Crooks who peddle stolen credit cards on the Internet face a constant challenge: Keeping their shops online and reachable in the face of meddling from law enforcement officials, security firms, researchers and vigilantes. In this post, we’ll examine a large collection of hacked computers around the world that currently serves as a criminal cloud hosting environment for a variety of cybercrime operations, from sending spam to hosting malicious software and stolen credit card shops.
I first became aware of this botnet, which I’ve been referring to as the “Dark Cloud” for want of a better term, after hearing from Noah Dunker, director of security labs at Kansas City-based vendor RiskAnalytics. Dunker reached out after watching a Youtube video I posted that featured some existing and historic credit card fraud sites. He asked what I knew about one of the carding sites in the video: A fraud shop called “Uncle Sam,” whose home page pictures a pointing Uncle Sam saying “I want YOU to swipe.”
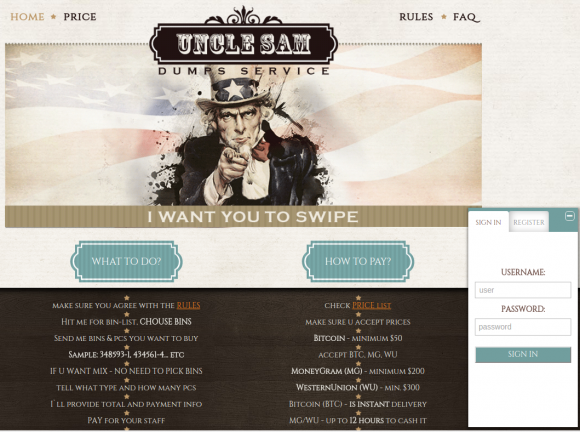
The “Uncle Sam” carding shop is one of a half-dozen that reside on a Dark Cloud criminal hosting environment.
I confessed that I knew little of this shop other than its existence, and asked why he was so interested in this particular crime store. Dunker showed me how the Uncle Sam card shop and at least four others were hosted by the same Dark Cloud, and how the system changed the Internet address of each Web site roughly every three minutes. The entire robot network, or”botnet,” consisted of thousands of hacked home computers spread across virtually every time zone in the world, he said.
Dunker urged me not to take his word for it, but to check for myself the domain name server (DNS) settings of the Uncle Sam shop every few minutes. DNS acts as a kind of Internet white pages, by translating Web site names to numeric addresses that are easier for computers to navigate. The way this so-called “fast-flux” botnet works is that it automatically updates the DNS records of each site hosted in the Dark Cloud every few minutes, randomly shuffling the Internet address of every site on the network from one compromised machine to another in a bid to frustrate those who might try to take the sites offline.
Sure enough, a simple script was all it took to find a few dozen Internet addresses assigned to the Uncle Sam shop over just 20 minutes of running the script. When I let the DNS lookup script run overnight, it came back with more than 1,000 unique addresses to which the site had been moved during the 12 or so hours I let it run. According to Dunker, the vast majority of those Internet addresses (> 80 percent) tie back to home Internet connections in Ukraine, with the rest in Russia and Romania.
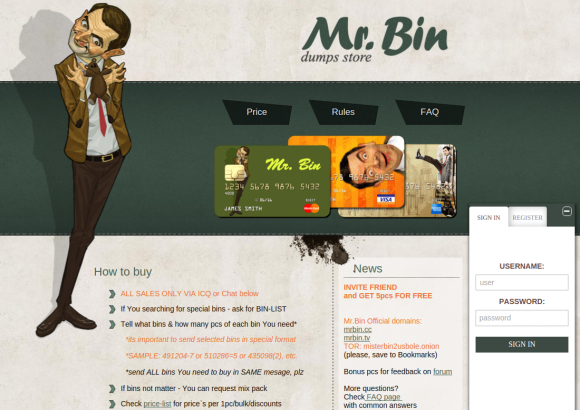
‘Mr. Bin,’ another carding shop hosting on the dark cloud service. A ‘bin’ is the “bank identification number” or the first six digits on a card, and it’s mainly how fraudsters search for stolen cards.
