two outstanding zero-day vulnerabilities exposed in the Hacking Team breach.
We are likely to continue to see additional Flash zero day bugs surface as a result of this breach. Instead of waiting for Adobe to fix yet another flaw in Flash, please consider removing or at least hobbling this program.
Google Chrome comes with its own version of Flash pre-installed, but disabling it is easy enough. On a Windows, Mac, Linux or Chrome OS installation of Chrome, type “chrome:plugins” into the address bar, and on the Plug-ins page look for the “Flash” listing: To disable Flash, click the disable link (to re-enable it, click “enable”).
Windows users can remove Flash from non-Chrome browsers from the Add/Remove Programs panel, and/or using this Flash Removal Tool. Note that you must exit out of all Web browsers before running the tool. To verify that Flash has been removed, visit this page; if it says your browser needs Flash, you’ve successfully removed it.
For Mac users, AppleInsider carries a story today that has solid instructions for nixing the program from OS X once and for all.
“Flash has become such an information security nightmare that Facebook’s Chief Security Officer called on Adobe to sunset the platform as soon as possible and ask browser vendors to forcibly kill it off,” AppleInsider’s Shane Cole writes. “Though most exploits are targeted at Windows, Mac users are not invincible.”
I removed Flash entirely more than a month ago and haven’t missed the program one bit. Unfortunately, some sites — including many government Web sites — may prompt users to install Flash in order to view certain content. Perhaps it’s time for a petition to remove Flash Player from U.S. Government Web sites altogether? If you agree, make your voice heard here. For more on spreading the word about Flash, see the campaign at OccupyFlash.org.
If you decide that removing Flash altogether or disabling it until needed is impractical, there are in-between solutions. Script-blocking applications like Noscript and ScriptSafe are useful in blocking Flash content, but script blockers can be challenging for many users to handle.
Another approach is click-to-play, which is a feature available for most browsers (except IE, sadly) that blocks Flash content from loading by default, replacing the content on Web sites with a blank box. With click-to-play, users who wish to view the blocked content need only click the boxes to enable Flash content inside of them (click-to-play also blocks Java applets from loading by default).
Windows users who decide to keep Flash installed and/or enabled also should take full advantage of the Enhanced Mitigation Experience Toolkit (EMET), a free tool from Microsoft that can help Windows users beef up the security of third-party applications.




Am I the only one amused by the fact the “occupyflash.com” website, setup to denounce flash on all systems… uses flash?
That’s because it has a section that tells you if you have it installed already.
Flash insecure!? No way. Kill it off once and for all. Take java too while at it.
Hacking Team claims they’re the good guys but they were holding undisclosed 0-days that are now being weaponized and actively being used against every day citizens and organizations …
Really, the good guys? They sell exploit information and programs to governments… Now I agree that Governments need to monitor/police for bad people, but that’s a fine line… Hacking Team cannot legitimately claim they’re one of the good guys… they’re gray at best…
Krebs,
Does this refer to Flash version 18.0.0.203 from last week as still including this newly discovered flaw?
Thanks
Yes, this affects version 18.0.0.203.
Users should also install Anti-Exploit from Malwarebytes which blocked all 3 of the Flash exploits even before they were known to be zero days. Can’t say enough good about that product, highly recommend it.
I discovered to my horror that AARP.org makes extensive use of Flash, even to the point of using flash on its login page. If Flash is disabled you can’t log it. Under the assumption that AARP members may be less security savvy than some, this is simply unacceptable.
I sent a comment to the webmaster, and got a “bedbug letter” in response, telling me how concerned they are about security.
another reason not to join aarp…they use flash
Flash silently installed McAfee antivirus on millions computers. How it can be insecure?
[sarcasm\] +1
“Flash silently installed McAfee antivirus”
No, the Flash download asks if you want to install something called Security Scan Plus, which is just a McAfee marketing tool. You don’t have to accept it, but many people will get the program by clicking through the download process without paying attention to what’s being offered. It’s Adobe’s fault for making this an opt-out decision rather than an opt-in one.
Interesting…..
Where is the red flag on this one?
That’s too idiomatic for me at this time of night. Would you care to rephrase the question?
I’m sorry,
I was thinking about the fact that there has been soooo many issues with flash lately and yet adobe has it set up for bring in additional software (software that you refer to as a “marketing tool” at that). Something from McAfee ….I just that that this was quite interesting.
Only one out of nine of my computers here still have flash on it and that one hasn’t been updated in a while. So I wouldn’t even see this happen.
It’s Adobe’s fault for trying to profit off their free player download, which should instead be paid for by everyone who generates content for Flash using their professional tools (Creative Suite, Creative Cloud, etc.).
Instead they’re trying to double-dip and make money on both sides, thereby insuring that fewer people get the Flash player (some people will simply not install a product if it includes a bundle like this), thereby decreasing the value of their professional products (which is where they make money hand over fist).
I swear Adobe had its heart cut out years ago but nobody’s bothered to tell them they’re dead yet.
http://www.badboys.pw usa all the information ends here
note:flash can be called from attachments for example word even if it is disabled from chrome, removing flash is the safest bet
Sorry I’ll have to block some of your advertisements here Brian – we’ll turn in back on once the patch comes through!
Not sure what you mean. As far as I know, there are no Flash ads on the site.
Well that is what I get for making an assumption. My bad! I blocked ScriptSafe and Ad Block Plus once, and some of the ads went away, so I turned them both back on later after I got the previous flash update, and the place holders came alive again. I used to get pop up tabs that Comodo or WOT blocked when clicking on comment tools here, but since Comodo Dragon updated they’ve stopped.
Keep up the excellent work! I’ll continue to try keep things going when visiting your site! I’ll always recommend you when discussing IT security with my peers.
I installed .203 last week, the adobe site says that is still the latest version.
Adobe has not yet released an update that fixes the two latest vulnerabilities. Adobe has stated those will come this week.
1) You should highlight your Whitehouse.gov petition a little more on this page
2) You should update the Whitehouse.gov petition title with proper capitalization (‘remove’ is not currently capitalized)
I made sure to sign it, I’m going to write a letter to c-span too.
What is the link to the Whitehouse.gov petition?
Troy.
#
https://petitions.whitehouse.gov//petition/remove-requirement-adobe-flash-player-all-us-government-web-sites-favor-html5
Enough troubles for adobe flash player in a week
Does this 3rd Flash “problem” (in a week!),
also affect thr latest Firefox and PaleMoon browsers
under Ubuntu Linux 12.04?
What about the previous two
Flash problems, this week?
Brian, anyone?
This isn’t about the browser or OS. It’s about Flash. Don’t run flash and you will be ok.
Well I did it. Yesterday I uninstalled Flash from my daughters and my computer. I just got so tired of doing these stupid patches and wondering when my computer will gets hit, hijacked or what not.
Will I miss it, Hell No, it’s the websites loss not mine, I’ll just go to another site.
Will my daughter miss it, HELL YES, but like I told her I am not going to spend hours fixing her computer because she goes on these music websites, downloads all this crap and winds up with viruses, malaware etc. (yes, she has multiple antivirus and malaware on her puter but doesn’t update them!)
FLash is gone and I can now relax on Sundays ( I Think)
Thank You, Mr. Krebs for your great informative website
About the best you can do is remove admin rights from her account and block the obvious infection vectors (Flash, Java, Acrobat), but if she’s downloading software willy-nilly then she’ll still need regular visits from the computer doc since much of what she’s getting is likely trojans that spread via executables. If you could block her ability to run not-already-installed executables (so everything under her user account) then that’d slow down that.
Just a word of advice from another member of family tech support. I wish you well.
Thank you for your advise and that is exactly what she is getting…trojans that even went to her portable hard drive.
I never thought of admin rights, great idea, thanx.
http://hardenwindows7forsecurity.com/Harden%20Windows%207%20Home%20Premium%2064bit%20-%20Standalone.html
this is the app I use to stop exectuables from launching when not in the program directory, which needs admin access http://iwrconsultancy.co.uk/softwarepolicy It acts as a simple group policy for home editions of windows.
That’s some good info. Thanks for sharing. I’ll have to try some of that out on my parents’ computer.
I wonder what it’s like to work on the Adobe team that supports Flash? Does the boss yell at them every week because there are still problems with the code? Do the programmers get raises or promotions? Is working on the Flash Player punishment for something else they did? Is anybody embarrassed when yet-another problem is announced? Have they thought about re-writing it from the ground up instead of patching and patching? Or maybe it’s just one guy’s project and nobody cares because they give it away free and they’re just tired of fixing it anyway? There have been over 175 updates since 2006. (https://helpx.adobe.com/security/products/flash-player.html) Maybe it’s just really, really hard to write robust, secure code?
Uraaa !! Ya pidaras !!
Drugs, hacking , carding job offer !!
Yes, we can`t bliad !!!!!!!!
Everyone hating flash here, but do you think the lack of flash would stop them? They probably have a dozen other 0-day exploits unrelated to flash.
That makes me wonder how well the browser writers are handling the HTML5 video players and other animation gegaws. It seems that there are an infinite number of ways to trick Flash’s code with bad content.
Very true (there are other ways the bad guys would attack), but that would limit the attack surfaces the bad guys can use to one less – so we can concentrate on fixing the ones that remain (making the job easier to focus on).
Flash, like the Java Browser Plugin were created when security was not a concern – and here we are. I’m very curious about whether HTML5 and its extensive capabilities will be a vector once Flash becomes not worth it to use for the bad guys.
Couldnt stop laughing at the part “Unfortunately, some sites — including many government Web sites”
Call me a tinfoil hat wearer but these flash issues seems conveniently Govmnt encouraged ! 😀
You don’t think this:
https://firstlook.org/theintercept/2014/03/12/nsa-plans-infect-millions-computers-malware/
Is just going to happen without the government leveraging its civilian facing computer infrastructure? \s
That said, I’d ascribe it to the incompetence of the govt as opposed to a grand plan.
Many of these exploits the gov’t learns from other malicious hackers. This is just one example. When 17 year old kids can utilize these exploits, the only upper hand the gov’t has is technology like prism and subpoena power.
Brian,
For IT admin’s, like myself, who cannot remove Flash Player from their environment because we depend on websites that reqire Flash and therefore must continuously update it, I stumbled accross this option from Adobe
Extended Support Release – (Flash Player 13.0.0.302)
here is a quote from the link below
“Adobe makes available a version of Flash Player called the “Extended Support Release” (ESR) to organizations that prefer Flash Player stability over new functionality. We have created a branch of the Flash Player code that we keep up to date with all of the latest security updates, but none of the new features or bug fixes available in our current release branch. This allows organizations to ceritify and stay secure on Flash Player with minimal effort.
We recommend that companies focused on security and stability take a close look at this release option.”
http://www.adobe.com/uk/products/flashplayer/distribution3.html
Are you familiar with this? does it minimize the attack surface? less patches?
Thank for a all your good work!
Mozilla announces that it is blocking all versions of Flash Player in its browser with its latest update.
http://betanews.com/2015/07/14/mozilla-firefox-blocks-flash/
—————————
Just like the need to move away from using FAX machines……It’s time to see the writing on the wall
@GrifiN
The ESR version would be useful for organizations that use Flash for one of their internal applications. The ESR version would mean that the internal application would not need to be tested for any new features in a newer version of Flash, just for the bug fixes. It would still mean the same number of security updates, just less internal testing and fixing issues with the internal application due to new features in Flash. For what it is worth Firefox also has an ESR version.
So bottom line, same number of security patches and same attack surface, just easier to manage for an organization that leverages Flash.
Flash needs a whitelist option.
Flash Player 18.0.0.209 is now available for download from
http://www.adobe.com/uk/products/flashplayer/distribution3.html
Rumor has it there is a Java zero day as well….First one in several years.
http://www.csoonline.com/article/2947461/data-protection/cyberespionage-group-pawn-storm-uses-exploit-for-unpatched-java-flaw.html#tk.rss_news
I always wonder if there is a conspiracy with minecraft lol.
Brian,
You bring up some good “how to’s” for the average user. Is there any plans to have a quicktips/how to URL on your site so people can find them quicker than digging through all the articles?
I know some of these suggestions can be date sensitive, but for those needing a helping hand, it may be beneficial.
Good idea, thanks.
I see how to “disable” Flash on my desktop Mac (via Tools|Add-ons) but how do I clean remove the plug-in altogether? Or do I need to bother, once it is disabled?
Flash can still get triggered from other vectors & it’ll just get out of date with vulnerabilities as time goes on – best to remove it.
Here’s where you go for the Mac (Adobe has a separate un-installer):
https://helpx.adobe.com/flash-player/kb/uninstall-flash-player-mac-os.html
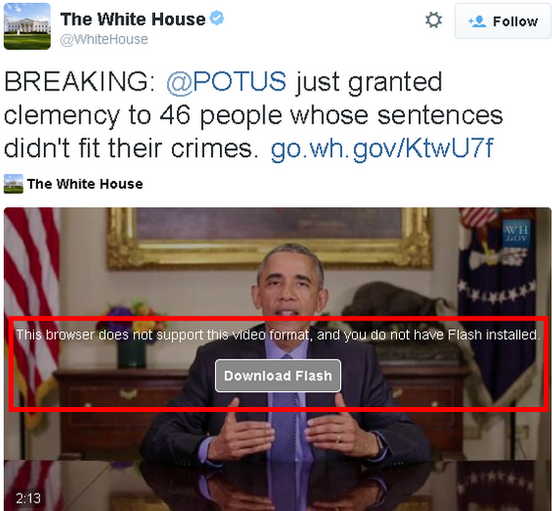
I have a quick question, in the article you show a image that is of a Twitter Post, and a Fake Video that says you do not have flash installed and to install it. Is this the way that this flash vulnerability is exploited?
That’s NOT a fake video; it’s Brian’s screenshot of a White House video tweet as it appears in his Flash-free browser. The message has nothing to do with the exploit; it just says Brian needs Flash to watch the video. If you still have Flash (just patched mine to .209 in both Chrome & Firefox — IE still doesn’t have it — *and* updated EMET), you won’t see the message even if you visit the White House’s Twitter feed directly — just the video with “play” button.
18.0.0.209 is out, and Firefox isn’t blocking it. I guess this new version fixes the latest holes?
I noticed this too. It is unfortunate that the organizations involved (Adobe, Mozilla) have not made any official up to date pronouncements on this issue. Instead we users are left with out of date press coverage.
I hope the press starts asking Adobe why it is not making official pronouncements on it’s web site about the current state of play. Every time a new flash version comes out Adobe should put out a press release explaining what it fixes.
I see that version 18.0.0.209 of Adobe Flash Player is out today. Any specific opinions about it?
It’s possible that Adobe have gone beyond the minimum, which be to just fix the CVE-2015-5122 and CVE-2015-5123 flaws. The Hack Crew dump is public, and one would hope that, given that it has already revealed three 0-days against Flash, Adobe engineers have been all through it, looking for a 4th, or 5th, or nth.
Vendors do silent (no CVE number, etc., requested) security fixes all the time. If they haven’t reviewed the contents of that dump, and another 0-day is found, it’s going to look astonishingly bad for them. It would solid proof, if more were needed, that Adobe just doesn’t care. So I have at least some hope that they have made a better-than-their-poor-usual research and engineering effort on this version.
Arguing against that is that they were undoubtedly in a hurry, due to the deadly accuracy of their footgun.
Version 209 is now out.
https://www.adobe.com/products/flashplayer/distribution3.html
Adobe Flash is a disaster and I’ve had problems with it for years. I keep Adobe off my machines as much as possible. Flash is a particular a problem in that it slows my computer and I can’t fix it by uninstalling and reinstalling it. The sooner they dump this program the better as far as I’m concerned. God its awful!
Hi, predominantly clueless tech guy wondering…
System requirements:
18.0.0.209 of Adobe Flash Player
2.33GHz or faster x86-compatible processor, or Intel® Atom™ 1.6GHz or faster processor for netbooks.
I’ve a Intel®Pentium®Dalton M 780 2.26GHz ~
Does/Will 0.07GHz make much of a difference?
–> Begin snark
Yes it will make a difference. It will take about 5% longer for your system to be pwned.
<– End snark
Perhaps I am missing something here. You could be a long-time poster, known and loved by all the regulars, for your really great sense of humor. But then perhaps I'm *not* missing something, so this has to be asked.
Brian's post is absolutely and completely about the security horror of having Flash installed *at all*. Rather than being so desperate to have it that you are worried about a 5% CPU clock difference slowing it down, Brian is advocating slowing it by 100%, by not having it installed.
I'm thinking that this may not be the ideal place to ask Flash performance questions.