Imagine buying an internet-enabled surveillance camera, network attached storage device, or home automation gizmo, only to find that it secretly and constantly phones home to a vast peer-to-peer (P2P) network run by the Chinese manufacturer of the hardware. Now imagine that the geek gear you bought doesn’t actually let you block this P2P communication without some serious networking expertise or hardware surgery that few users would attempt.

The FI9286P, a Foscam camera that includes P2P communication by default.
This is the nightmare “Internet of Things” (IoT) scenario for any system administrator: The IP cameras that you bought to secure your physical space suddenly turn into a vast cloud network designed to share your pictures and videos far and wide. The best part? It’s all plug-and-play, no configuration necessary!
I first became aware of this bizarre experiment in how not to do IoT last week when a reader sent a link to a lengthy discussion thread on the support forum for Foscam, a Chinese firm that makes and sells security cameras. The thread was started by a Foscam user who noticed his IP camera was noisily and incessantly calling out to more than a dozen online hosts in almost as many countries.
Turns out, this Focscam camera was one of several newer models the company makes that comes with peer-to-peer networking capabilities baked in. This fact is not exactly spelled out for the user (although some of the models listed do say “P2P” in the product name, others do not).
But the bigger issue with these P2P -based cameras is that while the user interface for the camera has a setting to disable P2P traffic (it is enabled by default), Foscam admits that disabling the P2P option doesn’t actually do anything to stop the device from seeking out other P2P hosts online (see screenshot below).
This is a concern because the P2P function built into Foscam P2P cameras is designed to punch through firewalls and can’t be switched off without applying a firmware update plus an additional patch that the company only released after repeated pleas from users on its support forum.
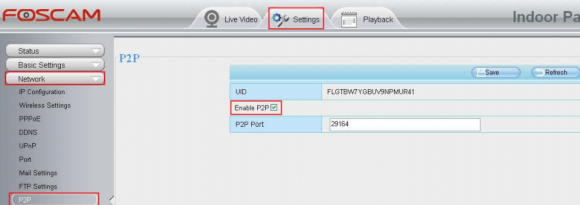
Yeah, this setting doesn’t work. P2P is still enabled even after you uncheck the box.
One of the many hosts that Foscam users reported seeing in their firewall logs was iotcplatform.com, a domain registered to Chinese communications firm ThroughTek Co., Ltd. Turns out, this domain has shown up in firewall logs for a number of other curious tinkerers who cared to take a closer look at what their network attached storage and home automation toys were doing on their network.
In January 2015, a contributing writer for the threat-tracking SANS Internet Storm Center wrote in IoT: The Rise of the Machines that he found the same iotcplatform.com domain called out in network traffic generated by a Maginon SmartPlug he’d purchased (smart plugs are power receptacles into which you plug lights and other appliances you may wish to control remotely).
What is the IOTC Plaform? According to ThroughTek, it’s a service developed to establish P2P communications between devices.
“I read the documentation provided with the device as well as all the website pages and there is no mention of this service,” wrote Xavier Mertens, an incident handler and blogger for SANS. “Manufacturers should include some technical documentation about the network requirements (ex: to download firmware updates).”
In another instance from May 2015, this blogger noted similar communications traffic emanating from a digital video recorder (DVR) device that’s sold in tandem with Internet-enabled surveillance cameras made by a company called Swann.
Likewise, postings from Dec. 2014 on the QNAP network attached storage (NAS) user forum indicate that some QNAP customers discovered mysterious traffic to iotcplatform.com and other Internet address requests that also were found in the Swann and Smart Plug traffic.
What do all of these things have in common? A visit to ThroughTek’s Web lists several “case studies” for its products, including Swann, QNAP and a home automation company based in Taiwan called AboCom.
ThroughTek did not respond to requests for comment. A ThroughTek press release from October 2015 announced that the company’s P2P network — which it calls the Kalay Network — had grown to support more than seven million connected devices and 100 million “IoT connections.”
I contacted Foscam to better understand the company’s relationship to ThroughTek, and to learn just how many Foscam devices now ship with ThroughTek’s built-in, always-on P2P technology. Foscam declined to say how many different models bundled the P2P technology, but it’s at least a dozen by my count of the models mentioned in the Foscam user manual and discussion thread.