“Right now there’s probably over 2,000 infected endpoints that are mostly broadband subscribers in Eastern Europe,” enslaved as part of this botnet, Dunker said. “It’s a highly functional network, and it feels kind of like a black market version of Amazon Web Services. Some of the systems appear to be used for sending spam and some are for big dynamic scaled content delivery.”
Dunker said that historic DNS records indicate that this botnet has been in operation for at least the past year, but that there are signs it was up and running as early as Summer 2014.
Wayne Crowder, director of threat intelligence for RiskAnalytics, said the botnet appears to be a network structure set up to push different crimeware, including ransomware, click fraud tools, banking Trojans and spam.
Crowder said the Windows-based malware that powers the botnet assigns infected hosts different roles, depending on the victim machine’s strengths or weaknesses: More powerful systems might be used as DNS servers, while infected systems behind home routers may be infected with a “reverse proxy,” which lets the attackers control the system remotely.
“Once it’s infected, it phones home and gets a role assigned to it,” Crowder said. “That may be to continue sending spam, host a reverse proxy, or run a DNS server. It kind of depends on what capabilities it has.”
Indeed, this network does feel rather spammy. In my book Spam Nation, I detailed how the largest spam affiliate program on the planet at the time used a similar fast-flux network of compromised systems to host its network of pill sites that were being promoted in the junk email. Many of the domains used in those spam campaigns were two- and three-word domains that appeared to be randomly created for use in malware and spam distribution.
“We’re seeing two English words separated by a dash,” Dunker said the hundreds of hostnames found on the dark cloud network that do not appear to be used for carding shops. “It’s a very spammy naming convention.”
It’s unclear whether this botnet is being used by more than one individual or group. The variety of crimeware campaigns that RiskAnalytics has tracked operated through the network suggests that it may be rented out to multiple different cybercrooks. Still, other clues suggests the whole thing may have been orchestrated by the same gang.
For example, nearly all of the carding sites hosted on the dark cloud network — including Uncle Sam, Scrooge McDuck, Mr. Bin, Try2Swipe, Popeye, and Royaldumps — share the same or very similar site designs. All of them say that customers can look up available cards for sale at the site, but that purchasing the cards requires first contacting the proprietor of the shops directly via instant message.
All six of these shops — and only these six — are advertised prominently on the cybercrime forum prvtzone[dot]su. It is unclear whether this forum is run or frequented by the people who run this botnet, but the forum does heavily steer members interested in carding toward these six carding services. It’s unclear why, but Prvtzone has a Google Analytics tracking ID (UA-65055767) embedded in the HTML source of its page that may hold clues about the proprietors of this crime forum.
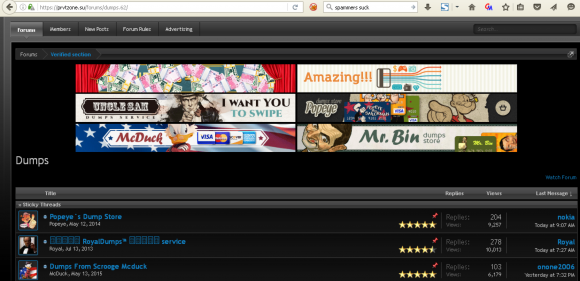
The “dumps” section of the cybercrime forum Prvtzone advertises all six of the carding domains found on the fast-flux network.
Dunker says he’s convinced it’s one group that occasionally rents out the infrastructure to other criminals.
“At this point, I’m positive that there’s one overarching organized crime operation driving this whole thing,” Dunker said. “But they do appear to be leasing parts of it out to others.”
Dunker and Crowder say they hope to release an initial report on their findings about the botnet sometime next week, but that for now the rabbit hole appears to go quite deep with this crime machine. For instance, there are several sites hosted on the network that appear to be clones of real businesses selling expensive farm equipment in Europe, and multiple sites report that these are fake companies looking to scam the unwary.
