A time-honored method of extracting cash from stolen credit cards involves “reshipping” scams, which manage the purchase, reshipment and resale of carded consumer goods from America to Eastern Europe — primarily Russia. A new study suggests that some 1.6 million credit and debit cards are used to commit at least $1.8 billion in reshipping fraud each year, and identifies some choke points for disrupting this lucrative money laundering activity.
Many retailers long ago stopped allowing direct shipments of consumer goods from the United States to Russia and Eastern Europe, citing the high rate of fraudulent transactions for goods destined to those areas. As a result, fraudsters have perfected the reshipping service, a criminal enterprise that allows card thieves and the service operators essentially split the profits from merchandise ordered with stolen credit and debit cards.
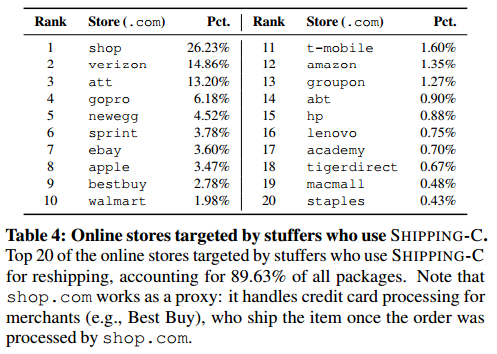
Much of the insight in this story comes from a study released last week called “Drops for Stuff: An Analysis of Reshipping Mule Scams,” which has multiple contributors (including this author). To better understand reshipping scheme, it helps to have a quick primer on the terminology thieves use to describe different actors in the scam.
The “operator” of the reshipping service specializes in recruiting “reshipping mules” or “drops” — essentially unwitting consumers in the United States who are enlisted through work-at-home job scams and promised up to $2,500 per month salary just for receiving and reshipping packages.
In practice, virtually all drops are cut loose after approximately 30 days of their first shipment — just before the promised paycheck is due. Because of this constant churn, the operator must be constantly recruiting new drops.
The operator sells access to his stable of drops to card thieves, also known as “stuffers.” The stuffers use stolen cards to purchase high-value products from merchants and have the merchants ship the items to the drops’ address. Once the drops receive the packages, the stuffers provide them with prepaid shipping labels that the mules will use to ship the packages to the stuffers themselves. After they receive the packaged relayed by the drops, the stuffers then sell the products on the local black market.
The shipping service operator will either take a percentage cut (up to 50 percent) where stuffers pay a portion of the product’s retail value to the site operator as the reshipping fee. On the other hand, those operations that target lower-priced products (clothing, e.g.) may simply charge a flat-rate fee of $50 to $70 per package. Depending on the sophistication of the reshipping service, stuffers can either buy shipping labels directly from the service — generally at a volume discount — or provide their own [for a discussion of ancillary criminal services that resell stolen USPS labels purchased wholesale, check out this story from 2014].
The researchers found that reshipping sites typically guarantee a certain level of customer satisfaction for successful package delivery, with some important caveats. If a drop who is not marked as problematic embezzles the package, reshipping sites offer free shipping for the next package or pay up to 15% of the item’s value as compensation to stuffers (e.g., as compensation for “burning” the credit card or the already-paid reshipping label).
However, in cases where the authorities identify the drop and intercept the package, the reshipping sites provide no compensation — it calls these incidents “acts of God” over which it has no control.
“For a premium, stuffers can rent private drops that no other stuffers will have access to,” the researchers wrote. “Such private drops are presumably more reliable and are shielded from interference by other stuffers and, in turn, have a reduced risk to be discovered (hence, lower risk of losing packages).”
AMPLIFYING PROFITS
One of the key benefits of cashing out stolen cards using a reshipping service is that many luxury consumer goods that are typically bought with stolen cards — gaming consoles, iPads, iPhones and other Apple devices, for instance — can be sold in Russia for a 30 percent to 5o percent markup on top of the original purchase price, allowing the thieves to increase their return on each stolen card.
 For example, an Apple MacBook selling for 1,000 US dollars in the United States typically retails for for about 1,400 US dollars in Russia because a variety of customs duties, taxes and other fees increase their price.
For example, an Apple MacBook selling for 1,000 US dollars in the United States typically retails for for about 1,400 US dollars in Russia because a variety of customs duties, taxes and other fees increase their price.
It’s not hard to see how this can become a very lucrative form of fraud for everyone involved (except the drops). According to the researchers, the average damage from a reshipping scheme per cardholder is $1, 156.93. In this case, the stuffer buys a card off the black market for $10, turns around and purchases more than $1,100 worth of goods. After the reshipping service takes its cut (~$550), and the stuffer pays for his reshipping label (~$100), the stuffer receives the stolen goods and sells them on the black market in Russia for $1,400. He has just turned a $10 investment into more than $700. Rinse, wash, and repeat.