Foscam customer service representative David Qu wrote in reply to requests for comment that “ThroughTek provides P2P technical support service for us.” He also said the P2P cameras merely keep a “heartbeat” connection to Foscam’s P2P server to check the connection status with the servers, and that no camera data will be stored on the company’s servers.
“The details about how P2P feature works which will be helpful for you understand why the camera need communicate with P2P servers,” Qu explained. “Our company deploy many servers in some regions of global world.” Qu further explained:
1. When the camera is powered on and connected to the internet, the camera will log in our main P2P server with fastest response and get the IP address of other server with low load and log in it. Then the camera will not connect the main P2P server.
2. When log in the camera via P2P with Foscam App, the app will also log in our main P2P server with fastest response and get the IP address of the server the camera connect to.
3. The App will ask the server create an independent tunnel between the app and the camera. The data and video will transfers directly between them and will not pass through the server. If the server fail to create the tunnel, the data and video will be forwarded by the server and all of them are encrypted.
4. Finally the camera will keep hearbeat connection with our P2P server in order to check the connection status with the servers so that the app can visit the camera directly via the server. Only when the camera power off/on or change another network, it will replicate the steps above.”
As I noted in a recent column IoT Reality: Smart Devices, Dumb Defaults, the problem with so many IoT devices is not necessarily that they’re ill-conceived, it’s that their default settings often ignore security and/or privacy concerns. I’m baffled as to why such a well-known brand as Foscam would enable P2P communications on a product that is primarily used to monitor and secure homes and offices.
Apparently I’m not alone in my bafflement. Nicholas Weaver, a senior researcher in networking and security for the International Computer Science Institute (ICSI), called the embedded P2P feature “an insanely bad idea” all around.
“It opens up all Foscam users not only to attacks on their cameras themselves (which may be very sensitive), but an exploit of the camera also enables further intrusions into the home network,” Weaver said.
“Given the seemingly cavalier attitude and the almost certain lack of automatic updates, it is almost certain that these devices are remotely exploitable,” he added. “It is no wonder that Director of National Intelligence James Clapper is worried about the Internet of Things, how many government officials have or may unwittingly install potential spies like this in their home.”
If you’re curious about an IoT device you purchased and what it might do after you connect it to a network, the information is there if you know how and where to look. This Lifehacker post walks through some of the basic software tools and steps that even a novice can follow to learn more about what’s going on across a local network.




The reality of IoT is not about denying its use throughout your home. In 5 years, you’ll have to search harder for non-IoT devices at your [insert favorite store here] then you will for an IoT-enabled device. Make no mistake: The concerns of IoT exploits are significant, but you’d better start preparing your network defense as opposed to denying the use of IoT in your home. Half the readers here will likely never know they are using an IoT device until they stumble upon the ability to network their [insert IoT device].
Not just No, but Hell No.
We do not have to assume the supine position to having relentless surveillance shoved at us. Public outrage killed off Google Glass (“become a walking surveillance drone and look like a dork”), and it can kill off the Insanely Dangerous Internet Of Things (IDIOT).
All it’s going to take is “teleplague” malware in IDIOT fridges (cycle the temp up when the humans are away, and back down when they’re in; humans eat spoiled food that’s within its expiration date; tens of thousands of food poisoning cases descend on hospitals; CDC and FBI go looking for bioterrorist attack….).
As in, all it’s going to take to kill off the obnoxious Roboto-Mobiles is kidnapware (“send us bitcoin now or we slam you into overpass”).
Nobody wants this crap except the hucksters who sell it, the cybercriminals & terrorists who plan to hijack it, and the deluded narcissists who think that talking to a forest of mics and cameras in their home makes them some kind of movie star rather than a prisoner of the New Stasi. Fie on all of them.
If I want home automation I’ll build it with relay logic. Otherwise I’ll get up off my arse to flip wall switches and turn on appliances the good old-fashioned way, that won’t get me a dossier in some sociopath’s identity theft file or some corporation’s “predict and control” algorithm, or some would-be tyrant’s politico file. And you should too. While you still can.
