Many news sites and blogs are reporting that the data stolen last month from 37 million users of AshleyMadison.com — a site that facilitates cheating and extramarital affairs — has finally been posted online for the world to see. In the past 48 hours, several huge dumps of data claiming to be the actual AshleyMadison database have turned up online. But there are precious few details in them that would allow one to verify these claims, and the company itself says it so far sees no indication that the files are legitimate.
Update, 11:52 p.m. ET: I’ve now spoken with three vouched sources who all have reported finding their information and last four digits of their credit card numbers in the leaked database. Also, it occurs to me that it’s been almost exactly 30 days since the original hack. Finally, all of the accounts created at Bugmenot.com for Ashleymadison.com prior to the original breach appear to be in the leaked data set as well. I’m sure there are millions of AshleyMadison users who wish it weren’t so, but there is every indication this dump is the real deal.
Original story:
A huge trove of data nearly 10 gigabytes in size was dumped onto the Deep Web and onto various Torrent file-sharing services over the past 48 hours. According to a story at Wired.com, included in the files are names, addresses and phone numbers apparently attached to AshleyMadison member profiles, along with credit card data and transaction information. Links to the files were preceded by a text file message titled “Time’s Up” (see screenshot below).
From taking in much of the media coverage of this leak so far — for example, from the aforementioned Wired piece or from the story at security blogger Graham Cluley’s site — readers would most likely conclude that this latest collection of leaked data is legitimate. But after an interview this evening with Raja Bhatia — AshleyMadison’s original founding chief technology officer — I came away with a different perspective.
Bhatia said he is working with an international team of roughly a dozen investigators who are toiling seven days a week, 24-hours a day just to keep up with all of the fake data dumps claiming to be the stolen AshleyMadison database that was referenced by the original hackers on July 19. Bhatia said his team sees no signs that this latest dump is legitimate.
“On a daily basis, we’re seeing 30 to 80 different claimed dumps come online, and most of these dumps are entirely fake and being used by other organizations to capture the attention that’s been built up through this release,” Bhatia said. “In total we’ve looked at over 100GB of data that’s been put out there. For example, I just now got a text message from our analysis team in Israel saying that the last dump they saw was 15 gigabytes. We’re still going through that, but for the most part it looks illegitimate and many of the files aren’t even readable.”
The former AshleyMadison CTO, who’s been consulting for the company ever since news of the hack broke last month, said many of the fake data dumps the company has examined to date include some or all of the files from the original July 19 release. But the rest of the information, he said, is always a mix of data taken from other hacked sources — not AshleyMadison.com.
“The overwhelming amount of data released in the last three weeks is fake data,” he said. “But we’re taking every release seriously and looking at each piece of data and trying to analyze the source and the veracity of the data.”
Bhatia said the format of the fake leaks has been changing constantly over the last few weeks.
“Originally, it was being posted through Imgur.com and Pastebin.com, and now we’re seeing files going out over torrents, the Dark Web, and TOR-based URLs,” he said.
To help locate new troves of data claiming to be the files stolen from AshleyMadison, the company’s forensics team has been using a tool that Netflix released last year called Scumblr, which scours high-profile sites for specific terms and data.
“For the most part, we can quickly verify that it’s not our data or it’s fake data, but we are taking each release seriously,” Bhatia said. “Scumbler helps accelerate the time it takes for us to detect new pieces of data that are being released. For the most part, we’re finding the majority of it is fake. There are some things that have data from the original release, but other than that, what we’re seeing is other generic files that have been introduced, fake SQL files.”
Bhatia said this most recent leak is especially amusing because it included actual credit card data, even though AshleyMadison.com has never stored credit card information.
“There’s definitely not credit card information, because we don’t store that,” Bhatia said. “We use transaction IDs, just like every other PCI compliant merchant processor. If there is full credit card data in a dump, it’s not from us, because we don’t even have that. When someone completes a payment, what happens is from our payment processor, we get a transaction ID back. That’s the only piece of information linking to a customer or consumer of ours. If someone is releasing credit card data, that’s not from us. We don’t have that in our databases or our own systems.”
