I spent four days last week in Mexico, tracking the damage wrought by an organized crime ring that is bribing ATM technicians to place Bluetooth skimmers inside of cash machines in and around the tourist areas of Cancun. Today’s piece chronicles the work of this gang in coastal regions farther south, following a trail of hacked ATMs from Playa Del Camen down to the ancient Mayan ruins in Tulum.
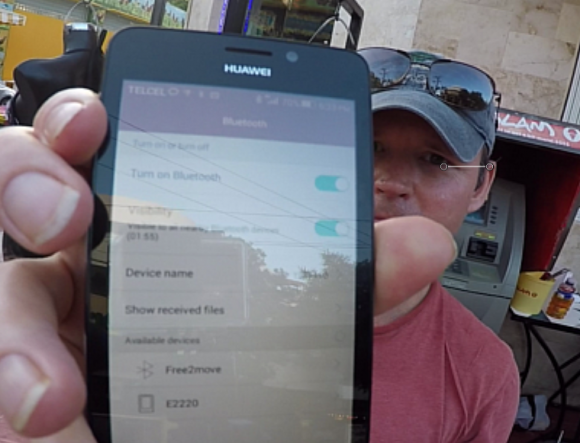
As I noted in yesterday’s story, the skimmers that this gang is placing in hacked ATMs consist of two Bluetooth components: One connected to the card reader inside each machine, and another attached to the PIN pad. Both components beacon out a Bluetooth signal called “Free2Move.” The thieves can retrieve the purloined card and PIN data just by strolling up to the hacked ATM with a smartphone, entering a secret passcode, and downloading all of the collected information.
Having found two hacked ATMs in Cancun — including one in the lobby of my hotel (the Marriott CasaMagna) — I decided to check out other tourist destinations in the region. On the way to Tulum, I dropped in at the Barcelo, a huge, all-inclusive resort. The security guards at the front gate at the resort initially prevented me from entering the complex because I didn’t have reservations.
After 10 minutes of Googling on my phone and a call to the front desk, the guards seemed satisfied that I was interested in buying a day pass to the hotel’s various facilities. The gate lifted and I was let in. Five minutes later, the very first ATM I stopped at was found to be emanating the telltale Free2Move Bluetooth signals indicating a compromise.
No sooner had I finished documenting that hacked ATM than a security guard rode up on a motorcycle and asked if I was having trouble finding the day-pass desk. I replied that I’d be headed that way shortly.
The Barcelo security guard followed me closely as I returned to my rented Jetta and drove to a different building in the complex. Multiple security guards were beginning to shadow me at a respectful distance. I decided it was best to at least demonstrate that I had an intention of buying a day pass.
The Barcelo reception desk said the price would be USD $80 per person. Feigning shock over the hefty price tag, I declared loudly that I had to hit the hotel’s ATM to withdraw more cash in order to pay such exorbitant prices. That ATM also was beaconing the Free2Move Bluetooth signal, but the ATM itself returned errors stating that it was temporarily offline and unable to dispense cash.
That outage turned out to be the perfect excuse to visit a third ATM in the complex, as I again loudly explained to the security guy following a few paces behind. By this point, a much more stern and beefy guard began following me around on foot, his walkie-talkie buzzing periodically as I crossed the hotel campus. The third and final ATM I checked also was compromised. While I was sure there were more ATMs I hadn’t checked in other areas of the resort, I decided not to press my luck, and hopped back in the Jetta and resumed my journey to Tulum.
TULUM
Halfway down the southbound four-lane highway from Cancun to the ancient ruins in Tulum, traffic inexplicably slowed to a halt. There was some sort of checkpoint ahead by the Mexican Federal Police. I began to wonder whether it was a good idea to have brought along the ATM skimmer I’d received from a source instead of leaving it in the hotel safe. If the cops searched my stuff, how could I explain having ultra-sophisticated Bluetooth ATM skimmer components in my backpack?
After several nervous minutes of creeping traffic, I was waved on through the checkpoint and immediately felt silly for having gotten so worked up about it. However, upon my arrival 20 minutes later in Tulum — a popular tourist destination due to its proximity to the Mayan ruins — I would have a much closer encounter with the police.
As I pulled into the area where tour buses normally drop off passengers by the hundreds each hour, a number of men stood waving pamphlets and offering “Cheap!” parking that was anything but (or at least I thought at the time). Each was trying to direct me to park the Volkswagen in one of several large, dusty lots.
“I’ll just be about five minutes,” I said, stupidly putting the vehicle in park on the main street right in front of the tourist lot. The attendants just shook their heads and began hailing other newcomers.
The Tulum visit yielded another three ATMs within a few hundred meters of each other that were all emanating the Free2Move signal. But unfortunately, that jaunt took more than five minutes: When I returned to the Volkswagen, I found a parking ticket on the windshield and the parking attendants smirking, gleefully shouting in Spanish that I should have listened to them and parked in their lot.