;p
Thank you, Squirrel.
P.s. Now we have to kill you.
Boris and Natasha
Let us know when you run for office (or declare incipient revolution?). I’ll vote for you.
Suspicious Swann DVR traffic…
https://thecomputerperson.wordpress.com/2015/05/03/compromised-or-suspicious-swann-dvr-traffic/
I’ve comment on this before but got no response. It’s not just cameras. Who knows what kind of surveillance and/or self-destruct circuitry the Chinese are building into the electronics they sell to us. We keep looking at the software for flaws, but is ANYONE looking at Chinese hardware? Probably not.
So this camera manufacturer got caught. They will apologize, they will lose business, but so what? The Chinese dictatorship will just lean on other companies over there to build Trojans into the products Americans want to buy because said hardware has “all the features we want” and it’s all cheap being built, as it is, by virtual slave labor.
So, Brian, would you care to reply to my comment this time?
Jeff B.
Many people scrutinize the hardware as well as the software, what you describe just wouldn’t be worth the effort to implement as it would lead to, too many premature failures.
As for this particular issue, its a dumb default setting in a long line of dumb default settings, pioneered by american companies insistence that consumers are idiots and must be given convenience above security at all times, i mean look at the US adoption of chip and pin to combat card fraud….
Jeff, picking specifically on China is unwarranted when we know the NSA is hacking hardware in America and leaning on HW developers to enable further subversion. This isn’t a country-specific problem.
If you will look. Its not just nationals doing this. Not just “”. How do you, as a company generate a revenue stream. Happy users spreading the name? Ad blasts? Newspaper, consumer advertising? How, sales. How do you target ads? Get relevant ads to a interested consumer, get your product in front of a consumer without walmart? Remember its not just NSA, or mossad,or GM looking, at whats in that stream.
I don’t like ANYONE putting Trojans into hardware or software. However China is a dictatorship with 1.35 BILLION people under the thumbs of a small number of people at the top. And who are those people anyway? The “Cultural Revolution” in China ended 40 years ago. How many people at the top in China today participated in the slaughter (30 million dead) of the Cultural Revolution, not to mention the “Great Leap Forward”? That suggests to me that China is a far bigger threat to the future of humanity than the NSA ever was or ever will be.
That’s right! Trust the governments?! When they don’t talk to each other? Even our own?
BTW: Bravo to apple for standing up to the NSA on the recent case of security vs privacy.
You’ve really got to stop listening to scare stories about [insert other country name here], and start looking more closely at who is telling you the scare stories.
As for China, it doesn’t give a damn about you, your computer, your pr0n downloads, or what you do in front of your camera.
Only your fellow countrymen can profit from such information, so only they will harvest it with an eye to profiting from it.
Mostly, though, whether foreign or domestic, this kind of ridiculously insecure behaviour is a result of the typical fervent belief held by software developers that their bunch of code is the most important thing in the entire universe.
lol the old Chinese dictatorship…. what about the younger US dictatorship, nobody cares about that…
That’s nice security insight of IOT devices .
Though i am in agreement with security & privacy issues and proprietary misdeeds by tech firms; But this is true with any new innovative technology – Even in Virtual Reality gadgets which claims to be next big thing , we will certainly get to see loopholes in security & privacy.
I think , Now its the time to have a standardization and control authority for security, A global Security Rating platform which will provide security rating for every online device n should be a mandate for every device before it lands in market.
Not really an IoT thing to be honest, more a dumb default setting meant to give any one without any experience remote access to their webcam. Its the old impressive safe door, dry wall on the sides problem.
As for a global rating agency wouldn’t work, as you still would have cloned hardware bypassing it getting into the market, never mind that it would be to much like govt imposing regulation on industries which already play by the book.
Hi,
does dnscrypt solve the problem of data transfer from our IoT to undesired “china” network ?