“There are a lot of questions that this research poses that we’d like to be able to answer,” Crowder said.
For now, I’d invite anyone interested to feel free to contribute to the research. This text file contains a historic record of domains I found that are or were at one time tied to the 40 or so Internet addresses I found in my initial, brief DNS scans of this network. Here’s a larger list of some 1,024 addresses that came up when I ran the scan for about 12 hours.
If you liked this story, check out this piece about another carding forum called Joker’s Stash, which also uses a unique communications system to keep itself online and reachable to all comers.





Hello Brian:
It would seem a way to defeat fast-flux would be to setup some sort of DNS black-list for domains that rapidly change address info repeatedly, for some given low threshold. Any domain that exceeds the threshold gets added to the black-list, so these changing sites get ignored.
Comments?
Thanks,
-Don Lenamond
General Communications, Inc.
You might want to whitelist amazon.com and some other sites as well to avoid blocking them.
There’s always the Mannheim score which can be used to detect a fast flux domain (and potentially n-flux).
1.32 * numIP + 18.54 * numASN > 142.38
where:
numIPs – number of distinct IP addresses
numASN – number of unique autonomous system numbers of IP addresses
numNS – number of used name servers for the given domain
It’s not a foolproof method but it could be improved with whois data, etc..
why? sites like this are used by carders, who aren’t going to care about your silly blacklist. You might be able to get them entered into the spam RBL databases (if they aren’t already) but that’s a lot of flux for those lists, since the spammers can call up new hosts just about any time they want.
Don,
I think blacklists are not a viable solution when dealing with large amount of domains since they become unwieldy fast. A better idea would be to disallow TTL for all newly-created domains below a fixed value (e.g., 24 hours) so that it’s easier to block and/or identify those which attempt to fast-flux. I’m sure there are many issues with this approach (AWS and other cloud vendors have lower TTLs for availability/load distribution/other legitimate reasons), this goes back to the “How to improve DNS without broad DNSSEC adoption?” discussion.
Setting TTL very low is a problem for a lot of legitimate sites that use high availability. If you’ve got two data centers, and need the ability to fail over from one to another using (for example) F5 load balancers, having a TTL of greater than 24 hours means it’ll take more than 24 hours to effectively fail over. This is unacceptable for pretty much every business function that would set themselves up with that kind of redundancy to begin with.
Well… great.
I will start by stating I am not an IT expert so this may sound incredible elementary, but, if these shops are changing their location every 3 minutes, how do users access them? I wouldn’t assume the forum postings are also updating the address every 3 minutes to show their current location. I could also assume people search by name but it seems it would have to be more detailed than that. can anyone explain this for a non-expert?
Ken: When you go to a Web site, you probably don’t type in its IP address; you type in its domain name. In the case of this site, that’s krebsonsecurity.com, but it also has another address: currently 72.52.7.144.
But you don’t have to know my numeric address to get to my site, even though pasting that numeric address above will also get you to my site. That’s what DNS does; it handles the lookup of “hey, where is this site” so you don’t have to. In this case, the bad guys have more or less told their sites to round-robin through a new IP every 3 minutes or so. But it doesn’t matter what IP it’s moved to. DNS just works, and your browser gets sent to the current IP.
Yes but normally DNS updates take some time to propagate – how does this system account for that?
DNS has a TTL setting (Time To Live) that dictates how often a DNS client will request an updated DNS record. Whoever maintains the DNS settings for a particular hostname can set a custom TTL value. In the case that Brian is describing, they likely set the TTL value to 3 minutes or less to ensure that DNS clients (including your router, mobile device, computer, etc.) request updated DNS records frequently enough to reflect the new IP address.