The study examined the inner workings of seven different reshipping services over a period of five years, from 2010 to 2015, and involved data shared by the FBI and the U.S. Postal Investigative Service. The analysis showed that at least 85 percent of packages being reshipped via these schemes were being sent to Moscow or to the immediate surrounding areas of Moscow.
The researchers wrote that “although it is often impossible to apprehend criminals who are abroad, the patterns of reshipping destinations can help to intercept the international shipping packages beforethey leave the country, e.g., at an USPS International Service Center. Focusing inspection efforts on the packages destined to the stuffers’ prime destination cities can increase the success of intercepting items from reshipping scams.”
The research team wrote that disrupting the reshipping chains of these scams has the potential to cripple the underground economy by affecting a major income stream of cybercriminals. By way of example, the team found that a single criminal-operated reshipping service can earn a yearly revenue of over 7.3 million US dollars, most of which is profit.
A copy of the full paper is available here (PDF).




Besides authorities intercepting a fraudulently ordered package, another “act of God” happens when UPS/FedEx/USPostalService delivers a package to an address different from the one printed on the address label.
I have been contacted at least 3 times from people wanting to buy multiple Hay Huts, an $800. Item. I tracked down the owner of the card in one instance, and it was indeed stolen. When these instances occur, to whom should I report them to?
Hi Brian, I can’t open the pdf as seems is corrupted or damaged. May you double check that
Thanks
pdf works for me
How about ddos/mitm combination attack on those suckers?
FBI should register massive amount of Drops, then work with Russian police (or perhaps FSB) to apprehend people getting those packages. I think it wouldn’t even require political negotiations (about US’ practice of “extraterritorial prosecution” of Russian citizens for example), since Russia would directly benefit from decimating this shadow market. There are quite a lot of taxes that could be extracted from $1.8 billion.
“Then work with Russian police”
Ha !
There’s about a 90% chance they already get a cut of the action.
Corruption is rampant in Russia and the government has no incentive to cooperate with outsiders as this is big income for the Russians
It probably more like 99% chance they’re in on it.
Indeed, when Putin was originally elected he promised to clean out all the corrupt officials working in government. Turns out all he did was clean out all the corrupt officials who refused to kick back money to him and his political backers. So now instead of thousands of corrupt schemes, there’s just one. Wooo, progress.
I actually am from Russia if that wasn’t obvious from my name. Although the corruption level is higher than in US i wouldn’t give it 90% figure. It’s organized crime’s MO (and kind of logical one) to have people on payroll. And by your (and 2 others’) reaction i gather you think that US police is somehow immune of it. Here’s the newsflash: it’s not! There are corrupt cops in US. Yet crime gets investigated and prosecuted in US and in Russia.
You don’t even have to leave this site to read about it:
http://krebsonsecurity.com/?s=russia&x=0&y=0
Nobody said the US is corruption free, quite the contrary. While crimes do get investigated in the US often times those that get priority are the ones that affect those political landscapes the most unfortunately. On a local level it happens far less however I would say that 99% of the politicians in the US are bought and paid for by big business and their interests will come first when push comes to shove.
PDF works fine for me, running Windows 10 Pro x64. I received goods about 8 years ago, I knew it was a scam, the scammer actually called me and asked me what was wrong. If I remember correctly it was from Neiman Marcus clothes worth about $700 charged to my credit card, I contacted local police and returned goods to Neiman Marcus.
Drops are apparently being recruited from listings on Monster and other on-line employment sites. I receive two to three offers a week. There is always a mismatch between the ‘company’ offering the job and the email address of the offeror.
Is there an agency that would investigate these job offers?
I think the problem with trying to track down the job posters is that they’re all overseas, and the posting itself isn’t illegal.
Very interesting information.
I work in a field that is involved in stolen credit cards purchasing retailer gift cards. From an interesting conversation with the Secret Service on a case, it would appear that almost all stolen CC information involves Russians.
I’m curious how long until – if they aren’t already doing so – the reshipping scam sites (the job posters) start collecting NPI on the applicants. If the drops think this is a real job, and the stuffers aren’t looking for a lasting relationship, why not ask for SSN and other personal info when “interviewing” the job applicant. You wouldn’t think twice to provide personal info to a potential employer.
These people do ask for personal information. I was contacted by an add from Monster.com to be a courier hub for smaller packages. I took a phone interview to see what it was about. A person working for this company contacted me and had an extremely strong foreign accent to the point where I could barely understand him. I was extremely skeptical at the time. They then sent me the most bare bones application I’ve seen to date, which had very poor grammar and misspelled words. Needless to say, I don’t contact them back.
Edit: Should have stated in the first post that I did not yet read the attached paper, which very early on states that they do collect this info. Thanks Derek!
Edit: Should have stated in my first post that I did not yet read the attached paper, which very early on states that they do collect this info. Thanks for that info, Derek!
Edit: Should have stated in the first post that I did not yet read the attached paper, which very early on states that they do collect this info. Thanks Derek!