Probably not, in this case its a stupid default setting, not any thing malicious per se, its meant to give standard users an easy to use remote access to their cam, as this software powers not just these cams but various baby monitors. Thats the price people keep paying for conveinience
Come across this a while back when installing a “comparable” cam to our usual rack mounted cameras, turned out i couldnt disable it via the gui, but if you downloaded the config file it was a simple case of flipping the 1 to 0 on the phone home line of the config…
HI-Safe super sustem Pvt.ltd
mr – sonu ku singh
con-0120-4227515- 7827077513 9015027515
Its another Matter of Convenience. When I bought my security system and cameras, I simply ran wires . Another thing I did NOT do was connect all of it to the internet. The odds of you NEEDING to see your house while away in minor.
I’ve had my internet capable DVR for many years. Even back then these stinking things have had hard coded user names (root) and a password in them.
Salted Hash put up an article about a username and password combo that has been found in a LOT of these devices. So, no matter how secure you want them, it only takes a moment for them to get in and change your config…… Unless you are wired and not connected to the Internet of Tragedies.
http://www.csoonline.com/article/3034284/security/hard-coded-password-exposes-up-to-46000-video-surveillance-dvrs-to-hacking.html
remember this?
http://www.csoonline.com/article/2989251/vulnerabilities/ip-camera-makers-pressure-researcher-to-cancel-security-talk.html
Here are a few others
http://www.csoonline.com/article/3029974/security/study-of-another-ip-camera-reveals-serious-problems.html
http://www.csoonline.com/article/2989251/vulnerabilities/ip-camera-makers-pressure-researcher-to-cancel-security-talk.html
Well put. I’ve also disconnected my security camera from the internet. Just google “IP Camera root access” to see a list of vulnerabilities. My camera has root password 123456 baked into firmware and even if you manage to change it, it reverts back on the next power cycle. Presumably for ease of use, the camera also uses UPnP to punch through your router firewall. This “feature” also cannot be disabled in the camera — you can “uncheck” it but it reverts back on the next boot. These two features are too much for me.
How complicated was not connecting your security system to the Internet? I’ve been looking all over for a good tutorial, so far with no success. I’m hoping someone will post a step by step guide on instructibles.com
(Yes, I’m just joking. Sort of.)
Cameras that phone home?
Seems like a wonderful way to gather pictures of people for software that “tags” individuals (and, perhaps, associates them with other data available on the web…and even with pictures gathered via the old-fashioned HUMINT way) in order to build profiles of where people work, live, and play.
In what is simultaneously granular yet broadly-scoped, such “tagging” and pattern analysis can tell you who/where/why to harvest sensitive data…said harvesting to be carried out, perhaps, by the original IoT device OR by other e-devices (PCs? Laptops? Tablets? Routers? etc., etc., etc. ad infinitum, ad nauseam.) that have chips/firmware providing additional, unpublished “features”. Merely identifying variations in the movement patterns of particular groups of “persons of interest” can yield notification of sudden activity/inactivity at “entities of interest”.
In toto, a treasure mine of information for (you guessed it) “interested parties”.
Funny you write this article, I have 8 of these cameras myself, some of different generations and types. I had this same issue but an even stranger issue. I have all traffic blocked outbound on my nextgen firewall unless allowed. I had purchased a couple of newer models of this camera and hooked them up just like previous ones. They would work for a couple minutes then lock up. Video would freeze and the system would become unresponsive. I went round and round with Foscam and Newegg and finally returned them for new ones. New ones did the same thing. I finally took them to another network and hooked them up and they worked fine. Immediately I saw the issue. Looked in my firewall and sure enough it was chatting like mad. I then opened up the ports for those cameras and they worked instantly. I then closed the ports back on the firewall and they continued to work until this day even. After looking at what the devices are doing basically the device WILL NOT WORK unless it is able to communicate out to Foscam ATLEAST once. No matter what I disabled in the camera it did not help it. But after that first communication it finally worked and continues to work. Very very shady activity with these cameras but I guess that’s the trade off for cheap stuff that functionally works these days from the Chinese.
The title of this article should actually be “Why people *should* fear the Internet of Things.” There are plenty of problems to be had:
1) The number of software architects and engineers who are capable of creating products like this correctly are fairly few and far-between. They are for the most part priced out of the realm of the consumer electronics companies making these products.
2) The management of most of these companies probably have no idea what the security issues are, don’t even consider the costs until product liability becomes an issue.
3) Only a very tiny percentage of consumers are technically savvy enough to understand the potential problems. They will generally assume that reasonable security is implied when they buy a product, but it takes fairly specialized expertise to determine whether or not a product is safe to use or not. Even so, the effort involved is so overwhelming that you either have to pursue it as a serious hobby or a paid profession.
4) Eventually there will be a demand for third-party audits and certifications. Obviously, they won’t find everything but at least they can find the really stupid mistakes that seem to be endemic in the industry. This demand won’t kick in until Bad Things happen and there is screaming and gnashing of legal teeth.
5) IoT vendors should probably commit to some policy of updates, which will have an interesting effect on the consumer electronics industry. Most people don’t replace their televisions, refrigerators, burglar alarms, etc. every 1-3 years, which is the normal duration for which software updates are provided (if ever). This is what strikes me as deeply problematic with the IoT business model – it makes quite a few purchases that were previously considered longer-term obsolete within an unacceptably short period. Unless you’re a Fortune 1000-sized company the budget and resources for this sort of support simply won’t pencil out (and even then they might not).
I remember hearing about the idea of automated refrigerators when I was in highschool. When you ran out of something, it’d order more of your favorite soda/food/whatever via the internet! I thought it sound silly then, but now with the rise of the IoT concept, silly has become frightening.
Does anyone know if the Ring doorbell is calling out unwanted?
It’s not calling out to anything other than the Ring server for update queries. It auto updates as needed.
Even more fun, it can be trivially hacked!
Go to YouTube and search for Samy Kamkar and see his video on doing it, or Google: Digital Ding Dong Ditch Prank – hacking wireless doorbells w/Arduino and RTL-SDR
Some years ago D-Link or was it Belkin had a issue that caused a lot of users with these routers to loose internet connection. The routers had been sending out a heart beat to a server that went down. The routers all had internet connection to them but since they could not hit the heart beat server, they all just stopped working. AS a ISP, we just had to take any traffic to that IP and relay it to another computer so it could respond to the routers & they could get online again.
This is starting to get exhausting. I just fixed my default user id and password on my router; now it’s possibly our security cameras. I tried the fix with the nMap and got so lost and confused I just deleted it; didn’t understand any of it. My husband and I have jokingly talked of turning the clock back 20yrs for one month and remember what it was like before we inundated ourselves with technology from hell. It is sounding more and more tempting.
This gets off topic, but five years ago I spent a year in a rural environment outside the U.S. Once a week or two weeks, I took a 45 minute bus ride into town where I would spend a few hours accessing the Internet, catching up on email, phoning friends, etc.
The first few weeks were hard. But being mostly disconnected for that year was amazing. Since that time I moved into town and finally got home internet and I’ve been connected ever since. I’ve had a difficult time finding a middle ground. Maybe it’s impossible. But that year of being mostly disconnected was so unstressful and relaxing. If anyone reading this ever gets the opportunity, I recommend trying it (and trying it for more than a few weeks).
I’ve got Foscams too for monitoring the street in front of the house. I got them after considerable research, the scary thing is that the Foscams are some of the least sucky IP cameras on the market, based on user reviews I’ve read of other cameras most of the rest are much, much worse. If anyone has any recommendations for decent outdoors night-vision IP cameras with Wifi and motion detection that don’t cost an arm and a leg, I’d be interested in hearing about them.
Thanks for article.
Curious, if the Ip Camera or other device is connected to the “guest” SSID/Network on a home router, is the main/primary network safe?
Thanks
I expect this all will be tied in with the UN conspiracy of one world government in which everyone will be monitored through the IoT. Expect a man with a placard picketing a government and now Apple office near where you live soon.
I’m much more worried that a sophisticated team of thieves will hack into my internet enabled security system to cover their tracks when they break into my house and steal my . . . security system? Not a helluva lot here they could steal! 🙂
The IOT are taking over. I recently read an article about how the internet of things also applies to children’s toys…https://securitycatch.com/internet-connected-toys-a-new-worry-for-parents/. I would have never thought that I am now going to have to pay attention to how a child’s toy is going to utilize data from the child online. However, it seems that this is how the world will be even more so in the future.