Yeah, I would think that it won’t be too difficult for the law enforcement to run your script for about a month or so and “scrape” the full list of IPs of infected computers/botnets. It’s a finite, and somewhat smaller subset of computers. And then either notify them via their ISPs, or if such is not possible, to simply “DDoS them”, which should not be that difficult in case of residential/small business PCs, to kill this “dark cloud.” DDoS’ing in theory should alert legitimate users of those PCs to a problem, and hopefully result in reinstallation of the OS, which would wipe out the infection.
The problem with DDOS infected machines is that you’ll never know when it has been disinfected. Toss in dynamic DNS addresses issued by an ISP swapping to another customer whenever, and you’ll see that’s no solution.
DDoSing is against the law, and could be also be viewed as an act of terrorism or war if someone in one country (such as US) did it to someone in Russia (which is the area where these are)
DDoSing with a flood of traffic is against the law (in certain jurisdictions) but that’s not what they are suggesting and its not the only way to DDoS. If you get the service providers to disconnect every available host, legally (since they are violating their terms of service by participating in a criminal network) then you have effectively DDoS’d that network by shutting every node down. Legally.
Then its rather DoS then DDoS. There are ISPs out here doing so if they see malicious traffic from customers, redirect all http to an own site stating the customer is taken offline since he seems to be infectetd.
There are many many different hosts as a part of this botnet. Taking them all down cant be done at once (a DoS) but requires a lot of small actions (hitting all the different parts) which fits the definition of a Distributed DoS.
Unfortunately, you can’t simply wipe the infection from a computer because the *user* will often still be infected. Not by the malware itself obviously, but by poor technical knowledge, poor attitude to improving this knowledge, poor security practices – and a tendency to click every shiny thing, email attachment, clickbait headline, and ‘official looking’ popup their computer presents them with. Then they’re simply going to reinfect their computer.
Your FREE Windows 11 upgrade is ready! Click here to install!
“All of them say that customers can look up available cards for sale at the site….” Is it risk-free for J.Q. Public to search these sites to learn if a particular card has been compromised?
I’d say yes, and if you live in US where you are protected from fraud, why would you bother?
@ Jay: Are you familiar with the ten-foot-pole rule?
Team Cymru blogged about this infrastructure last month. Back in March, it was observed providing double-flux (https://en.wikipedia.org/wiki/Fast_flux) infrastructure (proxies) for Kasidet, TreasureHunt, and Teslacrypt malware. As you’ve seen they have a massive number of domain names at their disposal, making this particularly challenging for anyone who doesn’t have arrest/subpoena authority.
Companies that only conduct business in the USA can do themselves a very big favor by blocking most non-US IP ranges. Try it, I think you’ll like it. 🙂
Like your dentist, Wendy’s, Home Depot, Target, etc. ?
Do you really think that they can’t figure out to use a US based proxy to get around blocking of non-US IP addresses?
I had an IT manager that did that once… My requests to unblock sites for business reasons piled up on his desk for days until I notified the CEO how much it was costing him for me to sit there and not do my job.
In short, it is an unworkable solution.
It depends upon the nature of your business. I know a business that blocks everything outside of the U.S. with exceptions for business partners, and it works well.
As an expat, it is getting increasingly annoying to find western websites that have blocked Chinese ips.
A significant portion of the web is blocked by a firewall at this side, then for the part that isn’t I come across sites that assume I am some criminal on the basis of my ip address.
Sure I can use a VPN – but that is a constant struggle and each morning when I wake I don’t know for sure that it will be working.
And yes, the site may think it only has customers within it’s own country – but organizations grow, and people retain links to countries they previously lived in.
PopeyeDs.cc, RoyalDumps.cc, try2swipe.bz have been registered fictitiously by one and the same person under alike names and with one and the same Moscow address, email and phone.
– Ivan Vladimirov http://whois.domaintools.com/popeyeds.cc
– Ivan Kuzmin http://whois.domaintools.com/royaldumps.cc
– Ivan Kazmin http://website.informer.com/Kazmin+Ivan.html
– Petr Vladimirov http://domainbigdata.com/email/ya.pvladimirov@yandex.com
I’ve always wondered how come that IANA officials register domains with bogus info.