There is a whole web site dedicated to “scamming the scammers” in the Nigerian fraud world, 419 Eater. Would be fun to find a community to do this anonymously for these credit cards thieves. Of course no one should want to use there real home adress though. Any ideas on scamming the scammers without having to actually receive stolen goods?
You can give them the address of your local police department pretending it is your own.
Should the AVS (address verification) protect the merchant against a lot of these types of scams? If the shipping address isn’t verified, and doesn’t match the CC’s billing address, shouldn’t the transaction be flagged as suspicious, and scrutinized?
AVS only applies to the billing address.
But yes, I develop ecommerce sites for several luxury brands and it is common practice to flag orders where the shipping and billing address do not match for manual inspection by customer service before shipping. We’ve found that in many cases it is easy to identify fraudulent orders based on the shipping address and email address used and whether they bear any relation to the billing info.
I suspect this is why most of the fraud is targeting larger volume resellers who do not have the customer service staff to manually inspect questionable orders..
As an issuer, we took nearly 100k loss, on one credit card account alone, about a year ago via the monster.com job listing technique described above. Good times.
Hi,
Just a minor thing, but I believe you have a bunch of hard html line breaks in your copy.
For example:
However, in cases where the authorities identify the drop and intercept the package, the reshipping
sites provide no compensation — it calls these incidents “acts of God” over which it has no control.
Cheers,
-Greg
These high-tech companies really could curb the market for their stolen goods by having a “stolen” database which retailers (and even validated end-users) can report back the stolen serial number to and then the high-tech company can brick the device as soon as it goes online.
Terrible idea. If there existed such a simple way to brick a device remotely, how long until that would be abused by criminals, or for censorship?
Not only is that a bad idea where possible (as Daniel wrote) but only a small number of goods are even theoretically “brickable”. If that really were implemented, the thieves would likely just switch away from those goods.
Brian, try “wash, rinse, repeat”. It makes more sense. Good part of another series it seems.
Money never smells in Russia it’s just other business in russsia I think nobody don’t cares banks don’t care either they can classified this as dept and from dept they just print more money so it’s just business for financial institutions aswell also JP Morgan Goldman sacs and other rich financial fat cats are related with Bolsheviks Lenin Trotsky and so on…. I think the hands washing hands and only looser is that most honest person who payes tax and work 8-hours per day as I do and I’m the person who keep this parasites alive I lost hope long time ago I don’t think government do anything serious about
What happens if somebody signs up to be a drop, then opens and keeps whatever merchandise is sent to them? And does this repeatedly?
Why don’t you try it and let us know how it worked out for you?
At best, you’ll need a good lawyer and a good doctor.
Interesting. I’d certainly not want to do that without using a disposable cell phone, a disposable email address and a disposable physical address. Remember that these scammers are probably pretty good at using the internet to uncover information. And if they’re smart they require a residential physical address for the drop (i.e.your home). If there’s an abandoned house nearby you can claim as yours, good for you, but no using one of those office store boxes.
Easy way for the US law agencies to have those thieves apprehended:
1- Pose as a drop willing to reship a product;
2- When the stolen good arrives, fill the package with so-called “homosexual propaganda”
3- Send the product to Russia
4- Notify Russian law agencies about the package containing the homosexual stuff
5- Sit back and relax: The Russian government will do all the work for you, free of charge!
Brilliant!
It seems the push towards EMV still focuses on transactions made on-site. It would be nice if the credit card industry would promote the availability of customer USB EMV readers to allow for website purchases based on EMV.
I started reading your blog regularly just recently because I was informed that it was a good computer security site. But it just seems to be about skimming.
Are you going to talk about anything else and if not can you recommend a good computer security blog.
Thanks
Rick
You can see categories on the right side of this page…
For other computer security blogs, you could try:
Schneier on Security
https://www.schneier.com
And pretty much every antivirus and security company… E.g.
Naked Security: Computer Security News, Advice and Research
https://nakedsecurity.sophos.com
(Also McAfee, Google, Verizon, VeriSign, Dell SecureWorks,…)
https://www.sans.org/
It would seem that the with the ubiquity of ATM’s we are in for a never ending escalation of techniques to ensure the continuation of the fraud.
My bank has the option to send me an email every time cash is withdrawn from an ATM … The email is sent within minutes of the withdrawal (letting me know when the withdrawal occurred) and tells me how much was withdrawn from the ATM. I’ve enabled that option. At least I will know quickly when the inevitable happens. There are actually many different kinds of email alerts I can setup with the account with the possibility to also set minimum trigger levels.
This is an actual sample of the email. I’m travelling outside the USA, so the time is translated to Eastern Standard and the currency shows the USD amount and not the local currency of the withdrawal:
Sat Sep 26, 2015 02:40:55 AM EDT
Debit Card Activity
For account ending in 1346:
An ATM Withdrawal for $218.24 from CASH ADVANCE ATM was posted to your account on 09/26.