The ticket wasn’t for that much money. More concerning, the license plate had been removed from the front of the car. At first I thought someone had stolen it, but one of the locals explained that this was a common practice used by Mexican police to ensure people actually pay quickly and — more importantly for them — locally, for their parking and traffic fines (and then some). The removal of the plates from the rented vehicle necessitated a stop at the police station at the entrance to the ruins; 20 minutes and the equivalent of $200 later, I was back in possession of the car’s front plate and headed back toward Cancun.
PLAYA DEL CARMEN
My next stop was Playa Del Carmen, another tourist destination popular with Americans but quite a bit less rowdy than the Plaza Caracol nightclub area in Cancun. A lengthy and sweaty stroll down Playa del Carmen’s leafy 5th Avenue revealed five more compromised ATMs pulsing out the Free2Move bluetooth signals.
After a late and thankfully enormous lunch at a local Argentinian steakhouse, I was feeling refreshed enough to continue to the third leg of the journey. With twilight approaching and colorfully lit signs blazing to life along the main tourist boulevard, a steady breeze set in and mercifully tamed the otherwise sticky and oppressive heat. It was time to board the hourly ferry to Cozumel.
COZUMEL
This speedy cruiser takes riders on a 45-minute ride to Cozumel, an island whose surrounding deep green-blue clear water makes it an immensely popular spot for scuba divers and tourists alike. By this time, the fitness tracker on my arm tapped my wrist to report that I’d massively overachieved my daily fitness goal: I’d walked almost 13 miles at that point, and I hadn’t even strolled around Cozumel yet.
Once off the ferry in Cozumel, I commenced about two more kilometers of walking the main commercial road adjacent to the ferry dock. I found four more apparently hacked ATMs that were blasting out the telltale bluetooth signals.
I was physically drained, but very happy with the results of my reconnaissance missions, and glad to have been able to see so many places on the coast in such a short time.
I arrived back at the CasaMagna Marriott after midnight, exhausted but also interested in stopping by the ATM to see if any action had been taken. To my astonishment, someone had finally unplugged the Cardtronics peso machine that was stealing card data and PINs from users. With the power to the hacked ATM unplugged, the Free2Move beacons were no longer transmitting.
Unfortunately, I had to catch a flight home the next morning. But as the taxi dropped me off in front of the airport, I decided to check all of the cash machines in the terminal. The first one I found just inside the check-in area was clean (at least it didn’t appear to be beaconing bluetooth signals). The second ATM, however — situated next to an escalator and a currency exchange shop but before the security screening checkpoint — was broadcasting the now familiar bluetooth signal.

This woman raced ahead of me as I was filming this compromised ATM. She was successfully dissuaded from using it.
As I prepared to document the compromise on my GoPro camera, an apparently American woman raced ahead of me and beat me to the ATM. Before she could enter her PIN, I turned off the camera and explained who I was. The traveler replied that she was in a great hurry. I told her that the ATM she was about to use would soon cause her checking account to be hijacked and drained.
The woman looked at me in what seemed to be exasperation for a moment, before withdrawing her card from the machine and heading wordlessly across the airport lobby to the other ATM.
Packing my camera gear back into its case, I carefully peered around the backside of the ATM. I noticed it was plugged into the wall facing the escalator.
As I rode the escalator up to the security gates and gazed down over the handrail, I could no longer see the darkened screen of the ATM, but somehow neither was the power cord still attached to the wall. Pulling out my new Hauwei phone for the last time, I smiled as the Bluetooth scanner tried in vain to find any beacons.
In case you missed it, please see the first installment in this series: Tracking a Bluetooth Skimmer Gang in Mexico. Later this week, we’ll take a look at the shadowy organization that appears to be responsible for this crime spree.
If you haven’t already seen them, please check out the other two stories in this three-part series:







I wish there were a list of what legitimate ATM Bluetooth Identifier/MACs might look like given that 100% of the ATMs I’ve looked at in 7-11’s and restaurants around Arlington County, VA have bluetooth on…
Good job.
Folks, here’s a heads up. Bluetooth can and most of the time, is a hidden signal. You have to have discover and bt card or chip active. On both sides. To receive it on your phone or tablet. Just because you do not receive a reply, does not mean its not comprised. It may be waiting for the join code. You stated in one part, you received a sporadic signal on Bluetooth, it may have just been activated and transmitting to the recorder. That would have been a good time for a fisheye shot. Maybe…
Gotta spread this one….
Brian, I’m curious that you only tested this in Mexico. I lived there (in Merida Yucatan) for over ten years without ever having a problem. I did get “skimmed” a few years ago, but my bank figured out it was from a Shell Station in California.
So, this isn’t just Mexico, right? I mean, maybe the masterminds behind this are from Mexico, but it seems to me that the ATMs in the USA (and elsewhere) are just as dangerous, no?
Shell station in California? My card was also skimmed from a Shell Station in California (near my house), was it the one in Malibu? Since that is where i figured it was from, also the owners of that station are Armenian and probably connected with Armenian Power (street gang in LA who are heavily involved in fraud).