I think to avoid this problem routers default configuration should disable UPnP configuration. On this way cameras would not be able to access P2P firstly
Thank you – we appreciate you for writing this article and raising awareness for security issues with the Internet-of-Things. We also apologize if we previously failed to respond or address a question about ThroughTek’s P2P technology.
Undoubtedly, allowing a device to be accessed with a domain name or public IP address poses risks and vulnerabilities for the device. ThroughTek works with device manufacturers and technology brands to establish secure and direct communications between devices, to enable direct data transfer without storing data, while minimizing exposure of devices. A common misconception about P2P is it means for downloading and file sharing for illegal use and copy right infringement. However, in our case, this actually reduces the risk and provides a more secure way for data transfer. Our core technology especially becomes crucial when handling IP Camera and surveillance devices, as we are able to deliver video streaming securely from camera devices directly to smartphones.
As a standard, we include encryption to secure communication with the device and authentication for access control to validate identity and to determine permissible interactions. As well, we continue to work with IoT partners to handle data transmission security and communication from hub to cloud.
As the concept of connecting things is slowly being adopted, it is important that industry leaders in the IoT space prioritize to increase overall understanding. It will take time to holistically look at the entire ecosystem and identify ways to improve IoT security.
We are glad to see that the public involved in discussions, and we take your feedback seriously as an opportunity for future improvements. Please send us a note below if you have more questions or feel free to send us an email directly mkt@tutk.com.
ThroughTek
Spoken like a true salesman.
“A common misconception about P2P is it means for downloading and file sharing for illegal use and copy right infringement.”
Tell that to the AA’s! If they had their way, P2P would be completely destroyed as a viable technology usable for ANYTHING.
Improving security? Did I just read “improving” security? Please. These devices are designed and built specifically without any type of security. Re-read the article, please: these devices boot up and start sending data without any notification or permission of the owner. There is no security, and it was intended this way.
“The IOT”
I think of that phrase as “The IdiOTs”
As far as I can tell the only real issue here is that they give you the option to disable the feature, but it still calls out to their central server.
If you are going to buy a camera that lets you view the images over the internet using your phone or web browser… how do you think it is going to work? Its going to have to send the data across the internet. And for this to work in a way that 99% of their customers can do it, there will need to a central server to coordinate the communication. It actually sounds like they did a good job of setting up the network and considering security (again except for the part where a ping still goes out when the feature is “disabled”).
One could argue that the default setting should be to have the internet access of the camera disabled. But if the device is being sold with one of the major features being images over the internet – then one can debate if the default should be for the feature to be disabled.
If you don’t want an internet enabled camera, don’t buy an internet enabled camera. And in response to the claim that some of the cameras don’t say anything about P2P, the link in the article goes to a camera’s whose description includes “cloud services.” Furthermore, it states that the images are viewable over the internet. P2P is just the technical way they are doing it – why advertise that detail?
IoT security is an issue, and 99% of products are not doing it correctly. However, I just don’t see the issue with anything described about these products – again except for the ping when the feature is disabled.
Am I missing something?
Why does it have to be a cloud server? Why does it have to use any kind of P2P protocol?
Why not run it all through a home based webserver? It would seem to be much more dangerous as it is than to do this.
If you want to setup my own webserver with cameras, and not have the camera have built in web services, that is easy – just buy a camera that doesn’t advertise _any_ kind of ability to view the image over the internet.
And if you are an IT pro or a well skilled “Computer Person” then yes, setup your own web server. But the average computer user can’t setup a web server. Furthermore, how do you secure the web server? Again, the pro can do it, but not the average user. If the web server gets hacked, the entire machine hosting it may be at risk. Now it may be more than just images, it could be the user’s TaxCut pro data, passwords, email, everything at risk (and no the average computer use isn’t going to buy a dedicated box to just host a web server.)
And then what service do you use so your smartphone knows what IP address your ISP has assigned to you at any given moment. Yes, there are services for that, but you have to know about them and set them up. And setting up a service like dynDNS isn’t that much different than the P2P solution this product puts in place.
Look, I’ve got my own webserver, I run ownCloud at home, and have a VPN. I back up using opensource enterprise level solutions. I got it all, but I’m a pro. My brother who needs to monitor his business, or my sister who wants a nanny-cam can’t set those things up and maintain them. And I don’t have the time to maintain such things for everyone I know. These cameras aren’t designed for me, they are designed for the 95% of computer users that are just users – not pros.
Again, IoT security is a real problem – I just don’t get why the specifics of this article are cause for alarm.
Ok, so the bigger question is one of user ineptitude and all this IoT stuff has less to do with manufacturers. I mean, if a user actually cared to learn something about this stuff and were actually willing to devote time and energy to taking responsibility for what they pay money to own….people (users) would not even waste their time on lesser quality stuff like what Krebs is talking about.
Uh, sorry, but I think some of this discussion has tunnel vision based on our interest in a complex field.
Do you really expect consumers to spend more time learning the technical details of a $99 webcam than they do their new car? The better and more sophisticated the technology, the more important and deceivingly simple the use of the technology must be. Would you say folks can’t drive their car unless they know how to program the on-board computer or modify most of the subsystems? That’s ridiculous, just as expecting consumers to have to secure network devices is ridiculous.
A balance must be struck, and the technology must be delivered in a way that millions of non-experts can “just use it” like a tool.
I agree with other posts close by this one – it seems like this manufacturer did very well except for the inability to fully disable the connectivity option.
I too am a pro in this field, one that is tired of having to tweak everything at home like I do at work all day. I base my purchases on the technical spec’s and then I just want it to work reliably as advertised.
I don’t expect people to know how to program the onboard computer subsystems. However, I do completely believe that it is perfectly reasonable to expect that the person that buys a car have an understanding that the engine oil will need to be changed on a regular basis and that the tires do get worn down as a natural course of driving. If you want to change the oil and tires yourself that’s fine. If you want someone else to do it, that’s fine. But thinking you can drive the car forever without ever considering it’s needs is the ‘ridiculous’ thing you speak of. Lots of people do this and are likely the same people that install antivirus software on their computer but never actually run it. Too many people are perfectly content with running a ton of toolbars in their browser. Then want to complain that their computer is running slow. THAT is the ridiculous thing. But, it’s never the fault of the user. The ISP should have warned them or blocked it.
It wont work if it isn’t plugged in and turned on.
(Hopefully, this isn’t a dual post. I had another, longer reply, but it is being moderated. Not sure why – my language was clean. Anyway…)
The option to use your own web server would be great. But the average user isn’t going to setup their own web server. In addition, having your own web server is an additional security risk and an additional point of failure. Also, for the “viewing over the internet” feature to work, you would either have to shell out $ for a static IP (in the USA) or use a dynamic IP DNS service. Those can also cost $. And then if you use a dynamic IP DNS service, you are essentially doing the same thing these devices do out of the box.
These devices are not being marketed to “pros” they are for the average home computer user. If you want to and can setup your own web server, there are IP cameras you can get that don’t have internet support baked in.
Back in the day I set up an Apache web server on some spare equipment just for the kicks. Used a dynamic IP redirect service and all that. It was an interesting experiment that lasted a year.
These days, I can’t be bothered. I realize one can do a lot more with a home based server now, but I am just not as interested like I once was in tweaking and configuring and all that goes with it. I’m more likely to use a setup wizard and then go back to change a config or two. I want things to “just work”, and preferably to “just work securely” without a lot of fuss.
I’m super interested in IoT, but my interest at this point is mostly academic. The security issues particularly bad and I have no intention of being someone else’s case study.
I do completely understand. There are plenty of things I’ve lost motivation for over the years (even with technology). Everyone has their own interests, motivations, and skill sets. There are things I’ve never been interested in doing. Even though I understand the dangers in leaving food preparation to other people, I spend alot of money on fast-food (mostly due to lack of time). It’s a choice. Though the burgers I sometimes cook from the pit are the best I’ve ever had. The basic fact is that this is a tech-security kinda website and I have always been driven by my deep heart-felt passions where technology is concerned. I really don’t see that feeling ever completely going away. I know that I am one of the few that feel what I do but that’s what makes life so interesting.
“Am I missing something?”
Nope. Most consumers, and apparently most people commenting here, don’t understand just how unfriendly the Internet is to connecting *in* to a specific service on your own Lan. You don’t have a fixed IP address, you either have to know how to open ports on your router/firewall or trust DLNA or some third party (like these guys are doing) to do it for you, and there are (horrors) a bunch of numbers involved in all of this. Numbers that can change, or have to be looked up in an easily-lost instruction manual or website. And if you do decide to allow it, watch out — if you’re not reading all the latest security bulletins you’ll likely eventually get hacked.
I have a lot of sympathy for companies that try to help consumers set up Internet devices like this. Yes, they need to do it better, and no, a non-expert won’t be able to tell the guys doing it for your good vs. bad guys doing it for their own. So you have to trust companies not to risk their brand by picking poorly. It’s a jungle on the Internet. If you choose to live in the jungle, you get to sleep with the snakes and lions, it’s just the way it is.
Great article on security problems with the IOT, Brian.
If only there were some consumer resources for everyday people (i.e. my parents or my neighbor) to turn to that can provide easy-to-understand and even easier-to-disable this sort of rogue traffic on our everyday home gateway routers/firewalls. Particularly either the kinds of devices provided by our cable/ISP providers. If it means buying some sort of “router-behind-a-router” to achieve that, then so be it.
The reality is that the average US consumer relies upon a non-negotiable mandatory router/gateway device that almost always has little or no firewall capabilities at all and guaranteed to have no exfiltration or data egress protection.
The IOT is the “rot from within” and will be the primary means for miscreants and criminals to attack and subvert our home networks – while our ISPs provide no ability or guidance towards protecting ourselves from these threats.
I would have to think…that when it comes to IoT…..business initiatives take precedence over security initiatives when marketing these IoT products and services to businesses, government, and consumers.
Let’s face it….consumers treat IoT devices no differently than any other appliances they have in their home. Even if they had the capability, most will never update their devices. And in some cases, updates are not possible by the way some IoT devices are designed; vendors will “fix” whatever the issue is in the next product line of the devices. It brings up a real problem with product life-cycle versus support life-cycle…
Even the comment that “its only a little heartbeat ping …” so don’t worry your pretty little consumer head over it is, in fact, completely disingenuous since that “little ping” will contain 2 bits of information (1) Your IP address along with the NAT’ed port the camera’s using (2) The fact that there’s a Foscam brand XYZ at that address.
So for any bad guy with either access to the camera’s s/w code or knowledge of of its (probably plentiful) security holes this is a huge step forward into hacking your home network.
More than a few people commenting do not get it, this guy does.
+1 FPR
Yes, the ping contains those two bits of information. But, your IP address can’t be considered private information. For most network setups, every web site you visit gets your IP address.
So that leaves the port information and fact that a certain brand/model camera is present. But who gets to see that information? How do you think a hacker would be able to get that info?
Don’t be so naive.
(In)security on IoT. In my multiple conversations with Silicon Valley startups (and their VCs), not ONE person wanted to bake security in right from the get-go. In fact, I was told explicitly by multiple people, that unless it was a customer requirement, or a regulatory/compliance/legal mandate – they were not pursuing security. And this was for the easiest part of security – i.e., technology (we didn’t even talk about people or processes).
Did any of them talk about this as being part of their marketing strategy? You know, so that after the first really big wave of IoT hacks, they can sell new and improved secure second generation devices.
The scary part of IoT won’t come for a few years, when devices will be end of life and no longer supported by the vendor. Now, imagine all of those unpatched security holes into your home network! Once a network has been breached …
China has a bad reputation. Remember about malware in Lenovo?
Not surprised at all
This is another example of the type exposures that are related to IoT and the need for improved controls and perhaps some standardization that addresses security protocols for connected devices used by many consumers.
It will affect children too… Toys will connect to internet too, and there are risks that the parents should know how to avoid:
https://securitycatch.com/internet-connected-toys-a-new-worry-for-parents/