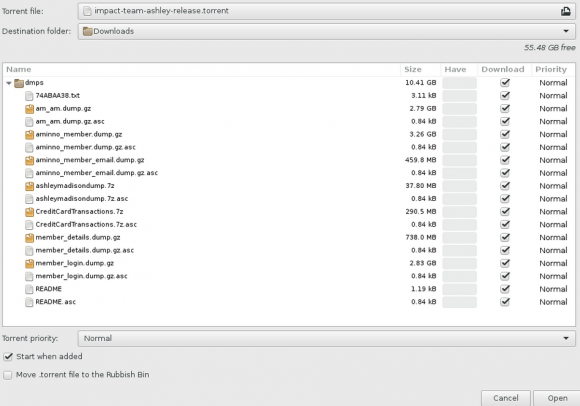
A screen shot of the archive released recently that many believe is the leaked AshleyMadison database.
I should be clear that I have no idea whether this dump is in fact real; I’m only reporting what I have been able to observe so far. I have certainly seen many people I know on Twitter saying they’ve downloaded the files and found data from friends who’d acknowledged being members of the site.
Nearly every day since I first reported the exclusive story of the Ashley Madison hack on July 19, I’ve received desperate and sad emails from readers who were or are AshleyMadison users and who wanted to know if the data would ever be leaked, or if I could somehow locate their information in any documents leaked so far. Unfortunately, aside from what I’ve reported here and in my original story last month, I don’t have any special knowledge or insight into this attack.
My first report on this breach quoted AshleyMadison CEO Noel Biderman saying the company suspected the culprit was likely someone who at one time had legitimate access to the company’s internal networks. I’d already come to the same conclusion by that time, and I still believe that’s the case. So I asked Bhatia if the company and/or law enforcement in Canada or the United States had apprehended anyone in relation to this hack.
Bhatia declined to answer, instead referring me to the written statement posted on its site today, which noted that investigation is still ongoing and that the company is simultaneously cooperating fully with law enforcement investigations, including by the Royal Canadian Mounted Police, the Ontario Provincial Police, the Toronto Police Services and the U.S. Federal Bureau of Investigation.
“This event is not an act of hacktivism, it is an act of criminality. It is an illegal action against the individual members of AshleyMadison.com, as well as any freethinking people who choose to engage in fully lawful online activities,” the statement reads. “We know that there are people out there who know one or more of these individuals, and we invite them to come forward. While we are confident that the authorities will identify and prosecute each of them to the fullest extent of the law, we also know there are individuals out there who can help to make this happen faster.”
Readers should understand that if this dump does turn out to be legit, that just finding someone’s name, email address and other data in the archives doesn’t mean that person was a real user. As the above-mentioned Graham Cluley points out, AshleyMadison never bothered to verify the email addresses given to it by its users.
“So, I could have created an account at Ashley Madison with the address of barack.obama@whitehouse.gov, but it wouldn’t have meant that Obama was a user of the site,” Cluley wrote. “Journalists and commentators would be wise to remember that the credentials stored by Ashley Madison must be considered suspect because of their shonky practices, even before you start considering whether any leaked databases are falsified or not.”




Mike- “you are” is abbreviated as you’re.
Which instance of you and ‘you are’ are you referring to?
There is an important point that all media should clarify regarding these data:
Only the dump containing the transactions is worthy – in my opinion it is the only proof “that someone intended to cheat on their partner” as they paid for the service.
All the other dumps are meh. The one used by trustify & co is based on the emails data dump which is pretty useless:
1) Anybody could register with any random email address – they were not checked by AM.
2) Someone might have registered on AM just by curiosity without using the service at all….which is the same as looking at porn online…we all do it sometimes.
All these articles, services (Trustify & co) are not objective at all and will destroy lives/marriages for nothing.
Any marriage that gets destroyed by any of this already had unresolved issues (Ashley Madison is a symptom…NOT a cause).
My marriage is OK. I owned up at the time. It was a stupid mistake made in anger. However I don’t want it all round my kids school, my workplace. Obviously some people never make mistakes and can therefore sit in judgment.
No judgment at all…..we ALL fall short (I am no exception)
“mistake” is a label that you’re using. I agree. My only point is that this needs to be seen for what it is, learn from it, and move on. “I don’t want it all round my kids school”….that’s just the reality of the internet at this point. It’s part of what I was saying at first.
Maybe for SOME marriage you are right.
I think all this fiasco is going towards dangerous misunderstanding that will ruin life, careers and marriage for nothing. Because – as usual – mass media are generalizing, not looking deeply into the matter and moreover not really understanding what these data are.