“ATM Machine?” Automated teller machine machine? Personal identification number number? Human immunodeficiency virus virus? Tsk, tsk, tsk.
“The Los Angeles Angels” = “The The Angels Angels.” (That’s always been my favorite one.)
You should visit the La Brea Tarpits sometime.
“More concerning, the license plate had been removed from the front of the car.”
PLEASE! Use proper English. This is an excellent blog but I hate to suddenly encounter such a glaring error.
Fixed: “Of more concern, the licence plate…”
Really… out of all that, this is what you can’t move past and feel the need to comment on?
Great article, great content, very informative.
Free2Move
http://www.digikey.com/product-detail/en/F2M03GLA-S01/647-1009-1-ND/1634848
47 bucks
They have 2066 in stock ready to ship !
It’s a piece of hobbyist bluetooth communications equipment, not nefarious in and of itself. Just like how because how hackers use the internet does not mean that the internet itself is an illegal tool.
you know those guards are most likely also working for the mexican mafia gangs and they could have been eyeing Krebs because they have to guard those compromised ATMs since the stolen funds from the skimming helps to pay those crooked guards under the table.
FYI. Those “guards” or internal police at the resorts, they are keeping the security of the property as is a Private Property, All Inclusive, nobody can trespass just like nothing, if not, everybody will pass freely, eat and drink everything they wish for free use all the facilities for hours and leave without paying a dime. Just for your info. Thanks
@Brian:
> The Tulum visit yielded another three ATMs within a few hundred meters of each other that were all emanating the FreetoMove signal.
I think you mean “Free2Move” here.
Question is, is the Free2Move bluetooth signal the only sign of a skimmer? What if the criminals change the name of the signal to “Hotel Blue” or something more innocent like that?
Bluetooth devices generally need to be set to “discoverable” to show up in a scan as Brian describes, and usually only stay discoverable for a minute or so… you can confirm this with most generic BT headsets right after they are turned on. Additionally bluetooth is typically 30′ range, although there are devices/operating modes capable of 300′.
Upshot… stand in the vicinity of an ATM and scan and if you see anything at all check again in 5 minutes. If the device still shows up, that’s probably questionable. Also many devices (my car for instance) will have sensible names, so anything that *isn’t* a skimmer may well be self explanatory.
I was thinking the same thing. I am sure a more improved scheme is underway somewhere unfortunately.
congratulations! successful and lived to tell about it.
Lessons Learned
1.)most physical safety levels are UNDERESTIMATED. Take the
‘tourist trip’ in Ukraine with heavy artillery.
2.)obvious targets tend to be ‘americans’ and ‘tourists.’
3.)the operation needs 2 or 3 person team. The problem with USA
journalism operations is the one man operation and/or one person
whistleblower
4.)how to recruit talent that is local such as college students, etc
5.)the simplest way to defeat couter-surveillance of such a ‘bugging
BT device’ would be the wireless is only on at 5am to 6am, during the
dark hours. An video security camera would get a fuzzy photo of
a man (in sunglasses and facial ‘hair’) with unbalanced IR.
6.) physical access to the ATM device is the root cause.
7.) in the signals battle, perhaps the next step will be spread
spectrum on alternative frequencies.
so, Krebs, pack your SDR software defined radio and auto scanning
hardware next time?
Excellent work, Brian.
The whole company is a fake front – be careful !
I felt like I was was reading a spy novel. It is a very serious matter for sure, but I found it to also be a great story.
Just goes to show: “you can’t make this stuff up”!
I am looking forward to testing some ATMS in my area to see if they happen to have this.
It is crazy how many different ways the bad guys think of to steal your sensitive data. It makes me wonder if anything at all will be safe to use over time!
I am surprised that the bad guys did not name the skimmer something more legitimate looking like the name of the hotel or gas station since giving it an unconventional name might raise some eyebrows.
3 of us were skimmed at the same machine in Puerto Aventuras (outside Chedraui) on the first week of Aug. 2015. We all had charges that showed up at Tommy Hilfilger in Cancun as well as other common venders. My card was also used for thousands of dollars in a restaurant. Clearly, I know these crooks did not eat that much in food or merchandise? (8,009 tota on Aug 8). There must be partners on the “cashing” side of this scam? I have written up the businesses on Trip Advisor. That’s as far as I could go. But there has to be more action.
Btw, my husband was in the airport on Thursday. That machine at the escalator has been removed.
I truly appreciate your report.
I live and Mexico ad yes, I have had occasional fraud usually form websites and gas stations
. Tourist areas are ripe for fraud everywhere . Most of my credit card fraud has come out of the US .
However this is great article to warn tourists of what can happen to yo
.( anywhere)
PAY Attention!!!
How do you use your own smart phone to test each ATM BEFORE you use it?
IS there a software you can buy or download??
Thanks again!
The tip I found for international travel was to find a single ATM near where you are which is a major bank and in a vestibule. This gives you the best chances of avoiding a skimmer and the best opportunity for tracking it later if there is fraud. For all other transactions, use a credit card.