Because as long as IANA gets paid, they won’t care. There used to be a time when checks were performed, but capitalism overtook common sense years ago.
I think you hit the nail on the head @Dave Horsfall. If money is the number one reason these sites are registered and there is no penalty for allowing sites to be registered for nefarious needs these points will always be open.
Botnets aside you can’t stop the Mom n Pop users clicking on links and getting infected…its damn near impossible. Tracking the offenders is most likely the best method of reducing this problem, the issue is the funding to track, investigate and prosecute these individuals is not necessarily funded by the card companies but the countries/targets of the carding scams. If the card companies had to contribute to the policing of the internet for these areas of access the resourcing issue may be lessened due to increased funding.
I preface all this with a simplistic view of the world and know there are much more complex matters at stake and equal legislation in various jurisdictions causes a myriad of headaches for local, state, federal and international policing efforts.
There are good reasons to allow fictitious information to register domains. Many repressive governments will not allow information to be distributed to their enslaved people. This may be religious, or political. The freedom you enjoy is not ubiquitous. Allowing registrations for paying customers with false information is one way to facilitate this and protect the site owner from oppression. As you can see it also benefits the criminals.
They don’t need the Dark Cloud. RSA put out a report a couple months back showing an incredible amount of fraud activity taking place right under our nose on Facebook and other social media sites. Go to Facebook, type in ‘cvv’ and see what you find. These guys are making no efforts to hide at all.
Another interesting asside. I’m still unsure of why everyone assumes DNS activity is bad. Unlike band switching of old radio, to get better output. Yea, I know, every request has a number attached. To get back home. So, how much information are they losing by hopping so fast. Sure, they must have a traceable home? A static for businesses purpose, wiretap? Loop a circuit, to trace? Another thought, could the server be backdoored?
What are the ratios of linux to windows bots on this sort of network? It wasn’t exactly mentioned in the article although the term “windows” was used…
does it matter? so what if linux is more leet. regular users dont care, period. they care about compatibility and familiarity, maybe not in that order. i was curious about linux then life happened and windows does everything i need 99.8% of the time, as a normal user…aka the type subject to being a bot, clicking links in emails, running files downloaded from the net, disabling noscript occasionally, pron sites, torrent sites, evej random googling for “free stuff”….i even started paying for av and firewall programs this year thinking it was a benefit(bit defender)…meh, still in the air, it has been PITA occasionally. no id theft, no viruses or malware taking hold, detections cleaned, no skittish behaviour or unexplained slow downs….
Coke, Pepsi, Dr. Pepper……
It all rots your teeth and offers a cool refreshing drink.
Linux does matter but only to a point (but isn’t the topic).
Thanks. I’m really interested in an actual answer because I pitched windows completely a few years back, basically because of what I read on Krebs…
I’m sure a good number of them are infected Linux based routers and such. Some home routers are more than powerful enough to use as a web server.
Wouldn’t the fast flux thing play hell with session management? I would think users of the carding sites would have trouble remaining authenticated long enough to do their misdeeds.
Some of the comments hint at reverse proxies. My guess is that when you connect to a fast flux end point, you’re just connecting to a proxy, whose main purpose is to prevent you from identifying the actual location of the true remote server.
Fwiw, modern Wi-Fi access points that use radius/whatever work similarly, they delegate all authentication to a central system, not the device to which you connect.
@Brian, I’d suggest not calling it a dark cloud, to me cloud indicates hosting the underlying infrastructure. This is more of a dark redirector. It’s probably much harder to get permission to eavesdrop on these middlemen, since some of the traffic is the private citizen traffic of the physical device owner. And if you contact that owner, they’re likely to take their machine down and clean it instead of letting you co-opt it to identify the real server address.