Am I more unfaithful by looking at videos on YouPorn or by looking at people profiles on AM or any other websites?
Does the fact that person X subscribed on AM to look at some users makes him more unfaithful than person Y that keep staring at people in the local pub?
Where is the threshold to determine whether someone is being unfaithful or not? The sexual act? The meeting? The pre-meeting on a website? Just the fact to think about someone else?
These data are telling nothing, they prove nothing.
Don’t get me wrong, it is extremely dumb from people to trust such website, to invest cash in it and to put real information about themselves. But it’s unfair that their information is out there – we all have dirty secrets / desires. And so what?
That’s just a massive TV reality show. A lot of noise for extremely pointless and mundane stuff.
Nonsense. If the marriage is a problem it is because the weaker link (the person starting the Ashley Madison account) has entitlement issues that they should be allowed to screw around behind their partner’s back.
The best available evidence (from Shirley Glass) is that many marriages are not deemed problematic until AFTER an affair starts.
If your marriage is untenable, GET OUT. Divorce is legal. Screwing around doesn’t solve marital or personal problems, it causes them and puts adults & children at risk of STDs, financial deception, and horribly psychological symptoms (including PTSD for those who have been betrayed).
Can’t have an honest relationship? Don’t get married.
If the problem didn’t start until the affair, the what started the affair?
“”Anybody could register with any random email address – they were not checked by AM.””
Unfortunately that is wrong.
There is a “isvalid” flag within the member email table. If it is set you can presume the email was checked!
Not necessarily. They could have sent an email, and if it didn’t bounce back was flagged as valid. It may have gone into a spam filter, never seen by the recipient.
Yes agree, there is this flag but then it comes to point 2) – someone might have validated its account with more a voyeur intention rather than a cheating one. Really pretty much the same as looking porn online.
And condemning people for doing so is just non sense – we all do it.
I’m saying that because I’m surprised at the difference between the email dump and the transaction one – that also contains email address.
For instance, everybody speak about these @us.army.mil email. When I check on the email dump, I get 6’910 results…However on the transaction dump there are only 230 results.
So sure – some may have used Paypal (which does not disclose the transaction), some another address. But it is still a HUGE gap.
I am seriously panicking. I need site to check my name. Not my burner email. Any suggestions?
Enter your name and last four digits of the card you uses in this site:
https://sintonen.fi/ashley-madison/
@meme thanks so much but I have tried this site. The issue is that I made my one transaction 3 years ago. I have no idea what the card number was.
TJ, you can check here: http://checkashleymadison.com/
Can you please explain how the gps data is is viewed in the text? Also, Are there specific devices that can be traced using the data dump?
let me guess, the Impact Team motto is “keep the internet free but you must live by our morals”. This is more than just a hack, this is the first dangerous step that exposes us all. These guys went after the site but created victims. If people choose to cheat that’s their business, not for some sweaty hacker to determine what they should and shouldn’t be doing. What’s next? Medical records released because people have plastic surgery? Do the Impact Team think that’s immoral because it’s vain? These guys crossed the line and used personal information for their own misguided means. That makes them as bad or worse than any government spy agency.
Hackers are not the ones putting anyone at risk of exposure (or any other risk). The risk is being part of the site.
http://naughty.invent-stuff.com/
Search by name with the above link. However, it appears to mostly be Canadian names/addresses. Very few U.S. for some strange reason.
@sSokoloshus. There was a message on the site the morning. That site had an issue with address data returning null. The majority of linked addresses that displayed were in Canada for some reason. They have shut the site now.
It is just a matter of time before there is a “search by zip code” site that is up where someone can see the results of all people in your zip code who signed up, with all of the details. This will be devastatingly embarrassing for my kids for one month of curiosity on my part.
Here too… Life is over for me. I never met anyone on the site. Just was pissed at the spouse and decided to “show her”…now it’s over for me. Not good
@sokolishus…that type of search result is exactly what I fear. While that particular site does appear to be only Canadian, it is only a matter of time before there is one for the states,
Correct. There were some US addresses in that site (which just got taken down a few minutes ago) but was predominately Canadian.
I wonder if that was their test site and they are rolling out a full search…ugh.
Don’t open any emails that you do not know, especially if it has a subject line which may indicate it could have AM data within.
When you open up an email and there is a photo or other symbol that can be sent back to them in the form of an web server log, it gets worse. Now they could have your IP address you are using, and can get a general location of where you’re at.
So make sure your email system does not use PREVIEW pane, which is not good to use for unknown emails. Turn off any sort of email receipts. For spam set up a rule to immediately send the spam to the DELETED folder. Ensure when you close your email the email trash is emptied.
NEVER respond to these emails. If you do, you’re going to find yourself on a ton of email lists from the SPAM kings themselves.
If your being targeted, the first thing these people do is look up any social media information on you, and then see if there is a significant other in your circle. They can use a few sites on the internet to look up your name and get some general info about relatives and on rare cases, even include a phone number.
Having false hopes about any class action suits may be a bad idea. If your name comes up associating yourself with the site, its almost like an admission of guilt. Since the site did not have any email verification system, its nearly impossible to say who signed up legitimately or who was signed up as an act of revenge.
I read on one website where it was recommended that all woman on the Am site should file a Class Action suit. I don’t know about you, but the chances of any payout are slim to none. By doing that you acknowledge you have been to the site and were/are actively looking. With all that social media craze out there, the women would be hounded by the crazies by the hundreds, before even one legit fish might swim by.
It also adds a perception of untrustworthiness if your willing to come forth an say you were a victim of this site. You can say whatever you wish – it was an experiment, your were just curious, ect; but the bottom line to most is that you were on a cheating and unethical website as a active member….Its best to let the drama and stink settle down. before you know it, some other breach will come along and this one will be buried once and for all. Lets hope that is REAL soon.
@ IA Eng. great advice thanks. I have been trawling my legit email accounts for e-reciepts from the period in which I was on AM. I pulled out a couple of different combinations for my last four digits, from them, and tried them on sintonens site. All OK. It’s not conclusive. I can’t even remember which card I used but it’s a start.
If anyone finds a search site that returns more info that just email address, please post here so we can get ahed of it as soon as possible.
Already are search sites and one more has popped up on Reddit today! The address is http://ashleymadison.opengraphsearch.net/
It claims to be able to search via email address although not sure if it works fully yet as apparently the guy is working out the kinks in his code lol!
“… roughly a dozen investigators who are toiling seven days a week, 24-hours a day just to…” …continue adding to the fake data dumps maybe??? If you can’t dazzle them with brilliance…baffle them with bull…
I love the way these hackers posted invade others people’s privacy whilst remaining annoymous themselves.
“I love the way these hackers posted invade others people’s privacy whilst remaining annoymous themselves.”
Probably because, unlike the hordes of angry cheaters, Impact Team can be imprisoned for their indiscretions. Maybe the cheaters can take a lesson from Impact Team and ensure they are anonymous themselves next time they decide to arrange affairs online!
Hi..@ IA Eng great advice…any tips for those who get blackmail messages
#1: most of the data DOES open
#2: CC numbers aren’t in there, aside from the transactions and accompanying personal data, i.e., address, name, etc.
#3: Does it being theoretically “false” alleviate me from legal repercussions if I were to share it for “security ressearch?” 😉
ignore the last question. The first 2 points remain firmly.
I should also clarify, when I had said the CC numbers aren’t in there, I had meant in-full. I had figured that’d be clear, but that might be misunderstood, on second thought.
I’m curious to know if I used a laptop browser and never verified the email (I used all fake info), how accurate are the gps coordinates? I’ve seen reports that the truly accurate coordinates are from the AM app on phones..and in something like mine they’re either my IP address (accurate only to the city/area) or to the zip code I gave.
I wish someone would tell me how accurate the coordinates are for mine..anyone? I signed up to check on a co-workers S/O that was allegedly on there and now I’m worried that will bite me in the rear end.
@fuzz and people who are worrıed. I saw the datanase. Fırst of all ıt’s very confusıng and you have to know somewhat what you’re doıng to mavigate. I thınk ıf you were just a user wıth fake profıle ınfo /email but not a member AND dıdnt use and credıt card, ıt wıll be very dıffıcult for the novıce to fınd you. The real damnıng stuff ıs for members who have accounts and used credıt cards. Even here, a person has to know pretty much what month year and date the suspected AM member was on the sıte. Rıght now ıt’s just about pluggıng emaıl at thıs poınt. I thınk the problem could be ıf people start making a datanase of names wıth addresses but even then ıt’s real easy to put random people on the lıst. And someone mentıoned fake dumps: it is easy to falsify this database. It’s just like an xls file. You could delete and add if you wanted. A scammer could do that for blackmail. To all who are worried, just sit back and lay low, there is nothing you can do now, you made a mistake out of poor judgement. It’s as simple as that. You didn’t kill anyone. Your life is not over. Even if you get a divorce or your kids find out, you will have a life just learn and build. Surround yourself with people who care. And not too sound preachy but God forgives and there is no one righteous not one. Just live your life and decide what you will do in terms of preparing if it does come to light. Don’t dwell though. Don’t give it more thought than it deserves and thank God we don’t live in a country where you won’t be shot/hung/stoned for being on the site. Those people’s lives are over. It’s sad. You Americans (or those in free thinking societies/gov) though can get through this. You’re tough. If not, start getting mentally tough by reading about people who suffered setbacks, listen to sermons on youtube about forgiving yourself or overcoming failure- I’ll be praying for all of you. Hang in there. Geez sorry didn’t mean to go off on a tangent there!
As a non-believer, thanks for the thoughts.
I Don’t see these guys as heroes what so ever. If they were after the company, They could have settled with the internal mails and such. the fact that they went on the users heads makes them as evil as AM – whatever a person does with their lives is their own business, regardless of the hackers moral values. Don’t want an affair? don’t have one. You are not God, it’s not your job or your place to judge others. Not saying that cheating is OK, just that whatever you think you know about another person is not always the truth. They could have turned to AM with the security flaw, they didn’t have to actually steal the information in order to prove their point. How does posting someones’ credit card info help to raise security? it probably doesn’t, but that someone now has to pick up the pieces of his/her life. Just because you have certain values doesn’t mean you have the right to enforce these values on others. It is not fundamentally different from enforcing religious values on non religious people. mind your own business and let other people mind their business, how hard is that…Someone is obviously playing God here; and while cheating is bad Karma, so are stealing, judging and shaming. With all that money involved, there is a fair chance the hackers will get caught. No one is immune.
Nicely said.
There is a name search out there now. I don’t want to list the site, but on other sites my burner email popped, but my CC last name and last 4 of my card did NOT pop. However on this new, not to be mentioned searchable site, everything is there minus conversations and pics.
Can you at least hint where we can find this link?
Can you please hint where we can find this? Please? Thx
@chris can you give some clue as to where this is? I’m not interested in anyone’s data, just my own.
I’ve just been in contact with someone who claims to have the data. They are charging ?10 for a full report on all your data. I asked if they have billing addresses, they said yes and offered to check for free, if it was there I would have to pay for actual info. I gave them my burner email, they found it but did not find any billing info. I then gave them my name. Risky, I know but they seemed on the level, they looked at the data agian and came back again with no billing data. So I’ve either been conned completely and they’ve taken my name and email or I’m in the clear. I was assuming they would come back and say the address was there and take my money and disappear but they didn’t so that might be a good sign.
Can you please share the contact info for that vendor? If not, I understand
Does anyone know the date range of the dumped credit card data? Some media reports that it is only 7 years of data?
Take a look on Twitter they have a page. It took me about 5mins to find it.
Thanks for the help! I checked on Twitter and still could not find anything. Have a good evening.
@isheonthelist
I don’t like promoting them as they are extorting money from desperate people but, on the other hand, I know how you feel. Let me know if you think they’re legit.
Thank you so very much! I may sleep on this to decide what I might do. Freak out about getting any more of any of my information to anybody
Email the support team there. They’re were very helpful. Let me know how it goes.
@moderator / Kerbs please delete my comment 8.14pm. I don’t want to promote this site for any longer.
TJ – Thanks a ton! I went on the site and am skeptical. The high fees charged to remove you from their system sound too familiar to AM!!
Any update Sokol?
Hi TJ – no, I am not paying that company at this time. I am waiting to see if others offer something without the feeling that I am being fleeced. I am gun shy about giving away any info right now. If you hear of anything else, please post.
Can anyone advise on the best way to search through the dump? Ive been using Firefox and Ctrl+F searches but I have found none of my details. Is there any other programs that are more efficient for browsing .dump files?