This problem isn’t really different from the one Clifford Stoll encountered when he was trying to track down unknown intruders. You had to contact the phone company, contact the court, get a court order, initiate a trace, all before the connection broke and any evidence was lost.
Would retrieving the authoritative DNS server for these temporary domains help? Or is it actually possible for anyone – say me on my private home internet – so set up a DNS server that feeds my DNS alterations BACK into the internet? If so well then that seems broken, doesn’t it? And if not then the target here should be the authoritative DNS servers that the criminals are using is it not?
PS: I realize doing that now is useless because those domains are gone. but your script is collecting data on the currently live domains couldn’t a ‘set query=ns’ be run on them simultaneously to look for authoritative DNS servers at the time?
I would say work on the at the domain registrar level, which is still problematic of course, but better than tracking ip addresses in my opinion.
The dns servers resolve the ip addresses and the domain registration specifies what dns servers to use. Shut down the domain at the registrar level and you have no dns servers and carder site is no longer accessible.
But that’s difficult to do ,I’m sure, even for law enforcement, and especially difficult if the registrar is in a foreign country as @timeless noted in his comment: contact ISP, then Court, get Court Order, work with foreign law enforcement , etc ….
Thus, combatting carders site is problematic, at best.
I just looked cloudcrimips.txt and mcduckips5-11.txt at the end of Brian’s blog post.
cloudcrimips.txt: the domains are changing frequently and the ip address stays the same
mcduckips5-11.txt : domain stays the same but ip address changes
So apparently both the domains AND the ip address rotate frequently .
Hmm… that makes combatting this strategy a bit difficult.
It’s pretty clear that the only way to stop these guys is to kill them. Kill 10-20 of them and the problem will diminish greatly.
But isn’t that murder? Hmm. Get wannabe murderer Jan Brewer to spearhead the operation.
Just get them labeled cyber ‘terrorists’ by the U.S. and let the drone ranger put them on his Tuesday assassination list and *voila*, problem solved!
RE: Using residential internet connections as reverse proxy for crime-site
Since most residential internet connections are behind NAT firewalls that require port forwarding, how is that dealt with?
a) Using web interface vulnerabilities to gain access to router admin panel to port forward.
b) Using UPnP (I’ve actually used UPnP at hotels to portforward servers)
c) The compromised bots are not behind NAT.
d) The routers themselves are compromised.
Also it could certainly be possible that the “back-end” server is hosted as a Tor hidden service so becoming your own compromised bot wouldn’t reveal the backend server IP to you.
I noticed the same thing a couple of months ago when I opened up a “secure” pdf attachment from a local construction company. I didn’t realize until I read this post that I was looking at the dark cloud. The name of the document contained a hyphen, which I didn’t know should have been a warning. It required me to log into Google Docs using my e-mail address and password. The attachment was a document about wealth management from Wells Fargo, which didn’t make sense coming from a construction company, and I noticed that the URL changed several times while the document was open. I contacted the company and learned that they had been hacked. I realized that it was a ruse to steal my e-mail address and password, so I quickly changed my password and reported the incident to Google and the FTA.
I hope you’ve enabled 2FA.
One of the good things about 2FA is that even if you temporarily leak your password, it isn’t good for much.
Attack the infected bots by encryption. Send key after owner has been notified of infection and sent instreuctions to disinfect machine and increase security.
Those too laszy or malicious wll be encrypted again. Not a total solution but maybe able to reduce size of botnet.
There has very recently been a change in the DNS information contained in certificates for many websites. It feels like this situation has alot to do with it. Not just in the amount of domains associated with this but also with the way these certs are written up and delivered.
Indeed thats a true statement. For further details you can visit to https://disqus.com
This botnet hasn’t been launching attacks indiscriminately. Neither the hostnames nor the IPs appear in the crowdsourced lists at
http://hosts-file.net/download/hosts.zip
http://feeds.dshield.org/block.txt
http://rules.emergingthreats.net/blockrules/compromised-ips.txt
http://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt